diff --git a/CHANGES.md b/CHANGES.md
index 5f625dad1d..72e8d64cf7 100644
--- a/CHANGES.md
+++ b/CHANGES.md
@@ -1,3 +1,184 @@
+Synapse 1.49.0rc1 (2021-12-07)
+==============================
+
+We've decided to move the existing, somewhat stagnant pages from the GitHub wiki
+to the [documentation website](https://matrix-org.github.io/synapse/latest/).
+
+This was done for two reasons. The first was to ensure that changes are checked by
+multiple authors before being committed (everyone makes mistakes!) and the second
+was visibility of the documentation. Not everyone knows that Synapse has some very
+useful information hidden away in its GitHub wiki pages. Bringing them to the
+documentation website should help with visibility, as well as keep all Synapse documentation
+in one, easily-searchable location.
+
+Note that contributions to the documentation website happen through [GitHub pull
+requests](https://github.com/matrix-org/synapse/pulls). Please visit [#synapse-dev:matrix.org](https://matrix.to/#/#synapse-dev:matrix.org)
+if you need help with the process!
+
+
+Features
+--------
+
+- Add [MSC3030](https://github.com/matrix-org/matrix-doc/pull/3030) experimental client and federation API endpoints to get the closest event to a given timestamp. ([\#9445](https://github.com/matrix-org/synapse/issues/9445))
+- Include bundled relation aggregations during a limited `/sync` request and `/relations` request, per [MSC2675](https://github.com/matrix-org/matrix-doc/pull/2675). ([\#11284](https://github.com/matrix-org/synapse/issues/11284), [\#11478](https://github.com/matrix-org/synapse/issues/11478))
+- Add plugin support for controlling database background updates. ([\#11306](https://github.com/matrix-org/synapse/issues/11306), [\#11475](https://github.com/matrix-org/synapse/issues/11475), [\#11479](https://github.com/matrix-org/synapse/issues/11479))
+- Support the stable API endpoints for [MSC2946](https://github.com/matrix-org/matrix-doc/pull/2946): the room `/hierarchy` endpoint. ([\#11329](https://github.com/matrix-org/synapse/issues/11329))
+- Add admin API to get some information about federation status with remote servers. ([\#11407](https://github.com/matrix-org/synapse/issues/11407))
+- Support expiry of refresh tokens and expiry of the overall session when refresh tokens are in use. ([\#11425](https://github.com/matrix-org/synapse/issues/11425))
+- Stabilise support for [MSC2918](https://github.com/matrix-org/matrix-doc/blob/main/proposals/2918-refreshtokens.md#msc2918-refresh-tokens) refresh tokens as they have now been merged into the Matrix specification. ([\#11435](https://github.com/matrix-org/synapse/issues/11435), [\#11522](https://github.com/matrix-org/synapse/issues/11522))
+- Update [MSC2918 refresh token](https://github.com/matrix-org/matrix-doc/blob/main/proposals/2918-refreshtokens.md#msc2918-refresh-tokens) support to confirm with the latest revision: accept the `refresh_tokens` parameter in the request body rather than in the URL parameters. ([\#11430](https://github.com/matrix-org/synapse/issues/11430))
+- Support configuring the lifetime of non-refreshable access tokens separately to refreshable access tokens. ([\#11445](https://github.com/matrix-org/synapse/issues/11445))
+- Expose `synapse_homeserver` and `synapse_worker` commands as entry points to run Synapse's main process and worker processes, respectively. Contributed by @Ma27. ([\#11449](https://github.com/matrix-org/synapse/issues/11449))
+- `synctl stop` will now wait for Synapse to exit before returning. ([\#11459](https://github.com/matrix-org/synapse/issues/11459), [\#11490](https://github.com/matrix-org/synapse/issues/11490))
+- Extend the "delete room" admin api to work correctly on rooms which have previously been partially deleted. ([\#11523](https://github.com/matrix-org/synapse/issues/11523))
+- Add support for the `/_matrix/client/v3/login/sso/redirect/{idpId}` API from Matrix v1.1. This endpoint was overlooked when support for v3 endpoints was added in Synapse 1.48.0rc1. ([\#11451](https://github.com/matrix-org/synapse/issues/11451))
+
+
+Bugfixes
+--------
+
+- Fix using [MSC2716](https://github.com/matrix-org/matrix-doc/pull/2716) batch sending in combination with event persistence workers. Contributed by @tulir at Beeper. ([\#11220](https://github.com/matrix-org/synapse/issues/11220))
+- Fix a long-standing bug where all requests that read events from the database could get stuck as a result of losing the database connection, properly this time. Also fix a race condition introduced in the previous insufficient fix in Synapse 1.47.0. ([\#11376](https://github.com/matrix-org/synapse/issues/11376))
+- The `/send_join` response now includes the stable `event` field instead of the unstable field from [MSC3083](https://github.com/matrix-org/matrix-doc/pull/3083). ([\#11413](https://github.com/matrix-org/synapse/issues/11413))
+- Fix a bug introduced in Synapse 1.47.0 where `send_join` could fail due to an outdated `ijson` version. ([\#11439](https://github.com/matrix-org/synapse/issues/11439), [\#11441](https://github.com/matrix-org/synapse/issues/11441), [\#11460](https://github.com/matrix-org/synapse/issues/11460))
+- Fix a bug introduced in Synapse 1.36.0 which could cause problems fetching event-signing keys from trusted key servers. ([\#11440](https://github.com/matrix-org/synapse/issues/11440))
+- Fix a bug introduced in Synapse 1.47.1 where the media repository would fail to work if the media store path contained any symbolic links. ([\#11446](https://github.com/matrix-org/synapse/issues/11446))
+- Fix an `LruCache` corruption bug, introduced in Synapse 1.38.0, that would cause certain requests to fail until the next Synapse restart. ([\#11454](https://github.com/matrix-org/synapse/issues/11454))
+- Fix a long-standing bug where invites from ignored users were included in incremental syncs. ([\#11511](https://github.com/matrix-org/synapse/issues/11511))
+- Fix a regression in Synapse 1.48.0 where presence workers would not clear their presence updates over replication on shutdown. ([\#11518](https://github.com/matrix-org/synapse/issues/11518))
+- Fix a regression in Synapse 1.48.0 where the module API's `looping_background_call` method would spam errors to the logs when given a non-async function. ([\#11524](https://github.com/matrix-org/synapse/issues/11524))
+
+
+Updates to the Docker image
+---------------------------
+
+- Update `Dockerfile-workers` to healthcheck all workers in the container. ([\#11429](https://github.com/matrix-org/synapse/issues/11429))
+
+
+Improved Documentation
+----------------------
+
+- Update the media repository documentation. ([\#11415](https://github.com/matrix-org/synapse/issues/11415))
+- Update section about backward extremities in the room DAG concepts doc to correct the misconception about backward extremities indicating whether we have fetched an events' `prev_events`. ([\#11469](https://github.com/matrix-org/synapse/issues/11469))
+
+
+Internal Changes
+----------------
+
+- Add `Final` annotation to string constants in `synapse.api.constants` so that they get typed as `Literal`s. ([\#11356](https://github.com/matrix-org/synapse/issues/11356))
+- Add a check to ensure that users cannot start the Synapse master process when `worker_app` is set. ([\#11416](https://github.com/matrix-org/synapse/issues/11416))
+- Add a note about postgres memory management and hugepages to postgres doc. ([\#11467](https://github.com/matrix-org/synapse/issues/11467))
+- Add missing type hints to `synapse.config` module. ([\#11465](https://github.com/matrix-org/synapse/issues/11465))
+- Add missing type hints to `synapse.federation`. ([\#11483](https://github.com/matrix-org/synapse/issues/11483))
+- Add type annotations to `tests.storage.test_appservice`. ([\#11488](https://github.com/matrix-org/synapse/issues/11488), [\#11492](https://github.com/matrix-org/synapse/issues/11492))
+- Add type annotations to some of the configuration surrounding refresh tokens. ([\#11428](https://github.com/matrix-org/synapse/issues/11428))
+- Add type hints to `synapse/tests/rest/admin`. ([\#11501](https://github.com/matrix-org/synapse/issues/11501))
+- Add type hints to storage classes. ([\#11411](https://github.com/matrix-org/synapse/issues/11411))
+- Add wiki pages to documentation website. ([\#11402](https://github.com/matrix-org/synapse/issues/11402))
+- Clean up `tests.storage.test_main` to remove use of legacy code. ([\#11493](https://github.com/matrix-org/synapse/issues/11493))
+- Clean up `tests.test_visibility` to remove legacy code. ([\#11495](https://github.com/matrix-org/synapse/issues/11495))
+- Convert status codes to `HTTPStatus` in `synapse.rest.admin`. ([\#11452](https://github.com/matrix-org/synapse/issues/11452), [\#11455](https://github.com/matrix-org/synapse/issues/11455))
+- Extend the `scripts-dev/sign_json` script to support signing events. ([\#11486](https://github.com/matrix-org/synapse/issues/11486))
+- Improve internal types in push code. ([\#11409](https://github.com/matrix-org/synapse/issues/11409))
+- Improve type annotations in `synapse.module_api`. ([\#11029](https://github.com/matrix-org/synapse/issues/11029))
+- Improve type hints for `LruCache`. ([\#11453](https://github.com/matrix-org/synapse/issues/11453))
+- Preparation for database schema simplifications: disambiguate queries on `state_key`. ([\#11497](https://github.com/matrix-org/synapse/issues/11497))
+- Refactor `backfilled` into specific behavior function arguments (`_persist_events_and_state_updates` and downstream calls). ([\#11417](https://github.com/matrix-org/synapse/issues/11417))
+- Refactor `get_version_string` to fix-up types and duplicated code. ([\#11468](https://github.com/matrix-org/synapse/issues/11468))
+- Refactor various parts of the `/sync` handler. ([\#11494](https://github.com/matrix-org/synapse/issues/11494), [\#11515](https://github.com/matrix-org/synapse/issues/11515))
+- Remove unnecessary `json.dumps` from `tests.rest.admin`. ([\#11461](https://github.com/matrix-org/synapse/issues/11461))
+- Save the OpenID Connect session ID on login. ([\#11482](https://github.com/matrix-org/synapse/issues/11482))
+- Update and clean up recently ported documentation pages. ([\#11466](https://github.com/matrix-org/synapse/issues/11466))
+
+
+Synapse 1.48.0 (2021-11-30)
+===========================
+
+This release removes support for the long-deprecated `trust_identity_server_for_password_resets` configuration flag.
+
+This release also fixes some performance issues with some background database updates introduced in Synapse 1.47.0.
+
+No significant changes since 1.48.0rc1.
+
+Synapse 1.48.0rc1 (2021-11-25)
+==============================
+
+Features
+--------
+
+- Experimental support for the thread relation defined in [MSC3440](https://github.com/matrix-org/matrix-doc/pull/3440). ([\#11161](https://github.com/matrix-org/synapse/issues/11161))
+- Support filtering by relation senders & types per [MSC3440](https://github.com/matrix-org/matrix-doc/pull/3440). ([\#11236](https://github.com/matrix-org/synapse/issues/11236))
+- Add support for the `/_matrix/client/v3` and `/_matrix/media/v3` APIs from Matrix v1.1. ([\#11318](https://github.com/matrix-org/synapse/issues/11318), [\#11371](https://github.com/matrix-org/synapse/issues/11371))
+- Support the stable version of [MSC2778](https://github.com/matrix-org/matrix-doc/pull/2778): the `m.login.application_service` login type. Contributed by @tulir. ([\#11335](https://github.com/matrix-org/synapse/issues/11335))
+- Add a new version of delete room admin API `DELETE /_synapse/admin/v2/rooms/<room_id>` to run it in the background. Contributed by @dklimpel. ([\#11223](https://github.com/matrix-org/synapse/issues/11223))
+- Allow the admin [Delete Room API](https://matrix-org.github.io/synapse/latest/admin_api/rooms.html#delete-room-api) to block a room without the need to join it. ([\#11228](https://github.com/matrix-org/synapse/issues/11228))
+- Add an admin API to un-shadow-ban a user. ([\#11347](https://github.com/matrix-org/synapse/issues/11347))
+- Add an admin API to run background database schema updates. ([\#11352](https://github.com/matrix-org/synapse/issues/11352))
+- Add an admin API for blocking a room. ([\#11324](https://github.com/matrix-org/synapse/issues/11324))
+- Update the JWT login type to support custom a `sub` claim. ([\#11361](https://github.com/matrix-org/synapse/issues/11361))
+- Store and allow querying of arbitrary event relations. ([\#11391](https://github.com/matrix-org/synapse/issues/11391))
+
+
+Bugfixes
+--------
+
+- Fix a long-standing bug wherein display names or avatar URLs containing null bytes cause an internal server error when stored in the DB. ([\#11230](https://github.com/matrix-org/synapse/issues/11230))
+- Prevent [MSC2716](https://github.com/matrix-org/matrix-doc/pull/2716) historical state events from being pushed to an application service via `/transactions`. ([\#11265](https://github.com/matrix-org/synapse/issues/11265))
+- Fix a long-standing bug where uploading extremely thin images (e.g. 1000x1) would fail. Contributed by @Neeeflix. ([\#11288](https://github.com/matrix-org/synapse/issues/11288))
+- Fix a bug, introduced in Synapse 1.46.0, which caused the `check_3pid_auth` and `on_logged_out` callbacks in legacy password authentication provider modules to not be registered. Modules using the generic module interface were not affected. ([\#11340](https://github.com/matrix-org/synapse/issues/11340))
+- Fix a bug introduced in 1.41.0 where space hierarchy responses would be incorrectly reused if multiple users were to make the same request at the same time. ([\#11355](https://github.com/matrix-org/synapse/issues/11355))
+- Fix a bug introduced in 1.45.0 where the `read_templates` method of the module API would error. ([\#11377](https://github.com/matrix-org/synapse/issues/11377))
+- Fix an issue introduced in 1.47.0 which prevented servers re-joining rooms they had previously left, if their signing keys were replaced. ([\#11379](https://github.com/matrix-org/synapse/issues/11379))
+- Fix a bug introduced in 1.13.0 where creating and publishing a room could cause errors if `room_list_publication_rules` is configured. ([\#11392](https://github.com/matrix-org/synapse/issues/11392))
+- Improve performance of various background database updates. ([\#11421](https://github.com/matrix-org/synapse/issues/11421), [\#11422](https://github.com/matrix-org/synapse/issues/11422))
+
+
+Improved Documentation
+----------------------
+
+- Suggest users of the Debian packages add configuration to `/etc/matrix-synapse/conf.d/` to prevent, upon upgrade, being asked to choose between their configuration and the maintainer's. ([\#11281](https://github.com/matrix-org/synapse/issues/11281))
+- Fix typos in the documentation for the `username_available` admin API. Contributed by Stanislav Motylkov. ([\#11286](https://github.com/matrix-org/synapse/issues/11286))
+- Add Single Sign-On, SAML and CAS pages to the documentation. ([\#11298](https://github.com/matrix-org/synapse/issues/11298))
+- Change the word 'Home server' as one word 'homeserver' in documentation. ([\#11320](https://github.com/matrix-org/synapse/issues/11320))
+- Fix missing quotes for wildcard domains in `federation_certificate_verification_whitelist`. ([\#11381](https://github.com/matrix-org/synapse/issues/11381))
+
+
+Deprecations and Removals
+-------------------------
+
+- Remove deprecated `trust_identity_server_for_password_resets` configuration flag. ([\#11333](https://github.com/matrix-org/synapse/issues/11333), [\#11395](https://github.com/matrix-org/synapse/issues/11395))
+
+
+Internal Changes
+----------------
+
+- Add type annotations to `synapse.metrics`. ([\#10847](https://github.com/matrix-org/synapse/issues/10847))
+- Split out federated PDU retrieval function into a non-cached version. ([\#11242](https://github.com/matrix-org/synapse/issues/11242))
+- Clean up code relating to to-device messages and sending ephemeral events to application services. ([\#11247](https://github.com/matrix-org/synapse/issues/11247))
+- Fix a small typo in the error response when a relation type other than 'm.annotation' is passed to `GET /rooms/{room_id}/aggregations/{event_id}`. ([\#11278](https://github.com/matrix-org/synapse/issues/11278))
+- Drop unused database tables `room_stats_historical` and `user_stats_historical`. ([\#11280](https://github.com/matrix-org/synapse/issues/11280))
+- Require all files in synapse/ and tests/ to pass mypy unless specifically excluded. ([\#11282](https://github.com/matrix-org/synapse/issues/11282), [\#11285](https://github.com/matrix-org/synapse/issues/11285), [\#11359](https://github.com/matrix-org/synapse/issues/11359))
+- Add missing type hints to `synapse.app`. ([\#11287](https://github.com/matrix-org/synapse/issues/11287))
+- Remove unused parameters on `FederationEventHandler._check_event_auth`. ([\#11292](https://github.com/matrix-org/synapse/issues/11292))
+- Add type hints to `synapse._scripts`. ([\#11297](https://github.com/matrix-org/synapse/issues/11297))
+- Fix an issue which prevented the `remove_deleted_devices_from_device_inbox` background database schema update from running when updating from a recent Synapse version. ([\#11303](https://github.com/matrix-org/synapse/issues/11303))
+- Add type hints to storage classes. ([\#11307](https://github.com/matrix-org/synapse/issues/11307), [\#11310](https://github.com/matrix-org/synapse/issues/11310), [\#11311](https://github.com/matrix-org/synapse/issues/11311), [\#11312](https://github.com/matrix-org/synapse/issues/11312), [\#11313](https://github.com/matrix-org/synapse/issues/11313), [\#11314](https://github.com/matrix-org/synapse/issues/11314), [\#11316](https://github.com/matrix-org/synapse/issues/11316), [\#11322](https://github.com/matrix-org/synapse/issues/11322), [\#11332](https://github.com/matrix-org/synapse/issues/11332), [\#11339](https://github.com/matrix-org/synapse/issues/11339), [\#11342](https://github.com/matrix-org/synapse/issues/11342))
+- Add type hints to `synapse.util`. ([\#11321](https://github.com/matrix-org/synapse/issues/11321), [\#11328](https://github.com/matrix-org/synapse/issues/11328))
+- Improve type annotations in Synapse's test suite. ([\#11323](https://github.com/matrix-org/synapse/issues/11323), [\#11330](https://github.com/matrix-org/synapse/issues/11330))
+- Test that room alias deletion works as intended. ([\#11327](https://github.com/matrix-org/synapse/issues/11327))
+- Add type annotations for some methods and properties in the module API. ([\#11341](https://github.com/matrix-org/synapse/issues/11341))
+- Fix running `scripts-dev/complement.sh`, which was broken in v1.47.0rc1. ([\#11368](https://github.com/matrix-org/synapse/issues/11368))
+- Rename internal functions for token generation to better reflect what they do. ([\#11369](https://github.com/matrix-org/synapse/issues/11369), [\#11370](https://github.com/matrix-org/synapse/issues/11370))
+- Add type hints to configuration classes. ([\#11377](https://github.com/matrix-org/synapse/issues/11377))
+- Publish a `develop` image to Docker Hub. ([\#11380](https://github.com/matrix-org/synapse/issues/11380))
+- Keep fallback key marked as used if it's re-uploaded. ([\#11382](https://github.com/matrix-org/synapse/issues/11382))
+- Use `auto_attribs` on the `attrs` class `RefreshTokenLookupResult`. ([\#11386](https://github.com/matrix-org/synapse/issues/11386))
+- Rename unstable `access_token_lifetime` configuration option to `refreshable_access_token_lifetime` to make it clear it only concerns refreshable access tokens. ([\#11388](https://github.com/matrix-org/synapse/issues/11388))
+- Do not run the broken MSC2716 tests when running `scripts-dev/complement.sh`. ([\#11389](https://github.com/matrix-org/synapse/issues/11389))
+- Remove dead code from supporting ACME. ([\#11393](https://github.com/matrix-org/synapse/issues/11393))
+- Refactor including the bundled relations when serializing an event. ([\#11408](https://github.com/matrix-org/synapse/issues/11408))
+
+
Synapse 1.47.1 (2021-11-23)
===========================
diff --git a/changelog.d/10520.misc b/changelog.d/10520.misc
new file mode 100644
index 0000000000..a911e165da
--- /dev/null
+++ b/changelog.d/10520.misc
@@ -0,0 +1 @@
+Send and handle cross-signing messages using the stable prefix.
diff --git a/changelog.d/10847.misc b/changelog.d/10847.misc
deleted file mode 100644
index 7933a38dca..0000000000
--- a/changelog.d/10847.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type annotations to `synapse.metrics`.
diff --git a/changelog.d/11029.misc b/changelog.d/11029.misc
deleted file mode 100644
index 111de5fc7a..0000000000
--- a/changelog.d/11029.misc
+++ /dev/null
@@ -1 +0,0 @@
-Improve type annotations in `synapse.module_api`.
\ No newline at end of file
diff --git a/changelog.d/11161.feature b/changelog.d/11161.feature
deleted file mode 100644
index 76b0d28084..0000000000
--- a/changelog.d/11161.feature
+++ /dev/null
@@ -1 +0,0 @@
-Experimental support for the thread relation defined in [MSC3440](https://github.com/matrix-org/matrix-doc/pull/3440).
diff --git a/changelog.d/11220.bugfix b/changelog.d/11220.bugfix
deleted file mode 100644
index 8baae28d5b..0000000000
--- a/changelog.d/11220.bugfix
+++ /dev/null
@@ -1 +0,0 @@
-Fix using MSC2716 batch sending in combination with event persistence workers. Contributed by @tulir at Beeper.
diff --git a/changelog.d/11223.feature b/changelog.d/11223.feature
deleted file mode 100644
index 55ea693dcd..0000000000
--- a/changelog.d/11223.feature
+++ /dev/null
@@ -1 +0,0 @@
-Add a new version of delete room admin API `DELETE /_synapse/admin/v2/rooms/<room_id>` to run it in background. Contributed by @dklimpel.
\ No newline at end of file
diff --git a/changelog.d/11228.feature b/changelog.d/11228.feature
deleted file mode 100644
index 33c1756b50..0000000000
--- a/changelog.d/11228.feature
+++ /dev/null
@@ -1 +0,0 @@
-Allow the admin [Delete Room API](https://matrix-org.github.io/synapse/latest/admin_api/rooms.html#delete-room-api) to block a room without the need to join it.
diff --git a/changelog.d/11230.bugfix b/changelog.d/11230.bugfix
deleted file mode 100644
index b2d6d4d024..0000000000
--- a/changelog.d/11230.bugfix
+++ /dev/null
@@ -1,2 +0,0 @@
-Fix a long-standing bug wherein display names or avatar URLs containing null bytes cause an internal server error
-when stored in the DB.
\ No newline at end of file
diff --git a/changelog.d/11236.feature b/changelog.d/11236.feature
deleted file mode 100644
index e7aeee2aa6..0000000000
--- a/changelog.d/11236.feature
+++ /dev/null
@@ -1 +0,0 @@
-Support filtering by relation senders & types per [MSC3440](https://github.com/matrix-org/matrix-doc/pull/3440).
diff --git a/changelog.d/11242.misc b/changelog.d/11242.misc
deleted file mode 100644
index 3a98259edf..0000000000
--- a/changelog.d/11242.misc
+++ /dev/null
@@ -1 +0,0 @@
-Split out federated PDU retrieval function into a non-cached version.
diff --git a/changelog.d/11247.misc b/changelog.d/11247.misc
deleted file mode 100644
index 5ce701560e..0000000000
--- a/changelog.d/11247.misc
+++ /dev/null
@@ -1 +0,0 @@
-Clean up code relating to to-device messages and sending ephemeral events to application services.
\ No newline at end of file
diff --git a/changelog.d/11265.bugfix b/changelog.d/11265.bugfix
deleted file mode 100644
index b0e9dfac53..0000000000
--- a/changelog.d/11265.bugfix
+++ /dev/null
@@ -1 +0,0 @@
-Prevent [MSC2716](https://github.com/matrix-org/matrix-doc/pull/2716) historical state events from being pushed to an application service via `/transactions`.
diff --git a/changelog.d/11278.misc b/changelog.d/11278.misc
deleted file mode 100644
index 9b014bc8b4..0000000000
--- a/changelog.d/11278.misc
+++ /dev/null
@@ -1 +0,0 @@
-Fix a small typo in the error response when a relation type other than 'm.annotation' is passed to `GET /rooms/{room_id}/aggregations/{event_id}`.
\ No newline at end of file
diff --git a/changelog.d/11280.misc b/changelog.d/11280.misc
deleted file mode 100644
index 8417c8ffef..0000000000
--- a/changelog.d/11280.misc
+++ /dev/null
@@ -1 +0,0 @@
-Drop unused db tables `room_stats_historical` and `user_stats_historical`.
\ No newline at end of file
diff --git a/changelog.d/11281.doc b/changelog.d/11281.doc
deleted file mode 100644
index ab27ed193c..0000000000
--- a/changelog.d/11281.doc
+++ /dev/null
@@ -1 +0,0 @@
-Suggest users of the Debian packages add configuration to `/etc/matrix-synapse/conf.d/` to prevent, upon upgrade, being asked to choose between their configuration and the maintainer's.
diff --git a/changelog.d/11282.misc b/changelog.d/11282.misc
deleted file mode 100644
index 4720519cbc..0000000000
--- a/changelog.d/11282.misc
+++ /dev/null
@@ -1 +0,0 @@
-Require all files in synapse/ and tests/ to pass mypy unless specifically excluded.
diff --git a/changelog.d/11285.misc b/changelog.d/11285.misc
deleted file mode 100644
index 4720519cbc..0000000000
--- a/changelog.d/11285.misc
+++ /dev/null
@@ -1 +0,0 @@
-Require all files in synapse/ and tests/ to pass mypy unless specifically excluded.
diff --git a/changelog.d/11286.doc b/changelog.d/11286.doc
deleted file mode 100644
index 890d7b4ee4..0000000000
--- a/changelog.d/11286.doc
+++ /dev/null
@@ -1 +0,0 @@
-Fix typo in the word `available` and fix HTTP method (should be `GET`) for the `username_available` admin API. Contributed by Stanislav Motylkov.
diff --git a/changelog.d/11287.misc b/changelog.d/11287.misc
deleted file mode 100644
index 26ec3cb657..0000000000
--- a/changelog.d/11287.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add missing type hints to `synapse.app`.
diff --git a/changelog.d/11288.bugfix b/changelog.d/11288.bugfix
deleted file mode 100644
index d85b1779ba..0000000000
--- a/changelog.d/11288.bugfix
+++ /dev/null
@@ -1 +0,0 @@
-Fix a long-standing bug where uploading extremely thin images (e.g. 1000x1) would fail. Contributed by @Neeeflix.
diff --git a/changelog.d/11292.misc b/changelog.d/11292.misc
deleted file mode 100644
index d1b76b1574..0000000000
--- a/changelog.d/11292.misc
+++ /dev/null
@@ -1 +0,0 @@
-Remove unused parameters on `FederationEventHandler._check_event_auth`.
diff --git a/changelog.d/11297.misc b/changelog.d/11297.misc
deleted file mode 100644
index 856b856847..0000000000
--- a/changelog.d/11297.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type hints to `synapse._scripts`.
diff --git a/changelog.d/11298.doc b/changelog.d/11298.doc
deleted file mode 100644
index 64ca1c84ed..0000000000
--- a/changelog.d/11298.doc
+++ /dev/null
@@ -1 +0,0 @@
-Add Single Sign-On, SAML and CAS pages to the documentation.
diff --git a/changelog.d/11303.misc b/changelog.d/11303.misc
deleted file mode 100644
index 50af92bfa5..0000000000
--- a/changelog.d/11303.misc
+++ /dev/null
@@ -1 +0,0 @@
-Fix an issue which prevented the 'remove deleted devices from device_inbox column' background process from running when updating from a recent Synapse version.
diff --git a/changelog.d/11306.feature b/changelog.d/11306.feature
deleted file mode 100644
index aba3292015..0000000000
--- a/changelog.d/11306.feature
+++ /dev/null
@@ -1 +0,0 @@
-Add plugin support for controlling database background updates.
diff --git a/changelog.d/11307.misc b/changelog.d/11307.misc
deleted file mode 100644
index 86594a332d..0000000000
--- a/changelog.d/11307.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type hints to storage classes.
diff --git a/changelog.d/11310.misc b/changelog.d/11310.misc
deleted file mode 100644
index e5c12445d5..0000000000
--- a/changelog.d/11310.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type hints to storage classes.
\ No newline at end of file
diff --git a/changelog.d/11311.misc b/changelog.d/11311.misc
deleted file mode 100644
index 86594a332d..0000000000
--- a/changelog.d/11311.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type hints to storage classes.
diff --git a/changelog.d/11312.misc b/changelog.d/11312.misc
deleted file mode 100644
index 86594a332d..0000000000
--- a/changelog.d/11312.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type hints to storage classes.
diff --git a/changelog.d/11313.misc b/changelog.d/11313.misc
deleted file mode 100644
index 86594a332d..0000000000
--- a/changelog.d/11313.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type hints to storage classes.
diff --git a/changelog.d/11314.misc b/changelog.d/11314.misc
deleted file mode 100644
index 86594a332d..0000000000
--- a/changelog.d/11314.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type hints to storage classes.
diff --git a/changelog.d/11316.misc b/changelog.d/11316.misc
deleted file mode 100644
index 86594a332d..0000000000
--- a/changelog.d/11316.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type hints to storage classes.
diff --git a/changelog.d/11318.feature b/changelog.d/11318.feature
deleted file mode 100644
index ce28fc1eef..0000000000
--- a/changelog.d/11318.feature
+++ /dev/null
@@ -1 +0,0 @@
-Add support for the `/_matrix/client/v3` APIs from Matrix v1.1.
\ No newline at end of file
diff --git a/changelog.d/11320.doc b/changelog.d/11320.doc
deleted file mode 100644
index 333101736f..0000000000
--- a/changelog.d/11320.doc
+++ /dev/null
@@ -1 +0,0 @@
-Changed the word 'Home server' as one word 'homeserver' in documentation.
\ No newline at end of file
diff --git a/changelog.d/11321.misc b/changelog.d/11321.misc
deleted file mode 100644
index 7c377813e8..0000000000
--- a/changelog.d/11321.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type hints to `synapse.util`.
diff --git a/changelog.d/11322.misc b/changelog.d/11322.misc
deleted file mode 100644
index 86594a332d..0000000000
--- a/changelog.d/11322.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type hints to storage classes.
diff --git a/changelog.d/11323.misc b/changelog.d/11323.misc
deleted file mode 100644
index 54f39e1844..0000000000
--- a/changelog.d/11323.misc
+++ /dev/null
@@ -1 +0,0 @@
-Improve type annotations in Synapse's test suite.
\ No newline at end of file
diff --git a/changelog.d/11324.feature b/changelog.d/11324.feature
deleted file mode 100644
index 55494358bb..0000000000
--- a/changelog.d/11324.feature
+++ /dev/null
@@ -1 +0,0 @@
-Add dedicated admin API for blocking a room.
\ No newline at end of file
diff --git a/changelog.d/11327.misc b/changelog.d/11327.misc
deleted file mode 100644
index 389e360457..0000000000
--- a/changelog.d/11327.misc
+++ /dev/null
@@ -1 +0,0 @@
-Test that room alias deletion works as intended.
\ No newline at end of file
diff --git a/changelog.d/11328.misc b/changelog.d/11328.misc
deleted file mode 100644
index 7c377813e8..0000000000
--- a/changelog.d/11328.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type hints to `synapse.util`.
diff --git a/changelog.d/11329.feature b/changelog.d/11329.feature
deleted file mode 100644
index 7e0efb3b00..0000000000
--- a/changelog.d/11329.feature
+++ /dev/null
@@ -1 +0,0 @@
-Support the stable API endpoints for [MSC2946](https://github.com/matrix-org/matrix-doc/pull/2946): the room `/hierarchy` endpoint.
diff --git a/changelog.d/11330.misc b/changelog.d/11330.misc
deleted file mode 100644
index 86f26543dd..0000000000
--- a/changelog.d/11330.misc
+++ /dev/null
@@ -1 +0,0 @@
-Improve type annotations in Synapse's test suite.
diff --git a/changelog.d/11331.misc b/changelog.d/11331.misc
new file mode 100644
index 0000000000..1ab3a6a975
--- /dev/null
+++ b/changelog.d/11331.misc
@@ -0,0 +1 @@
+A test helper (`wait_for_background_updates`) no longer depends on classes defining a `store` property.
diff --git a/changelog.d/11332.misc b/changelog.d/11332.misc
deleted file mode 100644
index 86594a332d..0000000000
--- a/changelog.d/11332.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type hints to storage classes.
diff --git a/changelog.d/11333.misc b/changelog.d/11333.misc
deleted file mode 100644
index 6c1fd560ad..0000000000
--- a/changelog.d/11333.misc
+++ /dev/null
@@ -1 +0,0 @@
-Remove deprecated `trust_identity_server_for_password_resets` configuration flag.
\ No newline at end of file
diff --git a/changelog.d/11335.feature b/changelog.d/11335.feature
deleted file mode 100644
index 9b6c1b9c23..0000000000
--- a/changelog.d/11335.feature
+++ /dev/null
@@ -1 +0,0 @@
-Support the stable version of [MSC2778](https://github.com/matrix-org/matrix-doc/pull/2778): the `m.login.application_service` login type. Contributed by @tulir.
diff --git a/changelog.d/11339.misc b/changelog.d/11339.misc
deleted file mode 100644
index 86594a332d..0000000000
--- a/changelog.d/11339.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type hints to storage classes.
diff --git a/changelog.d/11340.bugfix b/changelog.d/11340.bugfix
deleted file mode 100644
index 551817f42d..0000000000
--- a/changelog.d/11340.bugfix
+++ /dev/null
@@ -1 +0,0 @@
-Fix a bug, introduced in Synapse 1.46.0, which caused the `check_3pid_auth` and `on_logged_out` callbacks in legacy password authentication provider modules to not be registered. Modules using the generic module API were not affected.
diff --git a/changelog.d/11341.misc b/changelog.d/11341.misc
deleted file mode 100644
index 3d8da755ee..0000000000
--- a/changelog.d/11341.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type annotations for some methods and properties in the module API.
diff --git a/changelog.d/11342.misc b/changelog.d/11342.misc
deleted file mode 100644
index 86594a332d..0000000000
--- a/changelog.d/11342.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type hints to storage classes.
diff --git a/changelog.d/11347.feature b/changelog.d/11347.feature
deleted file mode 100644
index b0cb5345a0..0000000000
--- a/changelog.d/11347.feature
+++ /dev/null
@@ -1 +0,0 @@
-Add admin API to un-shadow-ban a user.
diff --git a/changelog.d/11352.feature b/changelog.d/11352.feature
deleted file mode 100644
index a4d01b3549..0000000000
--- a/changelog.d/11352.feature
+++ /dev/null
@@ -1 +0,0 @@
-Add admin API to run background jobs.
\ No newline at end of file
diff --git a/changelog.d/11355.bugfix b/changelog.d/11355.bugfix
deleted file mode 100644
index 91639f14b2..0000000000
--- a/changelog.d/11355.bugfix
+++ /dev/null
@@ -1 +0,0 @@
-Fix a bug introduced in 1.41.0 where space hierarchy responses would be incorrectly reused if multiple users were to make the same request at the same time.
diff --git a/changelog.d/11356.misc b/changelog.d/11356.misc
deleted file mode 100644
index 01ce6a306c..0000000000
--- a/changelog.d/11356.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add `Final` annotation to string constants in `synapse.api.constants` so that they get typed as `Literal`s.
diff --git a/changelog.d/11359.misc b/changelog.d/11359.misc
deleted file mode 100644
index 4720519cbc..0000000000
--- a/changelog.d/11359.misc
+++ /dev/null
@@ -1 +0,0 @@
-Require all files in synapse/ and tests/ to pass mypy unless specifically excluded.
diff --git a/changelog.d/11361.feature b/changelog.d/11361.feature
deleted file mode 100644
index 24c9244887..0000000000
--- a/changelog.d/11361.feature
+++ /dev/null
@@ -1 +0,0 @@
-Update the JWT login type to support custom a `sub` claim.
diff --git a/changelog.d/11368.misc b/changelog.d/11368.misc
deleted file mode 100644
index d623935865..0000000000
--- a/changelog.d/11368.misc
+++ /dev/null
@@ -1 +0,0 @@
-Fix running `scripts-dev/complement.sh`, which was broken in v1.47.0rc1.
diff --git a/changelog.d/11369.misc b/changelog.d/11369.misc
deleted file mode 100644
index 3c1dad544b..0000000000
--- a/changelog.d/11369.misc
+++ /dev/null
@@ -1 +0,0 @@
-Rename `get_access_token_for_user_id` to `create_access_token_for_user_id` to better reflect what it does.
diff --git a/changelog.d/11370.misc b/changelog.d/11370.misc
deleted file mode 100644
index 13d9f36bf3..0000000000
--- a/changelog.d/11370.misc
+++ /dev/null
@@ -1 +0,0 @@
-Rename `get_refresh_token_for_user_id` to `create_refresh_token_for_user_id` to better describe what it does.
diff --git a/changelog.d/11371.feature b/changelog.d/11371.feature
deleted file mode 100644
index 8e9ca2d633..0000000000
--- a/changelog.d/11371.feature
+++ /dev/null
@@ -1 +0,0 @@
-Add support for the `/_matrix/media/v3` APIs from Matrix v1.1.
\ No newline at end of file
diff --git a/changelog.d/11376.bugfix b/changelog.d/11376.bugfix
deleted file mode 100644
index 639e48b59b..0000000000
--- a/changelog.d/11376.bugfix
+++ /dev/null
@@ -1 +0,0 @@
-Fix a long-standing bug where all requests that read events from the database could get stuck as a result of losing the database connection, for real this time. Also fix a race condition introduced in the previous insufficient fix in 1.47.0.
diff --git a/changelog.d/11377.bugfix b/changelog.d/11377.bugfix
deleted file mode 100644
index 9831fb7bbe..0000000000
--- a/changelog.d/11377.bugfix
+++ /dev/null
@@ -1 +0,0 @@
-Fix a bug introduced in v1.45.0 where the `read_templates` method of the module API would error.
diff --git a/changelog.d/11377.misc b/changelog.d/11377.misc
deleted file mode 100644
index 3dac625576..0000000000
--- a/changelog.d/11377.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type hints to configuration classes.
diff --git a/changelog.d/11379.bugfix b/changelog.d/11379.bugfix
deleted file mode 100644
index a49d4eb776..0000000000
--- a/changelog.d/11379.bugfix
+++ /dev/null
@@ -1 +0,0 @@
-Fix an issue introduced in v1.47.0 which prevented servers re-joining rooms they had previously left, if their signing keys were replaced.
diff --git a/changelog.d/11380.misc b/changelog.d/11380.misc
deleted file mode 100644
index 703e80d14f..0000000000
--- a/changelog.d/11380.misc
+++ /dev/null
@@ -1 +0,0 @@
-Publish a `develop` image to dockerhub.
diff --git a/changelog.d/11381.doc b/changelog.d/11381.doc
deleted file mode 100644
index f99a432418..0000000000
--- a/changelog.d/11381.doc
+++ /dev/null
@@ -1 +0,0 @@
-Fix missing quotes for wildcard domains in `federation_certificate_verification_whitelist`.
diff --git a/changelog.d/11382.misc b/changelog.d/11382.misc
deleted file mode 100644
index d812ef309e..0000000000
--- a/changelog.d/11382.misc
+++ /dev/null
@@ -1 +0,0 @@
-Keep fallback key marked as used if it's re-uploaded.
diff --git a/changelog.d/11386.misc b/changelog.d/11386.misc
deleted file mode 100644
index 3178d53f05..0000000000
--- a/changelog.d/11386.misc
+++ /dev/null
@@ -1 +0,0 @@
-Use `auto_attribs` on the `attrs` class `RefreshTokenLookupResult`.
diff --git a/changelog.d/11388.misc b/changelog.d/11388.misc
deleted file mode 100644
index 7ce7ad0498..0000000000
--- a/changelog.d/11388.misc
+++ /dev/null
@@ -1 +0,0 @@
-Rename unstable `access_token_lifetime` configuration option to `refreshable_access_token_lifetime` to make it clear it only concerns refreshable access tokens.
\ No newline at end of file
diff --git a/changelog.d/11389.misc b/changelog.d/11389.misc
deleted file mode 100644
index 33672bb075..0000000000
--- a/changelog.d/11389.misc
+++ /dev/null
@@ -1 +0,0 @@
-Do not run the broken MSC2716 tests when running `scripts-dev/complement.sh`.
diff --git a/changelog.d/11391.feature b/changelog.d/11391.feature
deleted file mode 100644
index 4f696285a7..0000000000
--- a/changelog.d/11391.feature
+++ /dev/null
@@ -1 +0,0 @@
-Store and allow querying of arbitrary event relations.
diff --git a/changelog.d/11392.bugfix b/changelog.d/11392.bugfix
deleted file mode 100644
index fb15800327..0000000000
--- a/changelog.d/11392.bugfix
+++ /dev/null
@@ -1 +0,0 @@
-Fix a bug introduced in v1.13.0 where creating and publishing a room could cause errors if `room_list_publication_rules` is configured.
diff --git a/changelog.d/11393.misc b/changelog.d/11393.misc
deleted file mode 100644
index 6bf47ec2e0..0000000000
--- a/changelog.d/11393.misc
+++ /dev/null
@@ -1 +0,0 @@
-Remove dead code from supporting ACME.
diff --git a/changelog.d/11395.removal b/changelog.d/11395.removal
deleted file mode 100644
index 6c1fd560ad..0000000000
--- a/changelog.d/11395.removal
+++ /dev/null
@@ -1 +0,0 @@
-Remove deprecated `trust_identity_server_for_password_resets` configuration flag.
\ No newline at end of file
diff --git a/changelog.d/11408.misc b/changelog.d/11408.misc
deleted file mode 100644
index 55ed064672..0000000000
--- a/changelog.d/11408.misc
+++ /dev/null
@@ -1 +0,0 @@
-Refactor including the bundled relations when serializing an event.
diff --git a/changelog.d/11411.misc b/changelog.d/11411.misc
deleted file mode 100644
index 86594a332d..0000000000
--- a/changelog.d/11411.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type hints to storage classes.
diff --git a/changelog.d/11413.bugfix b/changelog.d/11413.bugfix
deleted file mode 100644
index 44111d8152..0000000000
--- a/changelog.d/11413.bugfix
+++ /dev/null
@@ -1 +0,0 @@
-The `/send_join` response now includes the stable `event` field instead of the unstable field from [MSC3083](https://github.com/matrix-org/matrix-doc/pull/3083).
diff --git a/changelog.d/11415.doc b/changelog.d/11415.doc
deleted file mode 100644
index e405531867..0000000000
--- a/changelog.d/11415.doc
+++ /dev/null
@@ -1 +0,0 @@
-Update the media repository documentation.
diff --git a/changelog.d/11421.bugfix b/changelog.d/11421.bugfix
deleted file mode 100644
index 28ac65ea7c..0000000000
--- a/changelog.d/11421.bugfix
+++ /dev/null
@@ -1 +0,0 @@
-Improve performance of various background database schema updates.
diff --git a/changelog.d/11422.bugfix b/changelog.d/11422.bugfix
deleted file mode 100644
index 28ac65ea7c..0000000000
--- a/changelog.d/11422.bugfix
+++ /dev/null
@@ -1 +0,0 @@
-Improve performance of various background database schema updates.
diff --git a/changelog.d/11425.feature b/changelog.d/11425.feature
deleted file mode 100644
index 806dd5d91c..0000000000
--- a/changelog.d/11425.feature
+++ /dev/null
@@ -1 +0,0 @@
-Support expiry of refresh tokens and expiry of the overall session when refresh tokens are in use.
\ No newline at end of file
diff --git a/changelog.d/11428.misc b/changelog.d/11428.misc
deleted file mode 100644
index 2f814fa5fb..0000000000
--- a/changelog.d/11428.misc
+++ /dev/null
@@ -1 +0,0 @@
-Add type annotations to some of the configuration surrounding refresh tokens.
\ No newline at end of file
diff --git a/changelog.d/11429.docker b/changelog.d/11429.docker
deleted file mode 100644
index 81db719ed6..0000000000
--- a/changelog.d/11429.docker
+++ /dev/null
@@ -1 +0,0 @@
-Update `Dockerfile-workers` to healthcheck all workers in container.
diff --git a/changelog.d/11430.misc b/changelog.d/11430.misc
deleted file mode 100644
index 28f06f4c4e..0000000000
--- a/changelog.d/11430.misc
+++ /dev/null
@@ -1 +0,0 @@
-Update [MSC2918 refresh token](https://github.com/matrix-org/matrix-doc/blob/main/proposals/2918-refreshtokens.md#msc2918-refresh-tokens) support to confirm with the latest revision: accept the `refresh_tokens` parameter in the request body rather than in the URL parameters.
\ No newline at end of file
diff --git a/changelog.d/11439.bugfix b/changelog.d/11439.bugfix
deleted file mode 100644
index fc6bc82b36..0000000000
--- a/changelog.d/11439.bugfix
+++ /dev/null
@@ -1 +0,0 @@
-Fix a bug introduced in 1.47.0 where `send_join` could fail due to an outdated `ijson` version.
diff --git a/changelog.d/11440.bugfix b/changelog.d/11440.bugfix
deleted file mode 100644
index 02ce2e428f..0000000000
--- a/changelog.d/11440.bugfix
+++ /dev/null
@@ -1 +0,0 @@
-Fix a bug introduced in Synapse 1.36 which could cause problems fetching event-signing keys from trusted key servers.
diff --git a/changelog.d/11441.bugfix b/changelog.d/11441.bugfix
deleted file mode 100644
index 1baef41d70..0000000000
--- a/changelog.d/11441.bugfix
+++ /dev/null
@@ -1 +0,0 @@
-Fix a bug introduced in 1.47.0 where `send_join` could fail due to an outdated `ijson` version.
\ No newline at end of file
diff --git a/debian/changelog b/debian/changelog
index 35c9063388..acc9f6049e 100644
--- a/debian/changelog
+++ b/debian/changelog
@@ -1,3 +1,21 @@
+matrix-synapse-py3 (1.49.0~rc1) stable; urgency=medium
+
+ * New synapse release 1.49.0~rc1.
+
+ -- Synapse Packaging team <packages@matrix.org> Tue, 07 Dec 2021 13:52:21 +0000
+
+matrix-synapse-py3 (1.48.0) stable; urgency=medium
+
+ * New synapse release 1.48.0.
+
+ -- Synapse Packaging team <packages@matrix.org> Tue, 30 Nov 2021 11:24:15 +0000
+
+matrix-synapse-py3 (1.48.0~rc1) stable; urgency=medium
+
+ * New synapse release 1.48.0~rc1.
+
+ -- Synapse Packaging team <packages@matrix.org> Thu, 25 Nov 2021 15:56:03 +0000
+
matrix-synapse-py3 (1.47.1) stable; urgency=medium
* New synapse release 1.47.1.
diff --git a/docs/SUMMARY.md b/docs/SUMMARY.md
index e71df89797..06d81c6663 100644
--- a/docs/SUMMARY.md
+++ b/docs/SUMMARY.md
@@ -44,6 +44,7 @@
- [Presence router callbacks](modules/presence_router_callbacks.md)
- [Account validity callbacks](modules/account_validity_callbacks.md)
- [Password auth provider callbacks](modules/password_auth_provider_callbacks.md)
+ - [Background update controller callbacks](modules/background_update_controller_callbacks.md)
- [Porting a legacy module to the new interface](modules/porting_legacy_module.md)
- [Workers](workers.md)
- [Using `synctl` with Workers](synctl_workers.md)
@@ -65,9 +66,15 @@
- [Statistics](admin_api/statistics.md)
- [Users](admin_api/user_admin_api.md)
- [Server Version](admin_api/version_api.md)
+ - [Federation](usage/administration/admin_api/federation.md)
- [Manhole](manhole.md)
- [Monitoring](metrics-howto.md)
+ - [Understanding Synapse Through Grafana Graphs](usage/administration/understanding_synapse_through_grafana_graphs.md)
+ - [Useful SQL for Admins](usage/administration/useful_sql_for_admins.md)
+ - [Database Maintenance Tools](usage/administration/database_maintenance_tools.md)
+ - [State Groups](usage/administration/state_groups.md)
- [Request log format](usage/administration/request_log.md)
+ - [Admin FAQ](usage/administration/admin_faq.md)
- [Scripts]()
# Development
@@ -95,3 +102,4 @@
# Other
- [Dependency Deprecation Policy](deprecation_policy.md)
+ - [Running Synapse on a Single-Board Computer](other/running_synapse_on_single_board_computers.md)
diff --git a/docs/development/room-dag-concepts.md b/docs/development/room-dag-concepts.md
index 5eed72bec6..cbc7cf2949 100644
--- a/docs/development/room-dag-concepts.md
+++ b/docs/development/room-dag-concepts.md
@@ -38,16 +38,15 @@ Most-recent-in-time events in the DAG which are not referenced by any other even
The forward extremities of a room are used as the `prev_events` when the next event is sent.
-## Backwards extremity
+## Backward extremity
The current marker of where we have backfilled up to and will generally be the
-oldest-in-time events we know of in the DAG.
+`prev_events` of the oldest-in-time events we have in the DAG. This gives a starting point when
+backfilling history.
-This is an event where we haven't fetched all of the `prev_events` for.
-
-Once we have fetched all of its `prev_events`, it's unmarked as a backwards
-extremity (although we may have formed new backwards extremities from the prev
-events during the backfilling process).
+When we persist a non-outlier event, we clear it as a backward extremity and set
+all of its `prev_events` as the new backward extremities if they aren't already
+persisted in the `events` table.
## Outliers
@@ -56,8 +55,7 @@ We mark an event as an `outlier` when we haven't figured out the state for the
room at that point in the DAG yet.
We won't *necessarily* have the `prev_events` of an `outlier` in the database,
-but it's entirely possible that we *might*. The status of whether we have all of
-the `prev_events` is marked as a [backwards extremity](#backwards-extremity).
+but it's entirely possible that we *might*.
For example, when we fetch the event auth chain or state for a given event, we
mark all of those claimed auth events as outliers because we haven't done the
diff --git a/docs/openid.md b/docs/openid.md
index c74e8bda60..ff9de9d5b8 100644
--- a/docs/openid.md
+++ b/docs/openid.md
@@ -83,7 +83,7 @@ oidc_providers:
### Dex
-[Dex][dex-idp] is a simple, open-source, certified OpenID Connect Provider.
+[Dex][dex-idp] is a simple, open-source OpenID Connect Provider.
Although it is designed to help building a full-blown provider with an
external database, it can be configured with static passwords in a config file.
@@ -523,7 +523,7 @@ The synapse config will look like this:
email_template: "{{ user.email }}"
```
-## Django OAuth Toolkit
+### Django OAuth Toolkit
[django-oauth-toolkit](https://github.com/jazzband/django-oauth-toolkit) is a
Django application providing out of the box all the endpoints, data and logic
diff --git a/docs/other/running_synapse_on_single_board_computers.md b/docs/other/running_synapse_on_single_board_computers.md
new file mode 100644
index 0000000000..ea14afa8b2
--- /dev/null
+++ b/docs/other/running_synapse_on_single_board_computers.md
@@ -0,0 +1,74 @@
+## Summary of performance impact of running on resource constrained devices such as SBCs
+
+I've been running my homeserver on a cubietruck at home now for some time and am often replying to statements like "you need loads of ram to join large rooms" with "it works fine for me". I thought it might be useful to curate a summary of the issues you're likely to run into to help as a scaling-down guide, maybe highlight these for development work or end up as documentation. It seems that once you get up to about 4x1.5GHz arm64 4GiB these issues are no longer a problem.
+
+- **Platform**: 2x1GHz armhf 2GiB ram [Single-board computers](https://wiki.debian.org/CheapServerBoxHardware), SSD, postgres.
+
+### Presence
+
+This is the main reason people have a poor matrix experience on resource constrained homeservers. Element web will frequently be saying the server is offline while the python process will be pegged at 100% cpu. This feature is used to tell when other users are active (have a client app in the foreground) and therefore more likely to respond, but requires a lot of network activity to maintain even when nobody is talking in a room.
+
+
+
+While synapse does have some performance issues with presence [#3971](https://github.com/matrix-org/synapse/issues/3971), the fundamental problem is that this is an easy feature to implement for a centralised service at nearly no overhead, but federation makes it combinatorial [#8055](https://github.com/matrix-org/synapse/issues/8055). There is also a client-side config option which disables the UI and idle tracking [enable_presence_by_hs_url] to blacklist the largest instances but I didn't notice much difference, so I recommend disabling the feature entirely at the server level as well.
+
+[enable_presence_by_hs_url]: https://github.com/vector-im/element-web/blob/v1.7.8/config.sample.json#L45
+
+### Joining
+
+Joining a "large", federated room will initially fail with the below message in Element web, but waiting a while (10-60mins) and trying again will succeed without any issue. What counts as "large" is not message history, user count, connections to homeservers or even a simple count of the state events, it is instead how long the state resolution algorithm takes. However, each of those numbers are reasonable proxies, so we can use them as estimates since user count is one of the few things you see before joining.
+
+
+
+This is [#1211](https://github.com/matrix-org/synapse/issues/1211) and will also hopefully be mitigated by peeking [matrix-org/matrix-doc#2753](https://github.com/matrix-org/matrix-doc/pull/2753) so at least you don't need to wait for a join to complete before finding out if it's the kind of room you want. Note that you should first disable presence, otherwise it'll just make the situation worse [#3120](https://github.com/matrix-org/synapse/issues/3120). There is a lot of database interaction too, so make sure you've [migrated your data](../postgres.md) from the default sqlite to postgresql. Personally, I recommend patience - once the initial join is complete there's rarely any issues with actually interacting with the room, but if you like you can just block "large" rooms entirely.
+
+### Sessions
+
+Anything that requires modifying the device list [#7721](https://github.com/matrix-org/synapse/issues/7721) will take a while to propagate, again taking the client "Offline" until it's complete. This includes signing in and out, editing the public name and verifying e2ee. The main mitigation I recommend is to keep long-running sessions open e.g. by using Firefox SSB "Use this site in App mode" or Chromium PWA "Install Element".
+
+### Recommended configuration
+
+Put the below in a new file at /etc/matrix-synapse/conf.d/sbc.yaml to override the defaults in homeserver.yaml.
+
+```
+# Set to false to disable presence tracking on this homeserver.
+use_presence: false
+
+# When this is enabled, the room "complexity" will be checked before a user
+# joins a new remote room. If it is above the complexity limit, the server will
+# disallow joining, or will instantly leave.
+limit_remote_rooms:
+ # Uncomment to enable room complexity checking.
+ #enabled: true
+ complexity: 3.0
+
+# Database configuration
+database:
+ name: psycopg2
+ args:
+ user: matrix-synapse
+ # Generate a long, secure one with a password manager
+ password: hunter2
+ database: matrix-synapse
+ host: localhost
+ cp_min: 5
+ cp_max: 10
+```
+
+Currently the complexity is measured by [current_state_events / 500](https://github.com/matrix-org/synapse/blob/v1.20.1/synapse/storage/databases/main/events_worker.py#L986). You can find join times and your most complex rooms like this:
+
+```
+admin@homeserver:~$ zgrep '/client/r0/join/' /var/log/matrix-synapse/homeserver.log* | awk '{print $18, $25}' | sort --human-numeric-sort
+29.922sec/-0.002sec /_matrix/client/r0/join/%23debian-fasttrack%3Apoddery.com
+182.088sec/0.003sec /_matrix/client/r0/join/%23decentralizedweb-general%3Amatrix.org
+911.625sec/-570.847sec /_matrix/client/r0/join/%23synapse%3Amatrix.org
+
+admin@homeserver:~$ sudo --user postgres psql matrix-synapse --command 'select canonical_alias, joined_members, current_state_events from room_stats_state natural join room_stats_current where canonical_alias is not null order by current_state_events desc fetch first 5 rows only'
+ canonical_alias | joined_members | current_state_events
+-------------------------------+----------------+----------------------
+ #_oftc_#debian:matrix.org | 871 | 52355
+ #matrix:matrix.org | 6379 | 10684
+ #irc:matrix.org | 461 | 3751
+ #decentralizedweb-general:matrix.org | 997 | 1509
+ #whatsapp:maunium.net | 554 | 854
+```
\ No newline at end of file
diff --git a/docs/postgres.md b/docs/postgres.md
index 083b0aaff0..e4861c1f12 100644
--- a/docs/postgres.md
+++ b/docs/postgres.md
@@ -118,6 +118,9 @@ performance:
Note that the appropriate values for those fields depend on the amount
of free memory the database host has available.
+Additionally, admins of large deployments might want to consider using huge pages
+to help manage memory, especially when using large values of `shared_buffers`. You
+can read more about that [here](https://www.postgresql.org/docs/10/kernel-resources.html#LINUX-HUGE-PAGES).
## Porting from SQLite
diff --git a/docs/sample_config.yaml b/docs/sample_config.yaml
index ae476d19ac..6696ed5d1e 100644
--- a/docs/sample_config.yaml
+++ b/docs/sample_config.yaml
@@ -1209,6 +1209,44 @@ oembed:
#
#session_lifetime: 24h
+# Time that an access token remains valid for, if the session is
+# using refresh tokens.
+# For more information about refresh tokens, please see the manual.
+# Note that this only applies to clients which advertise support for
+# refresh tokens.
+#
+# Note also that this is calculated at login time and refresh time:
+# changes are not applied to existing sessions until they are refreshed.
+#
+# By default, this is 5 minutes.
+#
+#refreshable_access_token_lifetime: 5m
+
+# Time that a refresh token remains valid for (provided that it is not
+# exchanged for another one first).
+# This option can be used to automatically log-out inactive sessions.
+# Please see the manual for more information.
+#
+# Note also that this is calculated at login time and refresh time:
+# changes are not applied to existing sessions until they are refreshed.
+#
+# By default, this is infinite.
+#
+#refresh_token_lifetime: 24h
+
+# Time that an access token remains valid for, if the session is NOT
+# using refresh tokens.
+# Please note that not all clients support refresh tokens, so setting
+# this to a short value may be inconvenient for some users who will
+# then be logged out frequently.
+#
+# Note also that this is calculated at login time: changes are not applied
+# retrospectively to existing sessions for users that have already logged in.
+#
+# By default, this is infinite.
+#
+#nonrefreshable_access_token_lifetime: 24h
+
# The user must provide all of the below types of 3PID when registering.
#
#registrations_require_3pid:
diff --git a/docs/templates.md b/docs/templates.md
index a240f58b54..2b66e9d862 100644
--- a/docs/templates.md
+++ b/docs/templates.md
@@ -71,7 +71,12 @@ Below are the templates Synapse will look for when generating the content of an
* `sender_avatar_url`: the avatar URL (as a `mxc://` URL) for the event's
sender
* `sender_hash`: a hash of the user ID of the sender
+ * `msgtype`: the type of the message
+ * `body_text_html`: html representation of the message
+ * `body_text_plain`: plaintext representation of the message
+ * `image_url`: mxc url of an image, when "msgtype" is "m.image"
* `link`: a `matrix.to` link to the room
+ * `avator_url`: url to the room's avator
* `reason`: information on the event that triggered the email to be sent. It's an
object with the following attributes:
* `room_id`: the ID of the room the event was sent in
diff --git a/docs/usage/administration/admin_api/federation.md b/docs/usage/administration/admin_api/federation.md
new file mode 100644
index 0000000000..8f9535f57b
--- /dev/null
+++ b/docs/usage/administration/admin_api/federation.md
@@ -0,0 +1,114 @@
+# Federation API
+
+This API allows a server administrator to manage Synapse's federation with other homeservers.
+
+Note: This API is new, experimental and "subject to change".
+
+## List of destinations
+
+This API gets the current destination retry timing info for all remote servers.
+
+The list contains all the servers with which the server federates,
+regardless of whether an error occurred or not.
+If an error occurs, it may take up to 20 minutes for the error to be displayed here,
+as a complete retry must have failed.
+
+The API is:
+
+A standard request with no filtering:
+
+```
+GET /_synapse/admin/v1/federation/destinations
+```
+
+A response body like the following is returned:
+
+```json
+{
+ "destinations":[
+ {
+ "destination": "matrix.org",
+ "retry_last_ts": 1557332397936,
+ "retry_interval": 3000000,
+ "failure_ts": 1557329397936,
+ "last_successful_stream_ordering": null
+ }
+ ],
+ "total": 1
+}
+```
+
+To paginate, check for `next_token` and if present, call the endpoint again
+with `from` set to the value of `next_token`. This will return a new page.
+
+If the endpoint does not return a `next_token` then there are no more destinations
+to paginate through.
+
+**Parameters**
+
+The following query parameters are available:
+
+- `from` - Offset in the returned list. Defaults to `0`.
+- `limit` - Maximum amount of destinations to return. Defaults to `100`.
+- `order_by` - The method in which to sort the returned list of destinations.
+ Valid values are:
+ - `destination` - Destinations are ordered alphabetically by remote server name.
+ This is the default.
+ - `retry_last_ts` - Destinations are ordered by time of last retry attempt in ms.
+ - `retry_interval` - Destinations are ordered by how long until next retry in ms.
+ - `failure_ts` - Destinations are ordered by when the server started failing in ms.
+ - `last_successful_stream_ordering` - Destinations are ordered by the stream ordering
+ of the most recent successfully-sent PDU.
+- `dir` - Direction of room order. Either `f` for forwards or `b` for backwards. Setting
+ this value to `b` will reverse the above sort order. Defaults to `f`.
+
+*Caution:* The database only has an index on the column `destination`.
+This means that if a different sort order is used,
+this can cause a large load on the database, especially for large environments.
+
+**Response**
+
+The following fields are returned in the JSON response body:
+
+- `destinations` - An array of objects, each containing information about a destination.
+ Destination objects contain the following fields:
+ - `destination` - string - Name of the remote server to federate.
+ - `retry_last_ts` - integer - The last time Synapse tried and failed to reach the
+ remote server, in ms. This is `0` if the last attempt to communicate with the
+ remote server was successful.
+ - `retry_interval` - integer - How long since the last time Synapse tried to reach
+ the remote server before trying again, in ms. This is `0` if no further retrying occuring.
+ - `failure_ts` - nullable integer - The first time Synapse tried and failed to reach the
+ remote server, in ms. This is `null` if communication with the remote server has never failed.
+ - `last_successful_stream_ordering` - nullable integer - The stream ordering of the most
+ recent successfully-sent [PDU](understanding_synapse_through_grafana_graphs.md#federation)
+ to this destination, or `null` if this information has not been tracked yet.
+- `next_token`: string representing a positive integer - Indication for pagination. See above.
+- `total` - integer - Total number of destinations.
+
+# Destination Details API
+
+This API gets the retry timing info for a specific remote server.
+
+The API is:
+
+```
+GET /_synapse/admin/v1/federation/destinations/<destination>
+```
+
+A response body like the following is returned:
+
+```json
+{
+ "destination": "matrix.org",
+ "retry_last_ts": 1557332397936,
+ "retry_interval": 3000000,
+ "failure_ts": 1557329397936,
+ "last_successful_stream_ordering": null
+}
+```
+
+**Response**
+
+The response fields are the same like in the `destinations` array in
+[List of destinations](#list-of-destinations) response.
diff --git a/docs/usage/administration/admin_faq.md b/docs/usage/administration/admin_faq.md
new file mode 100644
index 0000000000..3dcad4bbef
--- /dev/null
+++ b/docs/usage/administration/admin_faq.md
@@ -0,0 +1,103 @@
+## Admin FAQ
+
+How do I become a server admin?
+---
+If your server already has an admin account you should use the user admin API to promote other accounts to become admins. See [User Admin API](../../admin_api/user_admin_api.md#Change-whether-a-user-is-a-server-administrator-or-not)
+
+If you don't have any admin accounts yet you won't be able to use the admin API so you'll have to edit the database manually. Manually editing the database is generally not recommended so once you have an admin account, use the admin APIs to make further changes.
+
+```sql
+UPDATE users SET admin = 1 WHERE name = '@foo:bar.com';
+```
+What servers are my server talking to?
+---
+Run this sql query on your db:
+```sql
+SELECT * FROM destinations;
+```
+
+What servers are currently participating in this room?
+---
+Run this sql query on your db:
+```sql
+SELECT DISTINCT split_part(state_key, ':', 2)
+ FROM current_state_events AS c
+ INNER JOIN room_memberships AS m USING (room_id, event_id)
+ WHERE room_id = '!cURbafjkfsMDVwdRDQ:matrix.org' AND membership = 'join';
+```
+
+What users are registered on my server?
+---
+```sql
+SELECT NAME from users;
+```
+
+Manually resetting passwords:
+---
+See https://github.com/matrix-org/synapse/blob/master/README.rst#password-reset
+
+I have a problem with my server. Can I just delete my database and start again?
+---
+Deleting your database is unlikely to make anything better.
+
+It's easy to make the mistake of thinking that you can start again from a clean slate by dropping your database, but things don't work like that in a federated network: lots of other servers have information about your server.
+
+For example: other servers might think that you are in a room, your server will think that you are not, and you'll probably be unable to interact with that room in a sensible way ever again.
+
+In general, there are better solutions to any problem than dropping the database. Come and seek help in https://matrix.to/#/#synapse:matrix.org.
+
+There are two exceptions when it might be sensible to delete your database and start again:
+* You have *never* joined any rooms which are federated with other servers. For instance, a local deployment which the outside world can't talk to.
+* You are changing the `server_name` in the homeserver configuration. In effect this makes your server a completely new one from the point of view of the network, so in this case it makes sense to start with a clean database.
+(In both cases you probably also want to clear out the media_store.)
+
+I've stuffed up access to my room, how can I delete it to free up the alias?
+---
+Using the following curl command:
+```
+curl -H 'Authorization: Bearer <access-token>' -X DELETE https://matrix.org/_matrix/client/r0/directory/room/<room-alias>
+```
+`<access-token>` - can be obtained in riot by looking in the riot settings, down the bottom is:
+Access Token:\<click to reveal\>
+
+`<room-alias>` - the room alias, eg. #my_room:matrix.org this possibly needs to be URL encoded also, for example %23my_room%3Amatrix.org
+
+How can I find the lines corresponding to a given HTTP request in my homeserver log?
+---
+
+Synapse tags each log line according to the HTTP request it is processing. When it finishes processing each request, it logs a line containing the words `Processed request: `. For example:
+
+```
+2019-02-14 22:35:08,196 - synapse.access.http.8008 - 302 - INFO - GET-37 - ::1 - 8008 - {@richvdh:localhost} Processed request: 0.173sec/0.001sec (0.002sec, 0.000sec) (0.027sec/0.026sec/2) 687B 200 "GET /_matrix/client/r0/sync HTTP/1.1" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.3497.100 Safari/537.36" [0 dbevts]"
+```
+
+Here we can see that the request has been tagged with `GET-37`. (The tag depends on the method of the HTTP request, so might start with `GET-`, `PUT-`, `POST-`, `OPTIONS-` or `DELETE-`.) So to find all lines corresponding to this request, we can do:
+
+```
+grep 'GET-37' homeserver.log
+```
+
+If you want to paste that output into a github issue or matrix room, please remember to surround it with triple-backticks (```) to make it legible (see https://help.github.com/en/articles/basic-writing-and-formatting-syntax#quoting-code).
+
+
+What do all those fields in the 'Processed' line mean?
+---
+See [Request log format](request_log.md).
+
+
+What are the biggest rooms on my server?
+---
+
+```sql
+SELECT s.canonical_alias, g.room_id, count(*) AS num_rows
+FROM
+ state_groups_state AS g,
+ room_stats_state AS s
+WHERE g.room_id = s.room_id
+GROUP BY s.canonical_alias, g.room_id
+ORDER BY num_rows desc
+LIMIT 10;
+```
+
+You can also use the [List Room API](../../admin_api/rooms.md#list-room-api)
+and `order_by` `state_events`.
diff --git a/docs/usage/administration/database_maintenance_tools.md b/docs/usage/administration/database_maintenance_tools.md
new file mode 100644
index 0000000000..92b805d413
--- /dev/null
+++ b/docs/usage/administration/database_maintenance_tools.md
@@ -0,0 +1,18 @@
+This blog post by Victor Berger explains how to use many of the tools listed on this page: https://levans.fr/shrink-synapse-database.html
+
+# List of useful tools and scripts for maintenance Synapse database:
+
+## [Purge Remote Media API](../../admin_api/media_admin_api.md#purge-remote-media-api)
+The purge remote media API allows server admins to purge old cached remote media.
+
+## [Purge Local Media API](../../admin_api/media_admin_api.md#delete-local-media)
+This API deletes the *local* media from the disk of your own server.
+
+## [Purge History API](../../admin_api/purge_history_api.md)
+The purge history API allows server admins to purge historic events from their database, reclaiming disk space.
+
+## [synapse-compress-state](https://github.com/matrix-org/rust-synapse-compress-state)
+Tool for compressing (deduplicating) `state_groups_state` table.
+
+## [SQL for analyzing Synapse PostgreSQL database stats](useful_sql_for_admins.md)
+Some easy SQL that reports useful stats about your Synapse database.
\ No newline at end of file
diff --git a/docs/usage/administration/state_groups.md b/docs/usage/administration/state_groups.md
new file mode 100644
index 0000000000..f1dee7accf
--- /dev/null
+++ b/docs/usage/administration/state_groups.md
@@ -0,0 +1,25 @@
+# How do State Groups work?
+
+As a general rule, I encourage people who want to understand the deepest darkest secrets of the database schema to drop by #synapse-dev:matrix.org and ask questions.
+
+However, one question that comes up frequently is that of how "state groups" work, and why the `state_groups_state` table gets so big, so here's an attempt to answer that question.
+
+We need to be able to relatively quickly calculate the state of a room at any point in that room's history. In other words, we need to know the state of the room at each event in that room. This is done as follows:
+
+A sequence of events where the state is the same are grouped together into a `state_group`; the mapping is recorded in `event_to_state_groups`. (Technically speaking, since a state event usually changes the state in the room, we are recording the state of the room *after* the given event id: which is to say, to a handwavey simplification, the first event in a state group is normally a state event, and others in the same state group are normally non-state-events.)
+
+`state_groups` records, for each state group, the id of the room that we're looking at, and also the id of the first event in that group. (I'm not sure if that event id is used much in practice.)
+
+Now, if we stored all the room state for each `state_group`, that would be a huge amount of data. Instead, for each state group, we normally store the difference between the state in that group and some other state group, and only occasionally (every 100 state changes or so) record the full state.
+
+So, most state groups have an entry in `state_group_edges` (don't ask me why it's not a column in `state_groups`) which records the previous state group in the room, and `state_groups_state` records the differences in state since that previous state group.
+
+A full state group just records the event id for each piece of state in the room at that point.
+
+## Known bugs with state groups
+
+There are various reasons that we can end up creating many more state groups than we need: see https://github.com/matrix-org/synapse/issues/3364 for more details.
+
+## Compression tool
+
+There is a tool at https://github.com/matrix-org/rust-synapse-compress-state which can compress the `state_groups_state` on a room by-room basis (essentially, it reduces the number of "full" state groups). This can result in dramatic reductions of the storage used.
\ No newline at end of file
diff --git a/docs/usage/administration/understanding_synapse_through_grafana_graphs.md b/docs/usage/administration/understanding_synapse_through_grafana_graphs.md
new file mode 100644
index 0000000000..c365cc3923
--- /dev/null
+++ b/docs/usage/administration/understanding_synapse_through_grafana_graphs.md
@@ -0,0 +1,84 @@
+## Understanding Synapse through Grafana graphs
+
+It is possible to monitor much of the internal state of Synapse using [Prometheus](https://prometheus.io)
+metrics and [Grafana](https://grafana.com/).
+A guide for configuring Synapse to provide metrics is available [here](../../metrics-howto.md)
+and information on setting up Grafana is [here](https://github.com/matrix-org/synapse/tree/master/contrib/grafana).
+In this setup, Prometheus will periodically scrape the information Synapse provides and
+store a record of it over time. Grafana is then used as an interface to query and
+present this information through a series of pretty graphs.
+
+Once you have grafana set up, and assuming you're using [our grafana dashboard template](https://github.com/matrix-org/synapse/blob/master/contrib/grafana/synapse.json), look for the following graphs when debugging a slow/overloaded Synapse:
+
+## Message Event Send Time
+
+
+
+This, along with the CPU and Memory graphs, is a good way to check the general health of your Synapse instance. It represents how long it takes for a user on your homeserver to send a message.
+
+## Transaction Count and Transaction Duration
+
+
+
+
+
+These graphs show the database transactions that are occurring the most frequently, as well as those are that are taking the most amount of time to execute.
+
+
+
+In the first graph, we can see obvious spikes corresponding to lots of `get_user_by_id` transactions. This would be useful information to figure out which part of the Synapse codebase is potentially creating a heavy load on the system. However, be sure to cross-reference this with Transaction Duration, which states that `get_users_by_id` is actually a very quick database transaction and isn't causing as much load as others, like `persist_events`:
+
+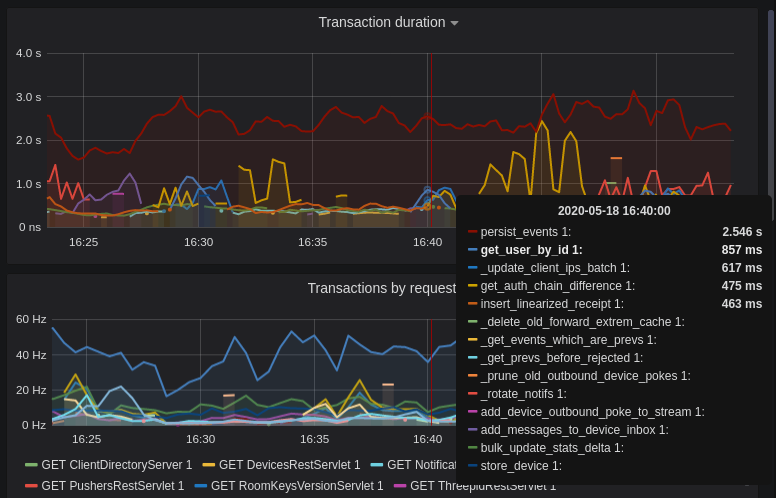
+
+Still, it's probably worth investigating why we're getting users from the database that often, and whether it's possible to reduce the amount of queries we make by adjusting our cache factor(s).
+
+The `persist_events` transaction is responsible for saving new room events to the Synapse database, so can often show a high transaction duration.
+
+## Federation
+
+The charts in the "Federation" section show information about incoming and outgoing federation requests. Federation data can be divided into two basic types:
+
+- PDU (Persistent Data Unit) - room events: messages, state events (join/leave), etc. These are permanently stored in the database.
+- EDU (Ephemeral Data Unit) - other data, which need not be stored permanently, such as read receipts, typing notifications.
+
+The "Outgoing EDUs by type" chart shows the EDUs within outgoing federation requests by type: `m.device_list_update`, `m.direct_to_device`, `m.presence`, `m.receipt`, `m.typing`.
+
+If you see a large number of `m.presence` EDUs and are having trouble with too much CPU load, you can disable `presence` in the Synapse config. See also [#3971](https://github.com/matrix-org/synapse/issues/3971).
+
+## Caches
+
+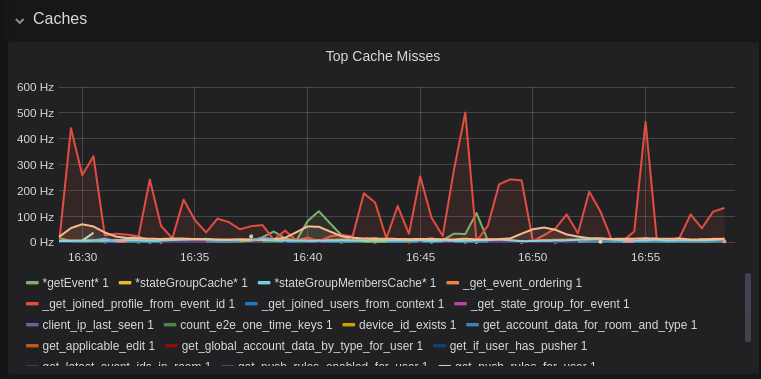
+
+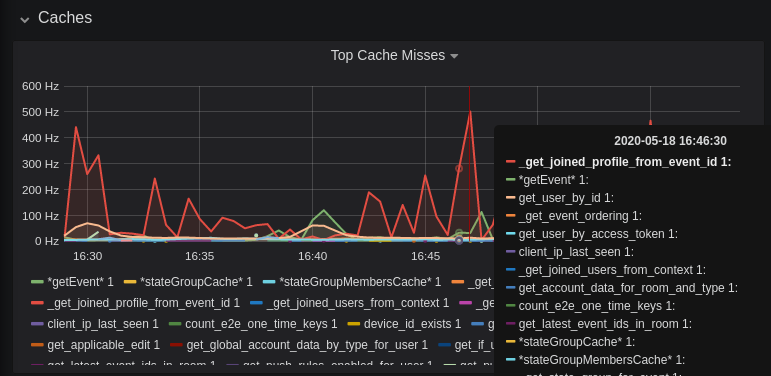
+
+This is quite a useful graph. It shows how many times Synapse attempts to retrieve a piece of data from a cache which the cache did not contain, thus resulting in a call to the database. We can see here that the `_get_joined_profile_from_event_id` cache is being requested a lot, and often the data we're after is not cached.
+
+Cross-referencing this with the Eviction Rate graph, which shows that entries are being evicted from `_get_joined_profile_from_event_id` quite often:
+
+
+
+we should probably consider raising the size of that cache by raising its cache factor (a multiplier value for the size of an individual cache). Information on doing so is available [here](https://github.com/matrix-org/synapse/blob/ee421e524478c1ad8d43741c27379499c2f6135c/docs/sample_config.yaml#L608-L642) (note that the configuration of individual cache factors through the configuration file is available in Synapse v1.14.0+, whereas doing so through environment variables has been supported for a very long time). Note that this will increase Synapse's overall memory usage.
+
+## Forward Extremities
+
+
+
+Forward extremities are the leaf events at the end of a DAG in a room, aka events that have no children. The more that exist in a room, the more [state resolution](https://spec.matrix.org/v1.1/server-server-api/#room-state-resolution) that Synapse needs to perform (hint: it's an expensive operation). While Synapse has code to prevent too many of these existing at one time in a room, bugs can sometimes make them crop up again.
+
+If a room has >10 forward extremities, it's worth checking which room is the culprit and potentially removing them using the SQL queries mentioned in [#1760](https://github.com/matrix-org/synapse/issues/1760).
+
+## Garbage Collection
+
+
+
+Large spikes in garbage collection times (bigger than shown here, I'm talking in the
+multiple seconds range), can cause lots of problems in Synapse performance. It's more an
+indicator of problems, and a symptom of other problems though, so check other graphs for what might be causing it.
+
+## Final Thoughts
+
+If you're still having performance problems with your Synapse instance and you've
+tried everything you can, it may just be a lack of system resources. Consider adding
+more CPU and RAM, and make use of [worker mode](../../workers.md)
+to make use of multiple CPU cores / multiple machines for your homeserver.
+
diff --git a/docs/usage/administration/useful_sql_for_admins.md b/docs/usage/administration/useful_sql_for_admins.md
new file mode 100644
index 0000000000..d4aada3272
--- /dev/null
+++ b/docs/usage/administration/useful_sql_for_admins.md
@@ -0,0 +1,156 @@
+## Some useful SQL queries for Synapse Admins
+
+## Size of full matrix db
+`SELECT pg_size_pretty( pg_database_size( 'matrix' ) );`
+### Result example:
+```
+pg_size_pretty
+----------------
+ 6420 MB
+(1 row)
+```
+## Show top 20 larger rooms by state events count
+```sql
+SELECT r.name, s.room_id, s.current_state_events
+ FROM room_stats_current s
+ LEFT JOIN room_stats_state r USING (room_id)
+ ORDER BY current_state_events DESC
+ LIMIT 20;
+```
+
+and by state_group_events count:
+```sql
+SELECT rss.name, s.room_id, count(s.room_id) FROM state_groups_state s
+LEFT JOIN room_stats_state rss USING (room_id)
+GROUP BY s.room_id, rss.name
+ORDER BY count(s.room_id) DESC
+LIMIT 20;
+```
+plus same, but with join removed for performance reasons:
+```sql
+SELECT s.room_id, count(s.room_id) FROM state_groups_state s
+GROUP BY s.room_id
+ORDER BY count(s.room_id) DESC
+LIMIT 20;
+```
+
+## Show top 20 larger tables by row count
+```sql
+SELECT relname, n_live_tup as rows
+ FROM pg_stat_user_tables
+ ORDER BY n_live_tup DESC
+ LIMIT 20;
+```
+This query is quick, but may be very approximate, for exact number of rows use `SELECT COUNT(*) FROM <table_name>`.
+### Result example:
+```
+state_groups_state - 161687170
+event_auth - 8584785
+event_edges - 6995633
+event_json - 6585916
+event_reference_hashes - 6580990
+events - 6578879
+received_transactions - 5713989
+event_to_state_groups - 4873377
+stream_ordering_to_exterm - 4136285
+current_state_delta_stream - 3770972
+event_search - 3670521
+state_events - 2845082
+room_memberships - 2785854
+cache_invalidation_stream - 2448218
+state_groups - 1255467
+state_group_edges - 1229849
+current_state_events - 1222905
+users_in_public_rooms - 364059
+device_lists_stream - 326903
+user_directory_search - 316433
+```
+
+## Show top 20 rooms by new events count in last 1 day:
+```sql
+SELECT e.room_id, r.name, COUNT(e.event_id) cnt FROM events e
+LEFT JOIN room_stats_state r USING (room_id)
+WHERE e.origin_server_ts >= DATE_PART('epoch', NOW() - INTERVAL '1 day') * 1000 GROUP BY e.room_id, r.name ORDER BY cnt DESC LIMIT 20;
+```
+
+## Show top 20 users on homeserver by sent events (messages) at last month:
+```sql
+SELECT user_id, SUM(total_events)
+ FROM user_stats_historical
+ WHERE TO_TIMESTAMP(end_ts/1000) AT TIME ZONE 'UTC' > date_trunc('day', now() - interval '1 month')
+ GROUP BY user_id
+ ORDER BY SUM(total_events) DESC
+ LIMIT 20;
+```
+
+## Show last 100 messages from needed user, with room names:
+```sql
+SELECT e.room_id, r.name, e.event_id, e.type, e.content, j.json FROM events e
+ LEFT JOIN event_json j USING (room_id)
+ LEFT JOIN room_stats_state r USING (room_id)
+ WHERE sender = '@LOGIN:example.com'
+ AND e.type = 'm.room.message'
+ ORDER BY stream_ordering DESC
+ LIMIT 100;
+```
+
+## Show top 20 larger tables by storage size
+```sql
+SELECT nspname || '.' || relname AS "relation",
+ pg_size_pretty(pg_total_relation_size(C.oid)) AS "total_size"
+ FROM pg_class C
+ LEFT JOIN pg_namespace N ON (N.oid = C.relnamespace)
+ WHERE nspname NOT IN ('pg_catalog', 'information_schema')
+ AND C.relkind <> 'i'
+ AND nspname !~ '^pg_toast'
+ ORDER BY pg_total_relation_size(C.oid) DESC
+ LIMIT 20;
+```
+### Result example:
+```
+public.state_groups_state - 27 GB
+public.event_json - 9855 MB
+public.events - 3675 MB
+public.event_edges - 3404 MB
+public.received_transactions - 2745 MB
+public.event_reference_hashes - 1864 MB
+public.event_auth - 1775 MB
+public.stream_ordering_to_exterm - 1663 MB
+public.event_search - 1370 MB
+public.room_memberships - 1050 MB
+public.event_to_state_groups - 948 MB
+public.current_state_delta_stream - 711 MB
+public.state_events - 611 MB
+public.presence_stream - 530 MB
+public.current_state_events - 525 MB
+public.cache_invalidation_stream - 466 MB
+public.receipts_linearized - 279 MB
+public.state_groups - 160 MB
+public.device_lists_remote_cache - 124 MB
+public.state_group_edges - 122 MB
+```
+
+## Show rooms with names, sorted by events in this rooms
+`echo "select event_json.room_id,room_stats_state.name from event_json,room_stats_state where room_stats_state.room_id=event_json.room_id" | psql synapse | sort | uniq -c | sort -n`
+### Result example:
+```
+ 9459 !FPUfgzXYWTKgIrwKxW:matrix.org | This Week in Matrix
+ 9459 !FPUfgzXYWTKgIrwKxW:matrix.org | This Week in Matrix (TWIM)
+ 17799 !iDIOImbmXxwNngznsa:matrix.org | Linux in Russian
+ 18739 !GnEEPYXUhoaHbkFBNX:matrix.org | Riot Android
+ 23373 !QtykxKocfZaZOUrTwp:matrix.org | Matrix HQ
+ 39504 !gTQfWzbYncrtNrvEkB:matrix.org | ru.[matrix]
+ 43601 !iNmaIQExDMeqdITdHH:matrix.org | Riot
+ 43601 !iNmaIQExDMeqdITdHH:matrix.org | Riot Web/Desktop
+```
+
+## Lookup room state info by list of room_id
+```sql
+SELECT rss.room_id, rss.name, rss.canonical_alias, rss.topic, rss.encryption, rsc.joined_members, rsc.local_users_in_room, rss.join_rules
+FROM room_stats_state rss
+LEFT JOIN room_stats_current rsc USING (room_id)
+WHERE room_id IN (WHERE room_id IN (
+ '!OGEhHVWSdvArJzumhm:matrix.org',
+ '!YTvKGNlinIzlkMTVRl:matrix.org'
+)
+```
\ No newline at end of file
diff --git a/mypy.ini b/mypy.ini
index 51056a8f64..1caf807e85 100644
--- a/mypy.ini
+++ b/mypy.ini
@@ -86,9 +86,6 @@ exclude = (?x)
|tests/push/test_presentable_names.py
|tests/push/test_push_rule_evaluator.py
|tests/rest/admin/test_admin.py
- |tests/rest/admin/test_device.py
- |tests/rest/admin/test_media.py
- |tests/rest/admin/test_server_notice.py
|tests/rest/admin/test_user.py
|tests/rest/admin/test_username_available.py
|tests/rest/client/test_account.py
@@ -111,7 +108,6 @@ exclude = (?x)
|tests/server_notices/test_resource_limits_server_notices.py
|tests/state/test_v2.py
|tests/storage/test_account_data.py
- |tests/storage/test_appservice.py
|tests/storage/test_background_update.py
|tests/storage/test_base.py
|tests/storage/test_client_ips.py
@@ -124,7 +120,6 @@ exclude = (?x)
|tests/test_server.py
|tests/test_state.py
|tests/test_terms_auth.py
- |tests/test_visibility.py
|tests/unittest.py
|tests/util/caches/test_cached_call.py
|tests/util/caches/test_deferred_cache.py
@@ -159,6 +154,12 @@ disallow_untyped_defs = True
[mypy-synapse.events.*]
disallow_untyped_defs = True
+[mypy-synapse.federation.*]
+disallow_untyped_defs = True
+
+[mypy-synapse.federation.transport.client]
+disallow_untyped_defs = False
+
[mypy-synapse.handlers.*]
disallow_untyped_defs = True
diff --git a/scripts-dev/federation_client.py b/scripts-dev/federation_client.py
index 6f76c08fcf..c72e19f61d 100755
--- a/scripts-dev/federation_client.py
+++ b/scripts-dev/federation_client.py
@@ -15,6 +15,25 @@
# See the License for the specific language governing permissions and
# limitations under the License.
+
+"""
+Script for signing and sending federation requests.
+
+Some tips on doing the join dance with this:
+
+ room_id=...
+ user_id=...
+
+ # make_join
+ federation_client.py "/_matrix/federation/v1/make_join/$room_id/$user_id?ver=5" > make_join.json
+
+ # sign
+ jq -M .event make_join.json | sign_json --sign-event-room-version=$(jq -r .room_version make_join.json) -o signed-join.json
+
+ # send_join
+ federation_client.py -X PUT "/_matrix/federation/v2/send_join/$room_id/x" --body $(<signed-join.json) > send_join.json
+"""
+
import argparse
import base64
import json
diff --git a/scripts-dev/sign_json b/scripts-dev/sign_json
index 6ac55ef2f7..9459543106 100755
--- a/scripts-dev/sign_json
+++ b/scripts-dev/sign_json
@@ -22,6 +22,8 @@ import yaml
from signedjson.key import read_signing_keys
from signedjson.sign import sign_json
+from synapse.api.room_versions import KNOWN_ROOM_VERSIONS
+from synapse.crypto.event_signing import add_hashes_and_signatures
from synapse.util import json_encoder
@@ -68,6 +70,16 @@ Example usage:
),
)
+ parser.add_argument(
+ "--sign-event-room-version",
+ type=str,
+ help=(
+ "Sign the JSON as an event for the given room version, rather than raw JSON. "
+ "This means that we will add a 'hashes' object, and redact the event before "
+ "signing."
+ ),
+ )
+
input_args = parser.add_mutually_exclusive_group()
input_args.add_argument("input_data", nargs="?", help="Raw JSON to be signed.")
@@ -116,7 +128,17 @@ Example usage:
print("Input json was not an object", file=sys.stderr)
sys.exit(1)
- sign_json(obj, args.server_name, keys[0])
+ if args.sign_event_room_version:
+ room_version = KNOWN_ROOM_VERSIONS.get(args.sign_event_room_version)
+ if not room_version:
+ print(
+ f"Unknown room version {args.sign_event_room_version}", file=sys.stderr
+ )
+ sys.exit(1)
+ add_hashes_and_signatures(room_version, obj, args.server_name, keys[0])
+ else:
+ sign_json(obj, args.server_name, keys[0])
+
for c in json_encoder.iterencode(obj):
args.output.write(c)
args.output.write("\n")
diff --git a/setup.py b/setup.py
index ad99b3bd2c..2c6fb9aacb 100755
--- a/setup.py
+++ b/setup.py
@@ -152,6 +152,12 @@ setup(
long_description=long_description,
long_description_content_type="text/x-rst",
python_requires="~=3.6",
+ entry_points={
+ "console_scripts": [
+ "synapse_homeserver = synapse.app.homeserver:main",
+ "synapse_worker = synapse.app.generic_worker:main",
+ ]
+ },
classifiers=[
"Development Status :: 5 - Production/Stable",
"Topic :: Communications :: Chat",
diff --git a/synapse/__init__.py b/synapse/__init__.py
index 48ac38aec6..6369f18a53 100644
--- a/synapse/__init__.py
+++ b/synapse/__init__.py
@@ -47,7 +47,7 @@ try:
except ImportError:
pass
-__version__ = "1.47.1"
+__version__ = "1.49.0rc1"
if bool(os.environ.get("SYNAPSE_TEST_PATCH_LOG_CONTEXTS", False)):
# We import here so that we don't have to install a bunch of deps when
diff --git a/synapse/app/_base.py b/synapse/app/_base.py
index 807ee3d46e..5fc59c1be1 100644
--- a/synapse/app/_base.py
+++ b/synapse/app/_base.py
@@ -32,6 +32,7 @@ from typing import (
Iterable,
List,
NoReturn,
+ Optional,
Tuple,
cast,
)
@@ -129,7 +130,7 @@ def start_worker_reactor(
def start_reactor(
appname: str,
soft_file_limit: int,
- gc_thresholds: Tuple[int, int, int],
+ gc_thresholds: Optional[Tuple[int, int, int]],
pid_file: str,
daemonize: bool,
print_pidfile: bool,
diff --git a/synapse/app/generic_worker.py b/synapse/app/generic_worker.py
index b4bed5bf40..e256de2003 100644
--- a/synapse/app/generic_worker.py
+++ b/synapse/app/generic_worker.py
@@ -505,6 +505,10 @@ def start(config_options: List[str]) -> None:
_base.start_worker_reactor("synapse-generic-worker", config)
-if __name__ == "__main__":
+def main() -> None:
with LoggingContext("main"):
start(sys.argv[1:])
+
+
+if __name__ == "__main__":
+ main()
diff --git a/synapse/app/homeserver.py b/synapse/app/homeserver.py
index 52541faab2..dd76e07321 100644
--- a/synapse/app/homeserver.py
+++ b/synapse/app/homeserver.py
@@ -358,6 +358,13 @@ def setup(config_options: List[str]) -> SynapseHomeServer:
# generating config files and shouldn't try to continue.
sys.exit(0)
+ if config.worker.worker_app:
+ raise ConfigError(
+ "You have specified `worker_app` in the config but are attempting to start a non-worker "
+ "instance. Please use `python -m synapse.app.generic_worker` instead (or remove the option if this is the main process)."
+ )
+ sys.exit(1)
+
events.USE_FROZEN_DICTS = config.server.use_frozen_dicts
synapse.util.caches.TRACK_MEMORY_USAGE = config.caches.track_memory_usage
diff --git a/synapse/appservice/__init__.py b/synapse/appservice/__init__.py
index 6504c6bd3f..f9d3bd337d 100644
--- a/synapse/appservice/__init__.py
+++ b/synapse/appservice/__init__.py
@@ -13,6 +13,7 @@
# limitations under the License.
import logging
import re
+from enum import Enum
from typing import TYPE_CHECKING, Iterable, List, Match, Optional
from synapse.api.constants import EventTypes
@@ -27,7 +28,7 @@ if TYPE_CHECKING:
logger = logging.getLogger(__name__)
-class ApplicationServiceState:
+class ApplicationServiceState(Enum):
DOWN = "down"
UP = "up"
diff --git a/synapse/config/__main__.py b/synapse/config/__main__.py
index c555f5f914..b2a7a89a35 100644
--- a/synapse/config/__main__.py
+++ b/synapse/config/__main__.py
@@ -13,12 +13,13 @@
# See the License for the specific language governing permissions and
# limitations under the License.
import sys
+from typing import List
from synapse.config._base import ConfigError
from synapse.config.homeserver import HomeServerConfig
-def main(args):
+def main(args: List[str]) -> None:
action = args[1] if len(args) > 1 and args[1] == "read" else None
# If we're reading a key in the config file, then `args[1]` will be `read` and `args[2]`
# will be the key to read.
diff --git a/synapse/config/appservice.py b/synapse/config/appservice.py
index 1ebea88db2..e4bb7224a4 100644
--- a/synapse/config/appservice.py
+++ b/synapse/config/appservice.py
@@ -1,4 +1,5 @@
# Copyright 2015, 2016 OpenMarket Ltd
+# Copyright 2021 The Matrix.org Foundation C.I.C.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
@@ -13,14 +14,14 @@
# limitations under the License.
import logging
-from typing import Dict
+from typing import Dict, List
from urllib import parse as urlparse
import yaml
from netaddr import IPSet
from synapse.appservice import ApplicationService
-from synapse.types import UserID
+from synapse.types import JsonDict, UserID
from ._base import Config, ConfigError
@@ -30,12 +31,12 @@ logger = logging.getLogger(__name__)
class AppServiceConfig(Config):
section = "appservice"
- def read_config(self, config, **kwargs):
+ def read_config(self, config, **kwargs) -> None:
self.app_service_config_files = config.get("app_service_config_files", [])
self.notify_appservices = config.get("notify_appservices", True)
self.track_appservice_user_ips = config.get("track_appservice_user_ips", False)
- def generate_config_section(cls, **kwargs):
+ def generate_config_section(cls, **kwargs) -> str:
return """\
# A list of application service config files to use
#
@@ -50,7 +51,9 @@ class AppServiceConfig(Config):
"""
-def load_appservices(hostname, config_files):
+def load_appservices(
+ hostname: str, config_files: List[str]
+) -> List[ApplicationService]:
"""Returns a list of Application Services from the config files."""
if not isinstance(config_files, list):
logger.warning("Expected %s to be a list of AS config files.", config_files)
@@ -93,7 +96,9 @@ def load_appservices(hostname, config_files):
return appservices
-def _load_appservice(hostname, as_info, config_filename):
+def _load_appservice(
+ hostname: str, as_info: JsonDict, config_filename: str
+) -> ApplicationService:
required_string_fields = ["id", "as_token", "hs_token", "sender_localpart"]
for field in required_string_fields:
if not isinstance(as_info.get(field), str):
@@ -115,9 +120,9 @@ def _load_appservice(hostname, as_info, config_filename):
user_id = user.to_string()
# Rate limiting for users of this AS is on by default (excludes sender)
- rate_limited = True
- if isinstance(as_info.get("rate_limited"), bool):
- rate_limited = as_info.get("rate_limited")
+ rate_limited = as_info.get("rate_limited")
+ if not isinstance(rate_limited, bool):
+ rate_limited = True
# namespace checks
if not isinstance(as_info.get("namespaces"), dict):
diff --git a/synapse/config/cache.py b/synapse/config/cache.py
index f054455534..d9d85f98e1 100644
--- a/synapse/config/cache.py
+++ b/synapse/config/cache.py
@@ -1,4 +1,4 @@
-# Copyright 2019 Matrix.org Foundation C.I.C.
+# Copyright 2019-2021 Matrix.org Foundation C.I.C.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
@@ -17,6 +17,8 @@ import re
import threading
from typing import Callable, Dict, Optional
+import attr
+
from synapse.python_dependencies import DependencyException, check_requirements
from ._base import Config, ConfigError
@@ -34,13 +36,13 @@ _DEFAULT_FACTOR_SIZE = 0.5
_DEFAULT_EVENT_CACHE_SIZE = "10K"
+@attr.s(slots=True, auto_attribs=True)
class CacheProperties:
- def __init__(self):
- # The default factor size for all caches
- self.default_factor_size = float(
- os.environ.get(_CACHE_PREFIX, _DEFAULT_FACTOR_SIZE)
- )
- self.resize_all_caches_func = None
+ # The default factor size for all caches
+ default_factor_size: float = float(
+ os.environ.get(_CACHE_PREFIX, _DEFAULT_FACTOR_SIZE)
+ )
+ resize_all_caches_func: Optional[Callable[[], None]] = None
properties = CacheProperties()
@@ -62,7 +64,7 @@ def _canonicalise_cache_name(cache_name: str) -> str:
def add_resizable_cache(
cache_name: str, cache_resize_callback: Callable[[float], None]
-):
+) -> None:
"""Register a cache that's size can dynamically change
Args:
@@ -91,7 +93,7 @@ class CacheConfig(Config):
_environ = os.environ
@staticmethod
- def reset():
+ def reset() -> None:
"""Resets the caches to their defaults. Used for tests."""
properties.default_factor_size = float(
os.environ.get(_CACHE_PREFIX, _DEFAULT_FACTOR_SIZE)
@@ -100,7 +102,7 @@ class CacheConfig(Config):
with _CACHES_LOCK:
_CACHES.clear()
- def generate_config_section(self, **kwargs):
+ def generate_config_section(self, **kwargs) -> str:
return """\
## Caching ##
@@ -162,7 +164,7 @@ class CacheConfig(Config):
#sync_response_cache_duration: 2m
"""
- def read_config(self, config, **kwargs):
+ def read_config(self, config, **kwargs) -> None:
self.event_cache_size = self.parse_size(
config.get("event_cache_size", _DEFAULT_EVENT_CACHE_SIZE)
)
@@ -232,7 +234,7 @@ class CacheConfig(Config):
# needing an instance of Config
properties.resize_all_caches_func = self.resize_all_caches
- def resize_all_caches(self):
+ def resize_all_caches(self) -> None:
"""Ensure all cache sizes are up to date
For each cache, run the mapped callback function with either
diff --git a/synapse/config/cas.py b/synapse/config/cas.py
index 3f81814043..6f2754092e 100644
--- a/synapse/config/cas.py
+++ b/synapse/config/cas.py
@@ -1,4 +1,5 @@
# Copyright 2015, 2016 OpenMarket Ltd
+# Copyright 2021 The Matrix.org Foundation C.I.C.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
@@ -28,7 +29,7 @@ class CasConfig(Config):
section = "cas"
- def read_config(self, config, **kwargs):
+ def read_config(self, config, **kwargs) -> None:
cas_config = config.get("cas_config", None)
self.cas_enabled = cas_config and cas_config.get("enabled", True)
@@ -51,7 +52,7 @@ class CasConfig(Config):
self.cas_displayname_attribute = None
self.cas_required_attributes = []
- def generate_config_section(self, config_dir_path, server_name, **kwargs):
+ def generate_config_section(self, config_dir_path, server_name, **kwargs) -> str:
return """\
# Enable Central Authentication Service (CAS) for registration and login.
#
diff --git a/synapse/config/database.py b/synapse/config/database.py
index 651e31b576..06ccf15cd9 100644
--- a/synapse/config/database.py
+++ b/synapse/config/database.py
@@ -1,5 +1,5 @@
# Copyright 2014-2016 OpenMarket Ltd
-# Copyright 2020 The Matrix.org Foundation C.I.C.
+# Copyright 2020-2021 The Matrix.org Foundation C.I.C.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
@@ -12,6 +12,7 @@
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
+import argparse
import logging
import os
@@ -119,7 +120,7 @@ class DatabaseConfig(Config):
self.databases = []
- def read_config(self, config, **kwargs):
+ def read_config(self, config, **kwargs) -> None:
# We *experimentally* support specifying multiple databases via the
# `databases` key. This is a map from a label to database config in the
# same format as the `database` config option, plus an extra
@@ -163,12 +164,12 @@ class DatabaseConfig(Config):
self.databases = [DatabaseConnectionConfig("master", database_config)]
self.set_databasepath(database_path)
- def generate_config_section(self, data_dir_path, **kwargs):
+ def generate_config_section(self, data_dir_path, **kwargs) -> str:
return DEFAULT_CONFIG % {
"database_path": os.path.join(data_dir_path, "homeserver.db")
}
- def read_arguments(self, args):
+ def read_arguments(self, args: argparse.Namespace) -> None:
"""
Cases for the cli input:
- If no databases are configured and no database_path is set, raise.
@@ -194,7 +195,7 @@ class DatabaseConfig(Config):
else:
logger.warning(NON_SQLITE_DATABASE_PATH_WARNING)
- def set_databasepath(self, database_path):
+ def set_databasepath(self, database_path: str) -> None:
if database_path != ":memory:":
database_path = self.abspath(database_path)
@@ -202,7 +203,7 @@ class DatabaseConfig(Config):
self.databases[0].config["args"]["database"] = database_path
@staticmethod
- def add_arguments(parser):
+ def add_arguments(parser: argparse.ArgumentParser) -> None:
db_group = parser.add_argument_group("database")
db_group.add_argument(
"-d",
diff --git a/synapse/config/experimental.py b/synapse/config/experimental.py
index 8b098ad48d..d78a15097c 100644
--- a/synapse/config/experimental.py
+++ b/synapse/config/experimental.py
@@ -46,3 +46,6 @@ class ExperimentalConfig(Config):
# MSC3266 (room summary api)
self.msc3266_enabled: bool = experimental.get("msc3266_enabled", False)
+
+ # MSC3030 (Jump to date API endpoint)
+ self.msc3030_enabled: bool = experimental.get("msc3030_enabled", False)
diff --git a/synapse/config/logger.py b/synapse/config/logger.py
index 63aab0babe..ea69b9bd9b 100644
--- a/synapse/config/logger.py
+++ b/synapse/config/logger.py
@@ -1,4 +1,5 @@
# Copyright 2014-2016 OpenMarket Ltd
+# Copyright 2021 The Matrix.org Foundation C.I.C.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
@@ -18,7 +19,7 @@ import os
import sys
import threading
from string import Template
-from typing import TYPE_CHECKING, Any, Dict
+from typing import TYPE_CHECKING, Any, Dict, Optional
import yaml
from zope.interface import implementer
@@ -40,6 +41,7 @@ from synapse.util.versionstring import get_version_string
from ._base import Config, ConfigError
if TYPE_CHECKING:
+ from synapse.config.homeserver import HomeServerConfig
from synapse.server import HomeServer
DEFAULT_LOG_CONFIG = Template(
@@ -141,13 +143,13 @@ removed in Synapse 1.3.0. You should instead set up a separate log configuration
class LoggingConfig(Config):
section = "logging"
- def read_config(self, config, **kwargs):
+ def read_config(self, config, **kwargs) -> None:
if config.get("log_file"):
raise ConfigError(LOG_FILE_ERROR)
self.log_config = self.abspath(config.get("log_config"))
self.no_redirect_stdio = config.get("no_redirect_stdio", False)
- def generate_config_section(self, config_dir_path, server_name, **kwargs):
+ def generate_config_section(self, config_dir_path, server_name, **kwargs) -> str:
log_config = os.path.join(config_dir_path, server_name + ".log.config")
return (
"""\
@@ -161,14 +163,14 @@ class LoggingConfig(Config):
% locals()
)
- def read_arguments(self, args):
+ def read_arguments(self, args: argparse.Namespace) -> None:
if args.no_redirect_stdio is not None:
self.no_redirect_stdio = args.no_redirect_stdio
if args.log_file is not None:
raise ConfigError(LOG_FILE_ERROR)
@staticmethod
- def add_arguments(parser):
+ def add_arguments(parser: argparse.ArgumentParser) -> None:
logging_group = parser.add_argument_group("logging")
logging_group.add_argument(
"-n",
@@ -197,7 +199,9 @@ class LoggingConfig(Config):
log_config_file.write(DEFAULT_LOG_CONFIG.substitute(log_file=log_file))
-def _setup_stdlib_logging(config, log_config_path, logBeginner: LogBeginner) -> None:
+def _setup_stdlib_logging(
+ config: "HomeServerConfig", log_config_path: Optional[str], logBeginner: LogBeginner
+) -> None:
"""
Set up Python standard library logging.
"""
@@ -230,7 +234,7 @@ def _setup_stdlib_logging(config, log_config_path, logBeginner: LogBeginner) ->
log_metadata_filter = MetadataFilter({"server_name": config.server.server_name})
old_factory = logging.getLogRecordFactory()
- def factory(*args, **kwargs):
+ def factory(*args: Any, **kwargs: Any) -> logging.LogRecord:
record = old_factory(*args, **kwargs)
log_context_filter.filter(record)
log_metadata_filter.filter(record)
@@ -297,7 +301,7 @@ def _load_logging_config(log_config_path: str) -> None:
logging.config.dictConfig(log_config)
-def _reload_logging_config(log_config_path):
+def _reload_logging_config(log_config_path: Optional[str]) -> None:
"""
Reload the log configuration from the file and apply it.
"""
@@ -311,8 +315,8 @@ def _reload_logging_config(log_config_path):
def setup_logging(
hs: "HomeServer",
- config,
- use_worker_options=False,
+ config: "HomeServerConfig",
+ use_worker_options: bool = False,
logBeginner: LogBeginner = globalLogBeginner,
) -> None:
"""
diff --git a/synapse/config/oidc.py b/synapse/config/oidc.py
index 42f113cd24..79c400fe30 100644
--- a/synapse/config/oidc.py
+++ b/synapse/config/oidc.py
@@ -14,7 +14,7 @@
# limitations under the License.
from collections import Counter
-from typing import Collection, Iterable, List, Mapping, Optional, Tuple, Type
+from typing import Any, Collection, Iterable, List, Mapping, Optional, Tuple, Type
import attr
@@ -36,7 +36,7 @@ LEGACY_USER_MAPPING_PROVIDER = "synapse.handlers.oidc_handler.JinjaOidcMappingPr
class OIDCConfig(Config):
section = "oidc"
- def read_config(self, config, **kwargs):
+ def read_config(self, config, **kwargs) -> None:
self.oidc_providers = tuple(_parse_oidc_provider_configs(config))
if not self.oidc_providers:
return
@@ -66,7 +66,7 @@ class OIDCConfig(Config):
# OIDC is enabled if we have a provider
return bool(self.oidc_providers)
- def generate_config_section(self, config_dir_path, server_name, **kwargs):
+ def generate_config_section(self, config_dir_path, server_name, **kwargs) -> str:
return """\
# List of OpenID Connect (OIDC) / OAuth 2.0 identity providers, for registration
# and login.
@@ -495,89 +495,89 @@ def _parse_oidc_config_dict(
)
-@attr.s(slots=True, frozen=True)
+@attr.s(slots=True, frozen=True, auto_attribs=True)
class OidcProviderClientSecretJwtKey:
# a pem-encoded signing key
- key = attr.ib(type=str)
+ key: str
# properties to include in the JWT header
- jwt_header = attr.ib(type=Mapping[str, str])
+ jwt_header: Mapping[str, str]
# properties to include in the JWT payload.
- jwt_payload = attr.ib(type=Mapping[str, str])
+ jwt_payload: Mapping[str, str]
-@attr.s(slots=True, frozen=True)
+@attr.s(slots=True, frozen=True, auto_attribs=True)
class OidcProviderConfig:
# a unique identifier for this identity provider. Used in the 'user_external_ids'
# table, as well as the query/path parameter used in the login protocol.
- idp_id = attr.ib(type=str)
+ idp_id: str
# user-facing name for this identity provider.
- idp_name = attr.ib(type=str)
+ idp_name: str
# Optional MXC URI for icon for this IdP.
- idp_icon = attr.ib(type=Optional[str])
+ idp_icon: Optional[str]
# Optional brand identifier for this IdP.
- idp_brand = attr.ib(type=Optional[str])
+ idp_brand: Optional[str]
# whether the OIDC discovery mechanism is used to discover endpoints
- discover = attr.ib(type=bool)
+ discover: bool
# the OIDC issuer. Used to validate tokens and (if discovery is enabled) to
# discover the provider's endpoints.
- issuer = attr.ib(type=str)
+ issuer: str
# oauth2 client id to use
- client_id = attr.ib(type=str)
+ client_id: str
# oauth2 client secret to use. if `None`, use client_secret_jwt_key to generate
# a secret.
- client_secret = attr.ib(type=Optional[str])
+ client_secret: Optional[str]
# key to use to construct a JWT to use as a client secret. May be `None` if
# `client_secret` is set.
- client_secret_jwt_key = attr.ib(type=Optional[OidcProviderClientSecretJwtKey])
+ client_secret_jwt_key: Optional[OidcProviderClientSecretJwtKey]
# auth method to use when exchanging the token.
# Valid values are 'client_secret_basic', 'client_secret_post' and
# 'none'.
- client_auth_method = attr.ib(type=str)
+ client_auth_method: str
# list of scopes to request
- scopes = attr.ib(type=Collection[str])
+ scopes: Collection[str]
# the oauth2 authorization endpoint. Required if discovery is disabled.
- authorization_endpoint = attr.ib(type=Optional[str])
+ authorization_endpoint: Optional[str]
# the oauth2 token endpoint. Required if discovery is disabled.
- token_endpoint = attr.ib(type=Optional[str])
+ token_endpoint: Optional[str]
# the OIDC userinfo endpoint. Required if discovery is disabled and the
# "openid" scope is not requested.
- userinfo_endpoint = attr.ib(type=Optional[str])
+ userinfo_endpoint: Optional[str]
# URI where to fetch the JWKS. Required if discovery is disabled and the
# "openid" scope is used.
- jwks_uri = attr.ib(type=Optional[str])
+ jwks_uri: Optional[str]
# Whether to skip metadata verification
- skip_verification = attr.ib(type=bool)
+ skip_verification: bool
# Whether to fetch the user profile from the userinfo endpoint. Valid
# values are: "auto" or "userinfo_endpoint".
- user_profile_method = attr.ib(type=str)
+ user_profile_method: str
# whether to allow a user logging in via OIDC to match a pre-existing account
# instead of failing
- allow_existing_users = attr.ib(type=bool)
+ allow_existing_users: bool
# the class of the user mapping provider
- user_mapping_provider_class = attr.ib(type=Type)
+ user_mapping_provider_class: Type
# the config of the user mapping provider
- user_mapping_provider_config = attr.ib()
+ user_mapping_provider_config: Any
# required attributes to require in userinfo to allow login/registration
- attribute_requirements = attr.ib(type=List[SsoAttributeRequirement])
+ attribute_requirements: List[SsoAttributeRequirement]
diff --git a/synapse/config/registration.py b/synapse/config/registration.py
index 1ddad7cb70..7a059c6dec 100644
--- a/synapse/config/registration.py
+++ b/synapse/config/registration.py
@@ -1,4 +1,5 @@
# Copyright 2015, 2016 OpenMarket Ltd
+# Copyright 2021 The Matrix.org Foundation C.I.C.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
@@ -11,6 +12,7 @@
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
+import argparse
from typing import Optional
from synapse.api.constants import RoomCreationPreset
@@ -128,11 +130,60 @@ class RegistrationConfig(Config):
int
] = refreshable_access_token_lifetime
+ if (
+ self.session_lifetime is not None
+ and "refreshable_access_token_lifetime" in config
+ ):
+ if self.session_lifetime < self.refreshable_access_token_lifetime:
+ raise ConfigError(
+ "Both `session_lifetime` and `refreshable_access_token_lifetime` "
+ "configuration options have been set, but `refreshable_access_token_lifetime` "
+ " exceeds `session_lifetime`!"
+ )
+
+ # The `nonrefreshable_access_token_lifetime` applies for tokens that can NOT be
+ # refreshed using a refresh token.
+ # If it is None, then these tokens last for the entire length of the session,
+ # which is infinite by default.
+ # The intention behind this configuration option is to help with requiring
+ # all clients to use refresh tokens, if the homeserver administrator requires.
+ nonrefreshable_access_token_lifetime = config.get(
+ "nonrefreshable_access_token_lifetime",
+ None,
+ )
+ if nonrefreshable_access_token_lifetime is not None:
+ nonrefreshable_access_token_lifetime = self.parse_duration(
+ nonrefreshable_access_token_lifetime
+ )
+ self.nonrefreshable_access_token_lifetime = nonrefreshable_access_token_lifetime
+
+ if (
+ self.session_lifetime is not None
+ and self.nonrefreshable_access_token_lifetime is not None
+ ):
+ if self.session_lifetime < self.nonrefreshable_access_token_lifetime:
+ raise ConfigError(
+ "Both `session_lifetime` and `nonrefreshable_access_token_lifetime` "
+ "configuration options have been set, but `nonrefreshable_access_token_lifetime` "
+ " exceeds `session_lifetime`!"
+ )
+
refresh_token_lifetime = config.get("refresh_token_lifetime")
if refresh_token_lifetime is not None:
refresh_token_lifetime = self.parse_duration(refresh_token_lifetime)
self.refresh_token_lifetime: Optional[int] = refresh_token_lifetime
+ if (
+ self.session_lifetime is not None
+ and self.refresh_token_lifetime is not None
+ ):
+ if self.session_lifetime < self.refresh_token_lifetime:
+ raise ConfigError(
+ "Both `session_lifetime` and `refresh_token_lifetime` "
+ "configuration options have been set, but `refresh_token_lifetime` "
+ " exceeds `session_lifetime`!"
+ )
+
# The fallback template used for authenticating using a registration token
self.registration_token_template = self.read_template("registration_token.html")
@@ -169,6 +220,44 @@ class RegistrationConfig(Config):
#
#session_lifetime: 24h
+ # Time that an access token remains valid for, if the session is
+ # using refresh tokens.
+ # For more information about refresh tokens, please see the manual.
+ # Note that this only applies to clients which advertise support for
+ # refresh tokens.
+ #
+ # Note also that this is calculated at login time and refresh time:
+ # changes are not applied to existing sessions until they are refreshed.
+ #
+ # By default, this is 5 minutes.
+ #
+ #refreshable_access_token_lifetime: 5m
+
+ # Time that a refresh token remains valid for (provided that it is not
+ # exchanged for another one first).
+ # This option can be used to automatically log-out inactive sessions.
+ # Please see the manual for more information.
+ #
+ # Note also that this is calculated at login time and refresh time:
+ # changes are not applied to existing sessions until they are refreshed.
+ #
+ # By default, this is infinite.
+ #
+ #refresh_token_lifetime: 24h
+
+ # Time that an access token remains valid for, if the session is NOT
+ # using refresh tokens.
+ # Please note that not all clients support refresh tokens, so setting
+ # this to a short value may be inconvenient for some users who will
+ # then be logged out frequently.
+ #
+ # Note also that this is calculated at login time: changes are not applied
+ # retrospectively to existing sessions for users that have already logged in.
+ #
+ # By default, this is infinite.
+ #
+ #nonrefreshable_access_token_lifetime: 24h
+
# The user must provide all of the below types of 3PID when registering.
#
#registrations_require_3pid:
@@ -362,7 +451,7 @@ class RegistrationConfig(Config):
)
@staticmethod
- def add_arguments(parser):
+ def add_arguments(parser: argparse.ArgumentParser) -> None:
reg_group = parser.add_argument_group("registration")
reg_group.add_argument(
"--enable-registration",
@@ -371,6 +460,6 @@ class RegistrationConfig(Config):
help="Enable registration for new users.",
)
- def read_arguments(self, args):
+ def read_arguments(self, args: argparse.Namespace) -> None:
if args.enable_registration is not None:
self.enable_registration = strtobool(str(args.enable_registration))
diff --git a/synapse/config/repository.py b/synapse/config/repository.py
index 69906a98d4..b129b9dd68 100644
--- a/synapse/config/repository.py
+++ b/synapse/config/repository.py
@@ -15,11 +15,12 @@
import logging
import os
from collections import namedtuple
-from typing import Dict, List
+from typing import Dict, List, Tuple
from urllib.request import getproxies_environment # type: ignore
from synapse.config.server import DEFAULT_IP_RANGE_BLACKLIST, generate_ip_set
from synapse.python_dependencies import DependencyException, check_requirements
+from synapse.types import JsonDict
from synapse.util.module_loader import load_module
from ._base import Config, ConfigError
@@ -57,7 +58,9 @@ MediaStorageProviderConfig = namedtuple(
)
-def parse_thumbnail_requirements(thumbnail_sizes):
+def parse_thumbnail_requirements(
+ thumbnail_sizes: List[JsonDict],
+) -> Dict[str, Tuple[ThumbnailRequirement, ...]]:
"""Takes a list of dictionaries with "width", "height", and "method" keys
and creates a map from image media types to the thumbnail size, thumbnailing
method, and thumbnail media type to precalculate
@@ -69,7 +72,7 @@ def parse_thumbnail_requirements(thumbnail_sizes):
Dictionary mapping from media type string to list of
ThumbnailRequirement tuples.
"""
- requirements: Dict[str, List] = {}
+ requirements: Dict[str, List[ThumbnailRequirement]] = {}
for size in thumbnail_sizes:
width = size["width"]
height = size["height"]
diff --git a/synapse/config/saml2.py b/synapse/config/saml2.py
index ba2b0905ff..ec9d9f65e7 100644
--- a/synapse/config/saml2.py
+++ b/synapse/config/saml2.py
@@ -1,5 +1,5 @@
# Copyright 2018 New Vector Ltd
-# Copyright 2019 The Matrix.org Foundation C.I.C.
+# Copyright 2019-2021 The Matrix.org Foundation C.I.C.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
@@ -14,10 +14,11 @@
# limitations under the License.
import logging
-from typing import Any, List
+from typing import Any, List, Set
from synapse.config.sso import SsoAttributeRequirement
from synapse.python_dependencies import DependencyException, check_requirements
+from synapse.types import JsonDict
from synapse.util.module_loader import load_module, load_python_module
from ._base import Config, ConfigError
@@ -33,7 +34,7 @@ LEGACY_USER_MAPPING_PROVIDER = (
)
-def _dict_merge(merge_dict, into_dict):
+def _dict_merge(merge_dict: dict, into_dict: dict) -> None:
"""Do a deep merge of two dicts
Recursively merges `merge_dict` into `into_dict`:
@@ -43,8 +44,8 @@ def _dict_merge(merge_dict, into_dict):
the value from `merge_dict`.
Args:
- merge_dict (dict): dict to merge
- into_dict (dict): target dict
+ merge_dict: dict to merge
+ into_dict: target dict to be modified
"""
for k, v in merge_dict.items():
if k not in into_dict:
@@ -64,7 +65,7 @@ def _dict_merge(merge_dict, into_dict):
class SAML2Config(Config):
section = "saml2"
- def read_config(self, config, **kwargs):
+ def read_config(self, config, **kwargs) -> None:
self.saml2_enabled = False
saml2_config = config.get("saml2_config")
@@ -183,8 +184,8 @@ class SAML2Config(Config):
)
def _default_saml_config_dict(
- self, required_attributes: set, optional_attributes: set
- ):
+ self, required_attributes: Set[str], optional_attributes: Set[str]
+ ) -> JsonDict:
"""Generate a configuration dictionary with required and optional attributes that
will be needed to process new user registration
@@ -195,7 +196,7 @@ class SAML2Config(Config):
additional information to Synapse user accounts, but are not required
Returns:
- dict: A SAML configuration dictionary
+ A SAML configuration dictionary
"""
import saml2
@@ -222,7 +223,7 @@ class SAML2Config(Config):
},
}
- def generate_config_section(self, config_dir_path, server_name, **kwargs):
+ def generate_config_section(self, config_dir_path, server_name, **kwargs) -> str:
return """\
## Single sign-on integration ##
diff --git a/synapse/config/server.py b/synapse/config/server.py
index 8445e9dd05..ba5b954263 100644
--- a/synapse/config/server.py
+++ b/synapse/config/server.py
@@ -12,6 +12,7 @@
# See the License for the specific language governing permissions and
# limitations under the License.
+import argparse
import itertools
import logging
import os.path
@@ -27,6 +28,7 @@ from netaddr import AddrFormatError, IPNetwork, IPSet
from twisted.conch.ssh.keys import Key
from synapse.api.room_versions import KNOWN_ROOM_VERSIONS
+from synapse.types import JsonDict
from synapse.util.module_loader import load_module
from synapse.util.stringutils import parse_and_validate_server_name
@@ -1223,7 +1225,7 @@ class ServerConfig(Config):
% locals()
)
- def read_arguments(self, args):
+ def read_arguments(self, args: argparse.Namespace) -> None:
if args.manhole is not None:
self.manhole = args.manhole
if args.daemonize is not None:
@@ -1232,7 +1234,7 @@ class ServerConfig(Config):
self.print_pidfile = args.print_pidfile
@staticmethod
- def add_arguments(parser):
+ def add_arguments(parser: argparse.ArgumentParser) -> None:
server_group = parser.add_argument_group("server")
server_group.add_argument(
"-D",
@@ -1274,14 +1276,16 @@ class ServerConfig(Config):
)
-def is_threepid_reserved(reserved_threepids, threepid):
+def is_threepid_reserved(
+ reserved_threepids: List[JsonDict], threepid: JsonDict
+) -> bool:
"""Check the threepid against the reserved threepid config
Args:
- reserved_threepids([dict]) - list of reserved threepids
- threepid(dict) - The threepid to test for
+ reserved_threepids: List of reserved threepids
+ threepid: The threepid to test for
Returns:
- boolean Is the threepid undertest reserved_user
+ Is the threepid undertest reserved_user
"""
for tp in reserved_threepids:
@@ -1290,7 +1294,9 @@ def is_threepid_reserved(reserved_threepids, threepid):
return False
-def read_gc_thresholds(thresholds):
+def read_gc_thresholds(
+ thresholds: Optional[List[Any]],
+) -> Optional[Tuple[int, int, int]]:
"""Reads the three integer thresholds for garbage collection. Ensures that
the thresholds are integers if thresholds are supplied.
"""
diff --git a/synapse/config/sso.py b/synapse/config/sso.py
index 60aacb13ea..e4a4243261 100644
--- a/synapse/config/sso.py
+++ b/synapse/config/sso.py
@@ -1,4 +1,4 @@
-# Copyright 2020 The Matrix.org Foundation C.I.C.
+# Copyright 2020-2021 The Matrix.org Foundation C.I.C.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
@@ -29,13 +29,13 @@ https://matrix-org.github.io/synapse/latest/templates.html
---------------------------------------------------------------------------------------"""
-@attr.s(frozen=True)
+@attr.s(frozen=True, auto_attribs=True)
class SsoAttributeRequirement:
"""Object describing a single requirement for SSO attributes."""
- attribute = attr.ib(type=str)
+ attribute: str
# If a value is not given, than the attribute must simply exist.
- value = attr.ib(type=Optional[str])
+ value: Optional[str]
JSON_SCHEMA = {
"type": "object",
@@ -49,7 +49,7 @@ class SSOConfig(Config):
section = "sso"
- def read_config(self, config, **kwargs):
+ def read_config(self, config, **kwargs) -> None:
sso_config: Dict[str, Any] = config.get("sso") or {}
# The sso-specific template_dir
@@ -106,7 +106,7 @@ class SSOConfig(Config):
)
self.sso_client_whitelist.append(login_fallback_url)
- def generate_config_section(self, **kwargs):
+ def generate_config_section(self, **kwargs) -> str:
return """\
# Additional settings to use with single-sign on systems such as OpenID Connect,
# SAML2 and CAS.
diff --git a/synapse/config/workers.py b/synapse/config/workers.py
index 4507992031..576f519188 100644
--- a/synapse/config/workers.py
+++ b/synapse/config/workers.py
@@ -1,4 +1,5 @@
# Copyright 2016 OpenMarket Ltd
+# Copyright 2021 The Matrix.org Foundation C.I.C.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
@@ -12,6 +13,7 @@
# See the License for the specific language governing permissions and
# limitations under the License.
+import argparse
from typing import List, Union
import attr
@@ -343,7 +345,7 @@ class WorkerConfig(Config):
#worker_replication_secret: ""
"""
- def read_arguments(self, args):
+ def read_arguments(self, args: argparse.Namespace) -> None:
# We support a bunch of command line arguments that override options in
# the config. A lot of these options have a worker_* prefix when running
# on workers so we also have to override them when command line options
diff --git a/synapse/events/utils.py b/synapse/events/utils.py
index e5967c995e..84ef69df67 100644
--- a/synapse/events/utils.py
+++ b/synapse/events/utils.py
@@ -306,6 +306,7 @@ def format_event_for_client_v2_without_room_id(d: JsonDict) -> JsonDict:
def serialize_event(
e: Union[JsonDict, EventBase],
time_now_ms: int,
+ *,
as_client_event: bool = True,
event_format: Callable[[JsonDict], JsonDict] = format_event_for_client_v1,
token_id: Optional[str] = None,
@@ -393,7 +394,8 @@ class EventClientSerializer:
self,
event: Union[JsonDict, EventBase],
time_now: int,
- bundle_relations: bool = True,
+ *,
+ bundle_aggregations: bool = True,
**kwargs: Any,
) -> JsonDict:
"""Serializes a single event.
@@ -401,8 +403,9 @@ class EventClientSerializer:
Args:
event: The event being serialized.
time_now: The current time in milliseconds
- bundle_relations: Whether to include the bundled relations for this
- event.
+ bundle_aggregations: Whether to include the bundled aggregations for this
+ event. Only applies to non-state events. (State events never include
+ bundled aggregations.)
**kwargs: Arguments to pass to `serialize_event`
Returns:
@@ -414,20 +417,27 @@ class EventClientSerializer:
serialized_event = serialize_event(event, time_now, **kwargs)
- # If MSC1849 is enabled then we need to look if there are any relations
- # we need to bundle in with the event.
- # Do not bundle relations if the event has been redacted
- if not event.internal_metadata.is_redacted() and (
- self._msc1849_enabled and bundle_relations
+ # Check if there are any bundled aggregations to include with the event.
+ #
+ # Do not bundle aggregations if any of the following at true:
+ #
+ # * Support is disabled via the configuration or the caller.
+ # * The event is a state event.
+ # * The event has been redacted.
+ if (
+ self._msc1849_enabled
+ and bundle_aggregations
+ and not event.is_state()
+ and not event.internal_metadata.is_redacted()
):
- await self._injected_bundled_relations(event, time_now, serialized_event)
+ await self._injected_bundled_aggregations(event, time_now, serialized_event)
return serialized_event
- async def _injected_bundled_relations(
+ async def _injected_bundled_aggregations(
self, event: EventBase, time_now: int, serialized_event: JsonDict
) -> None:
- """Potentially injects bundled relations into the unsigned portion of the serialized event.
+ """Potentially injects bundled aggregations into the unsigned portion of the serialized event.
Args:
event: The event being serialized.
@@ -435,20 +445,28 @@ class EventClientSerializer:
serialized_event: The serialized event which may be modified.
"""
+ # Do not bundle aggregations for an event which represents an edit or an
+ # annotation. It does not make sense for them to have related events.
+ relates_to = event.content.get("m.relates_to")
+ if isinstance(relates_to, (dict, frozendict)):
+ relation_type = relates_to.get("rel_type")
+ if relation_type in (RelationTypes.ANNOTATION, RelationTypes.REPLACE):
+ return
+
event_id = event.event_id
- # The bundled relations to include.
- relations = {}
+ # The bundled aggregations to include.
+ aggregations = {}
annotations = await self.store.get_aggregation_groups_for_event(event_id)
if annotations.chunk:
- relations[RelationTypes.ANNOTATION] = annotations.to_dict()
+ aggregations[RelationTypes.ANNOTATION] = annotations.to_dict()
references = await self.store.get_relations_for_event(
event_id, RelationTypes.REFERENCE, direction="f"
)
if references.chunk:
- relations[RelationTypes.REFERENCE] = references.to_dict()
+ aggregations[RelationTypes.REFERENCE] = references.to_dict()
edit = None
if event.type == EventTypes.Message:
@@ -474,7 +492,7 @@ class EventClientSerializer:
else:
serialized_event["content"].pop("m.relates_to", None)
- relations[RelationTypes.REPLACE] = {
+ aggregations[RelationTypes.REPLACE] = {
"event_id": edit.event_id,
"origin_server_ts": edit.origin_server_ts,
"sender": edit.sender,
@@ -487,17 +505,19 @@ class EventClientSerializer:
latest_thread_event,
) = await self.store.get_thread_summary(event_id)
if latest_thread_event:
- relations[RelationTypes.THREAD] = {
- # Don't bundle relations as this could recurse forever.
+ aggregations[RelationTypes.THREAD] = {
+ # Don't bundle aggregations as this could recurse forever.
"latest_event": await self.serialize_event(
- latest_thread_event, time_now, bundle_relations=False
+ latest_thread_event, time_now, bundle_aggregations=False
),
"count": thread_count,
}
- # If any bundled relations were found, include them.
- if relations:
- serialized_event["unsigned"].setdefault("m.relations", {}).update(relations)
+ # If any bundled aggregations were found, include them.
+ if aggregations:
+ serialized_event["unsigned"].setdefault("m.relations", {}).update(
+ aggregations
+ )
async def serialize_events(
self, events: Iterable[Union[JsonDict, EventBase]], time_now: int, **kwargs: Any
diff --git a/synapse/federation/federation_client.py b/synapse/federation/federation_client.py
index bc3f96c1fc..fee1477ab6 100644
--- a/synapse/federation/federation_client.py
+++ b/synapse/federation/federation_client.py
@@ -128,7 +128,7 @@ class FederationClient(FederationBase):
reset_expiry_on_get=False,
)
- def _clear_tried_cache(self):
+ def _clear_tried_cache(self) -> None:
"""Clear pdu_destination_tried cache"""
now = self._clock.time_msec()
@@ -800,7 +800,7 @@ class FederationClient(FederationBase):
no servers successfully handle the request.
"""
- async def send_request(destination) -> SendJoinResult:
+ async def send_request(destination: str) -> SendJoinResult:
response = await self._do_send_join(room_version, destination, pdu)
# If an event was returned (and expected to be returned):
@@ -1517,6 +1517,83 @@ class FederationClient(FederationBase):
self._get_room_hierarchy_cache[(room_id, suggested_only)] = result
return result
+ async def timestamp_to_event(
+ self, destination: str, room_id: str, timestamp: int, direction: str
+ ) -> "TimestampToEventResponse":
+ """
+ Calls a remote federating server at `destination` asking for their
+ closest event to the given timestamp in the given direction. Also
+ validates the response to always return the expected keys or raises an
+ error.
+
+ Args:
+ destination: Domain name of the remote homeserver
+ room_id: Room to fetch the event from
+ timestamp: The point in time (inclusive) we should navigate from in
+ the given direction to find the closest event.
+ direction: ["f"|"b"] to indicate whether we should navigate forward
+ or backward from the given timestamp to find the closest event.
+
+ Returns:
+ A parsed TimestampToEventResponse including the closest event_id
+ and origin_server_ts
+
+ Raises:
+ Various exceptions when the request fails
+ InvalidResponseError when the response does not have the correct
+ keys or wrong types
+ """
+ remote_response = await self.transport_layer.timestamp_to_event(
+ destination, room_id, timestamp, direction
+ )
+
+ if not isinstance(remote_response, dict):
+ raise InvalidResponseError(
+ "Response must be a JSON dictionary but received %r" % remote_response
+ )
+
+ try:
+ return TimestampToEventResponse.from_json_dict(remote_response)
+ except ValueError as e:
+ raise InvalidResponseError(str(e))
+
+
+@attr.s(frozen=True, slots=True, auto_attribs=True)
+class TimestampToEventResponse:
+ """Typed response dictionary for the federation /timestamp_to_event endpoint"""
+
+ event_id: str
+ origin_server_ts: int
+
+ # the raw data, including the above keys
+ data: JsonDict
+
+ @classmethod
+ def from_json_dict(cls, d: JsonDict) -> "TimestampToEventResponse":
+ """Parsed response from the federation /timestamp_to_event endpoint
+
+ Args:
+ d: JSON object response to be parsed
+
+ Raises:
+ ValueError if d does not the correct keys or they are the wrong types
+ """
+
+ event_id = d.get("event_id")
+ if not isinstance(event_id, str):
+ raise ValueError(
+ "Invalid response: 'event_id' must be a str but received %r" % event_id
+ )
+
+ origin_server_ts = d.get("origin_server_ts")
+ if not isinstance(origin_server_ts, int):
+ raise ValueError(
+ "Invalid response: 'origin_server_ts' must be a int but received %r"
+ % origin_server_ts
+ )
+
+ return cls(event_id, origin_server_ts, d)
+
@attr.s(frozen=True, slots=True, auto_attribs=True)
class FederationSpaceSummaryEventResult:
diff --git a/synapse/federation/federation_server.py b/synapse/federation/federation_server.py
index 8fbc75aa65..8e37e76206 100644
--- a/synapse/federation/federation_server.py
+++ b/synapse/federation/federation_server.py
@@ -1,6 +1,6 @@
# Copyright 2015, 2016 OpenMarket Ltd
# Copyright 2018 New Vector Ltd
-# Copyright 2019 Matrix.org Federation C.I.C
+# Copyright 2019-2021 Matrix.org Federation C.I.C
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
@@ -110,6 +110,7 @@ class FederationServer(FederationBase):
super().__init__(hs)
self.handler = hs.get_federation_handler()
+ self.storage = hs.get_storage()
self._federation_event_handler = hs.get_federation_event_handler()
self.state = hs.get_state_handler()
self._event_auth_handler = hs.get_event_auth_handler()
@@ -200,6 +201,48 @@ class FederationServer(FederationBase):
return 200, res
+ async def on_timestamp_to_event_request(
+ self, origin: str, room_id: str, timestamp: int, direction: str
+ ) -> Tuple[int, Dict[str, Any]]:
+ """When we receive a federated `/timestamp_to_event` request,
+ handle all of the logic for validating and fetching the event.
+
+ Args:
+ origin: The server we received the event from
+ room_id: Room to fetch the event from
+ timestamp: The point in time (inclusive) we should navigate from in
+ the given direction to find the closest event.
+ direction: ["f"|"b"] to indicate whether we should navigate forward
+ or backward from the given timestamp to find the closest event.
+
+ Returns:
+ Tuple indicating the response status code and dictionary response
+ body including `event_id`.
+ """
+ with (await self._server_linearizer.queue((origin, room_id))):
+ origin_host, _ = parse_server_name(origin)
+ await self.check_server_matches_acl(origin_host, room_id)
+
+ # We only try to fetch data from the local database
+ event_id = await self.store.get_event_id_for_timestamp(
+ room_id, timestamp, direction
+ )
+ if event_id:
+ event = await self.store.get_event(
+ event_id, allow_none=False, allow_rejected=False
+ )
+
+ return 200, {
+ "event_id": event_id,
+ "origin_server_ts": event.origin_server_ts,
+ }
+
+ raise SynapseError(
+ 404,
+ "Unable to find event from %s in direction %s" % (timestamp, direction),
+ errcode=Codes.NOT_FOUND,
+ )
+
async def on_incoming_transaction(
self,
origin: str,
@@ -407,7 +450,7 @@ class FederationServer(FederationBase):
# require callouts to other servers to fetch missing events), but
# impose a limit to avoid going too crazy with ram/cpu.
- async def process_pdus_for_room(room_id: str):
+ async def process_pdus_for_room(room_id: str) -> None:
with nested_logging_context(room_id):
logger.debug("Processing PDUs for %s", room_id)
@@ -504,7 +547,7 @@ class FederationServer(FederationBase):
async def on_state_ids_request(
self, origin: str, room_id: str, event_id: str
- ) -> Tuple[int, Dict[str, Any]]:
+ ) -> Tuple[int, JsonDict]:
if not event_id:
raise NotImplementedError("Specify an event")
@@ -524,7 +567,9 @@ class FederationServer(FederationBase):
return 200, resp
- async def _on_state_ids_request_compute(self, room_id, event_id):
+ async def _on_state_ids_request_compute(
+ self, room_id: str, event_id: str
+ ) -> JsonDict:
state_ids = await self.handler.get_state_ids_for_pdu(room_id, event_id)
auth_chain_ids = await self.store.get_auth_chain_ids(room_id, state_ids)
return {"pdu_ids": state_ids, "auth_chain_ids": auth_chain_ids}
diff --git a/synapse/federation/persistence.py b/synapse/federation/persistence.py
index 4fead6ca29..523ab1c51e 100644
--- a/synapse/federation/persistence.py
+++ b/synapse/federation/persistence.py
@@ -1,4 +1,5 @@
# Copyright 2014-2016 OpenMarket Ltd
+# Copyright 2021 The Matrix.org Foundation C.I.C.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
@@ -23,6 +24,7 @@ from typing import Optional, Tuple
from synapse.federation.units import Transaction
from synapse.logging.utils import log_function
+from synapse.storage.databases.main import DataStore
from synapse.types import JsonDict
logger = logging.getLogger(__name__)
@@ -31,7 +33,7 @@ logger = logging.getLogger(__name__)
class TransactionActions:
"""Defines persistence actions that relate to handling Transactions."""
- def __init__(self, datastore):
+ def __init__(self, datastore: DataStore):
self.store = datastore
@log_function
diff --git a/synapse/federation/send_queue.py b/synapse/federation/send_queue.py
index 1fbf325fdc..63289a5a33 100644
--- a/synapse/federation/send_queue.py
+++ b/synapse/federation/send_queue.py
@@ -1,4 +1,5 @@
# Copyright 2014-2016 OpenMarket Ltd
+# Copyright 2021 The Matrix.org Foundation C.I.C.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
@@ -350,7 +351,7 @@ class BaseFederationRow:
TypeId = "" # Unique string that ids the type. Must be overridden in sub classes.
@staticmethod
- def from_data(data):
+ def from_data(data: JsonDict) -> "BaseFederationRow":
"""Parse the data from the federation stream into a row.
Args:
@@ -359,7 +360,7 @@ class BaseFederationRow:
"""
raise NotImplementedError()
- def to_data(self):
+ def to_data(self) -> JsonDict:
"""Serialize this row to be sent over the federation stream.
Returns:
@@ -368,7 +369,7 @@ class BaseFederationRow:
"""
raise NotImplementedError()
- def add_to_buffer(self, buff):
+ def add_to_buffer(self, buff: "ParsedFederationStreamData") -> None:
"""Add this row to the appropriate field in the buffer ready for this
to be sent over federation.
@@ -391,15 +392,15 @@ class PresenceDestinationsRow(
TypeId = "pd"
@staticmethod
- def from_data(data):
+ def from_data(data: JsonDict) -> "PresenceDestinationsRow":
return PresenceDestinationsRow(
state=UserPresenceState.from_dict(data["state"]), destinations=data["dests"]
)
- def to_data(self):
+ def to_data(self) -> JsonDict:
return {"state": self.state.as_dict(), "dests": self.destinations}
- def add_to_buffer(self, buff):
+ def add_to_buffer(self, buff: "ParsedFederationStreamData") -> None:
buff.presence_destinations.append((self.state, self.destinations))
@@ -417,13 +418,13 @@ class KeyedEduRow(
TypeId = "k"
@staticmethod
- def from_data(data):
+ def from_data(data: JsonDict) -> "KeyedEduRow":
return KeyedEduRow(key=tuple(data["key"]), edu=Edu(**data["edu"]))
- def to_data(self):
+ def to_data(self) -> JsonDict:
return {"key": self.key, "edu": self.edu.get_internal_dict()}
- def add_to_buffer(self, buff):
+ def add_to_buffer(self, buff: "ParsedFederationStreamData") -> None:
buff.keyed_edus.setdefault(self.edu.destination, {})[self.key] = self.edu
@@ -433,13 +434,13 @@ class EduRow(BaseFederationRow, namedtuple("EduRow", ("edu",))): # Edu
TypeId = "e"
@staticmethod
- def from_data(data):
+ def from_data(data: JsonDict) -> "EduRow":
return EduRow(Edu(**data))
- def to_data(self):
+ def to_data(self) -> JsonDict:
return self.edu.get_internal_dict()
- def add_to_buffer(self, buff):
+ def add_to_buffer(self, buff: "ParsedFederationStreamData") -> None:
buff.edus.setdefault(self.edu.destination, []).append(self.edu)
diff --git a/synapse/federation/sender/per_destination_queue.py b/synapse/federation/sender/per_destination_queue.py
index afe35e72b6..391b30fbb5 100644
--- a/synapse/federation/sender/per_destination_queue.py
+++ b/synapse/federation/sender/per_destination_queue.py
@@ -1,5 +1,6 @@
# Copyright 2014-2016 OpenMarket Ltd
# Copyright 2019 New Vector Ltd
+# Copyright 2021 The Matrix.org Foundation C.I.C.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
@@ -14,7 +15,8 @@
# limitations under the License.
import datetime
import logging
-from typing import TYPE_CHECKING, Dict, Hashable, Iterable, List, Optional, Tuple
+from types import TracebackType
+from typing import TYPE_CHECKING, Dict, Hashable, Iterable, List, Optional, Tuple, Type
import attr
from prometheus_client import Counter
@@ -213,7 +215,7 @@ class PerDestinationQueue:
self._pending_edus_keyed[(edu.edu_type, key)] = edu
self.attempt_new_transaction()
- def send_edu(self, edu) -> None:
+ def send_edu(self, edu: Edu) -> None:
self._pending_edus.append(edu)
self.attempt_new_transaction()
@@ -701,7 +703,12 @@ class _TransactionQueueManager:
return self._pdus, pending_edus
- async def __aexit__(self, exc_type, exc, tb):
+ async def __aexit__(
+ self,
+ exc_type: Optional[Type[BaseException]],
+ exc: Optional[BaseException],
+ tb: Optional[TracebackType],
+ ) -> None:
if exc_type is not None:
# Failed to send transaction, so we bail out.
return
diff --git a/synapse/federation/transport/client.py b/synapse/federation/transport/client.py
index fe29bcfd4b..9fc4c31c93 100644
--- a/synapse/federation/transport/client.py
+++ b/synapse/federation/transport/client.py
@@ -21,6 +21,7 @@ from typing import (
Callable,
Collection,
Dict,
+ Generator,
Iterable,
List,
Mapping,
@@ -149,6 +150,42 @@ class TransportLayerClient:
)
@log_function
+ async def timestamp_to_event(
+ self, destination: str, room_id: str, timestamp: int, direction: str
+ ) -> Union[JsonDict, List]:
+ """
+ Calls a remote federating server at `destination` asking for their
+ closest event to the given timestamp in the given direction.
+
+ Args:
+ destination: Domain name of the remote homeserver
+ room_id: Room to fetch the event from
+ timestamp: The point in time (inclusive) we should navigate from in
+ the given direction to find the closest event.
+ direction: ["f"|"b"] to indicate whether we should navigate forward
+ or backward from the given timestamp to find the closest event.
+
+ Returns:
+ Response dict received from the remote homeserver.
+
+ Raises:
+ Various exceptions when the request fails
+ """
+ path = _create_path(
+ FEDERATION_UNSTABLE_PREFIX,
+ "/org.matrix.msc3030/timestamp_to_event/%s",
+ room_id,
+ )
+
+ args = {"ts": [str(timestamp)], "dir": [direction]}
+
+ remote_response = await self.client.get_json(
+ destination, path=path, args=args, try_trailing_slash_on_400=True
+ )
+
+ return remote_response
+
+ @log_function
async def send_transaction(
self,
transaction: Transaction,
@@ -199,11 +236,16 @@ class TransportLayerClient:
@log_function
async def make_query(
- self, destination, query_type, args, retry_on_dns_fail, ignore_backoff=False
- ):
+ self,
+ destination: str,
+ query_type: str,
+ args: dict,
+ retry_on_dns_fail: bool,
+ ignore_backoff: bool = False,
+ ) -> JsonDict:
path = _create_v1_path("/query/%s", query_type)
- content = await self.client.get_json(
+ return await self.client.get_json(
destination=destination,
path=path,
args=args,
@@ -212,8 +254,6 @@ class TransportLayerClient:
ignore_backoff=ignore_backoff,
)
- return content
-
@log_function
async def make_membership_event(
self,
@@ -1281,7 +1321,7 @@ class SendJoinResponse:
@ijson.coroutine
-def _event_parser(event_dict: JsonDict):
+def _event_parser(event_dict: JsonDict) -> Generator[None, Tuple[str, Any], None]:
"""Helper function for use with `ijson.kvitems_coro` to parse key-value pairs
to add them to a given dictionary.
"""
@@ -1292,7 +1332,9 @@ def _event_parser(event_dict: JsonDict):
@ijson.coroutine
-def _event_list_parser(room_version: RoomVersion, events: List[EventBase]):
+def _event_list_parser(
+ room_version: RoomVersion, events: List[EventBase]
+) -> Generator[None, JsonDict, None]:
"""Helper function for use with `ijson.items_coro` to parse an array of
events and add them to the given list.
"""
diff --git a/synapse/federation/transport/server/__init__.py b/synapse/federation/transport/server/__init__.py
index c32539bf5a..77b936361a 100644
--- a/synapse/federation/transport/server/__init__.py
+++ b/synapse/federation/transport/server/__init__.py
@@ -22,7 +22,10 @@ from synapse.federation.transport.server._base import (
Authenticator,
BaseFederationServlet,
)
-from synapse.federation.transport.server.federation import FEDERATION_SERVLET_CLASSES
+from synapse.federation.transport.server.federation import (
+ FEDERATION_SERVLET_CLASSES,
+ FederationTimestampLookupServlet,
+)
from synapse.federation.transport.server.groups_local import GROUP_LOCAL_SERVLET_CLASSES
from synapse.federation.transport.server.groups_server import (
GROUP_SERVER_SERVLET_CLASSES,
@@ -299,7 +302,7 @@ def register_servlets(
authenticator: Authenticator,
ratelimiter: FederationRateLimiter,
servlet_groups: Optional[Iterable[str]] = None,
-):
+) -> None:
"""Initialize and register servlet classes.
Will by default register all servlets. For custom behaviour, pass in
@@ -324,6 +327,13 @@ def register_servlets(
)
for servletclass in DEFAULT_SERVLET_GROUPS[servlet_group]:
+ # Only allow the `/timestamp_to_event` servlet if msc3030 is enabled
+ if (
+ servletclass == FederationTimestampLookupServlet
+ and not hs.config.experimental.msc3030_enabled
+ ):
+ continue
+
servletclass(
hs=hs,
authenticator=authenticator,
diff --git a/synapse/federation/transport/server/_base.py b/synapse/federation/transport/server/_base.py
index cef65929c5..dc39e3537b 100644
--- a/synapse/federation/transport/server/_base.py
+++ b/synapse/federation/transport/server/_base.py
@@ -15,10 +15,13 @@
import functools
import logging
import re
+from typing import Any, Awaitable, Callable, Optional, Tuple, cast
from synapse.api.errors import Codes, FederationDeniedError, SynapseError
from synapse.api.urls import FEDERATION_V1_PREFIX
+from synapse.http.server import HttpServer, ServletCallback
from synapse.http.servlet import parse_json_object_from_request
+from synapse.http.site import SynapseRequest
from synapse.logging import opentracing
from synapse.logging.context import run_in_background
from synapse.logging.opentracing import (
@@ -29,6 +32,7 @@ from synapse.logging.opentracing import (
whitelisted_homeserver,
)
from synapse.server import HomeServer
+from synapse.types import JsonDict
from synapse.util.ratelimitutils import FederationRateLimiter
from synapse.util.stringutils import parse_and_validate_server_name
@@ -59,9 +63,11 @@ class Authenticator:
self.replication_client = hs.get_tcp_replication()
# A method just so we can pass 'self' as the authenticator to the Servlets
- async def authenticate_request(self, request, content):
+ async def authenticate_request(
+ self, request: SynapseRequest, content: Optional[JsonDict]
+ ) -> str:
now = self._clock.time_msec()
- json_request = {
+ json_request: JsonDict = {
"method": request.method.decode("ascii"),
"uri": request.uri.decode("ascii"),
"destination": self.server_name,
@@ -114,7 +120,7 @@ class Authenticator:
return origin
- async def _reset_retry_timings(self, origin):
+ async def _reset_retry_timings(self, origin: str) -> None:
try:
logger.info("Marking origin %r as up", origin)
await self.store.set_destination_retry_timings(origin, None, 0, 0)
@@ -133,14 +139,14 @@ class Authenticator:
logger.exception("Error resetting retry timings on %s", origin)
-def _parse_auth_header(header_bytes):
+def _parse_auth_header(header_bytes: bytes) -> Tuple[str, str, str]:
"""Parse an X-Matrix auth header
Args:
- header_bytes (bytes): header value
+ header_bytes: header value
Returns:
- Tuple[str, str, str]: origin, key id, signature.
+ origin, key id, signature.
Raises:
AuthenticationError if the header could not be parsed
@@ -148,9 +154,9 @@ def _parse_auth_header(header_bytes):
try:
header_str = header_bytes.decode("utf-8")
params = header_str.split(" ")[1].split(",")
- param_dict = dict(kv.split("=") for kv in params)
+ param_dict = {k: v for k, v in (kv.split("=", maxsplit=1) for kv in params)}
- def strip_quotes(value):
+ def strip_quotes(value: str) -> str:
if value.startswith('"'):
return value[1:-1]
else:
@@ -233,23 +239,25 @@ class BaseFederationServlet:
self.ratelimiter = ratelimiter
self.server_name = server_name
- def _wrap(self, func):
+ def _wrap(self, func: Callable[..., Awaitable[Tuple[int, Any]]]) -> ServletCallback:
authenticator = self.authenticator
ratelimiter = self.ratelimiter
@functools.wraps(func)
- async def new_func(request, *args, **kwargs):
+ async def new_func(
+ request: SynapseRequest, *args: Any, **kwargs: str
+ ) -> Optional[Tuple[int, Any]]:
"""A callback which can be passed to HttpServer.RegisterPaths
Args:
- request (twisted.web.http.Request):
+ request:
*args: unused?
- **kwargs (dict[unicode, unicode]): the dict mapping keys to path
- components as specified in the path match regexp.
+ **kwargs: the dict mapping keys to path components as specified
+ in the path match regexp.
Returns:
- Tuple[int, object]|None: (response code, response object) as returned by
- the callback method. None if the request has already been handled.
+ (response code, response object) as returned by the callback method.
+ None if the request has already been handled.
"""
content = None
if request.method in [b"PUT", b"POST"]:
@@ -257,7 +265,9 @@ class BaseFederationServlet:
content = parse_json_object_from_request(request)
try:
- origin = await authenticator.authenticate_request(request, content)
+ origin: Optional[str] = await authenticator.authenticate_request(
+ request, content
+ )
except NoAuthenticationError:
origin = None
if self.REQUIRE_AUTH:
@@ -301,7 +311,7 @@ class BaseFederationServlet:
"client disconnected before we started processing "
"request"
)
- return -1, None
+ return None
response = await func(
origin, content, request.args, *args, **kwargs
)
@@ -312,9 +322,9 @@ class BaseFederationServlet:
return response
- return new_func
+ return cast(ServletCallback, new_func)
- def register(self, server):
+ def register(self, server: HttpServer) -> None:
pattern = re.compile("^" + self.PREFIX + self.PATH + "$")
for method in ("GET", "PUT", "POST"):
diff --git a/synapse/federation/transport/server/federation.py b/synapse/federation/transport/server/federation.py
index 66e915228c..77bfd88ad0 100644
--- a/synapse/federation/transport/server/federation.py
+++ b/synapse/federation/transport/server/federation.py
@@ -174,6 +174,46 @@ class FederationBackfillServlet(BaseFederationServerServlet):
return await self.handler.on_backfill_request(origin, room_id, versions, limit)
+class FederationTimestampLookupServlet(BaseFederationServerServlet):
+ """
+ API endpoint to fetch the `event_id` of the closest event to the given
+ timestamp (`ts` query parameter) in the given direction (`dir` query
+ parameter).
+
+ Useful for other homeservers when they're unable to find an event locally.
+
+ `ts` is a timestamp in milliseconds where we will find the closest event in
+ the given direction.
+
+ `dir` can be `f` or `b` to indicate forwards and backwards in time from the
+ given timestamp.
+
+ GET /_matrix/federation/unstable/org.matrix.msc3030/timestamp_to_event/<roomID>?ts=<timestamp>&dir=<direction>
+ {
+ "event_id": ...
+ }
+ """
+
+ PATH = "/timestamp_to_event/(?P<room_id>[^/]*)/?"
+ PREFIX = FEDERATION_UNSTABLE_PREFIX + "/org.matrix.msc3030"
+
+ async def on_GET(
+ self,
+ origin: str,
+ content: Literal[None],
+ query: Dict[bytes, List[bytes]],
+ room_id: str,
+ ) -> Tuple[int, JsonDict]:
+ timestamp = parse_integer_from_args(query, "ts", required=True)
+ direction = parse_string_from_args(
+ query, "dir", default="f", allowed_values=["f", "b"], required=True
+ )
+
+ return await self.handler.on_timestamp_to_event_request(
+ origin, room_id, timestamp, direction
+ )
+
+
class FederationQueryServlet(BaseFederationServerServlet):
PATH = "/query/(?P<query_type>[^/]*)"
@@ -683,6 +723,7 @@ FEDERATION_SERVLET_CLASSES: Tuple[Type[BaseFederationServlet], ...] = (
FederationStateV1Servlet,
FederationStateIdsServlet,
FederationBackfillServlet,
+ FederationTimestampLookupServlet,
FederationQueryServlet,
FederationMakeJoinServlet,
FederationMakeLeaveServlet,
diff --git a/synapse/handlers/auth.py b/synapse/handlers/auth.py
index 4d9c4e5834..61607cf2ba 100644
--- a/synapse/handlers/auth.py
+++ b/synapse/handlers/auth.py
@@ -39,6 +39,7 @@ import attr
import bcrypt
import pymacaroons
import unpaddedbase64
+from pymacaroons.exceptions import MacaroonVerificationFailedException
from twisted.web.server import Request
@@ -182,8 +183,11 @@ class LoginTokenAttributes:
user_id = attr.ib(type=str)
- # the SSO Identity Provider that the user authenticated with, to get this token
auth_provider_id = attr.ib(type=str)
+ """The SSO Identity Provider that the user authenticated with, to get this token."""
+
+ auth_provider_session_id = attr.ib(type=Optional[str])
+ """The session ID advertised by the SSO Identity Provider."""
class AuthHandler:
@@ -1650,6 +1654,7 @@ class AuthHandler:
client_redirect_url: str,
extra_attributes: Optional[JsonDict] = None,
new_user: bool = False,
+ auth_provider_session_id: Optional[str] = None,
) -> None:
"""Having figured out a mxid for this user, complete the HTTP request
@@ -1665,6 +1670,7 @@ class AuthHandler:
during successful login. Must be JSON serializable.
new_user: True if we should use wording appropriate to a user who has just
registered.
+ auth_provider_session_id: The session ID from the SSO IdP received during login.
"""
# If the account has been deactivated, do not proceed with the login
# flow.
@@ -1685,6 +1691,7 @@ class AuthHandler:
extra_attributes,
new_user=new_user,
user_profile_data=profile,
+ auth_provider_session_id=auth_provider_session_id,
)
def _complete_sso_login(
@@ -1696,6 +1703,7 @@ class AuthHandler:
extra_attributes: Optional[JsonDict] = None,
new_user: bool = False,
user_profile_data: Optional[ProfileInfo] = None,
+ auth_provider_session_id: Optional[str] = None,
) -> None:
"""
The synchronous portion of complete_sso_login.
@@ -1717,7 +1725,9 @@ class AuthHandler:
# Create a login token
login_token = self.macaroon_gen.generate_short_term_login_token(
- registered_user_id, auth_provider_id=auth_provider_id
+ registered_user_id,
+ auth_provider_id=auth_provider_id,
+ auth_provider_session_id=auth_provider_session_id,
)
# Append the login token to the original redirect URL (i.e. with its query
@@ -1822,6 +1832,7 @@ class MacaroonGenerator:
self,
user_id: str,
auth_provider_id: str,
+ auth_provider_session_id: Optional[str] = None,
duration_in_ms: int = (2 * 60 * 1000),
) -> str:
macaroon = self._generate_base_macaroon(user_id)
@@ -1830,6 +1841,10 @@ class MacaroonGenerator:
expiry = now + duration_in_ms
macaroon.add_first_party_caveat("time < %d" % (expiry,))
macaroon.add_first_party_caveat("auth_provider_id = %s" % (auth_provider_id,))
+ if auth_provider_session_id is not None:
+ macaroon.add_first_party_caveat(
+ "auth_provider_session_id = %s" % (auth_provider_session_id,)
+ )
return macaroon.serialize()
def verify_short_term_login_token(self, token: str) -> LoginTokenAttributes:
@@ -1851,15 +1866,28 @@ class MacaroonGenerator:
user_id = get_value_from_macaroon(macaroon, "user_id")
auth_provider_id = get_value_from_macaroon(macaroon, "auth_provider_id")
+ auth_provider_session_id: Optional[str] = None
+ try:
+ auth_provider_session_id = get_value_from_macaroon(
+ macaroon, "auth_provider_session_id"
+ )
+ except MacaroonVerificationFailedException:
+ pass
+
v = pymacaroons.Verifier()
v.satisfy_exact("gen = 1")
v.satisfy_exact("type = login")
v.satisfy_general(lambda c: c.startswith("user_id = "))
v.satisfy_general(lambda c: c.startswith("auth_provider_id = "))
+ v.satisfy_general(lambda c: c.startswith("auth_provider_session_id = "))
satisfy_expiry(v, self.hs.get_clock().time_msec)
v.verify(macaroon, self.hs.config.key.macaroon_secret_key)
- return LoginTokenAttributes(user_id=user_id, auth_provider_id=auth_provider_id)
+ return LoginTokenAttributes(
+ user_id=user_id,
+ auth_provider_id=auth_provider_id,
+ auth_provider_session_id=auth_provider_session_id,
+ )
def generate_delete_pusher_token(self, user_id: str) -> str:
macaroon = self._generate_base_macaroon(user_id)
diff --git a/synapse/handlers/device.py b/synapse/handlers/device.py
index 68b446eb66..82ee11e921 100644
--- a/synapse/handlers/device.py
+++ b/synapse/handlers/device.py
@@ -301,6 +301,8 @@ class DeviceHandler(DeviceWorkerHandler):
user_id: str,
device_id: Optional[str],
initial_device_display_name: Optional[str] = None,
+ auth_provider_id: Optional[str] = None,
+ auth_provider_session_id: Optional[str] = None,
) -> str:
"""
If the given device has not been registered, register it with the
@@ -312,6 +314,8 @@ class DeviceHandler(DeviceWorkerHandler):
user_id: @user:id
device_id: device id supplied by client
initial_device_display_name: device display name from client
+ auth_provider_id: The SSO IdP the user used, if any.
+ auth_provider_session_id: The session ID (sid) got from the SSO IdP.
Returns:
device id (generated if none was supplied)
"""
@@ -323,6 +327,8 @@ class DeviceHandler(DeviceWorkerHandler):
user_id=user_id,
device_id=device_id,
initial_device_display_name=initial_device_display_name,
+ auth_provider_id=auth_provider_id,
+ auth_provider_session_id=auth_provider_session_id,
)
if new_device:
await self.notify_device_update(user_id, [device_id])
@@ -337,6 +343,8 @@ class DeviceHandler(DeviceWorkerHandler):
user_id=user_id,
device_id=new_device_id,
initial_device_display_name=initial_device_display_name,
+ auth_provider_id=auth_provider_id,
+ auth_provider_session_id=auth_provider_session_id,
)
if new_device:
await self.notify_device_update(user_id, [new_device_id])
diff --git a/synapse/handlers/e2e_keys.py b/synapse/handlers/e2e_keys.py
index 60c11e3d21..b2554bda04 100644
--- a/synapse/handlers/e2e_keys.py
+++ b/synapse/handlers/e2e_keys.py
@@ -65,8 +65,12 @@ class E2eKeysHandler:
else:
# Only register this edu handler on master as it requires writing
# device updates to the db
- #
- # FIXME: switch to m.signing_key_update when MSC1756 is merged into the spec
+ federation_registry.register_edu_handler(
+ "m.signing_key_update",
+ self._edu_updater.incoming_signing_key_update,
+ )
+ # also handle the unstable version
+ # FIXME: remove this when enough servers have upgraded
federation_registry.register_edu_handler(
"org.matrix.signing_key_update",
self._edu_updater.incoming_signing_key_update,
diff --git a/synapse/handlers/events.py b/synapse/handlers/events.py
index b4ff935546..32b0254c5f 100644
--- a/synapse/handlers/events.py
+++ b/synapse/handlers/events.py
@@ -122,9 +122,8 @@ class EventStreamHandler:
events,
time_now,
as_client_event=as_client_event,
- # We don't bundle "live" events, as otherwise clients
- # will end up double counting annotations.
- bundle_relations=False,
+ # Don't bundle aggregations as this is a deprecated API.
+ bundle_aggregations=False,
)
chunk = {
diff --git a/synapse/handlers/federation.py b/synapse/handlers/federation.py
index 3112cc88b1..1ea837d082 100644
--- a/synapse/handlers/federation.py
+++ b/synapse/handlers/federation.py
@@ -68,6 +68,37 @@ if TYPE_CHECKING:
logger = logging.getLogger(__name__)
+def get_domains_from_state(state: StateMap[EventBase]) -> List[Tuple[str, int]]:
+ """Get joined domains from state
+
+ Args:
+ state: State map from type/state key to event.
+
+ Returns:
+ Returns a list of servers with the lowest depth of their joins.
+ Sorted by lowest depth first.
+ """
+ joined_users = [
+ (state_key, int(event.depth))
+ for (e_type, state_key), event in state.items()
+ if e_type == EventTypes.Member and event.membership == Membership.JOIN
+ ]
+
+ joined_domains: Dict[str, int] = {}
+ for u, d in joined_users:
+ try:
+ dom = get_domain_from_id(u)
+ old_d = joined_domains.get(dom)
+ if old_d:
+ joined_domains[dom] = min(d, old_d)
+ else:
+ joined_domains[dom] = d
+ except Exception:
+ pass
+
+ return sorted(joined_domains.items(), key=lambda d: d[1])
+
+
class FederationHandler:
"""Handles general incoming federation requests
@@ -268,36 +299,6 @@ class FederationHandler:
curr_state = await self.state_handler.get_current_state(room_id)
- def get_domains_from_state(state: StateMap[EventBase]) -> List[Tuple[str, int]]:
- """Get joined domains from state
-
- Args:
- state: State map from type/state key to event.
-
- Returns:
- Returns a list of servers with the lowest depth of their joins.
- Sorted by lowest depth first.
- """
- joined_users = [
- (state_key, int(event.depth))
- for (e_type, state_key), event in state.items()
- if e_type == EventTypes.Member and event.membership == Membership.JOIN
- ]
-
- joined_domains: Dict[str, int] = {}
- for u, d in joined_users:
- try:
- dom = get_domain_from_id(u)
- old_d = joined_domains.get(dom)
- if old_d:
- joined_domains[dom] = min(d, old_d)
- else:
- joined_domains[dom] = d
- except Exception:
- pass
-
- return sorted(joined_domains.items(), key=lambda d: d[1])
-
curr_domains = get_domains_from_state(curr_state)
likely_domains = [
diff --git a/synapse/handlers/initial_sync.py b/synapse/handlers/initial_sync.py
index d4e4556155..9cd21e7f2b 100644
--- a/synapse/handlers/initial_sync.py
+++ b/synapse/handlers/initial_sync.py
@@ -165,7 +165,11 @@ class InitialSyncHandler:
invite_event = await self.store.get_event(event.event_id)
d["invite"] = await self._event_serializer.serialize_event(
- invite_event, time_now, as_client_event
+ invite_event,
+ time_now,
+ # Don't bundle aggregations as this is a deprecated API.
+ bundle_aggregations=False,
+ as_client_event=as_client_event,
)
rooms_ret.append(d)
@@ -216,7 +220,11 @@ class InitialSyncHandler:
d["messages"] = {
"chunk": (
await self._event_serializer.serialize_events(
- messages, time_now=time_now, as_client_event=as_client_event
+ messages,
+ time_now=time_now,
+ # Don't bundle aggregations as this is a deprecated API.
+ bundle_aggregations=False,
+ as_client_event=as_client_event,
)
),
"start": await start_token.to_string(self.store),
@@ -226,6 +234,8 @@ class InitialSyncHandler:
d["state"] = await self._event_serializer.serialize_events(
current_state.values(),
time_now=time_now,
+ # Don't bundle aggregations as this is a deprecated API.
+ bundle_aggregations=False,
as_client_event=as_client_event,
)
@@ -366,14 +376,18 @@ class InitialSyncHandler:
"room_id": room_id,
"messages": {
"chunk": (
- await self._event_serializer.serialize_events(messages, time_now)
+ # Don't bundle aggregations as this is a deprecated API.
+ await self._event_serializer.serialize_events(
+ messages, time_now, bundle_aggregations=False
+ )
),
"start": await start_token.to_string(self.store),
"end": await end_token.to_string(self.store),
},
"state": (
+ # Don't bundle aggregations as this is a deprecated API.
await self._event_serializer.serialize_events(
- room_state.values(), time_now
+ room_state.values(), time_now, bundle_aggregations=False
)
),
"presence": [],
@@ -392,8 +406,9 @@ class InitialSyncHandler:
# TODO: These concurrently
time_now = self.clock.time_msec()
+ # Don't bundle aggregations as this is a deprecated API.
state = await self._event_serializer.serialize_events(
- current_state.values(), time_now
+ current_state.values(), time_now, bundle_aggregations=False
)
now_token = self.hs.get_event_sources().get_current_token()
@@ -467,7 +482,10 @@ class InitialSyncHandler:
"room_id": room_id,
"messages": {
"chunk": (
- await self._event_serializer.serialize_events(messages, time_now)
+ # Don't bundle aggregations as this is a deprecated API.
+ await self._event_serializer.serialize_events(
+ messages, time_now, bundle_aggregations=False
+ )
),
"start": await start_token.to_string(self.store),
"end": await end_token.to_string(self.store),
diff --git a/synapse/handlers/message.py b/synapse/handlers/message.py
index 95b4fad3c6..87f671708c 100644
--- a/synapse/handlers/message.py
+++ b/synapse/handlers/message.py
@@ -247,13 +247,7 @@ class MessageHandler:
room_state = room_state_events[membership_event_id]
now = self.clock.time_msec()
- events = await self._event_serializer.serialize_events(
- room_state.values(),
- now,
- # We don't bother bundling aggregations in when asked for state
- # events, as clients won't use them.
- bundle_relations=False,
- )
+ events = await self._event_serializer.serialize_events(room_state.values(), now)
return events
async def get_joined_members(self, requester: Requester, room_id: str) -> dict:
diff --git a/synapse/handlers/oidc.py b/synapse/handlers/oidc.py
index 3665d91513..deb3539751 100644
--- a/synapse/handlers/oidc.py
+++ b/synapse/handlers/oidc.py
@@ -23,7 +23,7 @@ from authlib.common.security import generate_token
from authlib.jose import JsonWebToken, jwt
from authlib.oauth2.auth import ClientAuth
from authlib.oauth2.rfc6749.parameters import prepare_grant_uri
-from authlib.oidc.core import CodeIDToken, ImplicitIDToken, UserInfo
+from authlib.oidc.core import CodeIDToken, UserInfo
from authlib.oidc.discovery import OpenIDProviderMetadata, get_well_known_url
from jinja2 import Environment, Template
from pymacaroons.exceptions import (
@@ -117,7 +117,8 @@ class OidcHandler:
for idp_id, p in self._providers.items():
try:
await p.load_metadata()
- await p.load_jwks()
+ if not p._uses_userinfo:
+ await p.load_jwks()
except Exception as e:
raise Exception(
"Error while initialising OIDC provider %r" % (idp_id,)
@@ -498,10 +499,6 @@ class OidcProvider:
return await self._jwks.get()
async def _load_jwks(self) -> JWKS:
- if self._uses_userinfo:
- # We're not using jwt signing, return an empty jwk set
- return {"keys": []}
-
metadata = await self.load_metadata()
# Load the JWKS using the `jwks_uri` metadata.
@@ -663,7 +660,7 @@ class OidcProvider:
return UserInfo(resp)
- async def _parse_id_token(self, token: Token, nonce: str) -> UserInfo:
+ async def _parse_id_token(self, token: Token, nonce: str) -> CodeIDToken:
"""Return an instance of UserInfo from token's ``id_token``.
Args:
@@ -673,7 +670,7 @@ class OidcProvider:
request. This value should match the one inside the token.
Returns:
- An object representing the user.
+ The decoded claims in the ID token.
"""
metadata = await self.load_metadata()
claims_params = {
@@ -684,9 +681,6 @@ class OidcProvider:
# If we got an `access_token`, there should be an `at_hash` claim
# in the `id_token` that we can check against.
claims_params["access_token"] = token["access_token"]
- claims_cls = CodeIDToken
- else:
- claims_cls = ImplicitIDToken
alg_values = metadata.get("id_token_signing_alg_values_supported", ["RS256"])
jwt = JsonWebToken(alg_values)
@@ -703,7 +697,7 @@ class OidcProvider:
claims = jwt.decode(
id_token,
key=jwk_set,
- claims_cls=claims_cls,
+ claims_cls=CodeIDToken,
claims_options=claim_options,
claims_params=claims_params,
)
@@ -713,7 +707,7 @@ class OidcProvider:
claims = jwt.decode(
id_token,
key=jwk_set,
- claims_cls=claims_cls,
+ claims_cls=CodeIDToken,
claims_options=claim_options,
claims_params=claims_params,
)
@@ -721,7 +715,8 @@ class OidcProvider:
logger.debug("Decoded id_token JWT %r; validating", claims)
claims.validate(leeway=120) # allows 2 min of clock skew
- return UserInfo(claims)
+
+ return claims
async def handle_redirect_request(
self,
@@ -837,8 +832,22 @@ class OidcProvider:
logger.debug("Successfully obtained OAuth2 token data: %r", token)
- # Now that we have a token, get the userinfo, either by decoding the
- # `id_token` or by fetching the `userinfo_endpoint`.
+ # If there is an id_token, it should be validated, regardless of the
+ # userinfo endpoint is used or not.
+ if token.get("id_token") is not None:
+ try:
+ id_token = await self._parse_id_token(token, nonce=session_data.nonce)
+ sid = id_token.get("sid")
+ except Exception as e:
+ logger.exception("Invalid id_token")
+ self._sso_handler.render_error(request, "invalid_token", str(e))
+ return
+ else:
+ id_token = None
+ sid = None
+
+ # Now that we have a token, get the userinfo either from the `id_token`
+ # claims or by fetching the `userinfo_endpoint`.
if self._uses_userinfo:
try:
userinfo = await self._fetch_userinfo(token)
@@ -846,13 +855,14 @@ class OidcProvider:
logger.exception("Could not fetch userinfo")
self._sso_handler.render_error(request, "fetch_error", str(e))
return
+ elif id_token is not None:
+ userinfo = UserInfo(id_token)
else:
- try:
- userinfo = await self._parse_id_token(token, nonce=session_data.nonce)
- except Exception as e:
- logger.exception("Invalid id_token")
- self._sso_handler.render_error(request, "invalid_token", str(e))
- return
+ logger.error("Missing id_token in token response")
+ self._sso_handler.render_error(
+ request, "invalid_token", "Missing id_token in token response"
+ )
+ return
# first check if we're doing a UIA
if session_data.ui_auth_session_id:
@@ -884,7 +894,7 @@ class OidcProvider:
# Call the mapper to register/login the user
try:
await self._complete_oidc_login(
- userinfo, token, request, session_data.client_redirect_url
+ userinfo, token, request, session_data.client_redirect_url, sid
)
except MappingException as e:
logger.exception("Could not map user")
@@ -896,6 +906,7 @@ class OidcProvider:
token: Token,
request: SynapseRequest,
client_redirect_url: str,
+ sid: Optional[str],
) -> None:
"""Given a UserInfo response, complete the login flow
@@ -1008,6 +1019,7 @@ class OidcProvider:
oidc_response_to_user_attributes,
grandfather_existing_users,
extra_attributes,
+ auth_provider_session_id=sid,
)
def _remote_id_from_userinfo(self, userinfo: UserInfo) -> str:
diff --git a/synapse/handlers/pagination.py b/synapse/handlers/pagination.py
index cd64142735..4f42438053 100644
--- a/synapse/handlers/pagination.py
+++ b/synapse/handlers/pagination.py
@@ -406,9 +406,6 @@ class PaginationHandler:
force: set true to skip checking for joined users.
"""
with await self.pagination_lock.write(room_id):
- # check we know about the room
- await self.store.get_room_version_id(room_id)
-
# first check that we have no users in this room
if not force:
joined = await self.store.is_host_joined(room_id, self._server_name)
diff --git a/synapse/handlers/presence.py b/synapse/handlers/presence.py
index 3df872c578..454d06c973 100644
--- a/synapse/handlers/presence.py
+++ b/synapse/handlers/presence.py
@@ -421,7 +421,7 @@ class WorkerPresenceHandler(BasePresenceHandler):
self._on_shutdown,
)
- def _on_shutdown(self) -> None:
+ async def _on_shutdown(self) -> None:
if self._presence_enabled:
self.hs.get_tcp_replication().send_command(
ClearUserSyncsCommand(self.instance_id)
diff --git a/synapse/handlers/register.py b/synapse/handlers/register.py
index 24ca11b924..f08a516a75 100644
--- a/synapse/handlers/register.py
+++ b/synapse/handlers/register.py
@@ -1,4 +1,5 @@
# Copyright 2014 - 2016 OpenMarket Ltd
+# Copyright 2021 The Matrix.org Foundation C.I.C.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
@@ -116,6 +117,9 @@ class RegistrationHandler:
self.pusher_pool = hs.get_pusherpool()
self.session_lifetime = hs.config.registration.session_lifetime
+ self.nonrefreshable_access_token_lifetime = (
+ hs.config.registration.nonrefreshable_access_token_lifetime
+ )
self.refreshable_access_token_lifetime = (
hs.config.registration.refreshable_access_token_lifetime
)
@@ -742,6 +746,7 @@ class RegistrationHandler:
is_appservice_ghost: bool = False,
auth_provider_id: Optional[str] = None,
should_issue_refresh_token: bool = False,
+ auth_provider_session_id: Optional[str] = None,
) -> Tuple[str, str, Optional[int], Optional[str]]:
"""Register a device for a user and generate an access token.
@@ -752,9 +757,9 @@ class RegistrationHandler:
device_id: The device ID to check, or None to generate a new one.
initial_display_name: An optional display name for the device.
is_guest: Whether this is a guest account
- auth_provider_id: The SSO IdP the user used, if any (just used for the
- prometheus metrics).
+ auth_provider_id: The SSO IdP the user used, if any.
should_issue_refresh_token: Whether it should also issue a refresh token
+ auth_provider_session_id: The session ID received during login from the SSO IdP.
Returns:
Tuple of device ID, access token, access token expiration time and refresh token
"""
@@ -765,6 +770,8 @@ class RegistrationHandler:
is_guest=is_guest,
is_appservice_ghost=is_appservice_ghost,
should_issue_refresh_token=should_issue_refresh_token,
+ auth_provider_id=auth_provider_id,
+ auth_provider_session_id=auth_provider_session_id,
)
login_counter.labels(
@@ -787,6 +794,8 @@ class RegistrationHandler:
is_guest: bool = False,
is_appservice_ghost: bool = False,
should_issue_refresh_token: bool = False,
+ auth_provider_id: Optional[str] = None,
+ auth_provider_session_id: Optional[str] = None,
) -> LoginDict:
"""Helper for register_device
@@ -794,19 +803,35 @@ class RegistrationHandler:
class and RegisterDeviceReplicationServlet.
"""
assert not self.hs.config.worker.worker_app
+ now_ms = self.clock.time_msec()
access_token_expiry = None
if self.session_lifetime is not None:
if is_guest:
raise Exception(
"session_lifetime is not currently implemented for guest access"
)
- access_token_expiry = self.clock.time_msec() + self.session_lifetime
+ access_token_expiry = now_ms + self.session_lifetime
+
+ if self.nonrefreshable_access_token_lifetime is not None:
+ if access_token_expiry is not None:
+ # Don't allow the non-refreshable access token to outlive the
+ # session.
+ access_token_expiry = min(
+ now_ms + self.nonrefreshable_access_token_lifetime,
+ access_token_expiry,
+ )
+ else:
+ access_token_expiry = now_ms + self.nonrefreshable_access_token_lifetime
refresh_token = None
refresh_token_id = None
registered_device_id = await self.device_handler.check_device_registered(
- user_id, device_id, initial_display_name
+ user_id,
+ device_id,
+ initial_display_name,
+ auth_provider_id=auth_provider_id,
+ auth_provider_session_id=auth_provider_session_id,
)
if is_guest:
assert access_token_expiry is None
@@ -818,8 +843,6 @@ class RegistrationHandler:
# that this value is set before setting this flag).
assert self.refreshable_access_token_lifetime is not None
- now_ms = self.clock.time_msec()
-
# Set the expiry time of the refreshable access token
access_token_expiry = now_ms + self.refreshable_access_token_lifetime
diff --git a/synapse/handlers/room.py b/synapse/handlers/room.py
index 88053f9869..ead2198e14 100644
--- a/synapse/handlers/room.py
+++ b/synapse/handlers/room.py
@@ -46,6 +46,7 @@ from synapse.api.constants import (
from synapse.api.errors import (
AuthError,
Codes,
+ HttpResponseException,
LimitExceededError,
NotFoundError,
StoreError,
@@ -56,6 +57,8 @@ from synapse.api.room_versions import KNOWN_ROOM_VERSIONS, RoomVersion
from synapse.event_auth import validate_event_for_room_version
from synapse.events import EventBase
from synapse.events.utils import copy_power_levels_contents
+from synapse.federation.federation_client import InvalidResponseError
+from synapse.handlers.federation import get_domains_from_state
from synapse.rest.admin._base import assert_user_is_admin
from synapse.storage.state import StateFilter
from synapse.streams import EventSource
@@ -1220,6 +1223,147 @@ class RoomContextHandler:
return results
+class TimestampLookupHandler:
+ def __init__(self, hs: "HomeServer"):
+ self.server_name = hs.hostname
+ self.store = hs.get_datastore()
+ self.state_handler = hs.get_state_handler()
+ self.federation_client = hs.get_federation_client()
+
+ async def get_event_for_timestamp(
+ self,
+ requester: Requester,
+ room_id: str,
+ timestamp: int,
+ direction: str,
+ ) -> Tuple[str, int]:
+ """Find the closest event to the given timestamp in the given direction.
+ If we can't find an event locally or the event we have locally is next to a gap,
+ it will ask other federated homeservers for an event.
+
+ Args:
+ requester: The user making the request according to the access token
+ room_id: Room to fetch the event from
+ timestamp: The point in time (inclusive) we should navigate from in
+ the given direction to find the closest event.
+ direction: ["f"|"b"] to indicate whether we should navigate forward
+ or backward from the given timestamp to find the closest event.
+
+ Returns:
+ A tuple containing the `event_id` closest to the given timestamp in
+ the given direction and the `origin_server_ts`.
+
+ Raises:
+ SynapseError if unable to find any event locally in the given direction
+ """
+
+ local_event_id = await self.store.get_event_id_for_timestamp(
+ room_id, timestamp, direction
+ )
+ logger.debug(
+ "get_event_for_timestamp: locally, we found event_id=%s closest to timestamp=%s",
+ local_event_id,
+ timestamp,
+ )
+
+ # Check for gaps in the history where events could be hiding in between
+ # the timestamp given and the event we were able to find locally
+ is_event_next_to_backward_gap = False
+ is_event_next_to_forward_gap = False
+ if local_event_id:
+ local_event = await self.store.get_event(
+ local_event_id, allow_none=False, allow_rejected=False
+ )
+
+ if direction == "f":
+ # We only need to check for a backward gap if we're looking forwards
+ # to ensure there is nothing in between.
+ is_event_next_to_backward_gap = (
+ await self.store.is_event_next_to_backward_gap(local_event)
+ )
+ elif direction == "b":
+ # We only need to check for a forward gap if we're looking backwards
+ # to ensure there is nothing in between
+ is_event_next_to_forward_gap = (
+ await self.store.is_event_next_to_forward_gap(local_event)
+ )
+
+ # If we found a gap, we should probably ask another homeserver first
+ # about more history in between
+ if (
+ not local_event_id
+ or is_event_next_to_backward_gap
+ or is_event_next_to_forward_gap
+ ):
+ logger.debug(
+ "get_event_for_timestamp: locally, we found event_id=%s closest to timestamp=%s which is next to a gap in event history so we're asking other homeservers first",
+ local_event_id,
+ timestamp,
+ )
+
+ # Find other homeservers from the given state in the room
+ curr_state = await self.state_handler.get_current_state(room_id)
+ curr_domains = get_domains_from_state(curr_state)
+ likely_domains = [
+ domain for domain, depth in curr_domains if domain != self.server_name
+ ]
+
+ # Loop through each homeserver candidate until we get a succesful response
+ for domain in likely_domains:
+ try:
+ remote_response = await self.federation_client.timestamp_to_event(
+ domain, room_id, timestamp, direction
+ )
+ logger.debug(
+ "get_event_for_timestamp: response from domain(%s)=%s",
+ domain,
+ remote_response,
+ )
+
+ # TODO: Do we want to persist this as an extremity?
+ # TODO: I think ideally, we would try to backfill from
+ # this event and run this whole
+ # `get_event_for_timestamp` function again to make sure
+ # they didn't give us an event from their gappy history.
+ remote_event_id = remote_response.event_id
+ origin_server_ts = remote_response.origin_server_ts
+
+ # Only return the remote event if it's closer than the local event
+ if not local_event or (
+ abs(origin_server_ts - timestamp)
+ < abs(local_event.origin_server_ts - timestamp)
+ ):
+ return remote_event_id, origin_server_ts
+ except (HttpResponseException, InvalidResponseError) as ex:
+ # Let's not put a high priority on some other homeserver
+ # failing to respond or giving a random response
+ logger.debug(
+ "Failed to fetch /timestamp_to_event from %s because of exception(%s) %s args=%s",
+ domain,
+ type(ex).__name__,
+ ex,
+ ex.args,
+ )
+ except Exception as ex:
+ # But we do want to see some exceptions in our code
+ logger.warning(
+ "Failed to fetch /timestamp_to_event from %s because of exception(%s) %s args=%s",
+ domain,
+ type(ex).__name__,
+ ex,
+ ex.args,
+ )
+
+ if not local_event_id:
+ raise SynapseError(
+ 404,
+ "Unable to find event from %s in direction %s" % (timestamp, direction),
+ errcode=Codes.NOT_FOUND,
+ )
+
+ return local_event_id, local_event.origin_server_ts
+
+
class RoomEventSource(EventSource[RoomStreamToken, EventBase]):
def __init__(self, hs: "HomeServer"):
self.store = hs.get_datastore()
@@ -1391,20 +1535,13 @@ class RoomShutdownHandler:
await self.store.block_room(room_id, requester_user_id)
if not await self.store.get_room(room_id):
- if block:
- # We allow you to block an unknown room.
- return {
- "kicked_users": [],
- "failed_to_kick_users": [],
- "local_aliases": [],
- "new_room_id": None,
- }
- else:
- # But if you don't want to preventatively block another room,
- # this function can't do anything useful.
- raise NotFoundError(
- "Cannot shut down room: unknown room id %s" % (room_id,)
- )
+ # if we don't know about the room, there is nothing left to do.
+ return {
+ "kicked_users": [],
+ "failed_to_kick_users": [],
+ "local_aliases": [],
+ "new_room_id": None,
+ }
if new_room_user_id is not None:
if not self.hs.is_mine_id(new_room_user_id):
diff --git a/synapse/handlers/sso.py b/synapse/handlers/sso.py
index 49fde01cf0..65c27bc64a 100644
--- a/synapse/handlers/sso.py
+++ b/synapse/handlers/sso.py
@@ -365,6 +365,7 @@ class SsoHandler:
sso_to_matrix_id_mapper: Callable[[int], Awaitable[UserAttributes]],
grandfather_existing_users: Callable[[], Awaitable[Optional[str]]],
extra_login_attributes: Optional[JsonDict] = None,
+ auth_provider_session_id: Optional[str] = None,
) -> None:
"""
Given an SSO ID, retrieve the user ID for it and possibly register the user.
@@ -415,6 +416,8 @@ class SsoHandler:
extra_login_attributes: An optional dictionary of extra
attributes to be provided to the client in the login response.
+ auth_provider_session_id: An optional session ID from the IdP.
+
Raises:
MappingException if there was a problem mapping the response to a user.
RedirectException: if the mapping provider needs to redirect the user
@@ -490,6 +493,7 @@ class SsoHandler:
client_redirect_url,
extra_login_attributes,
new_user=new_user,
+ auth_provider_session_id=auth_provider_session_id,
)
async def _call_attribute_mapper(
diff --git a/synapse/handlers/sync.py b/synapse/handlers/sync.py
index 891435c14d..f3039c3c3f 100644
--- a/synapse/handlers/sync.py
+++ b/synapse/handlers/sync.py
@@ -334,6 +334,19 @@ class SyncHandler:
full_state: bool,
cache_context: ResponseCacheContext[SyncRequestKey],
) -> SyncResult:
+ """The start of the machinery that produces a /sync response.
+
+ See https://spec.matrix.org/v1.1/client-server-api/#syncing for full details.
+
+ This method does high-level bookkeeping:
+ - tracking the kind of sync in the logging context
+ - deleting any to_device messages whose delivery has been acknowledged.
+ - deciding if we should dispatch an instant or delayed response
+ - marking the sync as being lazily loaded, if appropriate
+
+ Computing the body of the response begins in the next method,
+ `current_sync_for_user`.
+ """
if since_token is None:
sync_type = "initial_sync"
elif full_state:
@@ -363,7 +376,7 @@ class SyncHandler:
sync_config, since_token, full_state=full_state
)
else:
-
+ # Otherwise, we wait for something to happen and report it to the user.
async def current_sync_callback(
before_token: StreamToken, after_token: StreamToken
) -> SyncResult:
@@ -402,7 +415,12 @@ class SyncHandler:
since_token: Optional[StreamToken] = None,
full_state: bool = False,
) -> SyncResult:
- """Get the sync for client needed to match what the server has now."""
+ """Generates the response body of a sync result, represented as a SyncResult.
+
+ This is a wrapper around `generate_sync_result` which starts an open tracing
+ span to track the sync. See `generate_sync_result` for the next part of your
+ indoctrination.
+ """
with start_active_span("current_sync_for_user"):
log_kv({"since_token": since_token})
sync_result = await self.generate_sync_result(
@@ -560,7 +578,7 @@ class SyncHandler:
# that have happened since `since_key` up to `end_key`, so we
# can just use `get_room_events_stream_for_room`.
# Otherwise, we want to return the last N events in the room
- # in toplogical ordering.
+ # in topological ordering.
if since_key:
events, end_key = await self.store.get_room_events_stream_for_room(
room_id,
@@ -1042,7 +1060,18 @@ class SyncHandler:
since_token: Optional[StreamToken] = None,
full_state: bool = False,
) -> SyncResult:
- """Generates a sync result."""
+ """Generates the response body of a sync result.
+
+ This is represented by a `SyncResult` struct, which is built from small pieces
+ using a `SyncResultBuilder`. See also
+ https://spec.matrix.org/v1.1/client-server-api/#get_matrixclientv3sync
+ the `sync_result_builder` is passed as a mutable ("inout") parameter to various
+ helper functions. These retrieve and process the data which forms the sync body,
+ often writing to the `sync_result_builder` to store their output.
+
+ At the end, we transfer data from the `sync_result_builder` to a new `SyncResult`
+ instance to signify that the sync calculation is complete.
+ """
# NB: The now_token gets changed by some of the generate_sync_* methods,
# this is due to some of the underlying streams not supporting the ability
# to query up to a given point.
@@ -1344,14 +1373,22 @@ class SyncHandler:
async def _generate_sync_entry_for_account_data(
self, sync_result_builder: "SyncResultBuilder"
) -> Dict[str, Dict[str, JsonDict]]:
- """Generates the account data portion of the sync response. Populates
- `sync_result_builder` with the result.
+ """Generates the account data portion of the sync response.
+
+ Account data (called "Client Config" in the spec) can be set either globally
+ or for a specific room. Account data consists of a list of events which
+ accumulate state, much like a room.
+
+ This function retrieves global and per-room account data. The former is written
+ to the given `sync_result_builder`. The latter is returned directly, to be
+ later written to the `sync_result_builder` on a room-by-room basis.
Args:
sync_result_builder
Returns:
- A dictionary containing the per room account data.
+ A dictionary whose keys (room ids) map to the per room account data for that
+ room.
"""
sync_config = sync_result_builder.sync_config
user_id = sync_result_builder.sync_config.user.to_string()
@@ -1359,7 +1396,7 @@ class SyncHandler:
if since_token and not sync_result_builder.full_state:
(
- account_data,
+ global_account_data,
account_data_by_room,
) = await self.store.get_updated_account_data_for_user(
user_id, since_token.account_data_key
@@ -1370,23 +1407,23 @@ class SyncHandler:
)
if push_rules_changed:
- account_data["m.push_rules"] = await self.push_rules_for_user(
+ global_account_data["m.push_rules"] = await self.push_rules_for_user(
sync_config.user
)
else:
(
- account_data,
+ global_account_data,
account_data_by_room,
) = await self.store.get_account_data_for_user(sync_config.user.to_string())
- account_data["m.push_rules"] = await self.push_rules_for_user(
+ global_account_data["m.push_rules"] = await self.push_rules_for_user(
sync_config.user
)
account_data_for_user = await sync_config.filter_collection.filter_account_data(
[
{"type": account_data_type, "content": content}
- for account_data_type, content in account_data.items()
+ for account_data_type, content in global_account_data.items()
]
)
@@ -1460,18 +1497,31 @@ class SyncHandler:
"""Generates the rooms portion of the sync response. Populates the
`sync_result_builder` with the result.
+ In the response that reaches the client, rooms are divided into four categories:
+ `invite`, `join`, `knock`, `leave`. These aren't the same as the four sets of
+ room ids returned by this function.
+
Args:
sync_result_builder
account_data_by_room: Dictionary of per room account data
Returns:
- Returns a 4-tuple of
- `(newly_joined_rooms, newly_joined_or_invited_users,
- newly_left_rooms, newly_left_users)`
+ Returns a 4-tuple describing rooms the user has joined or left, and users who've
+ joined or left rooms any rooms the user is in. This gets used later in
+ `_generate_sync_entry_for_device_list`.
+
+ Its entries are:
+ - newly_joined_rooms
+ - newly_joined_or_invited_or_knocked_users
+ - newly_left_rooms
+ - newly_left_users
"""
+ since_token = sync_result_builder.since_token
+
+ # 1. Start by fetching all ephemeral events in rooms we've joined (if required).
user_id = sync_result_builder.sync_config.user.to_string()
block_all_room_ephemeral = (
- sync_result_builder.since_token is None
+ since_token is None
and sync_result_builder.sync_config.filter_collection.blocks_all_room_ephemeral()
)
@@ -1485,9 +1535,8 @@ class SyncHandler:
)
sync_result_builder.now_token = now_token
- # We check up front if anything has changed, if it hasn't then there is
+ # 2. We check up front if anything has changed, if it hasn't then there is
# no point in going further.
- since_token = sync_result_builder.since_token
if not sync_result_builder.full_state:
if since_token and not ephemeral_by_room and not account_data_by_room:
have_changed = await self._have_rooms_changed(sync_result_builder)
@@ -1500,20 +1549,8 @@ class SyncHandler:
logger.debug("no-oping sync")
return set(), set(), set(), set()
- ignored_account_data = (
- await self.store.get_global_account_data_by_type_for_user(
- AccountDataTypes.IGNORED_USER_LIST, user_id=user_id
- )
- )
-
- # If there is ignored users account data and it matches the proper type,
- # then use it.
- ignored_users: FrozenSet[str] = frozenset()
- if ignored_account_data:
- ignored_users_data = ignored_account_data.get("ignored_users", {})
- if isinstance(ignored_users_data, dict):
- ignored_users = frozenset(ignored_users_data.keys())
-
+ # 3. Work out which rooms need reporting in the sync response.
+ ignored_users = await self._get_ignored_users(user_id)
if since_token:
room_changes = await self._get_rooms_changed(
sync_result_builder, ignored_users
@@ -1523,7 +1560,6 @@ class SyncHandler:
)
else:
room_changes = await self._get_all_rooms(sync_result_builder, ignored_users)
-
tags_by_room = await self.store.get_tags_for_user(user_id)
log_kv({"rooms_changed": len(room_changes.room_entries)})
@@ -1534,6 +1570,8 @@ class SyncHandler:
newly_joined_rooms = room_changes.newly_joined_rooms
newly_left_rooms = room_changes.newly_left_rooms
+ # 4. We need to apply further processing to `room_entries` (rooms considered
+ # joined or archived).
async def handle_room_entries(room_entry: "RoomSyncResultBuilder") -> None:
logger.debug("Generating room entry for %s", room_entry.room_id)
await self._generate_room_entry(
@@ -1552,31 +1590,13 @@ class SyncHandler:
sync_result_builder.invited.extend(invited)
sync_result_builder.knocked.extend(knocked)
- # Now we want to get any newly joined, invited or knocking users
- newly_joined_or_invited_or_knocked_users = set()
- newly_left_users = set()
- if since_token:
- for joined_sync in sync_result_builder.joined:
- it = itertools.chain(
- joined_sync.timeline.events, joined_sync.state.values()
- )
- for event in it:
- if event.type == EventTypes.Member:
- if (
- event.membership == Membership.JOIN
- or event.membership == Membership.INVITE
- or event.membership == Membership.KNOCK
- ):
- newly_joined_or_invited_or_knocked_users.add(
- event.state_key
- )
- else:
- prev_content = event.unsigned.get("prev_content", {})
- prev_membership = prev_content.get("membership", None)
- if prev_membership == Membership.JOIN:
- newly_left_users.add(event.state_key)
-
- newly_left_users -= newly_joined_or_invited_or_knocked_users
+ # 5. Work out which users have joined or left rooms we're in. We use this
+ # to build the device_list part of the sync response in
+ # `_generate_sync_entry_for_device_list`.
+ (
+ newly_joined_or_invited_or_knocked_users,
+ newly_left_users,
+ ) = sync_result_builder.calculate_user_changes()
return (
set(newly_joined_rooms),
@@ -1585,11 +1605,36 @@ class SyncHandler:
newly_left_users,
)
+ async def _get_ignored_users(self, user_id: str) -> FrozenSet[str]:
+ """Retrieve the users ignored by the given user from their global account_data.
+
+ Returns an empty set if
+ - there is no global account_data entry for ignored_users
+ - there is such an entry, but it's not a JSON object.
+ """
+ # TODO: Can we `SELECT ignored_user_id FROM ignored_users WHERE ignorer_user_id=?;` instead?
+ ignored_account_data = (
+ await self.store.get_global_account_data_by_type_for_user(
+ AccountDataTypes.IGNORED_USER_LIST, user_id=user_id
+ )
+ )
+
+ # If there is ignored users account data and it matches the proper type,
+ # then use it.
+ ignored_users: FrozenSet[str] = frozenset()
+ if ignored_account_data:
+ ignored_users_data = ignored_account_data.get("ignored_users", {})
+ if isinstance(ignored_users_data, dict):
+ ignored_users = frozenset(ignored_users_data.keys())
+ return ignored_users
+
async def _have_rooms_changed(
self, sync_result_builder: "SyncResultBuilder"
) -> bool:
"""Returns whether there may be any new events that should be sent down
the sync. Returns True if there are.
+
+ Does not modify the `sync_result_builder`.
"""
user_id = sync_result_builder.sync_config.user.to_string()
since_token = sync_result_builder.since_token
@@ -1597,12 +1642,13 @@ class SyncHandler:
assert since_token
- # Get a list of membership change events that have happened.
- rooms_changed = await self.store.get_membership_changes_for_user(
+ # Get a list of membership change events that have happened to the user
+ # requesting the sync.
+ membership_changes = await self.store.get_membership_changes_for_user(
user_id, since_token.room_key, now_token.room_key
)
- if rooms_changed:
+ if membership_changes:
return True
stream_id = since_token.room_key.stream
@@ -1614,7 +1660,25 @@ class SyncHandler:
async def _get_rooms_changed(
self, sync_result_builder: "SyncResultBuilder", ignored_users: FrozenSet[str]
) -> _RoomChanges:
- """Gets the the changes that have happened since the last sync."""
+ """Determine the changes in rooms to report to the user.
+
+ Ideally, we want to report all events whose stream ordering `s` lies in the
+ range `since_token < s <= now_token`, where the two tokens are read from the
+ sync_result_builder.
+
+ If there are too many events in that range to report, things get complicated.
+ In this situation we return a truncated list of the most recent events, and
+ indicate in the response that there is a "gap" of omitted events. Additionally:
+
+ - we include a "state_delta", to describe the changes in state over the gap,
+ - we include all membership events applying to the user making the request,
+ even those in the gap.
+
+ See the spec for the rationale:
+ https://spec.matrix.org/v1.1/client-server-api/#syncing
+
+ The sync_result_builder is not modified by this function.
+ """
user_id = sync_result_builder.sync_config.user.to_string()
since_token = sync_result_builder.since_token
now_token = sync_result_builder.now_token
@@ -1622,21 +1686,36 @@ class SyncHandler:
assert since_token
- # Get a list of membership change events that have happened.
- rooms_changed = await self.store.get_membership_changes_for_user(
+ # The spec
+ # https://spec.matrix.org/v1.1/client-server-api/#get_matrixclientv3sync
+ # notes that membership events need special consideration:
+ #
+ # > When a sync is limited, the server MUST return membership events for events
+ # > in the gap (between since and the start of the returned timeline), regardless
+ # > as to whether or not they are redundant.
+ #
+ # We fetch such events here, but we only seem to use them for categorising rooms
+ # as newly joined, newly left, invited or knocked.
+ # TODO: we've already called this function and ran this query in
+ # _have_rooms_changed. We could keep the results in memory to avoid a
+ # second query, at the cost of more complicated source code.
+ membership_change_events = await self.store.get_membership_changes_for_user(
user_id, since_token.room_key, now_token.room_key
)
mem_change_events_by_room_id: Dict[str, List[EventBase]] = {}
- for event in rooms_changed:
+ for event in membership_change_events:
mem_change_events_by_room_id.setdefault(event.room_id, []).append(event)
- newly_joined_rooms = []
- newly_left_rooms = []
- room_entries = []
- invited = []
- knocked = []
+ newly_joined_rooms: List[str] = []
+ newly_left_rooms: List[str] = []
+ room_entries: List[RoomSyncResultBuilder] = []
+ invited: List[InvitedSyncResult] = []
+ knocked: List[KnockedSyncResult] = []
for room_id, events in mem_change_events_by_room_id.items():
+ # The body of this loop will add this room to at least one of the five lists
+ # above. Things get messy if you've e.g. joined, left, joined then left the
+ # room all in the same sync period.
logger.debug(
"Membership changes in %s: [%s]",
room_id,
@@ -1691,6 +1770,7 @@ class SyncHandler:
if not non_joins:
continue
+ last_non_join = non_joins[-1]
# Check if we have left the room. This can either be because we were
# joined before *or* that we since joined and then left.
@@ -1712,18 +1792,18 @@ class SyncHandler:
newly_left_rooms.append(room_id)
# Only bother if we're still currently invited
- should_invite = non_joins[-1].membership == Membership.INVITE
+ should_invite = last_non_join.membership == Membership.INVITE
if should_invite:
- if event.sender not in ignored_users:
- invite_room_sync = InvitedSyncResult(room_id, invite=non_joins[-1])
+ if last_non_join.sender not in ignored_users:
+ invite_room_sync = InvitedSyncResult(room_id, invite=last_non_join)
if invite_room_sync:
invited.append(invite_room_sync)
# Only bother if our latest membership in the room is knock (and we haven't
# been accepted/rejected in the meantime).
- should_knock = non_joins[-1].membership == Membership.KNOCK
+ should_knock = last_non_join.membership == Membership.KNOCK
if should_knock:
- knock_room_sync = KnockedSyncResult(room_id, knock=non_joins[-1])
+ knock_room_sync = KnockedSyncResult(room_id, knock=last_non_join)
if knock_room_sync:
knocked.append(knock_room_sync)
@@ -1781,7 +1861,9 @@ class SyncHandler:
timeline_limit = sync_config.filter_collection.timeline_limit()
- # Get all events for rooms we're currently joined to.
+ # Get all events since the `from_key` in rooms we're currently joined to.
+ # If there are too many, we get the most recent events only. This leaves
+ # a "gap" in the timeline, as described by the spec for /sync.
room_to_events = await self.store.get_room_events_stream_for_rooms(
room_ids=sync_result_builder.joined_room_ids,
from_key=since_token.room_key,
@@ -1842,6 +1924,10 @@ class SyncHandler:
) -> _RoomChanges:
"""Returns entries for all rooms for the user.
+ Like `_get_rooms_changed`, but assumes the `since_token` is `None`.
+
+ This function does not modify the sync_result_builder.
+
Args:
sync_result_builder
ignored_users: Set of users ignored by user.
@@ -1853,16 +1939,9 @@ class SyncHandler:
now_token = sync_result_builder.now_token
sync_config = sync_result_builder.sync_config
- membership_list = (
- Membership.INVITE,
- Membership.KNOCK,
- Membership.JOIN,
- Membership.LEAVE,
- Membership.BAN,
- )
-
room_list = await self.store.get_rooms_for_local_user_where_membership_is(
- user_id=user_id, membership_list=membership_list
+ user_id=user_id,
+ membership_list=Membership.LIST,
)
room_entries = []
@@ -2212,8 +2291,7 @@ def _calculate_state(
# to only include membership events for the senders in the timeline.
# In practice, we can do this by removing them from the p_ids list,
# which is the list of relevant state we know we have already sent to the client.
- # see https://github.com/matrix-org/synapse/pull/2970
- # /files/efcdacad7d1b7f52f879179701c7e0d9b763511f#r204732809
+ # see https://github.com/matrix-org/synapse/pull/2970/files/efcdacad7d1b7f52f879179701c7e0d9b763511f#r204732809
if lazy_load_members:
p_ids.difference_update(
@@ -2262,6 +2340,39 @@ class SyncResultBuilder:
groups: Optional[GroupsSyncResult] = None
to_device: List[JsonDict] = attr.Factory(list)
+ def calculate_user_changes(self) -> Tuple[Set[str], Set[str]]:
+ """Work out which other users have joined or left rooms we are joined to.
+
+ This data only is only useful for an incremental sync.
+
+ The SyncResultBuilder is not modified by this function.
+ """
+ newly_joined_or_invited_or_knocked_users = set()
+ newly_left_users = set()
+ if self.since_token:
+ for joined_sync in self.joined:
+ it = itertools.chain(
+ joined_sync.timeline.events, joined_sync.state.values()
+ )
+ for event in it:
+ if event.type == EventTypes.Member:
+ if (
+ event.membership == Membership.JOIN
+ or event.membership == Membership.INVITE
+ or event.membership == Membership.KNOCK
+ ):
+ newly_joined_or_invited_or_knocked_users.add(
+ event.state_key
+ )
+ else:
+ prev_content = event.unsigned.get("prev_content", {})
+ prev_membership = prev_content.get("membership", None)
+ if prev_membership == Membership.JOIN:
+ newly_left_users.add(event.state_key)
+
+ newly_left_users -= newly_joined_or_invited_or_knocked_users
+ return newly_joined_or_invited_or_knocked_users, newly_left_users
+
@attr.s(slots=True, auto_attribs=True)
class RoomSyncResultBuilder:
diff --git a/synapse/http/servlet.py b/synapse/http/servlet.py
index 91ba93372c..6dd9b9ad03 100644
--- a/synapse/http/servlet.py
+++ b/synapse/http/servlet.py
@@ -79,6 +79,35 @@ def parse_integer(
return parse_integer_from_args(args, name, default, required)
+@overload
+def parse_integer_from_args(
+ args: Mapping[bytes, Sequence[bytes]],
+ name: str,
+ default: Optional[int] = None,
+) -> Optional[int]:
+ ...
+
+
+@overload
+def parse_integer_from_args(
+ args: Mapping[bytes, Sequence[bytes]],
+ name: str,
+ *,
+ required: Literal[True],
+) -> int:
+ ...
+
+
+@overload
+def parse_integer_from_args(
+ args: Mapping[bytes, Sequence[bytes]],
+ name: str,
+ default: Optional[int] = None,
+ required: bool = False,
+) -> Optional[int]:
+ ...
+
+
def parse_integer_from_args(
args: Mapping[bytes, Sequence[bytes]],
name: str,
diff --git a/synapse/module_api/__init__.py b/synapse/module_api/__init__.py
index a8154168be..662e60bc33 100644
--- a/synapse/module_api/__init__.py
+++ b/synapse/module_api/__init__.py
@@ -108,6 +108,7 @@ from synapse.types import (
create_requester,
)
from synapse.util import Clock
+from synapse.util.async_helpers import maybe_awaitable
from synapse.util.caches.descriptors import cached
if TYPE_CHECKING:
@@ -626,6 +627,7 @@ class ModuleApi:
user_id: str,
duration_in_ms: int = (2 * 60 * 1000),
auth_provider_id: str = "",
+ auth_provider_session_id: Optional[str] = None,
) -> str:
"""Generate a login token suitable for m.login.token authentication
@@ -643,6 +645,7 @@ class ModuleApi:
return self._hs.get_macaroon_generator().generate_short_term_login_token(
user_id,
auth_provider_id,
+ auth_provider_session_id,
duration_in_ms,
)
@@ -1012,9 +1015,7 @@ class ModuleApi:
run_as_background_process,
msec,
desc,
- f,
- *args,
- **kwargs,
+ lambda: maybe_awaitable(f(*args, **kwargs)),
)
else:
logger.warning(
diff --git a/synapse/push/emailpusher.py b/synapse/push/emailpusher.py
index cf5abdfbda..4f13c0418a 100644
--- a/synapse/push/emailpusher.py
+++ b/synapse/push/emailpusher.py
@@ -21,6 +21,8 @@ from twisted.internet.interfaces import IDelayedCall
from synapse.metrics.background_process_metrics import run_as_background_process
from synapse.push import Pusher, PusherConfig, PusherConfigException, ThrottleParams
from synapse.push.mailer import Mailer
+from synapse.push.push_types import EmailReason
+from synapse.storage.databases.main.event_push_actions import EmailPushAction
from synapse.util.threepids import validate_email
if TYPE_CHECKING:
@@ -190,7 +192,7 @@ class EmailPusher(Pusher):
# we then consider all previously outstanding notifications
# to be delivered.
- reason = {
+ reason: EmailReason = {
"room_id": push_action["room_id"],
"now": self.clock.time_msec(),
"received_at": received_at,
@@ -275,7 +277,7 @@ class EmailPusher(Pusher):
return may_send_at
async def sent_notif_update_throttle(
- self, room_id: str, notified_push_action: dict
+ self, room_id: str, notified_push_action: EmailPushAction
) -> None:
# We have sent a notification, so update the throttle accordingly.
# If the event that triggered the notif happened more than
@@ -315,7 +317,9 @@ class EmailPusher(Pusher):
self.pusher_id, room_id, self.throttle_params[room_id]
)
- async def send_notification(self, push_actions: List[dict], reason: dict) -> None:
+ async def send_notification(
+ self, push_actions: List[EmailPushAction], reason: EmailReason
+ ) -> None:
logger.info("Sending notif email for user %r", self.user_id)
await self.mailer.send_notification_mail(
diff --git a/synapse/push/httppusher.py b/synapse/push/httppusher.py
index dbf4ad7f97..3fa603ccb7 100644
--- a/synapse/push/httppusher.py
+++ b/synapse/push/httppusher.py
@@ -26,6 +26,7 @@ from synapse.events import EventBase
from synapse.logging import opentracing
from synapse.metrics.background_process_metrics import run_as_background_process
from synapse.push import Pusher, PusherConfig, PusherConfigException
+from synapse.storage.databases.main.event_push_actions import HttpPushAction
from . import push_rule_evaluator, push_tools
@@ -273,7 +274,7 @@ class HttpPusher(Pusher):
)
break
- async def _process_one(self, push_action: dict) -> bool:
+ async def _process_one(self, push_action: HttpPushAction) -> bool:
if "notify" not in push_action["actions"]:
return True
diff --git a/synapse/push/mailer.py b/synapse/push/mailer.py
index ce299ba3da..ba4f866487 100644
--- a/synapse/push/mailer.py
+++ b/synapse/push/mailer.py
@@ -14,7 +14,7 @@
import logging
import urllib.parse
-from typing import TYPE_CHECKING, Any, Dict, Iterable, List, Optional, TypeVar
+from typing import TYPE_CHECKING, Dict, Iterable, List, Optional, TypeVar
import bleach
import jinja2
@@ -28,6 +28,14 @@ from synapse.push.presentable_names import (
descriptor_from_member_events,
name_from_member_event,
)
+from synapse.push.push_types import (
+ EmailReason,
+ MessageVars,
+ NotifVars,
+ RoomVars,
+ TemplateVars,
+)
+from synapse.storage.databases.main.event_push_actions import EmailPushAction
from synapse.storage.state import StateFilter
from synapse.types import StateMap, UserID
from synapse.util.async_helpers import concurrently_execute
@@ -135,7 +143,7 @@ class Mailer:
% urllib.parse.urlencode(params)
)
- template_vars = {"link": link}
+ template_vars: TemplateVars = {"link": link}
await self.send_email(
email_address,
@@ -165,7 +173,7 @@ class Mailer:
% urllib.parse.urlencode(params)
)
- template_vars = {"link": link}
+ template_vars: TemplateVars = {"link": link}
await self.send_email(
email_address,
@@ -196,7 +204,7 @@ class Mailer:
% urllib.parse.urlencode(params)
)
- template_vars = {"link": link}
+ template_vars: TemplateVars = {"link": link}
await self.send_email(
email_address,
@@ -210,8 +218,8 @@ class Mailer:
app_id: str,
user_id: str,
email_address: str,
- push_actions: Iterable[Dict[str, Any]],
- reason: Dict[str, Any],
+ push_actions: Iterable[EmailPushAction],
+ reason: EmailReason,
) -> None:
"""
Send email regarding a user's room notifications
@@ -230,7 +238,7 @@ class Mailer:
[pa["event_id"] for pa in push_actions]
)
- notifs_by_room: Dict[str, List[Dict[str, Any]]] = {}
+ notifs_by_room: Dict[str, List[EmailPushAction]] = {}
for pa in push_actions:
notifs_by_room.setdefault(pa["room_id"], []).append(pa)
@@ -258,7 +266,7 @@ class Mailer:
# actually sort our so-called rooms_in_order list, most recent room first
rooms_in_order.sort(key=lambda r: -(notifs_by_room[r][-1]["received_ts"] or 0))
- rooms: List[Dict[str, Any]] = []
+ rooms: List[RoomVars] = []
for r in rooms_in_order:
roomvars = await self._get_room_vars(
@@ -289,7 +297,7 @@ class Mailer:
notifs_by_room, state_by_room, notif_events, reason
)
- template_vars = {
+ template_vars: TemplateVars = {
"user_display_name": user_display_name,
"unsubscribe_link": self._make_unsubscribe_link(
user_id, app_id, email_address
@@ -302,10 +310,10 @@ class Mailer:
await self.send_email(email_address, summary_text, template_vars)
async def send_email(
- self, email_address: str, subject: str, extra_template_vars: Dict[str, Any]
+ self, email_address: str, subject: str, extra_template_vars: TemplateVars
) -> None:
"""Send an email with the given information and template text"""
- template_vars = {
+ template_vars: TemplateVars = {
"app_name": self.app_name,
"server_name": self.hs.config.server.server_name,
}
@@ -327,10 +335,10 @@ class Mailer:
self,
room_id: str,
user_id: str,
- notifs: Iterable[Dict[str, Any]],
+ notifs: Iterable[EmailPushAction],
notif_events: Dict[str, EventBase],
room_state_ids: StateMap[str],
- ) -> Dict[str, Any]:
+ ) -> RoomVars:
"""
Generate the variables for notifications on a per-room basis.
@@ -356,7 +364,7 @@ class Mailer:
room_name = await calculate_room_name(self.store, room_state_ids, user_id)
- room_vars: Dict[str, Any] = {
+ room_vars: RoomVars = {
"title": room_name,
"hash": string_ordinal_total(room_id), # See sender avatar hash
"notifs": [],
@@ -417,11 +425,11 @@ class Mailer:
async def _get_notif_vars(
self,
- notif: Dict[str, Any],
+ notif: EmailPushAction,
user_id: str,
notif_event: EventBase,
room_state_ids: StateMap[str],
- ) -> Dict[str, Any]:
+ ) -> NotifVars:
"""
Generate the variables for a single notification.
@@ -442,7 +450,7 @@ class Mailer:
after_limit=CONTEXT_AFTER,
)
- ret = {
+ ret: NotifVars = {
"link": self._make_notif_link(notif),
"ts": notif["received_ts"],
"messages": [],
@@ -461,8 +469,8 @@ class Mailer:
return ret
async def _get_message_vars(
- self, notif: Dict[str, Any], event: EventBase, room_state_ids: StateMap[str]
- ) -> Optional[Dict[str, Any]]:
+ self, notif: EmailPushAction, event: EventBase, room_state_ids: StateMap[str]
+ ) -> Optional[MessageVars]:
"""
Generate the variables for a single event, if possible.
@@ -494,7 +502,9 @@ class Mailer:
if sender_state_event:
sender_name = name_from_member_event(sender_state_event)
- sender_avatar_url = sender_state_event.content.get("avatar_url")
+ sender_avatar_url: Optional[str] = sender_state_event.content.get(
+ "avatar_url"
+ )
else:
# No state could be found, fallback to the MXID.
sender_name = event.sender
@@ -504,7 +514,7 @@ class Mailer:
# sender_hash % the number of default images to choose from
sender_hash = string_ordinal_total(event.sender)
- ret = {
+ ret: MessageVars = {
"event_type": event.type,
"is_historical": event.event_id != notif["event_id"],
"id": event.event_id,
@@ -519,6 +529,8 @@ class Mailer:
return ret
msgtype = event.content.get("msgtype")
+ if not isinstance(msgtype, str):
+ msgtype = None
ret["msgtype"] = msgtype
@@ -533,7 +545,7 @@ class Mailer:
return ret
def _add_text_message_vars(
- self, messagevars: Dict[str, Any], event: EventBase
+ self, messagevars: MessageVars, event: EventBase
) -> None:
"""
Potentially add a sanitised message body to the message variables.
@@ -543,8 +555,8 @@ class Mailer:
event: The event under consideration.
"""
msgformat = event.content.get("format")
-
- messagevars["format"] = msgformat
+ if not isinstance(msgformat, str):
+ msgformat = None
formatted_body = event.content.get("formatted_body")
body = event.content.get("body")
@@ -555,7 +567,7 @@ class Mailer:
messagevars["body_text_html"] = safe_text(body)
def _add_image_message_vars(
- self, messagevars: Dict[str, Any], event: EventBase
+ self, messagevars: MessageVars, event: EventBase
) -> None:
"""
Potentially add an image URL to the message variables.
@@ -570,7 +582,7 @@ class Mailer:
async def _make_summary_text_single_room(
self,
room_id: str,
- notifs: List[Dict[str, Any]],
+ notifs: List[EmailPushAction],
room_state_ids: StateMap[str],
notif_events: Dict[str, EventBase],
user_id: str,
@@ -685,10 +697,10 @@ class Mailer:
async def _make_summary_text(
self,
- notifs_by_room: Dict[str, List[Dict[str, Any]]],
+ notifs_by_room: Dict[str, List[EmailPushAction]],
room_state_ids: Dict[str, StateMap[str]],
notif_events: Dict[str, EventBase],
- reason: Dict[str, Any],
+ reason: EmailReason,
) -> str:
"""
Make a summary text for the email when multiple rooms have notifications.
@@ -718,7 +730,7 @@ class Mailer:
async def _make_summary_text_from_member_events(
self,
room_id: str,
- notifs: List[Dict[str, Any]],
+ notifs: List[EmailPushAction],
room_state_ids: StateMap[str],
notif_events: Dict[str, EventBase],
) -> str:
@@ -805,7 +817,7 @@ class Mailer:
base_url = "https://matrix.to/#"
return "%s/%s" % (base_url, room_id)
- def _make_notif_link(self, notif: Dict[str, str]) -> str:
+ def _make_notif_link(self, notif: EmailPushAction) -> str:
"""
Generate a link to open an event in the web client.
diff --git a/synapse/push/push_types.py b/synapse/push/push_types.py
new file mode 100644
index 0000000000..8d16ab62ce
--- /dev/null
+++ b/synapse/push/push_types.py
@@ -0,0 +1,136 @@
+# Copyright 2021 The Matrix.org Foundation C.I.C.
+#
+# Licensed under the Apache License, Version 2.0 (the "License");
+# you may not use this file except in compliance with the License.
+# You may obtain a copy of the License at
+#
+# http://www.apache.org/licenses/LICENSE-2.0
+#
+# Unless required by applicable law or agreed to in writing, software
+# distributed under the License is distributed on an "AS IS" BASIS,
+# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
+# See the License for the specific language governing permissions and
+# limitations under the License.
+from typing import List, Optional
+
+from typing_extensions import TypedDict
+
+
+class EmailReason(TypedDict, total=False):
+ """
+ Information on the event that triggered the email to be sent
+
+ room_id: the ID of the room the event was sent in
+ now: timestamp in ms when the email is being sent out
+ room_name: a human-readable name for the room the event was sent in
+ received_at: the time in milliseconds at which the event was received
+ delay_before_mail_ms: the amount of time in milliseconds Synapse always waits
+ before ever emailing about a notification (to give the user a chance to respond
+ to other push or notice the window)
+ last_sent_ts: the time in milliseconds at which a notification was last sent
+ for an event in this room
+ throttle_ms: the minimum amount of time in milliseconds between two
+ notifications can be sent for this room
+ """
+
+ room_id: str
+ now: int
+ room_name: Optional[str]
+ received_at: int
+ delay_before_mail_ms: int
+ last_sent_ts: int
+ throttle_ms: int
+
+
+class MessageVars(TypedDict, total=False):
+ """
+ Details about a specific message to include in a notification
+
+ event_type: the type of the event
+ is_historical: a boolean, which is `False` if the message is the one
+ that triggered the notification, `True` otherwise
+ id: the ID of the event
+ ts: the time in milliseconds at which the event was sent
+ sender_name: the display name for the event's sender
+ sender_avatar_url: the avatar URL (as a `mxc://` URL) for the event's
+ sender
+ sender_hash: a hash of the user ID of the sender
+ msgtype: the type of the message
+ body_text_html: html representation of the message
+ body_text_plain: plaintext representation of the message
+ image_url: mxc url of an image, when "msgtype" is "m.image"
+ """
+
+ event_type: str
+ is_historical: bool
+ id: str
+ ts: int
+ sender_name: str
+ sender_avatar_url: Optional[str]
+ sender_hash: int
+ msgtype: Optional[str]
+ body_text_html: str
+ body_text_plain: str
+ image_url: str
+
+
+class NotifVars(TypedDict):
+ """
+ Details about an event we are about to include in a notification
+
+ link: a `matrix.to` link to the event
+ ts: the time in milliseconds at which the event was received
+ messages: a list of messages containing one message before the event, the
+ message in the event, and one message after the event.
+ """
+
+ link: str
+ ts: Optional[int]
+ messages: List[MessageVars]
+
+
+class RoomVars(TypedDict):
+ """
+ Represents a room containing events to include in the email.
+
+ title: a human-readable name for the room
+ hash: a hash of the ID of the room
+ invite: a boolean, which is `True` if the room is an invite the user hasn't
+ accepted yet, `False` otherwise
+ notifs: a list of events, or an empty list if `invite` is `True`.
+ link: a `matrix.to` link to the room
+ avator_url: url to the room's avator
+ """
+
+ title: Optional[str]
+ hash: int
+ invite: bool
+ notifs: List[NotifVars]
+ link: str
+ avatar_url: Optional[str]
+
+
+class TemplateVars(TypedDict, total=False):
+ """
+ Generic structure for passing to the email sender, can hold all the fields used in email templates.
+
+ app_name: name of the app/service this homeserver is associated with
+ server_name: name of our own homeserver
+ link: a link to include into the email to be sent
+ user_display_name: the display name for the user receiving the notification
+ unsubscribe_link: the link users can click to unsubscribe from email notifications
+ summary_text: a summary of the notification(s). The text used can be customised
+ by configuring the various settings in the `email.subjects` section of the
+ configuration file.
+ rooms: a list of rooms containing events to include in the email
+ reason: information on the event that triggered the email to be sent
+ """
+
+ app_name: str
+ server_name: str
+ link: str
+ user_display_name: str
+ unsubscribe_link: str
+ summary_text: str
+ rooms: List[RoomVars]
+ reason: EmailReason
diff --git a/synapse/replication/http/login.py b/synapse/replication/http/login.py
index 0db419ea57..daacc34cea 100644
--- a/synapse/replication/http/login.py
+++ b/synapse/replication/http/login.py
@@ -46,6 +46,8 @@ class RegisterDeviceReplicationServlet(ReplicationEndpoint):
is_guest,
is_appservice_ghost,
should_issue_refresh_token,
+ auth_provider_id,
+ auth_provider_session_id,
):
"""
Args:
@@ -63,6 +65,8 @@ class RegisterDeviceReplicationServlet(ReplicationEndpoint):
"is_guest": is_guest,
"is_appservice_ghost": is_appservice_ghost,
"should_issue_refresh_token": should_issue_refresh_token,
+ "auth_provider_id": auth_provider_id,
+ "auth_provider_session_id": auth_provider_session_id,
}
async def _handle_request(self, request, user_id):
@@ -73,6 +77,8 @@ class RegisterDeviceReplicationServlet(ReplicationEndpoint):
is_guest = content["is_guest"]
is_appservice_ghost = content["is_appservice_ghost"]
should_issue_refresh_token = content["should_issue_refresh_token"]
+ auth_provider_id = content["auth_provider_id"]
+ auth_provider_session_id = content["auth_provider_session_id"]
res = await self.registration_handler.register_device_inner(
user_id,
@@ -81,6 +87,8 @@ class RegisterDeviceReplicationServlet(ReplicationEndpoint):
is_guest,
is_appservice_ghost=is_appservice_ghost,
should_issue_refresh_token=should_issue_refresh_token,
+ auth_provider_id=auth_provider_id,
+ auth_provider_session_id=auth_provider_session_id,
)
return 200, res
diff --git a/synapse/rest/admin/__init__.py b/synapse/rest/admin/__init__.py
index d7621981d9..79f765548b 100644
--- a/synapse/rest/admin/__init__.py
+++ b/synapse/rest/admin/__init__.py
@@ -17,6 +17,7 @@
import logging
import platform
+from http import HTTPStatus
from typing import TYPE_CHECKING, Optional, Tuple
import synapse
@@ -39,6 +40,10 @@ from synapse.rest.admin.event_reports import (
EventReportDetailRestServlet,
EventReportsRestServlet,
)
+from synapse.rest.admin.federation import (
+ DestinationsRestServlet,
+ ListDestinationsRestServlet,
+)
from synapse.rest.admin.groups import DeleteGroupAdminRestServlet
from synapse.rest.admin.media import ListMediaInRoom, register_servlets_for_media_repo
from synapse.rest.admin.registration_tokens import (
@@ -99,7 +104,7 @@ class VersionServlet(RestServlet):
}
def on_GET(self, request: SynapseRequest) -> Tuple[int, JsonDict]:
- return 200, self.res
+ return HTTPStatus.OK, self.res
class PurgeHistoryRestServlet(RestServlet):
@@ -131,7 +136,7 @@ class PurgeHistoryRestServlet(RestServlet):
event = await self.store.get_event(event_id)
if event.room_id != room_id:
- raise SynapseError(400, "Event is for wrong room.")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Event is for wrong room.")
# RoomStreamToken expects [int] not Optional[int]
assert event.internal_metadata.stream_ordering is not None
@@ -145,7 +150,9 @@ class PurgeHistoryRestServlet(RestServlet):
ts = body["purge_up_to_ts"]
if not isinstance(ts, int):
raise SynapseError(
- 400, "purge_up_to_ts must be an int", errcode=Codes.BAD_JSON
+ HTTPStatus.BAD_REQUEST,
+ "purge_up_to_ts must be an int",
+ errcode=Codes.BAD_JSON,
)
stream_ordering = await self.store.find_first_stream_ordering_after_ts(ts)
@@ -161,7 +168,9 @@ class PurgeHistoryRestServlet(RestServlet):
stream_ordering,
)
raise SynapseError(
- 404, "there is no event to be purged", errcode=Codes.NOT_FOUND
+ HTTPStatus.NOT_FOUND,
+ "there is no event to be purged",
+ errcode=Codes.NOT_FOUND,
)
(stream, topo, _event_id) = r
token = "t%d-%d" % (topo, stream)
@@ -174,7 +183,7 @@ class PurgeHistoryRestServlet(RestServlet):
)
else:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"must specify purge_up_to_event_id or purge_up_to_ts",
errcode=Codes.BAD_JSON,
)
@@ -183,7 +192,7 @@ class PurgeHistoryRestServlet(RestServlet):
room_id, token, delete_local_events=delete_local_events
)
- return 200, {"purge_id": purge_id}
+ return HTTPStatus.OK, {"purge_id": purge_id}
class PurgeHistoryStatusRestServlet(RestServlet):
@@ -202,7 +211,7 @@ class PurgeHistoryStatusRestServlet(RestServlet):
if purge_status is None:
raise NotFoundError("purge id '%s' not found" % purge_id)
- return 200, purge_status.asdict()
+ return HTTPStatus.OK, purge_status.asdict()
########################################################################################
@@ -257,6 +266,8 @@ def register_servlets(hs: "HomeServer", http_server: HttpServer) -> None:
ListRegistrationTokensRestServlet(hs).register(http_server)
NewRegistrationTokenRestServlet(hs).register(http_server)
RegistrationTokenRestServlet(hs).register(http_server)
+ DestinationsRestServlet(hs).register(http_server)
+ ListDestinationsRestServlet(hs).register(http_server)
RemoveSpaceMemberRestServlet(hs).register(http_server)
# Some servlets only get registered for the main process.
diff --git a/synapse/rest/admin/_base.py b/synapse/rest/admin/_base.py
index d9a2f6ca15..399b205aaf 100644
--- a/synapse/rest/admin/_base.py
+++ b/synapse/rest/admin/_base.py
@@ -13,6 +13,7 @@
# limitations under the License.
import re
+from http import HTTPStatus
from typing import Iterable, Pattern
from synapse.api.auth import Auth
@@ -62,4 +63,4 @@ async def assert_user_is_admin(auth: Auth, user_id: UserID) -> None:
"""
is_admin = await auth.is_server_admin(user_id)
if not is_admin:
- raise AuthError(403, "You are not a server admin")
+ raise AuthError(HTTPStatus.FORBIDDEN, "You are not a server admin")
diff --git a/synapse/rest/admin/devices.py b/synapse/rest/admin/devices.py
index 80fbf32f17..2e5a6600d3 100644
--- a/synapse/rest/admin/devices.py
+++ b/synapse/rest/admin/devices.py
@@ -12,6 +12,7 @@
# See the License for the specific language governing permissions and
# limitations under the License.
import logging
+from http import HTTPStatus
from typing import TYPE_CHECKING, Tuple
from synapse.api.errors import NotFoundError, SynapseError
@@ -53,7 +54,7 @@ class DeviceRestServlet(RestServlet):
target_user = UserID.from_string(user_id)
if not self.hs.is_mine(target_user):
- raise SynapseError(400, "Can only lookup local users")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Can only lookup local users")
u = await self.store.get_user_by_id(target_user.to_string())
if u is None:
@@ -62,7 +63,7 @@ class DeviceRestServlet(RestServlet):
device = await self.device_handler.get_device(
target_user.to_string(), device_id
)
- return 200, device
+ return HTTPStatus.OK, device
async def on_DELETE(
self, request: SynapseRequest, user_id: str, device_id: str
@@ -71,14 +72,14 @@ class DeviceRestServlet(RestServlet):
target_user = UserID.from_string(user_id)
if not self.hs.is_mine(target_user):
- raise SynapseError(400, "Can only lookup local users")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Can only lookup local users")
u = await self.store.get_user_by_id(target_user.to_string())
if u is None:
raise NotFoundError("Unknown user")
await self.device_handler.delete_device(target_user.to_string(), device_id)
- return 200, {}
+ return HTTPStatus.OK, {}
async def on_PUT(
self, request: SynapseRequest, user_id: str, device_id: str
@@ -87,7 +88,7 @@ class DeviceRestServlet(RestServlet):
target_user = UserID.from_string(user_id)
if not self.hs.is_mine(target_user):
- raise SynapseError(400, "Can only lookup local users")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Can only lookup local users")
u = await self.store.get_user_by_id(target_user.to_string())
if u is None:
@@ -97,7 +98,7 @@ class DeviceRestServlet(RestServlet):
await self.device_handler.update_device(
target_user.to_string(), device_id, body
)
- return 200, {}
+ return HTTPStatus.OK, {}
class DevicesRestServlet(RestServlet):
@@ -124,14 +125,14 @@ class DevicesRestServlet(RestServlet):
target_user = UserID.from_string(user_id)
if not self.hs.is_mine(target_user):
- raise SynapseError(400, "Can only lookup local users")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Can only lookup local users")
u = await self.store.get_user_by_id(target_user.to_string())
if u is None:
raise NotFoundError("Unknown user")
devices = await self.device_handler.get_devices_by_user(target_user.to_string())
- return 200, {"devices": devices, "total": len(devices)}
+ return HTTPStatus.OK, {"devices": devices, "total": len(devices)}
class DeleteDevicesRestServlet(RestServlet):
@@ -155,7 +156,7 @@ class DeleteDevicesRestServlet(RestServlet):
target_user = UserID.from_string(user_id)
if not self.hs.is_mine(target_user):
- raise SynapseError(400, "Can only lookup local users")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Can only lookup local users")
u = await self.store.get_user_by_id(target_user.to_string())
if u is None:
@@ -167,4 +168,4 @@ class DeleteDevicesRestServlet(RestServlet):
await self.device_handler.delete_devices(
target_user.to_string(), body["devices"]
)
- return 200, {}
+ return HTTPStatus.OK, {}
diff --git a/synapse/rest/admin/event_reports.py b/synapse/rest/admin/event_reports.py
index bbfcaf723b..5ee8b11110 100644
--- a/synapse/rest/admin/event_reports.py
+++ b/synapse/rest/admin/event_reports.py
@@ -13,6 +13,7 @@
# limitations under the License.
import logging
+from http import HTTPStatus
from typing import TYPE_CHECKING, Tuple
from synapse.api.errors import Codes, NotFoundError, SynapseError
@@ -66,21 +67,23 @@ class EventReportsRestServlet(RestServlet):
if start < 0:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"The start parameter must be a positive integer.",
errcode=Codes.INVALID_PARAM,
)
if limit < 0:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"The limit parameter must be a positive integer.",
errcode=Codes.INVALID_PARAM,
)
if direction not in ("f", "b"):
raise SynapseError(
- 400, "Unknown direction: %s" % (direction,), errcode=Codes.INVALID_PARAM
+ HTTPStatus.BAD_REQUEST,
+ "Unknown direction: %s" % (direction,),
+ errcode=Codes.INVALID_PARAM,
)
event_reports, total = await self.store.get_event_reports_paginate(
@@ -90,7 +93,7 @@ class EventReportsRestServlet(RestServlet):
if (start + limit) < total:
ret["next_token"] = start + len(event_reports)
- return 200, ret
+ return HTTPStatus.OK, ret
class EventReportDetailRestServlet(RestServlet):
@@ -127,13 +130,17 @@ class EventReportDetailRestServlet(RestServlet):
try:
resolved_report_id = int(report_id)
except ValueError:
- raise SynapseError(400, message, errcode=Codes.INVALID_PARAM)
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, message, errcode=Codes.INVALID_PARAM
+ )
if resolved_report_id < 0:
- raise SynapseError(400, message, errcode=Codes.INVALID_PARAM)
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, message, errcode=Codes.INVALID_PARAM
+ )
ret = await self.store.get_event_report(resolved_report_id)
if not ret:
raise NotFoundError("Event report not found")
- return 200, ret
+ return HTTPStatus.OK, ret
diff --git a/synapse/rest/admin/federation.py b/synapse/rest/admin/federation.py
new file mode 100644
index 0000000000..744687be35
--- /dev/null
+++ b/synapse/rest/admin/federation.py
@@ -0,0 +1,135 @@
+# Copyright 2021 The Matrix.org Foundation C.I.C.
+#
+# Licensed under the Apache License, Version 2.0 (the "License");
+# you may not use this file except in compliance with the License.
+# You may obtain a copy of the License at
+#
+# http://www.apache.org/licenses/LICENSE-2.0
+#
+# Unless required by applicable law or agreed to in writing, software
+# distributed under the License is distributed on an "AS IS" BASIS,
+# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
+# See the License for the specific language governing permissions and
+# limitations under the License.
+import logging
+from http import HTTPStatus
+from typing import TYPE_CHECKING, Tuple
+
+from synapse.api.errors import Codes, NotFoundError, SynapseError
+from synapse.http.servlet import RestServlet, parse_integer, parse_string
+from synapse.http.site import SynapseRequest
+from synapse.rest.admin._base import admin_patterns, assert_requester_is_admin
+from synapse.storage.databases.main.transactions import DestinationSortOrder
+from synapse.types import JsonDict
+
+if TYPE_CHECKING:
+ from synapse.server import HomeServer
+
+logger = logging.getLogger(__name__)
+
+
+class ListDestinationsRestServlet(RestServlet):
+ """Get request to list all destinations.
+ This needs user to have administrator access in Synapse.
+
+ GET /_synapse/admin/v1/federation/destinations?from=0&limit=10
+
+ returns:
+ 200 OK with list of destinations if success otherwise an error.
+
+ The parameters `from` and `limit` are required only for pagination.
+ By default, a `limit` of 100 is used.
+ The parameter `destination` can be used to filter by destination.
+ The parameter `order_by` can be used to order the result.
+ """
+
+ PATTERNS = admin_patterns("/federation/destinations$")
+
+ def __init__(self, hs: "HomeServer"):
+ self._auth = hs.get_auth()
+ self._store = hs.get_datastore()
+
+ async def on_GET(self, request: SynapseRequest) -> Tuple[int, JsonDict]:
+ await assert_requester_is_admin(self._auth, request)
+
+ start = parse_integer(request, "from", default=0)
+ limit = parse_integer(request, "limit", default=100)
+
+ if start < 0:
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST,
+ "Query parameter from must be a string representing a positive integer.",
+ errcode=Codes.INVALID_PARAM,
+ )
+
+ if limit < 0:
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST,
+ "Query parameter limit must be a string representing a positive integer.",
+ errcode=Codes.INVALID_PARAM,
+ )
+
+ destination = parse_string(request, "destination")
+
+ order_by = parse_string(
+ request,
+ "order_by",
+ default=DestinationSortOrder.DESTINATION.value,
+ allowed_values=[dest.value for dest in DestinationSortOrder],
+ )
+
+ direction = parse_string(request, "dir", default="f", allowed_values=("f", "b"))
+
+ destinations, total = await self._store.get_destinations_paginate(
+ start, limit, destination, order_by, direction
+ )
+ response = {"destinations": destinations, "total": total}
+ if (start + limit) < total:
+ response["next_token"] = str(start + len(destinations))
+
+ return HTTPStatus.OK, response
+
+
+class DestinationsRestServlet(RestServlet):
+ """Get details of a destination.
+ This needs user to have administrator access in Synapse.
+
+ GET /_synapse/admin/v1/federation/destinations/<destination>
+
+ returns:
+ 200 OK with details of a destination if success otherwise an error.
+ """
+
+ PATTERNS = admin_patterns("/federation/destinations/(?P<destination>[^/]+)$")
+
+ def __init__(self, hs: "HomeServer"):
+ self._auth = hs.get_auth()
+ self._store = hs.get_datastore()
+
+ async def on_GET(
+ self, request: SynapseRequest, destination: str
+ ) -> Tuple[int, JsonDict]:
+ await assert_requester_is_admin(self._auth, request)
+
+ destination_retry_timings = await self._store.get_destination_retry_timings(
+ destination
+ )
+
+ if not destination_retry_timings:
+ raise NotFoundError("Unknown destination")
+
+ last_successful_stream_ordering = (
+ await self._store.get_destination_last_successful_stream_ordering(
+ destination
+ )
+ )
+
+ response = {
+ "destination": destination,
+ "failure_ts": destination_retry_timings.failure_ts,
+ "retry_last_ts": destination_retry_timings.retry_last_ts,
+ "retry_interval": destination_retry_timings.retry_interval,
+ "last_successful_stream_ordering": last_successful_stream_ordering,
+ }
+
+ return HTTPStatus.OK, response
diff --git a/synapse/rest/admin/groups.py b/synapse/rest/admin/groups.py
index 68a3ba3cb7..a27110388f 100644
--- a/synapse/rest/admin/groups.py
+++ b/synapse/rest/admin/groups.py
@@ -12,6 +12,7 @@
# See the License for the specific language governing permissions and
# limitations under the License.
import logging
+from http import HTTPStatus
from typing import TYPE_CHECKING, Tuple
from synapse.api.errors import SynapseError
@@ -43,7 +44,7 @@ class DeleteGroupAdminRestServlet(RestServlet):
await assert_user_is_admin(self.auth, requester.user)
if not self.is_mine_id(group_id):
- raise SynapseError(400, "Can only delete local groups")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Can only delete local groups")
await self.group_server.delete_group(group_id, requester.user.to_string())
- return 200, {}
+ return HTTPStatus.OK, {}
diff --git a/synapse/rest/admin/media.py b/synapse/rest/admin/media.py
index 30a687d234..9e23e2d8fc 100644
--- a/synapse/rest/admin/media.py
+++ b/synapse/rest/admin/media.py
@@ -14,6 +14,7 @@
# limitations under the License.
import logging
+from http import HTTPStatus
from typing import TYPE_CHECKING, Tuple
from synapse.api.errors import AuthError, Codes, NotFoundError, SynapseError
@@ -62,7 +63,7 @@ class QuarantineMediaInRoom(RestServlet):
room_id, requester.user.to_string()
)
- return 200, {"num_quarantined": num_quarantined}
+ return HTTPStatus.OK, {"num_quarantined": num_quarantined}
class QuarantineMediaByUser(RestServlet):
@@ -89,7 +90,7 @@ class QuarantineMediaByUser(RestServlet):
user_id, requester.user.to_string()
)
- return 200, {"num_quarantined": num_quarantined}
+ return HTTPStatus.OK, {"num_quarantined": num_quarantined}
class QuarantineMediaByID(RestServlet):
@@ -118,7 +119,7 @@ class QuarantineMediaByID(RestServlet):
server_name, media_id, requester.user.to_string()
)
- return 200, {}
+ return HTTPStatus.OK, {}
class UnquarantineMediaByID(RestServlet):
@@ -147,7 +148,7 @@ class UnquarantineMediaByID(RestServlet):
# Remove from quarantine this media id
await self.store.quarantine_media_by_id(server_name, media_id, None)
- return 200, {}
+ return HTTPStatus.OK, {}
class ProtectMediaByID(RestServlet):
@@ -170,7 +171,7 @@ class ProtectMediaByID(RestServlet):
# Protect this media id
await self.store.mark_local_media_as_safe(media_id, safe=True)
- return 200, {}
+ return HTTPStatus.OK, {}
class UnprotectMediaByID(RestServlet):
@@ -193,7 +194,7 @@ class UnprotectMediaByID(RestServlet):
# Unprotect this media id
await self.store.mark_local_media_as_safe(media_id, safe=False)
- return 200, {}
+ return HTTPStatus.OK, {}
class ListMediaInRoom(RestServlet):
@@ -211,11 +212,11 @@ class ListMediaInRoom(RestServlet):
requester = await self.auth.get_user_by_req(request)
is_admin = await self.auth.is_server_admin(requester.user)
if not is_admin:
- raise AuthError(403, "You are not a server admin")
+ raise AuthError(HTTPStatus.FORBIDDEN, "You are not a server admin")
local_mxcs, remote_mxcs = await self.store.get_media_mxcs_in_room(room_id)
- return 200, {"local": local_mxcs, "remote": remote_mxcs}
+ return HTTPStatus.OK, {"local": local_mxcs, "remote": remote_mxcs}
class PurgeMediaCacheRestServlet(RestServlet):
@@ -233,13 +234,13 @@ class PurgeMediaCacheRestServlet(RestServlet):
if before_ts < 0:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Query parameter before_ts must be a positive integer.",
errcode=Codes.INVALID_PARAM,
)
elif before_ts < 30000000000: # Dec 1970 in milliseconds, Aug 2920 in seconds
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Query parameter before_ts you provided is from the year 1970. "
+ "Double check that you are providing a timestamp in milliseconds.",
errcode=Codes.INVALID_PARAM,
@@ -247,7 +248,7 @@ class PurgeMediaCacheRestServlet(RestServlet):
ret = await self.media_repository.delete_old_remote_media(before_ts)
- return 200, ret
+ return HTTPStatus.OK, ret
class DeleteMediaByID(RestServlet):
@@ -267,7 +268,7 @@ class DeleteMediaByID(RestServlet):
await assert_requester_is_admin(self.auth, request)
if self.server_name != server_name:
- raise SynapseError(400, "Can only delete local media")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Can only delete local media")
if await self.store.get_local_media(media_id) is None:
raise NotFoundError("Unknown media")
@@ -277,7 +278,7 @@ class DeleteMediaByID(RestServlet):
deleted_media, total = await self.media_repository.delete_local_media_ids(
[media_id]
)
- return 200, {"deleted_media": deleted_media, "total": total}
+ return HTTPStatus.OK, {"deleted_media": deleted_media, "total": total}
class DeleteMediaByDateSize(RestServlet):
@@ -304,26 +305,26 @@ class DeleteMediaByDateSize(RestServlet):
if before_ts < 0:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Query parameter before_ts must be a positive integer.",
errcode=Codes.INVALID_PARAM,
)
elif before_ts < 30000000000: # Dec 1970 in milliseconds, Aug 2920 in seconds
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Query parameter before_ts you provided is from the year 1970. "
+ "Double check that you are providing a timestamp in milliseconds.",
errcode=Codes.INVALID_PARAM,
)
if size_gt < 0:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Query parameter size_gt must be a string representing a positive integer.",
errcode=Codes.INVALID_PARAM,
)
if self.server_name != server_name:
- raise SynapseError(400, "Can only delete local media")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Can only delete local media")
logging.info(
"Deleting local media by timestamp: %s, size larger than: %s, keep profile media: %s"
@@ -333,7 +334,7 @@ class DeleteMediaByDateSize(RestServlet):
deleted_media, total = await self.media_repository.delete_old_local_media(
before_ts, size_gt, keep_profiles
)
- return 200, {"deleted_media": deleted_media, "total": total}
+ return HTTPStatus.OK, {"deleted_media": deleted_media, "total": total}
class UserMediaRestServlet(RestServlet):
@@ -369,7 +370,7 @@ class UserMediaRestServlet(RestServlet):
await assert_requester_is_admin(self.auth, request)
if not self.is_mine(UserID.from_string(user_id)):
- raise SynapseError(400, "Can only look up local users")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Can only look up local users")
user = await self.store.get_user_by_id(user_id)
if user is None:
@@ -380,14 +381,14 @@ class UserMediaRestServlet(RestServlet):
if start < 0:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Query parameter from must be a string representing a positive integer.",
errcode=Codes.INVALID_PARAM,
)
if limit < 0:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Query parameter limit must be a string representing a positive integer.",
errcode=Codes.INVALID_PARAM,
)
@@ -425,7 +426,7 @@ class UserMediaRestServlet(RestServlet):
if (start + limit) < total:
ret["next_token"] = start + len(media)
- return 200, ret
+ return HTTPStatus.OK, ret
async def on_DELETE(
self, request: SynapseRequest, user_id: str
@@ -436,7 +437,7 @@ class UserMediaRestServlet(RestServlet):
await assert_requester_is_admin(self.auth, request)
if not self.is_mine(UserID.from_string(user_id)):
- raise SynapseError(400, "Can only look up local users")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Can only look up local users")
user = await self.store.get_user_by_id(user_id)
if user is None:
@@ -447,14 +448,14 @@ class UserMediaRestServlet(RestServlet):
if start < 0:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Query parameter from must be a string representing a positive integer.",
errcode=Codes.INVALID_PARAM,
)
if limit < 0:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Query parameter limit must be a string representing a positive integer.",
errcode=Codes.INVALID_PARAM,
)
@@ -492,7 +493,7 @@ class UserMediaRestServlet(RestServlet):
([row["media_id"] for row in media])
)
- return 200, {"deleted_media": deleted_media, "total": total}
+ return HTTPStatus.OK, {"deleted_media": deleted_media, "total": total}
def register_servlets_for_media_repo(hs: "HomeServer", http_server: HttpServer) -> None:
diff --git a/synapse/rest/admin/registration_tokens.py b/synapse/rest/admin/registration_tokens.py
index aba48f6e7b..891b98c088 100644
--- a/synapse/rest/admin/registration_tokens.py
+++ b/synapse/rest/admin/registration_tokens.py
@@ -14,6 +14,7 @@
import logging
import string
+from http import HTTPStatus
from typing import TYPE_CHECKING, Tuple
from synapse.api.errors import Codes, NotFoundError, SynapseError
@@ -77,7 +78,7 @@ class ListRegistrationTokensRestServlet(RestServlet):
await assert_requester_is_admin(self.auth, request)
valid = parse_boolean(request, "valid")
token_list = await self.store.get_registration_tokens(valid)
- return 200, {"registration_tokens": token_list}
+ return HTTPStatus.OK, {"registration_tokens": token_list}
class NewRegistrationTokenRestServlet(RestServlet):
@@ -123,16 +124,20 @@ class NewRegistrationTokenRestServlet(RestServlet):
if "token" in body:
token = body["token"]
if not isinstance(token, str):
- raise SynapseError(400, "token must be a string", Codes.INVALID_PARAM)
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST,
+ "token must be a string",
+ Codes.INVALID_PARAM,
+ )
if not (0 < len(token) <= 64):
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"token must not be empty and must not be longer than 64 characters",
Codes.INVALID_PARAM,
)
if not set(token).issubset(self.allowed_chars_set):
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"token must consist only of characters matched by the regex [A-Za-z0-9-_]",
Codes.INVALID_PARAM,
)
@@ -142,11 +147,13 @@ class NewRegistrationTokenRestServlet(RestServlet):
length = body.get("length", 16)
if not isinstance(length, int):
raise SynapseError(
- 400, "length must be an integer", Codes.INVALID_PARAM
+ HTTPStatus.BAD_REQUEST,
+ "length must be an integer",
+ Codes.INVALID_PARAM,
)
if not (0 < length <= 64):
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"length must be greater than zero and not greater than 64",
Codes.INVALID_PARAM,
)
@@ -162,7 +169,7 @@ class NewRegistrationTokenRestServlet(RestServlet):
or (isinstance(uses_allowed, int) and uses_allowed >= 0)
):
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"uses_allowed must be a non-negative integer or null",
Codes.INVALID_PARAM,
)
@@ -170,11 +177,15 @@ class NewRegistrationTokenRestServlet(RestServlet):
expiry_time = body.get("expiry_time", None)
if not isinstance(expiry_time, (int, type(None))):
raise SynapseError(
- 400, "expiry_time must be an integer or null", Codes.INVALID_PARAM
+ HTTPStatus.BAD_REQUEST,
+ "expiry_time must be an integer or null",
+ Codes.INVALID_PARAM,
)
if isinstance(expiry_time, int) and expiry_time < self.clock.time_msec():
raise SynapseError(
- 400, "expiry_time must not be in the past", Codes.INVALID_PARAM
+ HTTPStatus.BAD_REQUEST,
+ "expiry_time must not be in the past",
+ Codes.INVALID_PARAM,
)
created = await self.store.create_registration_token(
@@ -182,7 +193,9 @@ class NewRegistrationTokenRestServlet(RestServlet):
)
if not created:
raise SynapseError(
- 400, f"Token already exists: {token}", Codes.INVALID_PARAM
+ HTTPStatus.BAD_REQUEST,
+ f"Token already exists: {token}",
+ Codes.INVALID_PARAM,
)
resp = {
@@ -192,7 +205,7 @@ class NewRegistrationTokenRestServlet(RestServlet):
"completed": 0,
"expiry_time": expiry_time,
}
- return 200, resp
+ return HTTPStatus.OK, resp
class RegistrationTokenRestServlet(RestServlet):
@@ -261,7 +274,7 @@ class RegistrationTokenRestServlet(RestServlet):
if token_info is None:
raise NotFoundError(f"No such registration token: {token}")
- return 200, token_info
+ return HTTPStatus.OK, token_info
async def on_PUT(self, request: SynapseRequest, token: str) -> Tuple[int, JsonDict]:
"""Update a registration token."""
@@ -277,7 +290,7 @@ class RegistrationTokenRestServlet(RestServlet):
or (isinstance(uses_allowed, int) and uses_allowed >= 0)
):
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"uses_allowed must be a non-negative integer or null",
Codes.INVALID_PARAM,
)
@@ -287,11 +300,15 @@ class RegistrationTokenRestServlet(RestServlet):
expiry_time = body["expiry_time"]
if not isinstance(expiry_time, (int, type(None))):
raise SynapseError(
- 400, "expiry_time must be an integer or null", Codes.INVALID_PARAM
+ HTTPStatus.BAD_REQUEST,
+ "expiry_time must be an integer or null",
+ Codes.INVALID_PARAM,
)
if isinstance(expiry_time, int) and expiry_time < self.clock.time_msec():
raise SynapseError(
- 400, "expiry_time must not be in the past", Codes.INVALID_PARAM
+ HTTPStatus.BAD_REQUEST,
+ "expiry_time must not be in the past",
+ Codes.INVALID_PARAM,
)
new_attributes["expiry_time"] = expiry_time
@@ -307,7 +324,7 @@ class RegistrationTokenRestServlet(RestServlet):
if token_info is None:
raise NotFoundError(f"No such registration token: {token}")
- return 200, token_info
+ return HTTPStatus.OK, token_info
async def on_DELETE(
self, request: SynapseRequest, token: str
@@ -316,6 +333,6 @@ class RegistrationTokenRestServlet(RestServlet):
await assert_requester_is_admin(self.auth, request)
if await self.store.delete_registration_token(token):
- return 200, {}
+ return HTTPStatus.OK, {}
raise NotFoundError(f"No such registration token: {token}")
diff --git a/synapse/rest/admin/rooms.py b/synapse/rest/admin/rooms.py
index a89dda1ba5..829e86675a 100644
--- a/synapse/rest/admin/rooms.py
+++ b/synapse/rest/admin/rooms.py
@@ -102,10 +102,9 @@ class RoomRestV2Servlet(RestServlet):
)
if not RoomID.is_valid(room_id):
- raise SynapseError(400, "%s is not a legal room ID" % (room_id,))
-
- if not await self._store.get_room(room_id):
- raise NotFoundError("Unknown room id %s" % (room_id,))
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, "%s is not a legal room ID" % (room_id,)
+ )
delete_id = self._pagination_handler.start_shutdown_and_purge_room(
room_id=room_id,
@@ -118,7 +117,7 @@ class RoomRestV2Servlet(RestServlet):
force_purge=force_purge,
)
- return 200, {"delete_id": delete_id}
+ return HTTPStatus.OK, {"delete_id": delete_id}
class DeleteRoomStatusByRoomIdRestServlet(RestServlet):
@@ -137,7 +136,9 @@ class DeleteRoomStatusByRoomIdRestServlet(RestServlet):
await assert_requester_is_admin(self._auth, request)
if not RoomID.is_valid(room_id):
- raise SynapseError(400, "%s is not a legal room ID" % (room_id,))
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, "%s is not a legal room ID" % (room_id,)
+ )
delete_ids = self._pagination_handler.get_delete_ids_by_room(room_id)
if delete_ids is None:
@@ -153,7 +154,7 @@ class DeleteRoomStatusByRoomIdRestServlet(RestServlet):
**delete.asdict(),
}
]
- return 200, {"results": cast(JsonDict, response)}
+ return HTTPStatus.OK, {"results": cast(JsonDict, response)}
class DeleteRoomStatusByDeleteIdRestServlet(RestServlet):
@@ -175,7 +176,7 @@ class DeleteRoomStatusByDeleteIdRestServlet(RestServlet):
if delete_status is None:
raise NotFoundError("delete id '%s' not found" % delete_id)
- return 200, cast(JsonDict, delete_status.asdict())
+ return HTTPStatus.OK, cast(JsonDict, delete_status.asdict())
class ListRoomRestServlet(RestServlet):
@@ -217,7 +218,7 @@ class ListRoomRestServlet(RestServlet):
RoomSortOrder.STATE_EVENTS.value,
):
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Unknown value for order_by: %s" % (order_by,),
errcode=Codes.INVALID_PARAM,
)
@@ -225,7 +226,7 @@ class ListRoomRestServlet(RestServlet):
search_term = parse_string(request, "search_term", encoding="utf-8")
if search_term == "":
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"search_term cannot be an empty string",
errcode=Codes.INVALID_PARAM,
)
@@ -233,7 +234,9 @@ class ListRoomRestServlet(RestServlet):
direction = parse_string(request, "dir", default="f")
if direction not in ("f", "b"):
raise SynapseError(
- 400, "Unknown direction: %s" % (direction,), errcode=Codes.INVALID_PARAM
+ HTTPStatus.BAD_REQUEST,
+ "Unknown direction: %s" % (direction,),
+ errcode=Codes.INVALID_PARAM,
)
reverse_order = True if direction == "b" else False
@@ -265,7 +268,7 @@ class ListRoomRestServlet(RestServlet):
else:
response["prev_batch"] = 0
- return 200, response
+ return HTTPStatus.OK, response
class RoomRestServlet(RestServlet):
@@ -310,7 +313,7 @@ class RoomRestServlet(RestServlet):
members = await self.store.get_users_in_room(room_id)
ret["joined_local_devices"] = await self.store.count_devices_by_users(members)
- return 200, ret
+ return HTTPStatus.OK, ret
async def on_DELETE(
self, request: SynapseRequest, room_id: str
@@ -386,7 +389,7 @@ class RoomRestServlet(RestServlet):
# See https://github.com/python/mypy/issues/4976#issuecomment-579883622
# for some discussion on why this is necessary. Either way,
# `ret` is an opaque dictionary blob as far as the rest of the app cares.
- return 200, cast(JsonDict, ret)
+ return HTTPStatus.OK, cast(JsonDict, ret)
class RoomMembersRestServlet(RestServlet):
@@ -413,7 +416,7 @@ class RoomMembersRestServlet(RestServlet):
members = await self.store.get_users_in_room(room_id)
ret = {"members": members, "total": len(members)}
- return 200, ret
+ return HTTPStatus.OK, ret
class RoomStateRestServlet(RestServlet):
@@ -443,16 +446,10 @@ class RoomStateRestServlet(RestServlet):
event_ids = await self.store.get_current_state_ids(room_id)
events = await self.store.get_events(event_ids.values())
now = self.clock.time_msec()
- room_state = await self._event_serializer.serialize_events(
- events.values(),
- now,
- # We don't bother bundling aggregations in when asked for state
- # events, as clients won't use them.
- bundle_relations=False,
- )
+ room_state = await self._event_serializer.serialize_events(events.values(), now)
ret = {"state": room_state}
- return 200, ret
+ return HTTPStatus.OK, ret
class JoinRoomAliasServlet(ResolveRoomIdMixin, RestServlet):
@@ -481,7 +478,10 @@ class JoinRoomAliasServlet(ResolveRoomIdMixin, RestServlet):
target_user = UserID.from_string(content["user_id"])
if not self.hs.is_mine(target_user):
- raise SynapseError(400, "This endpoint can only be used with local users")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST,
+ "This endpoint can only be used with local users",
+ )
if not await self.admin_handler.get_user(target_user):
raise NotFoundError("User not found")
@@ -527,7 +527,7 @@ class JoinRoomAliasServlet(ResolveRoomIdMixin, RestServlet):
ratelimit=False,
)
- return 200, {"room_id": room_id}
+ return HTTPStatus.OK, {"room_id": room_id}
class MakeRoomAdminRestServlet(ResolveRoomIdMixin, RestServlet):
@@ -568,7 +568,7 @@ class MakeRoomAdminRestServlet(ResolveRoomIdMixin, RestServlet):
# Figure out which local users currently have power in the room, if any.
room_state = await self.state_handler.get_current_state(room_id)
if not room_state:
- raise SynapseError(400, "Server not in room")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Server not in room")
create_event = room_state[(EventTypes.Create, "")]
power_levels = room_state.get((EventTypes.PowerLevels, ""))
@@ -582,7 +582,9 @@ class MakeRoomAdminRestServlet(ResolveRoomIdMixin, RestServlet):
admin_users.sort(key=lambda user: user_power[user])
if not admin_users:
- raise SynapseError(400, "No local admin user in room")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, "No local admin user in room"
+ )
admin_user_id = None
@@ -599,7 +601,7 @@ class MakeRoomAdminRestServlet(ResolveRoomIdMixin, RestServlet):
if not admin_user_id:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"No local admin user in room",
)
@@ -610,7 +612,7 @@ class MakeRoomAdminRestServlet(ResolveRoomIdMixin, RestServlet):
admin_user_id = create_event.sender
if not self.is_mine_id(admin_user_id):
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"No local admin user in room",
)
@@ -639,7 +641,8 @@ class MakeRoomAdminRestServlet(ResolveRoomIdMixin, RestServlet):
except AuthError:
# The admin user we found turned out not to have enough power.
raise SynapseError(
- 400, "No local admin user in room with power to update power levels."
+ HTTPStatus.BAD_REQUEST,
+ "No local admin user in room with power to update power levels.",
)
# Now we check if the user we're granting admin rights to is already in
@@ -653,7 +656,7 @@ class MakeRoomAdminRestServlet(ResolveRoomIdMixin, RestServlet):
)
if is_joined:
- return 200, {}
+ return HTTPStatus.OK, {}
join_rules = room_state.get((EventTypes.JoinRules, ""))
is_public = False
@@ -661,7 +664,7 @@ class MakeRoomAdminRestServlet(ResolveRoomIdMixin, RestServlet):
is_public = join_rules.content.get("join_rule") == JoinRules.PUBLIC
if is_public:
- return 200, {}
+ return HTTPStatus.OK, {}
await self.room_member_handler.update_membership(
fake_requester,
@@ -670,7 +673,7 @@ class MakeRoomAdminRestServlet(ResolveRoomIdMixin, RestServlet):
action=Membership.INVITE,
)
- return 200, {}
+ return HTTPStatus.OK, {}
class ForwardExtremitiesRestServlet(ResolveRoomIdMixin, RestServlet):
@@ -702,7 +705,7 @@ class ForwardExtremitiesRestServlet(ResolveRoomIdMixin, RestServlet):
room_id, _ = await self.resolve_room_id(room_identifier)
deleted_count = await self.store.delete_forward_extremities_for_room(room_id)
- return 200, {"deleted": deleted_count}
+ return HTTPStatus.OK, {"deleted": deleted_count}
async def on_GET(
self, request: SynapseRequest, room_identifier: str
@@ -713,7 +716,7 @@ class ForwardExtremitiesRestServlet(ResolveRoomIdMixin, RestServlet):
room_id, _ = await self.resolve_room_id(room_identifier)
extremities = await self.store.get_forward_extremities_for_room(room_id)
- return 200, {"count": len(extremities), "results": extremities}
+ return HTTPStatus.OK, {"count": len(extremities), "results": extremities}
class RoomEventContextServlet(RestServlet):
@@ -762,7 +765,9 @@ class RoomEventContextServlet(RestServlet):
)
if not results:
- raise SynapseError(404, "Event not found.", errcode=Codes.NOT_FOUND)
+ raise SynapseError(
+ HTTPStatus.NOT_FOUND, "Event not found.", errcode=Codes.NOT_FOUND
+ )
time_now = self.clock.time_msec()
results["events_before"] = await self._event_serializer.serialize_events(
@@ -775,13 +780,10 @@ class RoomEventContextServlet(RestServlet):
results["events_after"], time_now
)
results["state"] = await self._event_serializer.serialize_events(
- results["state"],
- time_now,
- # No need to bundle aggregations for state events
- bundle_relations=False,
+ results["state"], time_now
)
- return 200, results
+ return HTTPStatus.OK, results
class BlockRoomRestServlet(RestServlet):
diff --git a/synapse/rest/admin/server_notice_servlet.py b/synapse/rest/admin/server_notice_servlet.py
index 19f84f33f2..b295fb078b 100644
--- a/synapse/rest/admin/server_notice_servlet.py
+++ b/synapse/rest/admin/server_notice_servlet.py
@@ -11,6 +11,7 @@
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
+from http import HTTPStatus
from typing import TYPE_CHECKING, Awaitable, Optional, Tuple
from synapse.api.constants import EventTypes
@@ -82,11 +83,15 @@ class SendServerNoticeServlet(RestServlet):
# but worker processes still need to initialise SendServerNoticeServlet (as it is part of the
# admin api).
if not self.server_notices_manager.is_enabled():
- raise SynapseError(400, "Server notices are not enabled on this server")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, "Server notices are not enabled on this server"
+ )
target_user = UserID.from_string(body["user_id"])
if not self.hs.is_mine(target_user):
- raise SynapseError(400, "Server notices can only be sent to local users")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, "Server notices can only be sent to local users"
+ )
if not await self.admin_handler.get_user(target_user):
raise NotFoundError("User not found")
@@ -99,7 +104,7 @@ class SendServerNoticeServlet(RestServlet):
txn_id=txn_id,
)
- return 200, {"event_id": event.event_id}
+ return HTTPStatus.OK, {"event_id": event.event_id}
def on_PUT(
self, request: SynapseRequest, txn_id: str
diff --git a/synapse/rest/admin/statistics.py b/synapse/rest/admin/statistics.py
index 948de94ccd..ca41fd45f2 100644
--- a/synapse/rest/admin/statistics.py
+++ b/synapse/rest/admin/statistics.py
@@ -13,6 +13,7 @@
# limitations under the License.
import logging
+from http import HTTPStatus
from typing import TYPE_CHECKING, Tuple
from synapse.api.errors import Codes, SynapseError
@@ -53,7 +54,7 @@ class UserMediaStatisticsRestServlet(RestServlet):
UserSortOrder.DISPLAYNAME.value,
):
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Unknown value for order_by: %s" % (order_by,),
errcode=Codes.INVALID_PARAM,
)
@@ -61,7 +62,7 @@ class UserMediaStatisticsRestServlet(RestServlet):
start = parse_integer(request, "from", default=0)
if start < 0:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Query parameter from must be a string representing a positive integer.",
errcode=Codes.INVALID_PARAM,
)
@@ -69,7 +70,7 @@ class UserMediaStatisticsRestServlet(RestServlet):
limit = parse_integer(request, "limit", default=100)
if limit < 0:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Query parameter limit must be a string representing a positive integer.",
errcode=Codes.INVALID_PARAM,
)
@@ -77,7 +78,7 @@ class UserMediaStatisticsRestServlet(RestServlet):
from_ts = parse_integer(request, "from_ts", default=0)
if from_ts < 0:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Query parameter from_ts must be a string representing a positive integer.",
errcode=Codes.INVALID_PARAM,
)
@@ -86,13 +87,13 @@ class UserMediaStatisticsRestServlet(RestServlet):
if until_ts is not None:
if until_ts < 0:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Query parameter until_ts must be a string representing a positive integer.",
errcode=Codes.INVALID_PARAM,
)
if until_ts <= from_ts:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Query parameter until_ts must be greater than from_ts.",
errcode=Codes.INVALID_PARAM,
)
@@ -100,7 +101,7 @@ class UserMediaStatisticsRestServlet(RestServlet):
search_term = parse_string(request, "search_term")
if search_term == "":
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Query parameter search_term cannot be an empty string.",
errcode=Codes.INVALID_PARAM,
)
@@ -108,7 +109,9 @@ class UserMediaStatisticsRestServlet(RestServlet):
direction = parse_string(request, "dir", default="f")
if direction not in ("f", "b"):
raise SynapseError(
- 400, "Unknown direction: %s" % (direction,), errcode=Codes.INVALID_PARAM
+ HTTPStatus.BAD_REQUEST,
+ "Unknown direction: %s" % (direction,),
+ errcode=Codes.INVALID_PARAM,
)
users_media, total = await self.store.get_users_media_usage_paginate(
@@ -118,4 +121,4 @@ class UserMediaStatisticsRestServlet(RestServlet):
if (start + limit) < total:
ret["next_token"] = start + len(users_media)
- return 200, ret
+ return HTTPStatus.OK, ret
diff --git a/synapse/rest/admin/users.py b/synapse/rest/admin/users.py
index ccd9a2a175..2a60b602b1 100644
--- a/synapse/rest/admin/users.py
+++ b/synapse/rest/admin/users.py
@@ -79,14 +79,14 @@ class UsersRestServletV2(RestServlet):
if start < 0:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Query parameter from must be a string representing a positive integer.",
errcode=Codes.INVALID_PARAM,
)
if limit < 0:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Query parameter limit must be a string representing a positive integer.",
errcode=Codes.INVALID_PARAM,
)
@@ -122,7 +122,7 @@ class UsersRestServletV2(RestServlet):
if (start + limit) < total:
ret["next_token"] = str(start + len(users))
- return 200, ret
+ return HTTPStatus.OK, ret
class UserRestServletV2(RestServlet):
@@ -172,14 +172,14 @@ class UserRestServletV2(RestServlet):
target_user = UserID.from_string(user_id)
if not self.hs.is_mine(target_user):
- raise SynapseError(400, "Can only look up local users")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Can only look up local users")
ret = await self.admin_handler.get_user(target_user)
if not ret:
raise NotFoundError("User not found")
- return 200, ret
+ return HTTPStatus.OK, ret
async def on_PUT(
self, request: SynapseRequest, user_id: str
@@ -191,7 +191,10 @@ class UserRestServletV2(RestServlet):
body = parse_json_object_from_request(request)
if not self.hs.is_mine(target_user):
- raise SynapseError(400, "This endpoint can only be used with local users")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST,
+ "This endpoint can only be used with local users",
+ )
user = await self.admin_handler.get_user(target_user)
user_id = target_user.to_string()
@@ -210,7 +213,7 @@ class UserRestServletV2(RestServlet):
user_type = body.get("user_type", None)
if user_type is not None and user_type not in UserTypes.ALL_USER_TYPES:
- raise SynapseError(400, "Invalid user type")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Invalid user type")
set_admin_to = body.get("admin", False)
if not isinstance(set_admin_to, bool):
@@ -223,11 +226,13 @@ class UserRestServletV2(RestServlet):
password = body.get("password", None)
if password is not None:
if not isinstance(password, str) or len(password) > 512:
- raise SynapseError(400, "Invalid password")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Invalid password")
deactivate = body.get("deactivated", False)
if not isinstance(deactivate, bool):
- raise SynapseError(400, "'deactivated' parameter is not of type boolean")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, "'deactivated' parameter is not of type boolean"
+ )
# convert List[Dict[str, str]] into List[Tuple[str, str]]
if external_ids is not None:
@@ -282,7 +287,9 @@ class UserRestServletV2(RestServlet):
user_id,
)
except ExternalIDReuseException:
- raise SynapseError(409, "External id is already in use.")
+ raise SynapseError(
+ HTTPStatus.CONFLICT, "External id is already in use."
+ )
if "avatar_url" in body and isinstance(body["avatar_url"], str):
await self.profile_handler.set_avatar_url(
@@ -293,7 +300,9 @@ class UserRestServletV2(RestServlet):
if set_admin_to != user["admin"]:
auth_user = requester.user
if target_user == auth_user and not set_admin_to:
- raise SynapseError(400, "You may not demote yourself.")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, "You may not demote yourself."
+ )
await self.store.set_server_admin(target_user, set_admin_to)
@@ -319,7 +328,8 @@ class UserRestServletV2(RestServlet):
and self.auth_handler.can_change_password()
):
raise SynapseError(
- 400, "Must provide a password to re-activate an account."
+ HTTPStatus.BAD_REQUEST,
+ "Must provide a password to re-activate an account.",
)
await self.deactivate_account_handler.activate_account(
@@ -332,7 +342,7 @@ class UserRestServletV2(RestServlet):
user = await self.admin_handler.get_user(target_user)
assert user is not None
- return 200, user
+ return HTTPStatus.OK, user
else: # create user
displayname = body.get("displayname", None)
@@ -381,7 +391,9 @@ class UserRestServletV2(RestServlet):
user_id,
)
except ExternalIDReuseException:
- raise SynapseError(409, "External id is already in use.")
+ raise SynapseError(
+ HTTPStatus.CONFLICT, "External id is already in use."
+ )
if "avatar_url" in body and isinstance(body["avatar_url"], str):
await self.profile_handler.set_avatar_url(
@@ -429,51 +441,61 @@ class UserRegisterServlet(RestServlet):
nonce = secrets.token_hex(64)
self.nonces[nonce] = int(self.reactor.seconds())
- return 200, {"nonce": nonce}
+ return HTTPStatus.OK, {"nonce": nonce}
async def on_POST(self, request: SynapseRequest) -> Tuple[int, JsonDict]:
self._clear_old_nonces()
if not self.hs.config.registration.registration_shared_secret:
- raise SynapseError(400, "Shared secret registration is not enabled")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, "Shared secret registration is not enabled"
+ )
body = parse_json_object_from_request(request)
if "nonce" not in body:
- raise SynapseError(400, "nonce must be specified", errcode=Codes.BAD_JSON)
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST,
+ "nonce must be specified",
+ errcode=Codes.BAD_JSON,
+ )
nonce = body["nonce"]
if nonce not in self.nonces:
- raise SynapseError(400, "unrecognised nonce")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "unrecognised nonce")
# Delete the nonce, so it can't be reused, even if it's invalid
del self.nonces[nonce]
if "username" not in body:
raise SynapseError(
- 400, "username must be specified", errcode=Codes.BAD_JSON
+ HTTPStatus.BAD_REQUEST,
+ "username must be specified",
+ errcode=Codes.BAD_JSON,
)
else:
if not isinstance(body["username"], str) or len(body["username"]) > 512:
- raise SynapseError(400, "Invalid username")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Invalid username")
username = body["username"].encode("utf-8")
if b"\x00" in username:
- raise SynapseError(400, "Invalid username")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Invalid username")
if "password" not in body:
raise SynapseError(
- 400, "password must be specified", errcode=Codes.BAD_JSON
+ HTTPStatus.BAD_REQUEST,
+ "password must be specified",
+ errcode=Codes.BAD_JSON,
)
else:
password = body["password"]
if not isinstance(password, str) or len(password) > 512:
- raise SynapseError(400, "Invalid password")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Invalid password")
password_bytes = password.encode("utf-8")
if b"\x00" in password_bytes:
- raise SynapseError(400, "Invalid password")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Invalid password")
password_hash = await self.auth_handler.hash(password)
@@ -482,10 +504,12 @@ class UserRegisterServlet(RestServlet):
displayname = body.get("displayname", None)
if user_type is not None and user_type not in UserTypes.ALL_USER_TYPES:
- raise SynapseError(400, "Invalid user type")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Invalid user type")
if "mac" not in body:
- raise SynapseError(400, "mac must be specified", errcode=Codes.BAD_JSON)
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, "mac must be specified", errcode=Codes.BAD_JSON
+ )
got_mac = body["mac"]
@@ -507,7 +531,7 @@ class UserRegisterServlet(RestServlet):
want_mac = want_mac_builder.hexdigest()
if not hmac.compare_digest(want_mac.encode("ascii"), got_mac.encode("ascii")):
- raise SynapseError(403, "HMAC incorrect")
+ raise SynapseError(HTTPStatus.FORBIDDEN, "HMAC incorrect")
# Reuse the parts of RegisterRestServlet to reduce code duplication
from synapse.rest.client.register import RegisterRestServlet
@@ -524,7 +548,7 @@ class UserRegisterServlet(RestServlet):
)
result = await register._create_registration_details(user_id, body)
- return 200, result
+ return HTTPStatus.OK, result
class WhoisRestServlet(RestServlet):
@@ -552,11 +576,11 @@ class WhoisRestServlet(RestServlet):
await assert_user_is_admin(self.auth, auth_user)
if not self.hs.is_mine(target_user):
- raise SynapseError(400, "Can only whois a local user")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Can only whois a local user")
ret = await self.admin_handler.get_whois(target_user)
- return 200, ret
+ return HTTPStatus.OK, ret
class DeactivateAccountRestServlet(RestServlet):
@@ -575,7 +599,9 @@ class DeactivateAccountRestServlet(RestServlet):
await assert_user_is_admin(self.auth, requester.user)
if not self.is_mine(UserID.from_string(target_user_id)):
- raise SynapseError(400, "Can only deactivate local users")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, "Can only deactivate local users"
+ )
if not await self.store.get_user_by_id(target_user_id):
raise NotFoundError("User not found")
@@ -597,7 +623,7 @@ class DeactivateAccountRestServlet(RestServlet):
else:
id_server_unbind_result = "no-support"
- return 200, {"id_server_unbind_result": id_server_unbind_result}
+ return HTTPStatus.OK, {"id_server_unbind_result": id_server_unbind_result}
class AccountValidityRenewServlet(RestServlet):
@@ -620,7 +646,7 @@ class AccountValidityRenewServlet(RestServlet):
if "user_id" not in body:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"Missing property 'user_id' in the request body",
)
@@ -631,7 +657,7 @@ class AccountValidityRenewServlet(RestServlet):
)
res = {"expiration_ts": expiration_ts}
- return 200, res
+ return HTTPStatus.OK, res
class ResetPasswordRestServlet(RestServlet):
@@ -678,7 +704,7 @@ class ResetPasswordRestServlet(RestServlet):
await self._set_password_handler.set_password(
target_user_id, new_password_hash, logout_devices, requester
)
- return 200, {}
+ return HTTPStatus.OK, {}
class SearchUsersRestServlet(RestServlet):
@@ -712,16 +738,16 @@ class SearchUsersRestServlet(RestServlet):
# To allow all users to get the users list
# if not is_admin and target_user != auth_user:
- # raise AuthError(403, "You are not a server admin")
+ # raise AuthError(HTTPStatus.FORBIDDEN, "You are not a server admin")
if not self.hs.is_mine(target_user):
- raise SynapseError(400, "Can only users a local user")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Can only users a local user")
term = parse_string(request, "term", required=True)
logger.info("term: %s ", term)
ret = await self.store.search_users(term)
- return 200, ret
+ return HTTPStatus.OK, ret
class UserAdminServlet(RestServlet):
@@ -765,11 +791,14 @@ class UserAdminServlet(RestServlet):
target_user = UserID.from_string(user_id)
if not self.hs.is_mine(target_user):
- raise SynapseError(400, "Only local users can be admins of this homeserver")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST,
+ "Only local users can be admins of this homeserver",
+ )
is_admin = await self.store.is_server_admin(target_user)
- return 200, {"admin": is_admin}
+ return HTTPStatus.OK, {"admin": is_admin}
async def on_PUT(
self, request: SynapseRequest, user_id: str
@@ -785,16 +814,19 @@ class UserAdminServlet(RestServlet):
assert_params_in_dict(body, ["admin"])
if not self.hs.is_mine(target_user):
- raise SynapseError(400, "Only local users can be admins of this homeserver")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST,
+ "Only local users can be admins of this homeserver",
+ )
set_admin_to = bool(body["admin"])
if target_user == auth_user and not set_admin_to:
- raise SynapseError(400, "You may not demote yourself.")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "You may not demote yourself.")
await self.store.set_server_admin(target_user, set_admin_to)
- return 200, {}
+ return HTTPStatus.OK, {}
class UserMembershipRestServlet(RestServlet):
@@ -816,7 +848,7 @@ class UserMembershipRestServlet(RestServlet):
room_ids = await self.store.get_rooms_for_user(user_id)
ret = {"joined_rooms": list(room_ids), "total": len(room_ids)}
- return 200, ret
+ return HTTPStatus.OK, ret
class PushersRestServlet(RestServlet):
@@ -845,7 +877,7 @@ class PushersRestServlet(RestServlet):
await assert_requester_is_admin(self.auth, request)
if not self.is_mine(UserID.from_string(user_id)):
- raise SynapseError(400, "Can only look up local users")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Can only look up local users")
if not await self.store.get_user_by_id(user_id):
raise NotFoundError("User not found")
@@ -854,7 +886,10 @@ class PushersRestServlet(RestServlet):
filtered_pushers = [p.as_dict() for p in pushers]
- return 200, {"pushers": filtered_pushers, "total": len(filtered_pushers)}
+ return HTTPStatus.OK, {
+ "pushers": filtered_pushers,
+ "total": len(filtered_pushers),
+ }
class UserTokenRestServlet(RestServlet):
@@ -887,16 +922,22 @@ class UserTokenRestServlet(RestServlet):
auth_user = requester.user
if not self.hs.is_mine_id(user_id):
- raise SynapseError(400, "Only local users can be logged in as")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, "Only local users can be logged in as"
+ )
body = parse_json_object_from_request(request, allow_empty_body=True)
valid_until_ms = body.get("valid_until_ms")
if valid_until_ms and not isinstance(valid_until_ms, int):
- raise SynapseError(400, "'valid_until_ms' parameter must be an int")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, "'valid_until_ms' parameter must be an int"
+ )
if auth_user.to_string() == user_id:
- raise SynapseError(400, "Cannot use admin API to login as self")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, "Cannot use admin API to login as self"
+ )
token = await self.auth_handler.create_access_token_for_user_id(
user_id=auth_user.to_string(),
@@ -905,7 +946,7 @@ class UserTokenRestServlet(RestServlet):
puppets_user_id=user_id,
)
- return 200, {"access_token": token}
+ return HTTPStatus.OK, {"access_token": token}
class ShadowBanRestServlet(RestServlet):
@@ -947,11 +988,13 @@ class ShadowBanRestServlet(RestServlet):
await assert_requester_is_admin(self.auth, request)
if not self.hs.is_mine_id(user_id):
- raise SynapseError(400, "Only local users can be shadow-banned")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, "Only local users can be shadow-banned"
+ )
await self.store.set_shadow_banned(UserID.from_string(user_id), True)
- return 200, {}
+ return HTTPStatus.OK, {}
async def on_DELETE(
self, request: SynapseRequest, user_id: str
@@ -959,11 +1002,13 @@ class ShadowBanRestServlet(RestServlet):
await assert_requester_is_admin(self.auth, request)
if not self.hs.is_mine_id(user_id):
- raise SynapseError(400, "Only local users can be shadow-banned")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, "Only local users can be shadow-banned"
+ )
await self.store.set_shadow_banned(UserID.from_string(user_id), False)
- return 200, {}
+ return HTTPStatus.OK, {}
class RateLimitRestServlet(RestServlet):
@@ -995,7 +1040,7 @@ class RateLimitRestServlet(RestServlet):
await assert_requester_is_admin(self.auth, request)
if not self.hs.is_mine_id(user_id):
- raise SynapseError(400, "Can only look up local users")
+ raise SynapseError(HTTPStatus.BAD_REQUEST, "Can only look up local users")
if not await self.store.get_user_by_id(user_id):
raise NotFoundError("User not found")
@@ -1016,7 +1061,7 @@ class RateLimitRestServlet(RestServlet):
else:
ret = {}
- return 200, ret
+ return HTTPStatus.OK, ret
async def on_POST(
self, request: SynapseRequest, user_id: str
@@ -1024,7 +1069,9 @@ class RateLimitRestServlet(RestServlet):
await assert_requester_is_admin(self.auth, request)
if not self.hs.is_mine_id(user_id):
- raise SynapseError(400, "Only local users can be ratelimited")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, "Only local users can be ratelimited"
+ )
if not await self.store.get_user_by_id(user_id):
raise NotFoundError("User not found")
@@ -1036,14 +1083,14 @@ class RateLimitRestServlet(RestServlet):
if not isinstance(messages_per_second, int) or messages_per_second < 0:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"%r parameter must be a positive int" % (messages_per_second,),
errcode=Codes.INVALID_PARAM,
)
if not isinstance(burst_count, int) or burst_count < 0:
raise SynapseError(
- 400,
+ HTTPStatus.BAD_REQUEST,
"%r parameter must be a positive int" % (burst_count,),
errcode=Codes.INVALID_PARAM,
)
@@ -1059,7 +1106,7 @@ class RateLimitRestServlet(RestServlet):
"burst_count": ratelimit.burst_count,
}
- return 200, ret
+ return HTTPStatus.OK, ret
async def on_DELETE(
self, request: SynapseRequest, user_id: str
@@ -1067,11 +1114,13 @@ class RateLimitRestServlet(RestServlet):
await assert_requester_is_admin(self.auth, request)
if not self.hs.is_mine_id(user_id):
- raise SynapseError(400, "Only local users can be ratelimited")
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST, "Only local users can be ratelimited"
+ )
if not await self.store.get_user_by_id(user_id):
raise NotFoundError("User not found")
await self.store.delete_ratelimit_for_user(user_id)
- return 200, {}
+ return HTTPStatus.OK, {}
diff --git a/synapse/rest/client/login.py b/synapse/rest/client/login.py
index 09f378f919..f9994658c4 100644
--- a/synapse/rest/client/login.py
+++ b/synapse/rest/client/login.py
@@ -72,7 +72,7 @@ class LoginRestServlet(RestServlet):
JWT_TYPE_DEPRECATED = "m.login.jwt"
APPSERVICE_TYPE = "m.login.application_service"
APPSERVICE_TYPE_UNSTABLE = "uk.half-shot.msc2778.login.application_service"
- REFRESH_TOKEN_PARAM = "org.matrix.msc2918.refresh_token"
+ REFRESH_TOKEN_PARAM = "refresh_token"
def __init__(self, hs: "HomeServer"):
super().__init__()
@@ -90,7 +90,7 @@ class LoginRestServlet(RestServlet):
self.saml2_enabled = hs.config.saml2.saml2_enabled
self.cas_enabled = hs.config.cas.cas_enabled
self.oidc_enabled = hs.config.oidc.oidc_enabled
- self._msc2918_enabled = (
+ self._refresh_tokens_enabled = (
hs.config.registration.refreshable_access_token_lifetime is not None
)
@@ -163,17 +163,16 @@ class LoginRestServlet(RestServlet):
async def on_POST(self, request: SynapseRequest) -> Tuple[int, LoginResponse]:
login_submission = parse_json_object_from_request(request)
- if self._msc2918_enabled:
- # Check if this login should also issue a refresh token, as per MSC2918
- should_issue_refresh_token = login_submission.get(
- "org.matrix.msc2918.refresh_token", False
- )
- if not isinstance(should_issue_refresh_token, bool):
- raise SynapseError(
- 400, "`org.matrix.msc2918.refresh_token` should be true or false."
- )
- else:
- should_issue_refresh_token = False
+ # Check to see if the client requested a refresh token.
+ client_requested_refresh_token = login_submission.get(
+ LoginRestServlet.REFRESH_TOKEN_PARAM, False
+ )
+ if not isinstance(client_requested_refresh_token, bool):
+ raise SynapseError(400, "`refresh_token` should be true or false.")
+
+ should_issue_refresh_token = (
+ self._refresh_tokens_enabled and client_requested_refresh_token
+ )
try:
if login_submission["type"] in (
@@ -303,6 +302,7 @@ class LoginRestServlet(RestServlet):
ratelimit: bool = True,
auth_provider_id: Optional[str] = None,
should_issue_refresh_token: bool = False,
+ auth_provider_session_id: Optional[str] = None,
) -> LoginResponse:
"""Called when we've successfully authed the user and now need to
actually login them in (e.g. create devices). This gets called on
@@ -318,10 +318,10 @@ class LoginRestServlet(RestServlet):
create_non_existent_users: Whether to create the user if they don't
exist. Defaults to False.
ratelimit: Whether to ratelimit the login request.
- auth_provider_id: The SSO IdP the user used, if any (just used for the
- prometheus metrics).
+ auth_provider_id: The SSO IdP the user used, if any.
should_issue_refresh_token: True if this login should issue
a refresh token alongside the access token.
+ auth_provider_session_id: The session ID got during login from the SSO IdP.
Returns:
result: Dictionary of account information after successful login.
@@ -354,6 +354,7 @@ class LoginRestServlet(RestServlet):
initial_display_name,
auth_provider_id=auth_provider_id,
should_issue_refresh_token=should_issue_refresh_token,
+ auth_provider_session_id=auth_provider_session_id,
)
result = LoginResponse(
@@ -399,6 +400,7 @@ class LoginRestServlet(RestServlet):
self.auth_handler._sso_login_callback,
auth_provider_id=res.auth_provider_id,
should_issue_refresh_token=should_issue_refresh_token,
+ auth_provider_session_id=res.auth_provider_session_id,
)
async def _do_jwt_login(
@@ -460,9 +462,7 @@ def _get_auth_flow_dict_for_idp(idp: SsoIdentityProvider) -> JsonDict:
class RefreshTokenServlet(RestServlet):
- PATTERNS = client_patterns(
- "/org.matrix.msc2918.refresh_token/refresh$", releases=(), unstable=True
- )
+ PATTERNS = (re.compile("^/_matrix/client/v1/refresh$"),)
def __init__(self, hs: "HomeServer"):
self._auth_handler = hs.get_auth_handler()
@@ -513,7 +513,7 @@ class SsoRedirectServlet(RestServlet):
re.compile(
"^"
+ CLIENT_API_PREFIX
- + "/r0/login/sso/redirect/(?P<idp_id>[A-Za-z0-9_.~-]+)$"
+ + "/(r0|v3)/login/sso/redirect/(?P<idp_id>[A-Za-z0-9_.~-]+)$"
)
]
diff --git a/synapse/rest/client/register.py b/synapse/rest/client/register.py
index 11fd6cd24d..8b56c76aed 100644
--- a/synapse/rest/client/register.py
+++ b/synapse/rest/client/register.py
@@ -419,7 +419,7 @@ class RegisterRestServlet(RestServlet):
self.password_policy_handler = hs.get_password_policy_handler()
self.clock = hs.get_clock()
self._registration_enabled = self.hs.config.registration.enable_registration
- self._msc2918_enabled = (
+ self._refresh_tokens_enabled = (
hs.config.registration.refreshable_access_token_lifetime is not None
)
@@ -445,18 +445,15 @@ class RegisterRestServlet(RestServlet):
f"Do not understand membership kind: {kind}",
)
- if self._msc2918_enabled:
- # Check if this registration should also issue a refresh token, as
- # per MSC2918
- should_issue_refresh_token = body.get(
- "org.matrix.msc2918.refresh_token", False
- )
- if not isinstance(should_issue_refresh_token, bool):
- raise SynapseError(
- 400, "`org.matrix.msc2918.refresh_token` should be true or false."
- )
- else:
- should_issue_refresh_token = False
+ # Check if the clients wishes for this registration to issue a refresh
+ # token.
+ client_requested_refresh_tokens = body.get("refresh_token", False)
+ if not isinstance(client_requested_refresh_tokens, bool):
+ raise SynapseError(400, "`refresh_token` should be true or false.")
+
+ should_issue_refresh_token = (
+ self._refresh_tokens_enabled and client_requested_refresh_tokens
+ )
# Pull out the provided username and do basic sanity checks early since
# the auth layer will store these in sessions.
diff --git a/synapse/rest/client/relations.py b/synapse/rest/client/relations.py
index 45e9f1dd90..fc4e6921c5 100644
--- a/synapse/rest/client/relations.py
+++ b/synapse/rest/client/relations.py
@@ -224,18 +224,14 @@ class RelationPaginationServlet(RestServlet):
)
now = self.clock.time_msec()
- # We set bundle_relations to False when retrieving the original
- # event because we want the content before relations were applied to
- # it.
+ # Do not bundle aggregations when retrieving the original event because
+ # we want the content before relations are applied to it.
original_event = await self._event_serializer.serialize_event(
- event, now, bundle_relations=False
- )
- # Similarly, we don't allow relations to be applied to relations, so we
- # return the original relations without any aggregations on top of them
- # here.
- serialized_events = await self._event_serializer.serialize_events(
- events, now, bundle_relations=False
+ event, now, bundle_aggregations=False
)
+ # The relations returned for the requested event do include their
+ # bundled aggregations.
+ serialized_events = await self._event_serializer.serialize_events(events, now)
return_value = pagination_chunk.to_dict()
return_value["chunk"] = serialized_events
diff --git a/synapse/rest/client/room.py b/synapse/rest/client/room.py
index 73d0f7c950..f48e2e6ca2 100644
--- a/synapse/rest/client/room.py
+++ b/synapse/rest/client/room.py
@@ -716,10 +716,7 @@ class RoomEventContextServlet(RestServlet):
results["events_after"], time_now
)
results["state"] = await self._event_serializer.serialize_events(
- results["state"],
- time_now,
- # No need to bundle aggregations for state events
- bundle_relations=False,
+ results["state"], time_now
)
return 200, results
@@ -1070,6 +1067,62 @@ def register_txn_path(
)
+class TimestampLookupRestServlet(RestServlet):
+ """
+ API endpoint to fetch the `event_id` of the closest event to the given
+ timestamp (`ts` query parameter) in the given direction (`dir` query
+ parameter).
+
+ Useful for cases like jump to date so you can start paginating messages from
+ a given date in the archive.
+
+ `ts` is a timestamp in milliseconds where we will find the closest event in
+ the given direction.
+
+ `dir` can be `f` or `b` to indicate forwards and backwards in time from the
+ given timestamp.
+
+ GET /_matrix/client/unstable/org.matrix.msc3030/rooms/<roomID>/timestamp_to_event?ts=<timestamp>&dir=<direction>
+ {
+ "event_id": ...
+ }
+ """
+
+ PATTERNS = (
+ re.compile(
+ "^/_matrix/client/unstable/org.matrix.msc3030"
+ "/rooms/(?P<room_id>[^/]*)/timestamp_to_event$"
+ ),
+ )
+
+ def __init__(self, hs: "HomeServer"):
+ super().__init__()
+ self._auth = hs.get_auth()
+ self._store = hs.get_datastore()
+ self.timestamp_lookup_handler = hs.get_timestamp_lookup_handler()
+
+ async def on_GET(
+ self, request: SynapseRequest, room_id: str
+ ) -> Tuple[int, JsonDict]:
+ requester = await self._auth.get_user_by_req(request)
+ await self._auth.check_user_in_room(room_id, requester.user.to_string())
+
+ timestamp = parse_integer(request, "ts", required=True)
+ direction = parse_string(request, "dir", default="f", allowed_values=["f", "b"])
+
+ (
+ event_id,
+ origin_server_ts,
+ ) = await self.timestamp_lookup_handler.get_event_for_timestamp(
+ requester, room_id, timestamp, direction
+ )
+
+ return 200, {
+ "event_id": event_id,
+ "origin_server_ts": origin_server_ts,
+ }
+
+
class RoomSpaceSummaryRestServlet(RestServlet):
PATTERNS = (
re.compile(
@@ -1138,12 +1191,12 @@ class RoomSpaceSummaryRestServlet(RestServlet):
class RoomHierarchyRestServlet(RestServlet):
- PATTERNS = [
+ PATTERNS = (
re.compile(
"^/_matrix/client/(v1|unstable/org.matrix.msc2946)"
"/rooms/(?P<room_id>[^/]*)/hierarchy$"
),
- ]
+ )
def __init__(self, hs: "HomeServer"):
super().__init__()
@@ -1239,6 +1292,8 @@ def register_servlets(
RoomAliasListServlet(hs).register(http_server)
SearchRestServlet(hs).register(http_server)
RoomCreateRestServlet(hs).register(http_server)
+ if hs.config.experimental.msc3030_enabled:
+ TimestampLookupRestServlet(hs).register(http_server)
# Some servlets only get registered for the main process.
if not is_worker:
diff --git a/synapse/rest/client/sync.py b/synapse/rest/client/sync.py
index b6a2485732..88e4f5e063 100644
--- a/synapse/rest/client/sync.py
+++ b/synapse/rest/client/sync.py
@@ -520,9 +520,9 @@ class SyncRestServlet(RestServlet):
return self._event_serializer.serialize_events(
events,
time_now=time_now,
- # We don't bundle "live" events, as otherwise clients
- # will end up double counting annotations.
- bundle_relations=False,
+ # Don't bother to bundle aggregations if the timeline is unlimited,
+ # as clients will have all the necessary information.
+ bundle_aggregations=room.timeline.limited,
token_id=token_id,
event_format=event_formatter,
only_event_fields=only_fields,
diff --git a/synapse/rest/media/v1/filepath.py b/synapse/rest/media/v1/filepath.py
index c0e15c6513..1f6441c412 100644
--- a/synapse/rest/media/v1/filepath.py
+++ b/synapse/rest/media/v1/filepath.py
@@ -43,47 +43,75 @@ GetPathMethod = TypeVar(
)
-def _wrap_with_jail_check(func: GetPathMethod) -> GetPathMethod:
+def _wrap_with_jail_check(relative: bool) -> Callable[[GetPathMethod], GetPathMethod]:
"""Wraps a path-returning method to check that the returned path(s) do not escape
the media store directory.
+ The path-returning method may return either a single path, or a list of paths.
+
The check is not expected to ever fail, unless `func` is missing a call to
`_validate_path_component`, or `_validate_path_component` is buggy.
Args:
- func: The `MediaFilePaths` method to wrap. The method may return either a single
- path, or a list of paths. Returned paths may be either absolute or relative.
+ relative: A boolean indicating whether the wrapped method returns paths relative
+ to the media store directory.
Returns:
- The method, wrapped with a check to ensure that the returned path(s) lie within
- the media store directory. Raises a `ValueError` if the check fails.
+ A method which will wrap a path-returning method, adding a check to ensure that
+ the returned path(s) lie within the media store directory. The check will raise
+ a `ValueError` if it fails.
"""
- @functools.wraps(func)
- def _wrapped(
- self: "MediaFilePaths", *args: Any, **kwargs: Any
- ) -> Union[str, List[str]]:
- path_or_paths = func(self, *args, **kwargs)
-
- if isinstance(path_or_paths, list):
- paths_to_check = path_or_paths
- else:
- paths_to_check = [path_or_paths]
-
- for path in paths_to_check:
- # path may be an absolute or relative path, depending on the method being
- # wrapped. When "appending" an absolute path, `os.path.join` discards the
- # previous path, which is desired here.
- normalized_path = os.path.normpath(os.path.join(self.real_base_path, path))
- if (
- os.path.commonpath([normalized_path, self.real_base_path])
- != self.real_base_path
- ):
- raise ValueError(f"Invalid media store path: {path!r}")
-
- return path_or_paths
-
- return cast(GetPathMethod, _wrapped)
+ def _wrap_with_jail_check_inner(func: GetPathMethod) -> GetPathMethod:
+ @functools.wraps(func)
+ def _wrapped(
+ self: "MediaFilePaths", *args: Any, **kwargs: Any
+ ) -> Union[str, List[str]]:
+ path_or_paths = func(self, *args, **kwargs)
+
+ if isinstance(path_or_paths, list):
+ paths_to_check = path_or_paths
+ else:
+ paths_to_check = [path_or_paths]
+
+ for path in paths_to_check:
+ # Construct the path that will ultimately be used.
+ # We cannot guess whether `path` is relative to the media store
+ # directory, since the media store directory may itself be a relative
+ # path.
+ if relative:
+ path = os.path.join(self.base_path, path)
+ normalized_path = os.path.normpath(path)
+
+ # Now that `normpath` has eliminated `../`s and `./`s from the path,
+ # `os.path.commonpath` can be used to check whether it lies within the
+ # media store directory.
+ if (
+ os.path.commonpath([normalized_path, self.normalized_base_path])
+ != self.normalized_base_path
+ ):
+ # The path resolves to outside the media store directory,
+ # or `self.base_path` is `.`, which is an unlikely configuration.
+ raise ValueError(f"Invalid media store path: {path!r}")
+
+ # Note that `os.path.normpath`/`abspath` has a subtle caveat:
+ # `a/b/c/../c` will normalize to `a/b/c`, but the former refers to a
+ # different path if `a/b/c` is a symlink. That is, the check above is
+ # not perfect and may allow a certain restricted subset of untrustworthy
+ # paths through. Since the check above is secondary to the main
+ # `_validate_path_component` checks, it's less important for it to be
+ # perfect.
+ #
+ # As an alternative, `os.path.realpath` will resolve symlinks, but
+ # proves problematic if there are symlinks inside the media store.
+ # eg. if `url_store/` is symlinked to elsewhere, its canonical path
+ # won't match that of the main media store directory.
+
+ return path_or_paths
+
+ return cast(GetPathMethod, _wrapped)
+
+ return _wrap_with_jail_check_inner
ALLOWED_CHARACTERS = set(
@@ -127,9 +155,7 @@ class MediaFilePaths:
def __init__(self, primary_base_path: str):
self.base_path = primary_base_path
-
- # The media store directory, with all symlinks resolved.
- self.real_base_path = os.path.realpath(primary_base_path)
+ self.normalized_base_path = os.path.normpath(self.base_path)
# Refuse to initialize if paths cannot be validated correctly for the current
# platform.
@@ -140,7 +166,7 @@ class MediaFilePaths:
# for certain homeservers there, since ":"s aren't allowed in paths.
assert os.name == "posix"
- @_wrap_with_jail_check
+ @_wrap_with_jail_check(relative=True)
def local_media_filepath_rel(self, media_id: str) -> str:
return os.path.join(
"local_content",
@@ -151,7 +177,7 @@ class MediaFilePaths:
local_media_filepath = _wrap_in_base_path(local_media_filepath_rel)
- @_wrap_with_jail_check
+ @_wrap_with_jail_check(relative=True)
def local_media_thumbnail_rel(
self, media_id: str, width: int, height: int, content_type: str, method: str
) -> str:
@@ -167,7 +193,7 @@ class MediaFilePaths:
local_media_thumbnail = _wrap_in_base_path(local_media_thumbnail_rel)
- @_wrap_with_jail_check
+ @_wrap_with_jail_check(relative=False)
def local_media_thumbnail_dir(self, media_id: str) -> str:
"""
Retrieve the local store path of thumbnails of a given media_id
@@ -185,7 +211,7 @@ class MediaFilePaths:
_validate_path_component(media_id[4:]),
)
- @_wrap_with_jail_check
+ @_wrap_with_jail_check(relative=True)
def remote_media_filepath_rel(self, server_name: str, file_id: str) -> str:
return os.path.join(
"remote_content",
@@ -197,7 +223,7 @@ class MediaFilePaths:
remote_media_filepath = _wrap_in_base_path(remote_media_filepath_rel)
- @_wrap_with_jail_check
+ @_wrap_with_jail_check(relative=True)
def remote_media_thumbnail_rel(
self,
server_name: str,
@@ -223,7 +249,7 @@ class MediaFilePaths:
# Legacy path that was used to store thumbnails previously.
# Should be removed after some time, when most of the thumbnails are stored
# using the new path.
- @_wrap_with_jail_check
+ @_wrap_with_jail_check(relative=True)
def remote_media_thumbnail_rel_legacy(
self, server_name: str, file_id: str, width: int, height: int, content_type: str
) -> str:
@@ -238,6 +264,7 @@ class MediaFilePaths:
_validate_path_component(file_name),
)
+ @_wrap_with_jail_check(relative=False)
def remote_media_thumbnail_dir(self, server_name: str, file_id: str) -> str:
return os.path.join(
self.base_path,
@@ -248,7 +275,7 @@ class MediaFilePaths:
_validate_path_component(file_id[4:]),
)
- @_wrap_with_jail_check
+ @_wrap_with_jail_check(relative=True)
def url_cache_filepath_rel(self, media_id: str) -> str:
if NEW_FORMAT_ID_RE.match(media_id):
# Media id is of the form <DATE><RANDOM_STRING>
@@ -268,7 +295,7 @@ class MediaFilePaths:
url_cache_filepath = _wrap_in_base_path(url_cache_filepath_rel)
- @_wrap_with_jail_check
+ @_wrap_with_jail_check(relative=False)
def url_cache_filepath_dirs_to_delete(self, media_id: str) -> List[str]:
"The dirs to try and remove if we delete the media_id file"
if NEW_FORMAT_ID_RE.match(media_id):
@@ -290,7 +317,7 @@ class MediaFilePaths:
),
]
- @_wrap_with_jail_check
+ @_wrap_with_jail_check(relative=True)
def url_cache_thumbnail_rel(
self, media_id: str, width: int, height: int, content_type: str, method: str
) -> str:
@@ -318,7 +345,7 @@ class MediaFilePaths:
url_cache_thumbnail = _wrap_in_base_path(url_cache_thumbnail_rel)
- @_wrap_with_jail_check
+ @_wrap_with_jail_check(relative=True)
def url_cache_thumbnail_directory_rel(self, media_id: str) -> str:
# Media id is of the form <DATE><RANDOM_STRING>
# E.g.: 2017-09-28-fsdRDt24DS234dsf
@@ -341,7 +368,7 @@ class MediaFilePaths:
url_cache_thumbnail_directory_rel
)
- @_wrap_with_jail_check
+ @_wrap_with_jail_check(relative=False)
def url_cache_thumbnail_dirs_to_delete(self, media_id: str) -> List[str]:
"The dirs to try and remove if we delete the media_id thumbnails"
# Media id is of the form <DATE><RANDOM_STRING>
diff --git a/synapse/server.py b/synapse/server.py
index 9b7dba013c..4ba158a3e8 100644
--- a/synapse/server.py
+++ b/synapse/server.py
@@ -97,6 +97,7 @@ from synapse.handlers.room import (
RoomContextHandler,
RoomCreationHandler,
RoomShutdownHandler,
+ TimestampLookupHandler,
)
from synapse.handlers.room_batch import RoomBatchHandler
from synapse.handlers.room_list import RoomListHandler
@@ -730,6 +731,10 @@ class HomeServer(metaclass=abc.ABCMeta):
return RoomContextHandler(self)
@cache_in_self
+ def get_timestamp_lookup_handler(self) -> TimestampLookupHandler:
+ return TimestampLookupHandler(self)
+
+ @cache_in_self
def get_registration_handler(self) -> RegistrationHandler:
return RegistrationHandler(self)
diff --git a/synapse/storage/databases/main/appservice.py b/synapse/storage/databases/main/appservice.py
index baec35ee27..4a883dc166 100644
--- a/synapse/storage/databases/main/appservice.py
+++ b/synapse/storage/databases/main/appservice.py
@@ -143,7 +143,7 @@ class ApplicationServiceTransactionWorkerStore(
A list of ApplicationServices, which may be empty.
"""
results = await self.db_pool.simple_select_list(
- "application_services_state", {"state": state}, ["as_id"]
+ "application_services_state", {"state": state.value}, ["as_id"]
)
# NB: This assumes this class is linked with ApplicationServiceStore
as_list = self.get_app_services()
@@ -173,7 +173,7 @@ class ApplicationServiceTransactionWorkerStore(
desc="get_appservice_state",
)
if result:
- return result.get("state")
+ return ApplicationServiceState(result.get("state"))
return None
async def set_appservice_state(
@@ -186,7 +186,7 @@ class ApplicationServiceTransactionWorkerStore(
state: The connectivity state to apply.
"""
await self.db_pool.simple_upsert(
- "application_services_state", {"as_id": service.id}, {"state": state}
+ "application_services_state", {"as_id": service.id}, {"state": state.value}
)
async def create_appservice_txn(
diff --git a/synapse/storage/databases/main/devices.py b/synapse/storage/databases/main/devices.py
index 9ccc66e589..838a2a6a3d 100644
--- a/synapse/storage/databases/main/devices.py
+++ b/synapse/storage/databases/main/devices.py
@@ -139,6 +139,27 @@ class DeviceWorkerStore(SQLBaseStore):
return {d["device_id"]: d for d in devices}
+ async def get_devices_by_auth_provider_session_id(
+ self, auth_provider_id: str, auth_provider_session_id: str
+ ) -> List[Dict[str, Any]]:
+ """Retrieve the list of devices associated with a SSO IdP session ID.
+
+ Args:
+ auth_provider_id: The SSO IdP ID as defined in the server config
+ auth_provider_session_id: The session ID within the IdP
+ Returns:
+ A list of dicts containing the device_id and the user_id of each device
+ """
+ return await self.db_pool.simple_select_list(
+ table="device_auth_providers",
+ keyvalues={
+ "auth_provider_id": auth_provider_id,
+ "auth_provider_session_id": auth_provider_session_id,
+ },
+ retcols=("user_id", "device_id"),
+ desc="get_devices_by_auth_provider_session_id",
+ )
+
@trace
async def get_device_updates_by_remote(
self, destination: str, from_stream_id: int, limit: int
@@ -253,7 +274,9 @@ class DeviceWorkerStore(SQLBaseStore):
# add the updated cross-signing keys to the results list
for user_id, result in cross_signing_keys_by_user.items():
result["user_id"] = user_id
- # FIXME: switch to m.signing_key_update when MSC1756 is merged into the spec
+ results.append(("m.signing_key_update", result))
+ # also send the unstable version
+ # FIXME: remove this when enough servers have upgraded
results.append(("org.matrix.signing_key_update", result))
return now_stream_id, results
@@ -1070,7 +1093,12 @@ class DeviceStore(DeviceWorkerStore, DeviceBackgroundUpdateStore):
)
async def store_device(
- self, user_id: str, device_id: str, initial_device_display_name: Optional[str]
+ self,
+ user_id: str,
+ device_id: str,
+ initial_device_display_name: Optional[str],
+ auth_provider_id: Optional[str] = None,
+ auth_provider_session_id: Optional[str] = None,
) -> bool:
"""Ensure the given device is known; add it to the store if not
@@ -1079,6 +1107,8 @@ class DeviceStore(DeviceWorkerStore, DeviceBackgroundUpdateStore):
device_id: id of device
initial_device_display_name: initial displayname of the device.
Ignored if device exists.
+ auth_provider_id: The SSO IdP the user used, if any.
+ auth_provider_session_id: The session ID (sid) got from a OIDC login.
Returns:
Whether the device was inserted or an existing device existed with that ID.
@@ -1115,6 +1145,18 @@ class DeviceStore(DeviceWorkerStore, DeviceBackgroundUpdateStore):
if hidden:
raise StoreError(400, "The device ID is in use", Codes.FORBIDDEN)
+ if auth_provider_id and auth_provider_session_id:
+ await self.db_pool.simple_insert(
+ "device_auth_providers",
+ values={
+ "user_id": user_id,
+ "device_id": device_id,
+ "auth_provider_id": auth_provider_id,
+ "auth_provider_session_id": auth_provider_session_id,
+ },
+ desc="store_device_auth_provider",
+ )
+
self.device_id_exists_cache.set(key, True)
return inserted
except StoreError:
@@ -1168,6 +1210,14 @@ class DeviceStore(DeviceWorkerStore, DeviceBackgroundUpdateStore):
keyvalues={"user_id": user_id},
)
+ self.db_pool.simple_delete_many_txn(
+ txn,
+ table="device_auth_providers",
+ column="device_id",
+ values=device_ids,
+ keyvalues={"user_id": user_id},
+ )
+
await self.db_pool.runInteraction("delete_devices", _delete_devices_txn)
for device_id in device_ids:
self.device_id_exists_cache.invalidate((user_id, device_id))
diff --git a/synapse/storage/databases/main/event_federation.py b/synapse/storage/databases/main/event_federation.py
index ef5d1ef01e..9580a40785 100644
--- a/synapse/storage/databases/main/event_federation.py
+++ b/synapse/storage/databases/main/event_federation.py
@@ -1552,9 +1552,9 @@ class EventFederationStore(EventFederationWorkerStore):
DELETE FROM event_auth
WHERE event_id IN (
SELECT event_id FROM events
- LEFT JOIN state_events USING (room_id, event_id)
+ LEFT JOIN state_events AS se USING (room_id, event_id)
WHERE ? <= stream_ordering AND stream_ordering < ?
- AND state_key IS null
+ AND se.state_key IS null
)
"""
diff --git a/synapse/storage/databases/main/event_push_actions.py b/synapse/storage/databases/main/event_push_actions.py
index d957e770dc..3efdd0c920 100644
--- a/synapse/storage/databases/main/event_push_actions.py
+++ b/synapse/storage/databases/main/event_push_actions.py
@@ -16,6 +16,7 @@ import logging
from typing import TYPE_CHECKING, Dict, List, Optional, Tuple, Union
import attr
+from typing_extensions import TypedDict
from synapse.metrics.background_process_metrics import wrap_as_background_process
from synapse.storage._base import SQLBaseStore, db_to_json
@@ -37,6 +38,20 @@ DEFAULT_HIGHLIGHT_ACTION = [
]
+class BasePushAction(TypedDict):
+ event_id: str
+ actions: List[Union[dict, str]]
+
+
+class HttpPushAction(BasePushAction):
+ room_id: str
+ stream_ordering: int
+
+
+class EmailPushAction(HttpPushAction):
+ received_ts: Optional[int]
+
+
def _serialize_action(actions, is_highlight):
"""Custom serializer for actions. This allows us to "compress" common actions.
@@ -221,7 +236,7 @@ class EventPushActionsWorkerStore(SQLBaseStore):
min_stream_ordering: int,
max_stream_ordering: int,
limit: int = 20,
- ) -> List[dict]:
+ ) -> List[HttpPushAction]:
"""Get a list of the most recent unread push actions for a given user,
within the given stream ordering range. Called by the httppusher.
@@ -326,7 +341,7 @@ class EventPushActionsWorkerStore(SQLBaseStore):
min_stream_ordering: int,
max_stream_ordering: int,
limit: int = 20,
- ) -> List[dict]:
+ ) -> List[EmailPushAction]:
"""Get a list of the most recent unread push actions for a given user,
within the given stream ordering range. Called by the emailpusher
diff --git a/synapse/storage/databases/main/events.py b/synapse/storage/databases/main/events.py
index c3440de2cb..4e528612ea 100644
--- a/synapse/storage/databases/main/events.py
+++ b/synapse/storage/databases/main/events.py
@@ -124,10 +124,12 @@ class PersistEventsStore:
async def _persist_events_and_state_updates(
self,
events_and_contexts: List[Tuple[EventBase, EventContext]],
+ *,
current_state_for_room: Dict[str, StateMap[str]],
state_delta_for_room: Dict[str, DeltaState],
new_forward_extremeties: Dict[str, List[str]],
- backfilled: bool = False,
+ use_negative_stream_ordering: bool = False,
+ inhibit_local_membership_updates: bool = False,
) -> None:
"""Persist a set of events alongside updates to the current state and
forward extremities tables.
@@ -140,7 +142,14 @@ class PersistEventsStore:
room state
new_forward_extremities: Map from room_id to list of event IDs
that are the new forward extremities of the room.
- backfilled
+ use_negative_stream_ordering: Whether to start stream_ordering on
+ the negative side and decrement. This should be set as True
+ for backfilled events because backfilled events get a negative
+ stream ordering so they don't come down incremental `/sync`.
+ inhibit_local_membership_updates: Stop the local_current_membership
+ from being updated by these events. This should be set to True
+ for backfilled events because backfilled events in the past do
+ not affect the current local state.
Returns:
Resolves when the events have been persisted
@@ -162,7 +171,7 @@ class PersistEventsStore:
#
# Note: Multiple instances of this function cannot be in flight at
# the same time for the same room.
- if backfilled:
+ if use_negative_stream_ordering:
stream_ordering_manager = self._backfill_id_gen.get_next_mult(
len(events_and_contexts)
)
@@ -179,13 +188,13 @@ class PersistEventsStore:
"persist_events",
self._persist_events_txn,
events_and_contexts=events_and_contexts,
- backfilled=backfilled,
+ inhibit_local_membership_updates=inhibit_local_membership_updates,
state_delta_for_room=state_delta_for_room,
new_forward_extremeties=new_forward_extremeties,
)
persist_event_counter.inc(len(events_and_contexts))
- if not backfilled:
+ if stream < 0:
# backfilled events have negative stream orderings, so we don't
# want to set the event_persisted_position to that.
synapse.metrics.event_persisted_position.set(
@@ -319,8 +328,9 @@ class PersistEventsStore:
def _persist_events_txn(
self,
txn: LoggingTransaction,
+ *,
events_and_contexts: List[Tuple[EventBase, EventContext]],
- backfilled: bool,
+ inhibit_local_membership_updates: bool = False,
state_delta_for_room: Optional[Dict[str, DeltaState]] = None,
new_forward_extremeties: Optional[Dict[str, List[str]]] = None,
):
@@ -333,7 +343,10 @@ class PersistEventsStore:
Args:
txn
events_and_contexts: events to persist
- backfilled: True if the events were backfilled
+ inhibit_local_membership_updates: Stop the local_current_membership
+ from being updated by these events. This should be set to True
+ for backfilled events because backfilled events in the past do
+ not affect the current local state.
delete_existing True to purge existing table rows for the events
from the database. This is useful when retrying due to
IntegrityError.
@@ -366,9 +379,7 @@ class PersistEventsStore:
events_and_contexts
)
- self._update_room_depths_txn(
- txn, events_and_contexts=events_and_contexts, backfilled=backfilled
- )
+ self._update_room_depths_txn(txn, events_and_contexts=events_and_contexts)
# _update_outliers_txn filters out any events which have already been
# persisted, and returns the filtered list.
@@ -401,7 +412,7 @@ class PersistEventsStore:
txn,
events_and_contexts=events_and_contexts,
all_events_and_contexts=all_events_and_contexts,
- backfilled=backfilled,
+ inhibit_local_membership_updates=inhibit_local_membership_updates,
)
# We call this last as it assumes we've inserted the events into
@@ -564,9 +575,9 @@ class PersistEventsStore:
# fetch their auth event info.
while missing_auth_chains:
sql = """
- SELECT event_id, events.type, state_key, chain_id, sequence_number
+ SELECT event_id, events.type, se.state_key, chain_id, sequence_number
FROM events
- INNER JOIN state_events USING (event_id)
+ INNER JOIN state_events AS se USING (event_id)
LEFT JOIN event_auth_chains USING (event_id)
WHERE
"""
@@ -1203,7 +1214,6 @@ class PersistEventsStore:
self,
txn,
events_and_contexts: List[Tuple[EventBase, EventContext]],
- backfilled: bool,
):
"""Update min_depth for each room
@@ -1211,13 +1221,18 @@ class PersistEventsStore:
txn (twisted.enterprise.adbapi.Connection): db connection
events_and_contexts (list[(EventBase, EventContext)]): events
we are persisting
- backfilled (bool): True if the events were backfilled
"""
depth_updates: Dict[str, int] = {}
for event, context in events_and_contexts:
# Remove the any existing cache entries for the event_ids
txn.call_after(self.store._invalidate_get_event_cache, event.event_id)
- if not backfilled:
+ # Then update the `stream_ordering` position to mark the latest
+ # event as the front of the room. This should not be done for
+ # backfilled events because backfilled events have negative
+ # stream_ordering and happened in the past so we know that we don't
+ # need to update the stream_ordering tip/front for the room.
+ assert event.internal_metadata.stream_ordering is not None
+ if event.internal_metadata.stream_ordering >= 0:
txn.call_after(
self.store._events_stream_cache.entity_has_changed,
event.room_id,
@@ -1430,7 +1445,12 @@ class PersistEventsStore:
return [ec for ec in events_and_contexts if ec[0] not in to_remove]
def _update_metadata_tables_txn(
- self, txn, events_and_contexts, all_events_and_contexts, backfilled
+ self,
+ txn,
+ *,
+ events_and_contexts,
+ all_events_and_contexts,
+ inhibit_local_membership_updates: bool = False,
):
"""Update all the miscellaneous tables for new events
@@ -1442,7 +1462,10 @@ class PersistEventsStore:
events that we were going to persist. This includes events
we've already persisted, etc, that wouldn't appear in
events_and_context.
- backfilled (bool): True if the events were backfilled
+ inhibit_local_membership_updates: Stop the local_current_membership
+ from being updated by these events. This should be set to True
+ for backfilled events because backfilled events in the past do
+ not affect the current local state.
"""
# Insert all the push actions into the event_push_actions table.
@@ -1516,7 +1539,7 @@ class PersistEventsStore:
for event, _ in events_and_contexts
if event.type == EventTypes.Member
],
- backfilled=backfilled,
+ inhibit_local_membership_updates=inhibit_local_membership_updates,
)
# Insert event_reference_hashes table.
@@ -1643,8 +1666,19 @@ class PersistEventsStore:
txn, table="event_reference_hashes", values=vals
)
- def _store_room_members_txn(self, txn, events, backfilled):
- """Store a room member in the database."""
+ def _store_room_members_txn(
+ self, txn, events, *, inhibit_local_membership_updates: bool = False
+ ):
+ """
+ Store a room member in the database.
+ Args:
+ txn: The transaction to use.
+ events: List of events to store.
+ inhibit_local_membership_updates: Stop the local_current_membership
+ from being updated by these events. This should be set to True
+ for backfilled events because backfilled events in the past do
+ not affect the current local state.
+ """
def non_null_str_or_none(val: Any) -> Optional[str]:
return val if isinstance(val, str) and "\u0000" not in val else None
@@ -1687,7 +1721,7 @@ class PersistEventsStore:
# band membership", like a remote invite or a rejection of a remote invite.
if (
self.is_mine_id(event.state_key)
- and not backfilled
+ and not inhibit_local_membership_updates
and event.internal_metadata.is_outlier()
and event.internal_metadata.is_out_of_band_membership()
):
diff --git a/synapse/storage/databases/main/events_worker.py b/synapse/storage/databases/main/events_worker.py
index 4cefc0a07e..c7b660ac5a 100644
--- a/synapse/storage/databases/main/events_worker.py
+++ b/synapse/storage/databases/main/events_worker.py
@@ -1408,10 +1408,10 @@ class EventsWorkerStore(SQLBaseStore):
) -> List[Tuple[int, str, str, str, str, str, str, str, str]]:
sql = (
"SELECT e.stream_ordering, e.event_id, e.room_id, e.type,"
- " state_key, redacts, relates_to_id, membership, rejections.reason IS NOT NULL"
+ " se.state_key, redacts, relates_to_id, membership, rejections.reason IS NOT NULL"
" FROM events AS e"
" LEFT JOIN redactions USING (event_id)"
- " LEFT JOIN state_events USING (event_id)"
+ " LEFT JOIN state_events AS se USING (event_id)"
" LEFT JOIN event_relations USING (event_id)"
" LEFT JOIN room_memberships USING (event_id)"
" LEFT JOIN rejections USING (event_id)"
@@ -1449,11 +1449,11 @@ class EventsWorkerStore(SQLBaseStore):
) -> List[Tuple[int, str, str, str, str, str, str, str, str]]:
sql = (
"SELECT event_stream_ordering, e.event_id, e.room_id, e.type,"
- " state_key, redacts, relates_to_id, membership, rejections.reason IS NOT NULL"
+ " se.state_key, redacts, relates_to_id, membership, rejections.reason IS NOT NULL"
" FROM events AS e"
" INNER JOIN ex_outlier_stream AS out USING (event_id)"
" LEFT JOIN redactions USING (event_id)"
- " LEFT JOIN state_events USING (event_id)"
+ " LEFT JOIN state_events AS se USING (event_id)"
" LEFT JOIN event_relations USING (event_id)"
" LEFT JOIN room_memberships USING (event_id)"
" LEFT JOIN rejections USING (event_id)"
@@ -1507,10 +1507,10 @@ class EventsWorkerStore(SQLBaseStore):
) -> Tuple[List[Tuple[int, Tuple[str, str, str, str, str, str]]], int, bool]:
sql = (
"SELECT -e.stream_ordering, e.event_id, e.room_id, e.type,"
- " state_key, redacts, relates_to_id"
+ " se.state_key, redacts, relates_to_id"
" FROM events AS e"
" LEFT JOIN redactions USING (event_id)"
- " LEFT JOIN state_events USING (event_id)"
+ " LEFT JOIN state_events AS se USING (event_id)"
" LEFT JOIN event_relations USING (event_id)"
" WHERE ? > stream_ordering AND stream_ordering >= ?"
" AND instance_name = ?"
@@ -1537,11 +1537,11 @@ class EventsWorkerStore(SQLBaseStore):
sql = (
"SELECT -event_stream_ordering, e.event_id, e.room_id, e.type,"
- " state_key, redacts, relates_to_id"
+ " se.state_key, redacts, relates_to_id"
" FROM events AS e"
" INNER JOIN ex_outlier_stream AS out USING (event_id)"
" LEFT JOIN redactions USING (event_id)"
- " LEFT JOIN state_events USING (event_id)"
+ " LEFT JOIN state_events AS se USING (event_id)"
" LEFT JOIN event_relations USING (event_id)"
" WHERE ? > event_stream_ordering"
" AND event_stream_ordering >= ?"
@@ -1762,3 +1762,198 @@ class EventsWorkerStore(SQLBaseStore):
"_cleanup_old_transaction_ids",
_cleanup_old_transaction_ids_txn,
)
+
+ async def is_event_next_to_backward_gap(self, event: EventBase) -> bool:
+ """Check if the given event is next to a backward gap of missing events.
+ <latest messages> A(False)--->B(False)--->C(True)---> <gap, unknown events> <oldest messages>
+
+ Args:
+ room_id: room where the event lives
+ event_id: event to check
+
+ Returns:
+ Boolean indicating whether it's an extremity
+ """
+
+ def is_event_next_to_backward_gap_txn(txn: LoggingTransaction) -> bool:
+ # If the event in question has any of its prev_events listed as a
+ # backward extremity, it's next to a gap.
+ #
+ # We can't just check the backward edges in `event_edges` because
+ # when we persist events, we will also record the prev_events as
+ # edges to the event in question regardless of whether we have those
+ # prev_events yet. We need to check whether those prev_events are
+ # backward extremities, also known as gaps, that need to be
+ # backfilled.
+ backward_extremity_query = """
+ SELECT 1 FROM event_backward_extremities
+ WHERE
+ room_id = ?
+ AND %s
+ LIMIT 1
+ """
+
+ # If the event in question is a backward extremity or has any of its
+ # prev_events listed as a backward extremity, it's next to a
+ # backward gap.
+ clause, args = make_in_list_sql_clause(
+ self.database_engine,
+ "event_id",
+ [event.event_id] + list(event.prev_event_ids()),
+ )
+
+ txn.execute(backward_extremity_query % (clause,), [event.room_id] + args)
+ backward_extremities = txn.fetchall()
+
+ # We consider any backward extremity as a backward gap
+ if len(backward_extremities):
+ return True
+
+ return False
+
+ return await self.db_pool.runInteraction(
+ "is_event_next_to_backward_gap_txn",
+ is_event_next_to_backward_gap_txn,
+ )
+
+ async def is_event_next_to_forward_gap(self, event: EventBase) -> bool:
+ """Check if the given event is next to a forward gap of missing events.
+ The gap in front of the latest events is not considered a gap.
+ <latest messages> A(False)--->B(False)--->C(False)---> <gap, unknown events> <oldest messages>
+ <latest messages> A(False)--->B(False)---> <gap, unknown events> --->D(True)--->E(False) <oldest messages>
+
+ Args:
+ room_id: room where the event lives
+ event_id: event to check
+
+ Returns:
+ Boolean indicating whether it's an extremity
+ """
+
+ def is_event_next_to_gap_txn(txn: LoggingTransaction) -> bool:
+ # If the event in question is a forward extremity, we will just
+ # consider any potential forward gap as not a gap since it's one of
+ # the latest events in the room.
+ #
+ # `event_forward_extremities` does not include backfilled or outlier
+ # events so we can't rely on it to find forward gaps. We can only
+ # use it to determine whether a message is the latest in the room.
+ #
+ # We can't combine this query with the `forward_edge_query` below
+ # because if the event in question has no forward edges (isn't
+ # referenced by any other event's prev_events) but is in
+ # `event_forward_extremities`, we don't want to return 0 rows and
+ # say it's next to a gap.
+ forward_extremity_query = """
+ SELECT 1 FROM event_forward_extremities
+ WHERE
+ room_id = ?
+ AND event_id = ?
+ LIMIT 1
+ """
+
+ # Check to see whether the event in question is already referenced
+ # by another event. If we don't see any edges, we're next to a
+ # forward gap.
+ forward_edge_query = """
+ SELECT 1 FROM event_edges
+ /* Check to make sure the event referencing our event in question is not rejected */
+ LEFT JOIN rejections ON event_edges.event_id == rejections.event_id
+ WHERE
+ event_edges.room_id = ?
+ AND event_edges.prev_event_id = ?
+ /* It's not a valid edge if the event referencing our event in
+ * question is rejected.
+ */
+ AND rejections.event_id IS NULL
+ LIMIT 1
+ """
+
+ # We consider any forward extremity as the latest in the room and
+ # not a forward gap.
+ #
+ # To expand, even though there is technically a gap at the front of
+ # the room where the forward extremities are, we consider those the
+ # latest messages in the room so asking other homeservers for more
+ # is useless. The new latest messages will just be federated as
+ # usual.
+ txn.execute(forward_extremity_query, (event.room_id, event.event_id))
+ forward_extremities = txn.fetchall()
+ if len(forward_extremities):
+ return False
+
+ # If there are no forward edges to the event in question (another
+ # event hasn't referenced this event in their prev_events), then we
+ # assume there is a forward gap in the history.
+ txn.execute(forward_edge_query, (event.room_id, event.event_id))
+ forward_edges = txn.fetchall()
+ if not len(forward_edges):
+ return True
+
+ return False
+
+ return await self.db_pool.runInteraction(
+ "is_event_next_to_gap_txn",
+ is_event_next_to_gap_txn,
+ )
+
+ async def get_event_id_for_timestamp(
+ self, room_id: str, timestamp: int, direction: str
+ ) -> Optional[str]:
+ """Find the closest event to the given timestamp in the given direction.
+
+ Args:
+ room_id: Room to fetch the event from
+ timestamp: The point in time (inclusive) we should navigate from in
+ the given direction to find the closest event.
+ direction: ["f"|"b"] to indicate whether we should navigate forward
+ or backward from the given timestamp to find the closest event.
+
+ Returns:
+ The closest event_id otherwise None if we can't find any event in
+ the given direction.
+ """
+
+ sql_template = """
+ SELECT event_id FROM events
+ LEFT JOIN rejections USING (event_id)
+ WHERE
+ origin_server_ts %s ?
+ AND room_id = ?
+ /* Make sure event is not rejected */
+ AND rejections.event_id IS NULL
+ ORDER BY origin_server_ts %s
+ LIMIT 1;
+ """
+
+ def get_event_id_for_timestamp_txn(txn: LoggingTransaction) -> Optional[str]:
+ if direction == "b":
+ # Find closest event *before* a given timestamp. We use descending
+ # (which gives values largest to smallest) because we want the
+ # largest possible timestamp *before* the given timestamp.
+ comparison_operator = "<="
+ order = "DESC"
+ else:
+ # Find closest event *after* a given timestamp. We use ascending
+ # (which gives values smallest to largest) because we want the
+ # closest possible timestamp *after* the given timestamp.
+ comparison_operator = ">="
+ order = "ASC"
+
+ txn.execute(
+ sql_template % (comparison_operator, order), (timestamp, room_id)
+ )
+ row = txn.fetchone()
+ if row:
+ (event_id,) = row
+ return event_id
+
+ return None
+
+ if direction not in ("f", "b"):
+ raise ValueError("Unknown direction: %s" % (direction,))
+
+ return await self.db_pool.runInteraction(
+ "get_event_id_for_timestamp_txn",
+ get_event_id_for_timestamp_txn,
+ )
diff --git a/synapse/storage/databases/main/purge_events.py b/synapse/storage/databases/main/purge_events.py
index 3eb30944bf..91b0576b85 100644
--- a/synapse/storage/databases/main/purge_events.py
+++ b/synapse/storage/databases/main/purge_events.py
@@ -118,7 +118,7 @@ class PurgeEventsStore(StateGroupWorkerStore, CacheInvalidationWorkerStore):
logger.info("[purge] looking for events to delete")
- should_delete_expr = "state_key IS NULL"
+ should_delete_expr = "state_events.state_key IS NULL"
should_delete_params: Tuple[Any, ...] = ()
if not delete_local_events:
should_delete_expr += " AND event_id NOT LIKE ?"
diff --git a/synapse/storage/databases/main/roommember.py b/synapse/storage/databases/main/roommember.py
index 033a9831d6..6b2a8d06a6 100644
--- a/synapse/storage/databases/main/roommember.py
+++ b/synapse/storage/databases/main/roommember.py
@@ -476,7 +476,7 @@ class RoomMemberWorkerStore(EventsWorkerStore):
INNER JOIN events AS e USING (room_id, event_id)
WHERE
c.type = 'm.room.member'
- AND state_key = ?
+ AND c.state_key = ?
AND c.membership = ?
"""
else:
@@ -487,7 +487,7 @@ class RoomMemberWorkerStore(EventsWorkerStore):
INNER JOIN events AS e USING (room_id, event_id)
WHERE
c.type = 'm.room.member'
- AND state_key = ?
+ AND c.state_key = ?
AND m.membership = ?
"""
diff --git a/synapse/storage/databases/main/stream.py b/synapse/storage/databases/main/stream.py
index 42dc807d17..57aab55259 100644
--- a/synapse/storage/databases/main/stream.py
+++ b/synapse/storage/databases/main/stream.py
@@ -497,7 +497,7 @@ class StreamWorkerStore(EventsWorkerStore, SQLBaseStore, metaclass=abc.ABCMeta):
oldest `limit` events.
Returns:
- The list of events (in ascending order) and the token from the start
+ The list of events (in ascending stream order) and the token from the start
of the chunk of events returned.
"""
if from_key == to_key:
@@ -510,7 +510,7 @@ class StreamWorkerStore(EventsWorkerStore, SQLBaseStore, metaclass=abc.ABCMeta):
if not has_changed:
return [], from_key
- def f(txn):
+ def f(txn: LoggingTransaction) -> List[_EventDictReturn]:
# To handle tokens with a non-empty instance_map we fetch more
# results than necessary and then filter down
min_from_id = from_key.stream
@@ -565,6 +565,13 @@ class StreamWorkerStore(EventsWorkerStore, SQLBaseStore, metaclass=abc.ABCMeta):
async def get_membership_changes_for_user(
self, user_id: str, from_key: RoomStreamToken, to_key: RoomStreamToken
) -> List[EventBase]:
+ """Fetch membership events for a given user.
+
+ All such events whose stream ordering `s` lies in the range
+ `from_key < s <= to_key` are returned. Events are ordered by ascending stream
+ order.
+ """
+ # Start by ruling out cases where a DB query is not necessary.
if from_key == to_key:
return []
@@ -575,7 +582,7 @@ class StreamWorkerStore(EventsWorkerStore, SQLBaseStore, metaclass=abc.ABCMeta):
if not has_changed:
return []
- def f(txn):
+ def f(txn: LoggingTransaction) -> List[_EventDictReturn]:
# To handle tokens with a non-empty instance_map we fetch more
# results than necessary and then filter down
min_from_id = from_key.stream
@@ -634,7 +641,7 @@ class StreamWorkerStore(EventsWorkerStore, SQLBaseStore, metaclass=abc.ABCMeta):
Returns:
A list of events and a token pointing to the start of the returned
- events. The events returned are in ascending order.
+ events. The events returned are in ascending topological order.
"""
rows, token = await self.get_recent_event_ids_for_room(
diff --git a/synapse/storage/databases/main/transactions.py b/synapse/storage/databases/main/transactions.py
index d7dc1f73ac..1622822552 100644
--- a/synapse/storage/databases/main/transactions.py
+++ b/synapse/storage/databases/main/transactions.py
@@ -14,6 +14,7 @@
import logging
from collections import namedtuple
+from enum import Enum
from typing import TYPE_CHECKING, Iterable, List, Optional, Tuple
import attr
@@ -44,6 +45,16 @@ _UpdateTransactionRow = namedtuple(
)
+class DestinationSortOrder(Enum):
+ """Enum to define the sorting method used when returning destinations."""
+
+ DESTINATION = "destination"
+ RETRY_LAST_TS = "retry_last_ts"
+ RETTRY_INTERVAL = "retry_interval"
+ FAILURE_TS = "failure_ts"
+ LAST_SUCCESSFUL_STREAM_ORDERING = "last_successful_stream_ordering"
+
+
@attr.s(slots=True, frozen=True, auto_attribs=True)
class DestinationRetryTimings:
"""The current destination retry timing info for a remote server."""
@@ -480,3 +491,62 @@ class TransactionWorkerStore(CacheInvalidationWorkerStore):
destinations = [row[0] for row in txn]
return destinations
+
+ async def get_destinations_paginate(
+ self,
+ start: int,
+ limit: int,
+ destination: Optional[str] = None,
+ order_by: str = DestinationSortOrder.DESTINATION.value,
+ direction: str = "f",
+ ) -> Tuple[List[JsonDict], int]:
+ """Function to retrieve a paginated list of destinations.
+ This will return a json list of destinations and the
+ total number of destinations matching the filter criteria.
+
+ Args:
+ start: start number to begin the query from
+ limit: number of rows to retrieve
+ destination: search string in destination
+ order_by: the sort order of the returned list
+ direction: sort ascending or descending
+ Returns:
+ A tuple of a list of mappings from destination to information
+ and a count of total destinations.
+ """
+
+ def get_destinations_paginate_txn(
+ txn: LoggingTransaction,
+ ) -> Tuple[List[JsonDict], int]:
+ order_by_column = DestinationSortOrder(order_by).value
+
+ if direction == "b":
+ order = "DESC"
+ else:
+ order = "ASC"
+
+ args = []
+ where_statement = ""
+ if destination:
+ args.extend(["%" + destination.lower() + "%"])
+ where_statement = "WHERE LOWER(destination) LIKE ?"
+
+ sql_base = f"FROM destinations {where_statement} "
+ sql = f"SELECT COUNT(*) as total_destinations {sql_base}"
+ txn.execute(sql, args)
+ count = txn.fetchone()[0]
+
+ sql = f"""
+ SELECT destination, retry_last_ts, retry_interval, failure_ts,
+ last_successful_stream_ordering
+ {sql_base}
+ ORDER BY {order_by_column} {order}, destination ASC
+ LIMIT ? OFFSET ?
+ """
+ txn.execute(sql, args + [limit, start])
+ destinations = self.db_pool.cursor_to_dict(txn)
+ return destinations, count
+
+ return await self.db_pool.runInteraction(
+ "get_destinations_paginate_txn", get_destinations_paginate_txn
+ )
diff --git a/synapse/storage/persist_events.py b/synapse/storage/persist_events.py
index 402f134d89..428d66a617 100644
--- a/synapse/storage/persist_events.py
+++ b/synapse/storage/persist_events.py
@@ -583,7 +583,8 @@ class EventsPersistenceStorage:
current_state_for_room=current_state_for_room,
state_delta_for_room=state_delta_for_room,
new_forward_extremeties=new_forward_extremeties,
- backfilled=backfilled,
+ use_negative_stream_ordering=backfilled,
+ inhibit_local_membership_updates=backfilled,
)
await self._handle_potentially_left_users(potentially_left_users)
diff --git a/synapse/storage/schema/__init__.py b/synapse/storage/schema/__init__.py
index 3a00ed6835..50d08094d5 100644
--- a/synapse/storage/schema/__init__.py
+++ b/synapse/storage/schema/__init__.py
@@ -12,7 +12,7 @@
# See the License for the specific language governing permissions and
# limitations under the License.
-SCHEMA_VERSION = 65 # remember to update the list below when updating
+SCHEMA_VERSION = 66 # remember to update the list below when updating
"""Represents the expectations made by the codebase about the database schema
This should be incremented whenever the codebase changes its requirements on the
@@ -46,6 +46,10 @@ Changes in SCHEMA_VERSION = 65:
- MSC2716: Remove unique event_id constraint from insertion_event_edges
because an insertion event can have multiple edges.
- Remove unused tables `user_stats_historical` and `room_stats_historical`.
+
+Changes in SCHEMA_VERSION = 66:
+ - Queries on state_key columns are now disambiguated (ie, the codebase can handle
+ the `events` table having a `state_key` column).
"""
diff --git a/synapse/storage/schema/main/delta/65/11_devices_auth_provider_session.sql b/synapse/storage/schema/main/delta/65/11_devices_auth_provider_session.sql
new file mode 100644
index 0000000000..a65bfb520d
--- /dev/null
+++ b/synapse/storage/schema/main/delta/65/11_devices_auth_provider_session.sql
@@ -0,0 +1,27 @@
+/* Copyright 2021 The Matrix.org Foundation C.I.C
+ *
+ * Licensed under the Apache License, Version 2.0 (the "License");
+ * you may not use this file except in compliance with the License.
+ * You may obtain a copy of the License at
+ *
+ * http://www.apache.org/licenses/LICENSE-2.0
+ *
+ * Unless required by applicable law or agreed to in writing, software
+ * distributed under the License is distributed on an "AS IS" BASIS,
+ * WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
+ * See the License for the specific language governing permissions and
+ * limitations under the License.
+ */
+
+-- Track the auth provider used by each login as well as the session ID
+CREATE TABLE device_auth_providers (
+ user_id TEXT NOT NULL,
+ device_id TEXT NOT NULL,
+ auth_provider_id TEXT NOT NULL,
+ auth_provider_session_id TEXT NOT NULL
+);
+
+CREATE INDEX device_auth_providers_devices
+ ON device_auth_providers (user_id, device_id);
+CREATE INDEX device_auth_providers_sessions
+ ON device_auth_providers (auth_provider_id, auth_provider_session_id);
diff --git a/synapse/util/caches/deferred_cache.py b/synapse/util/caches/deferred_cache.py
index 3c4cc093af..377c9a282a 100644
--- a/synapse/util/caches/deferred_cache.py
+++ b/synapse/util/caches/deferred_cache.py
@@ -22,6 +22,7 @@ from typing import (
Iterable,
MutableMapping,
Optional,
+ Sized,
TypeVar,
Union,
cast,
@@ -104,7 +105,13 @@ class DeferredCache(Generic[KT, VT]):
max_size=max_entries,
cache_name=name,
cache_type=cache_type,
- size_callback=(lambda d: len(d) or 1) if iterable else None,
+ size_callback=(
+ (lambda d: len(cast(Sized, d)) or 1)
+ # Argument 1 to "len" has incompatible type "VT"; expected "Sized"
+ # We trust that `VT` is `Sized` when `iterable` is `True`
+ if iterable
+ else None
+ ),
metrics_collection_callback=metrics_cb,
apply_cache_factor_from_config=apply_cache_factor_from_config,
prune_unread_entries=prune_unread_entries,
diff --git a/synapse/util/caches/lrucache.py b/synapse/util/caches/lrucache.py
index a0a7a9de32..eb96f7e665 100644
--- a/synapse/util/caches/lrucache.py
+++ b/synapse/util/caches/lrucache.py
@@ -15,14 +15,15 @@
import logging
import threading
import weakref
+from enum import Enum
from functools import wraps
from typing import (
TYPE_CHECKING,
Any,
Callable,
Collection,
+ Dict,
Generic,
- Iterable,
List,
Optional,
Type,
@@ -190,7 +191,7 @@ class _Node(Generic[KT, VT]):
root: "ListNode[_Node]",
key: KT,
value: VT,
- cache: "weakref.ReferenceType[LruCache]",
+ cache: "weakref.ReferenceType[LruCache[KT, VT]]",
clock: Clock,
callbacks: Collection[Callable[[], None]] = (),
prune_unread_entries: bool = True,
@@ -270,7 +271,10 @@ class _Node(Generic[KT, VT]):
removed from all lists.
"""
cache = self._cache()
- if not cache or not cache.pop(self.key, None):
+ if (
+ cache is None
+ or cache.pop(self.key, _Sentinel.sentinel) is _Sentinel.sentinel
+ ):
# `cache.pop` should call `drop_from_lists()`, unless this Node had
# already been removed from the cache.
self.drop_from_lists()
@@ -290,6 +294,12 @@ class _Node(Generic[KT, VT]):
self._global_list_node.update_last_access(clock)
+class _Sentinel(Enum):
+ # defining a sentinel in this way allows mypy to correctly handle the
+ # type of a dictionary lookup.
+ sentinel = object()
+
+
class LruCache(Generic[KT, VT]):
"""
Least-recently-used cache, supporting prometheus metrics and invalidation callbacks.
@@ -302,7 +312,7 @@ class LruCache(Generic[KT, VT]):
max_size: int,
cache_name: Optional[str] = None,
cache_type: Type[Union[dict, TreeCache]] = dict,
- size_callback: Optional[Callable] = None,
+ size_callback: Optional[Callable[[VT], int]] = None,
metrics_collection_callback: Optional[Callable[[], None]] = None,
apply_cache_factor_from_config: bool = True,
clock: Optional[Clock] = None,
@@ -339,7 +349,7 @@ class LruCache(Generic[KT, VT]):
else:
real_clock = clock
- cache = cache_type()
+ cache: Union[Dict[KT, _Node[KT, VT]], TreeCache] = cache_type()
self.cache = cache # Used for introspection.
self.apply_cache_factor_from_config = apply_cache_factor_from_config
@@ -374,7 +384,7 @@ class LruCache(Generic[KT, VT]):
# creating more each time we create a `_Node`.
weak_ref_to_self = weakref.ref(self)
- list_root = ListNode[_Node].create_root_node()
+ list_root = ListNode[_Node[KT, VT]].create_root_node()
lock = threading.Lock()
@@ -422,7 +432,7 @@ class LruCache(Generic[KT, VT]):
def add_node(
key: KT, value: VT, callbacks: Collection[Callable[[], None]] = ()
) -> None:
- node = _Node(
+ node: _Node[KT, VT] = _Node(
list_root,
key,
value,
@@ -439,10 +449,10 @@ class LruCache(Generic[KT, VT]):
if caches.TRACK_MEMORY_USAGE and metrics:
metrics.inc_memory_usage(node.memory)
- def move_node_to_front(node: _Node) -> None:
+ def move_node_to_front(node: _Node[KT, VT]) -> None:
node.move_to_front(real_clock, list_root)
- def delete_node(node: _Node) -> int:
+ def delete_node(node: _Node[KT, VT]) -> int:
node.drop_from_lists()
deleted_len = 1
@@ -496,7 +506,7 @@ class LruCache(Generic[KT, VT]):
@synchronized
def cache_set(
- key: KT, value: VT, callbacks: Iterable[Callable[[], None]] = ()
+ key: KT, value: VT, callbacks: Collection[Callable[[], None]] = ()
) -> None:
node = cache.get(key, None)
if node is not None:
@@ -590,8 +600,6 @@ class LruCache(Generic[KT, VT]):
def cache_contains(key: KT) -> bool:
return key in cache
- self.sentinel = object()
-
# make sure that we clear out any excess entries after we get resized.
self._on_resize = evict
@@ -608,18 +616,18 @@ class LruCache(Generic[KT, VT]):
self.clear = cache_clear
def __getitem__(self, key: KT) -> VT:
- result = self.get(key, self.sentinel)
- if result is self.sentinel:
+ result = self.get(key, _Sentinel.sentinel)
+ if result is _Sentinel.sentinel:
raise KeyError()
else:
- return cast(VT, result)
+ return result
def __setitem__(self, key: KT, value: VT) -> None:
self.set(key, value)
def __delitem__(self, key: KT, value: VT) -> None:
- result = self.pop(key, self.sentinel)
- if result is self.sentinel:
+ result = self.pop(key, _Sentinel.sentinel)
+ if result is _Sentinel.sentinel:
raise KeyError()
def __len__(self) -> int:
diff --git a/synapse/util/linked_list.py b/synapse/util/linked_list.py
index 9f4be757ba..8efbf061aa 100644
--- a/synapse/util/linked_list.py
+++ b/synapse/util/linked_list.py
@@ -84,7 +84,7 @@ class ListNode(Generic[P]):
# immediately rather than at the next GC.
self.cache_entry = None
- def move_after(self, node: "ListNode") -> None:
+ def move_after(self, node: "ListNode[P]") -> None:
"""Move this node from its current location in the list to after the
given node.
"""
@@ -122,7 +122,7 @@ class ListNode(Generic[P]):
self.prev_node = None
self.next_node = None
- def _refs_insert_after(self, node: "ListNode") -> None:
+ def _refs_insert_after(self, node: "ListNode[P]") -> None:
"""Internal method to insert the node after the given node."""
# This method should only be called when we're not already in the list.
diff --git a/synapse/util/versionstring.py b/synapse/util/versionstring.py
index 899ee0adc8..c144ff62c1 100644
--- a/synapse/util/versionstring.py
+++ b/synapse/util/versionstring.py
@@ -1,4 +1,5 @@
# Copyright 2016 OpenMarket Ltd
+# Copyright 2021 The Matrix.org Foundation C.I.C.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
@@ -29,10 +30,11 @@ def get_version_string(module: ModuleType) -> str:
If called on a module not in a git checkout will return `__version__`.
Args:
- module (module)
+ module: The module to check the version of. Must declare a __version__
+ attribute.
Returns:
- str
+ The module version (as a string).
"""
cached_version = version_cache.get(module)
@@ -44,71 +46,37 @@ def get_version_string(module: ModuleType) -> str:
version_string = module.__version__ # type: ignore[attr-defined]
try:
- null = open(os.devnull, "w")
cwd = os.path.dirname(os.path.abspath(module.__file__))
- try:
- git_branch = (
- subprocess.check_output(
- ["git", "rev-parse", "--abbrev-ref", "HEAD"], stderr=null, cwd=cwd
+ def _run_git_command(prefix: str, *params: str) -> str:
+ try:
+ result = (
+ subprocess.check_output(
+ ["git", *params], stderr=subprocess.DEVNULL, cwd=cwd
+ )
+ .strip()
+ .decode("ascii")
)
- .strip()
- .decode("ascii")
- )
- git_branch = "b=" + git_branch
- except (subprocess.CalledProcessError, FileNotFoundError):
- # FileNotFoundError can arise when git is not installed
- git_branch = ""
-
- try:
- git_tag = (
- subprocess.check_output(
- ["git", "describe", "--exact-match"], stderr=null, cwd=cwd
- )
- .strip()
- .decode("ascii")
- )
- git_tag = "t=" + git_tag
- except (subprocess.CalledProcessError, FileNotFoundError):
- git_tag = ""
-
- try:
- git_commit = (
- subprocess.check_output(
- ["git", "rev-parse", "--short", "HEAD"], stderr=null, cwd=cwd
- )
- .strip()
- .decode("ascii")
- )
- except (subprocess.CalledProcessError, FileNotFoundError):
- git_commit = ""
-
- try:
- dirty_string = "-this_is_a_dirty_checkout"
- is_dirty = (
- subprocess.check_output(
- ["git", "describe", "--dirty=" + dirty_string], stderr=null, cwd=cwd
- )
- .strip()
- .decode("ascii")
- .endswith(dirty_string)
- )
+ return prefix + result
+ except (subprocess.CalledProcessError, FileNotFoundError):
+ return ""
- git_dirty = "dirty" if is_dirty else ""
- except (subprocess.CalledProcessError, FileNotFoundError):
- git_dirty = ""
+ git_branch = _run_git_command("b=", "rev-parse", "--abbrev-ref", "HEAD")
+ git_tag = _run_git_command("t=", "describe", "--exact-match")
+ git_commit = _run_git_command("", "rev-parse", "--short", "HEAD")
+
+ dirty_string = "-this_is_a_dirty_checkout"
+ is_dirty = _run_git_command("", "describe", "--dirty=" + dirty_string).endswith(
+ dirty_string
+ )
+ git_dirty = "dirty" if is_dirty else ""
if git_branch or git_tag or git_commit or git_dirty:
git_version = ",".join(
s for s in (git_branch, git_tag, git_commit, git_dirty) if s
)
- version_string = "%s (%s)" % (
- # If the __version__ attribute doesn't exist, we'll have failed
- # loudly above.
- module.__version__, # type: ignore[attr-defined]
- git_version,
- )
+ version_string = f"{version_string} ({git_version})"
except Exception as e:
logger.info("Failed to check for git repository: %s", e)
diff --git a/synctl b/synctl
index 90559ded62..0e54f4847b 100755
--- a/synctl
+++ b/synctl
@@ -24,7 +24,7 @@ import signal
import subprocess
import sys
import time
-from typing import Iterable
+from typing import Iterable, Optional
import yaml
@@ -41,11 +41,24 @@ NORMAL = "\x1b[m"
def pid_running(pid):
try:
os.kill(pid, 0)
- return True
except OSError as err:
if err.errno == errno.EPERM:
- return True
- return False
+ pass # process exists
+ else:
+ return False
+
+ # When running in a container, orphan processes may not get reaped and their
+ # PIDs may remain valid. Try to work around the issue.
+ try:
+ with open(f"/proc/{pid}/status") as status_file:
+ if "zombie" in status_file.read():
+ return False
+ except Exception:
+ # This isn't Linux or `/proc/` is unavailable.
+ # Assume that the process is still running.
+ pass
+
+ return True
def write(message, colour=NORMAL, stream=sys.stdout):
@@ -109,15 +122,14 @@ def start(pidfile: str, app: str, config_files: Iterable[str], daemonize: bool)
return False
-def stop(pidfile: str, app: str) -> bool:
+def stop(pidfile: str, app: str) -> Optional[int]:
"""Attempts to kill a synapse worker from the pidfile.
Args:
pidfile: path to file containing worker's pid
app: name of the worker's appservice
Returns:
- True if the process stopped successfully
- False if process was already stopped or an error occured
+ process id, or None if the process was not running
"""
if os.path.exists(pidfile):
@@ -125,7 +137,7 @@ def stop(pidfile: str, app: str) -> bool:
try:
os.kill(pid, signal.SIGTERM)
write("stopped %s" % (app,), colour=GREEN)
- return True
+ return pid
except OSError as err:
if err.errno == errno.ESRCH:
write("%s not running" % (app,), colour=YELLOW)
@@ -133,14 +145,13 @@ def stop(pidfile: str, app: str) -> bool:
abort("Cannot stop %s: Operation not permitted" % (app,))
else:
abort("Cannot stop %s: Unknown error" % (app,))
- return False
else:
write(
"No running worker of %s found (from %s)\nThe process might be managed by another controller (e.g. systemd)"
% (app, pidfile),
colour=YELLOW,
)
- return False
+ return None
Worker = collections.namedtuple(
@@ -288,32 +299,23 @@ def main():
action = options.action
if action == "stop" or action == "restart":
- has_stopped = True
+ running_pids = []
for worker in workers:
- if not stop(worker.pidfile, worker.app):
- # A worker could not be stopped.
- has_stopped = False
+ pid = stop(worker.pidfile, worker.app)
+ if pid is not None:
+ running_pids.append(pid)
if start_stop_synapse:
- if not stop(pidfile, MAIN_PROCESS):
- has_stopped = False
- if not has_stopped and action == "stop":
- sys.exit(1)
+ pid = stop(pidfile, MAIN_PROCESS)
+ if pid is not None:
+ running_pids.append(pid)
- # Wait for synapse to actually shutdown before starting it again
- if action == "restart":
- running_pids = []
- if start_stop_synapse and os.path.exists(pidfile):
- running_pids.append(int(open(pidfile).read()))
- for worker in workers:
- if os.path.exists(worker.pidfile):
- running_pids.append(int(open(worker.pidfile).read()))
if len(running_pids) > 0:
- write("Waiting for process to exit before restarting...")
+ write("Waiting for processes to exit...")
for running_pid in running_pids:
while pid_running(running_pid):
time.sleep(0.2)
- write("All processes exited; now restarting...")
+ write("All processes exited")
if action == "start" or action == "restart":
error = False
diff --git a/tests/app/test_homeserver_start.py b/tests/app/test_homeserver_start.py
new file mode 100644
index 0000000000..cbcada0451
--- /dev/null
+++ b/tests/app/test_homeserver_start.py
@@ -0,0 +1,31 @@
+# Copyright 2021 The Matrix.org Foundation C.I.C.
+#
+# Licensed under the Apache License, Version 2.0 (the "License");
+# you may not use this file except in compliance with the License.
+# You may obtain a copy of the License at
+#
+# http://www.apache.org/licenses/LICENSE-2.0
+#
+# Unless required by applicable law or agreed to in writing, software
+# distributed under the License is distributed on an "AS IS" BASIS,
+# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
+# See the License for the specific language governing permissions and
+# limitations under the License.
+
+import synapse.app.homeserver
+from synapse.config._base import ConfigError
+
+from tests.config.utils import ConfigFileTestCase
+
+
+class HomeserverAppStartTestCase(ConfigFileTestCase):
+ def test_wrong_start_caught(self):
+ # Generate a config with a worker_app
+ self.generate_config()
+ # Add a blank line as otherwise the next addition ends up on a line with a comment
+ self.add_lines_to_config([" "])
+ self.add_lines_to_config(["worker_app: test_worker_app"])
+
+ # Ensure that starting master process with worker config raises an exception
+ with self.assertRaises(ConfigError):
+ synapse.app.homeserver.setup(["-c", self.config_file])
diff --git a/tests/config/test_registration_config.py b/tests/config/test_registration_config.py
new file mode 100644
index 0000000000..17a84d20d8
--- /dev/null
+++ b/tests/config/test_registration_config.py
@@ -0,0 +1,78 @@
+# Copyright 2021 The Matrix.org Foundation C.I.C.
+#
+# Licensed under the Apache License, Version 2.0 (the "License");
+# you may not use this file except in compliance with the License.
+# You may obtain a copy of the License at
+#
+# http://www.apache.org/licenses/LICENSE-2.0
+#
+# Unless required by applicable law or agreed to in writing, software
+# distributed under the License is distributed on an "AS IS" BASIS,
+# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
+# See the License for the specific language governing permissions and
+# limitations under the License.
+from synapse.config import ConfigError
+from synapse.config.homeserver import HomeServerConfig
+
+from tests.unittest import TestCase
+from tests.utils import default_config
+
+
+class RegistrationConfigTestCase(TestCase):
+ def test_session_lifetime_must_not_be_exceeded_by_smaller_lifetimes(self):
+ """
+ session_lifetime should logically be larger than, or at least as large as,
+ all the different token lifetimes.
+ Test that the user is faced with configuration errors if they make it
+ smaller, as that configuration doesn't make sense.
+ """
+ config_dict = default_config("test")
+
+ # First test all the error conditions
+ with self.assertRaises(ConfigError):
+ HomeServerConfig().parse_config_dict(
+ {
+ "session_lifetime": "30m",
+ "nonrefreshable_access_token_lifetime": "31m",
+ **config_dict,
+ }
+ )
+
+ with self.assertRaises(ConfigError):
+ HomeServerConfig().parse_config_dict(
+ {
+ "session_lifetime": "30m",
+ "refreshable_access_token_lifetime": "31m",
+ **config_dict,
+ }
+ )
+
+ with self.assertRaises(ConfigError):
+ HomeServerConfig().parse_config_dict(
+ {
+ "session_lifetime": "30m",
+ "refresh_token_lifetime": "31m",
+ **config_dict,
+ }
+ )
+
+ # Then test all the fine conditions
+ HomeServerConfig().parse_config_dict(
+ {
+ "session_lifetime": "31m",
+ "nonrefreshable_access_token_lifetime": "31m",
+ **config_dict,
+ }
+ )
+
+ HomeServerConfig().parse_config_dict(
+ {
+ "session_lifetime": "31m",
+ "refreshable_access_token_lifetime": "31m",
+ **config_dict,
+ }
+ )
+
+ HomeServerConfig().parse_config_dict(
+ {"session_lifetime": "31m", "refresh_token_lifetime": "31m", **config_dict}
+ )
diff --git a/tests/federation/test_federation_sender.py b/tests/federation/test_federation_sender.py
index b457dad6d2..b2376e2db9 100644
--- a/tests/federation/test_federation_sender.py
+++ b/tests/federation/test_federation_sender.py
@@ -266,7 +266,8 @@ class FederationSenderDevicesTestCases(HomeserverTestCase):
)
# expect signing key update edu
- self.assertEqual(len(self.edus), 1)
+ self.assertEqual(len(self.edus), 2)
+ self.assertEqual(self.edus.pop(0)["edu_type"], "m.signing_key_update")
self.assertEqual(self.edus.pop(0)["edu_type"], "org.matrix.signing_key_update")
# sign the devices
@@ -491,7 +492,7 @@ class FederationSenderDevicesTestCases(HomeserverTestCase):
) -> None:
"""Check that the txn has an EDU with a signing key update."""
edus = txn["edus"]
- self.assertEqual(len(edus), 1)
+ self.assertEqual(len(edus), 2)
def generate_and_upload_device_signing_key(
self, user_id: str, device_id: str
diff --git a/tests/federation/transport/test_client.py b/tests/federation/transport/test_client.py
index 0b19159961..a7031a55f2 100644
--- a/tests/federation/transport/test_client.py
+++ b/tests/federation/transport/test_client.py
@@ -1,3 +1,17 @@
+# Copyright 2021 The Matrix.org Foundation C.I.C.
+#
+# Licensed under the Apache License, Version 2.0 (the "License");
+# you may not use this file except in compliance with the License.
+# You may obtain a copy of the License at
+#
+# http://www.apache.org/licenses/LICENSE-2.0
+#
+# Unless required by applicable law or agreed to in writing, software
+# distributed under the License is distributed on an "AS IS" BASIS,
+# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
+# See the License for the specific language governing permissions and
+# limitations under the License.
+
import json
from synapse.api.room_versions import RoomVersions
diff --git a/tests/handlers/test_auth.py b/tests/handlers/test_auth.py
index 72e176da75..03b8b8615c 100644
--- a/tests/handlers/test_auth.py
+++ b/tests/handlers/test_auth.py
@@ -71,7 +71,7 @@ class AuthTestCase(unittest.HomeserverTestCase):
def test_short_term_login_token_gives_user_id(self):
token = self.macaroon_generator.generate_short_term_login_token(
- self.user1, "", 5000
+ self.user1, "", duration_in_ms=5000
)
res = self.get_success(self.auth_handler.validate_short_term_login_token(token))
self.assertEqual(self.user1, res.user_id)
@@ -94,7 +94,7 @@ class AuthTestCase(unittest.HomeserverTestCase):
def test_short_term_login_token_cannot_replace_user_id(self):
token = self.macaroon_generator.generate_short_term_login_token(
- self.user1, "", 5000
+ self.user1, "", duration_in_ms=5000
)
macaroon = pymacaroons.Macaroon.deserialize(token)
@@ -213,6 +213,6 @@ class AuthTestCase(unittest.HomeserverTestCase):
def _get_macaroon(self):
token = self.macaroon_generator.generate_short_term_login_token(
- self.user1, "", 5000
+ self.user1, "", duration_in_ms=5000
)
return pymacaroons.Macaroon.deserialize(token)
diff --git a/tests/handlers/test_cas.py b/tests/handlers/test_cas.py
index b625995d12..8705ff8943 100644
--- a/tests/handlers/test_cas.py
+++ b/tests/handlers/test_cas.py
@@ -66,7 +66,13 @@ class CasHandlerTestCase(HomeserverTestCase):
# check that the auth handler got called as expected
auth_handler.complete_sso_login.assert_called_once_with(
- "@test_user:test", "cas", request, "redirect_uri", None, new_user=True
+ "@test_user:test",
+ "cas",
+ request,
+ "redirect_uri",
+ None,
+ new_user=True,
+ auth_provider_session_id=None,
)
def test_map_cas_user_to_existing_user(self):
@@ -89,7 +95,13 @@ class CasHandlerTestCase(HomeserverTestCase):
# check that the auth handler got called as expected
auth_handler.complete_sso_login.assert_called_once_with(
- "@test_user:test", "cas", request, "redirect_uri", None, new_user=False
+ "@test_user:test",
+ "cas",
+ request,
+ "redirect_uri",
+ None,
+ new_user=False,
+ auth_provider_session_id=None,
)
# Subsequent calls should map to the same mxid.
@@ -98,7 +110,13 @@ class CasHandlerTestCase(HomeserverTestCase):
self.handler._handle_cas_response(request, cas_response, "redirect_uri", "")
)
auth_handler.complete_sso_login.assert_called_once_with(
- "@test_user:test", "cas", request, "redirect_uri", None, new_user=False
+ "@test_user:test",
+ "cas",
+ request,
+ "redirect_uri",
+ None,
+ new_user=False,
+ auth_provider_session_id=None,
)
def test_map_cas_user_to_invalid_localpart(self):
@@ -116,7 +134,13 @@ class CasHandlerTestCase(HomeserverTestCase):
# check that the auth handler got called as expected
auth_handler.complete_sso_login.assert_called_once_with(
- "@f=c3=b6=c3=b6:test", "cas", request, "redirect_uri", None, new_user=True
+ "@f=c3=b6=c3=b6:test",
+ "cas",
+ request,
+ "redirect_uri",
+ None,
+ new_user=True,
+ auth_provider_session_id=None,
)
@override_config(
@@ -160,7 +184,13 @@ class CasHandlerTestCase(HomeserverTestCase):
# check that the auth handler got called as expected
auth_handler.complete_sso_login.assert_called_once_with(
- "@test_user:test", "cas", request, "redirect_uri", None, new_user=True
+ "@test_user:test",
+ "cas",
+ request,
+ "redirect_uri",
+ None,
+ new_user=True,
+ auth_provider_session_id=None,
)
diff --git a/tests/handlers/test_oidc.py b/tests/handlers/test_oidc.py
index a25c89bd5b..cfe3de5266 100644
--- a/tests/handlers/test_oidc.py
+++ b/tests/handlers/test_oidc.py
@@ -252,13 +252,6 @@ class OidcHandlerTestCase(HomeserverTestCase):
with patch.object(self.provider, "load_metadata", patched_load_metadata):
self.get_failure(self.provider.load_jwks(force=True), RuntimeError)
- # Return empty key set if JWKS are not used
- self.provider._scopes = [] # not asking the openid scope
- self.http_client.get_json.reset_mock()
- jwks = self.get_success(self.provider.load_jwks(force=True))
- self.http_client.get_json.assert_not_called()
- self.assertEqual(jwks, {"keys": []})
-
@override_config({"oidc_config": DEFAULT_CONFIG})
def test_validate_config(self):
"""Provider metadatas are extensively validated."""
@@ -455,7 +448,13 @@ class OidcHandlerTestCase(HomeserverTestCase):
self.get_success(self.handler.handle_oidc_callback(request))
auth_handler.complete_sso_login.assert_called_once_with(
- expected_user_id, "oidc", request, client_redirect_url, None, new_user=True
+ expected_user_id,
+ "oidc",
+ request,
+ client_redirect_url,
+ None,
+ new_user=True,
+ auth_provider_session_id=None,
)
self.provider._exchange_code.assert_called_once_with(code)
self.provider._parse_id_token.assert_called_once_with(token, nonce=nonce)
@@ -482,17 +481,58 @@ class OidcHandlerTestCase(HomeserverTestCase):
self.provider._fetch_userinfo.reset_mock()
# With userinfo fetching
- self.provider._scopes = [] # do not ask the "openid" scope
+ self.provider._user_profile_method = "userinfo_endpoint"
+ token = {
+ "type": "bearer",
+ "access_token": "access_token",
+ }
+ self.provider._exchange_code = simple_async_mock(return_value=token)
self.get_success(self.handler.handle_oidc_callback(request))
auth_handler.complete_sso_login.assert_called_once_with(
- expected_user_id, "oidc", request, client_redirect_url, None, new_user=False
+ expected_user_id,
+ "oidc",
+ request,
+ client_redirect_url,
+ None,
+ new_user=False,
+ auth_provider_session_id=None,
)
self.provider._exchange_code.assert_called_once_with(code)
self.provider._parse_id_token.assert_not_called()
self.provider._fetch_userinfo.assert_called_once_with(token)
self.render_error.assert_not_called()
+ # With an ID token, userinfo fetching and sid in the ID token
+ self.provider._user_profile_method = "userinfo_endpoint"
+ token = {
+ "type": "bearer",
+ "access_token": "access_token",
+ "id_token": "id_token",
+ }
+ id_token = {
+ "sid": "abcdefgh",
+ }
+ self.provider._parse_id_token = simple_async_mock(return_value=id_token)
+ self.provider._exchange_code = simple_async_mock(return_value=token)
+ auth_handler.complete_sso_login.reset_mock()
+ self.provider._fetch_userinfo.reset_mock()
+ self.get_success(self.handler.handle_oidc_callback(request))
+
+ auth_handler.complete_sso_login.assert_called_once_with(
+ expected_user_id,
+ "oidc",
+ request,
+ client_redirect_url,
+ None,
+ new_user=False,
+ auth_provider_session_id=id_token["sid"],
+ )
+ self.provider._exchange_code.assert_called_once_with(code)
+ self.provider._parse_id_token.assert_called_once_with(token, nonce=nonce)
+ self.provider._fetch_userinfo.assert_called_once_with(token)
+ self.render_error.assert_not_called()
+
# Handle userinfo fetching error
self.provider._fetch_userinfo = simple_async_mock(raises=Exception())
self.get_success(self.handler.handle_oidc_callback(request))
@@ -776,6 +816,7 @@ class OidcHandlerTestCase(HomeserverTestCase):
client_redirect_url,
{"phone": "1234567"},
new_user=True,
+ auth_provider_session_id=None,
)
@override_config({"oidc_config": DEFAULT_CONFIG})
@@ -790,7 +831,13 @@ class OidcHandlerTestCase(HomeserverTestCase):
}
self.get_success(_make_callback_with_userinfo(self.hs, userinfo))
auth_handler.complete_sso_login.assert_called_once_with(
- "@test_user:test", "oidc", ANY, ANY, None, new_user=True
+ "@test_user:test",
+ "oidc",
+ ANY,
+ ANY,
+ None,
+ new_user=True,
+ auth_provider_session_id=None,
)
auth_handler.complete_sso_login.reset_mock()
@@ -801,7 +848,13 @@ class OidcHandlerTestCase(HomeserverTestCase):
}
self.get_success(_make_callback_with_userinfo(self.hs, userinfo))
auth_handler.complete_sso_login.assert_called_once_with(
- "@test_user_2:test", "oidc", ANY, ANY, None, new_user=True
+ "@test_user_2:test",
+ "oidc",
+ ANY,
+ ANY,
+ None,
+ new_user=True,
+ auth_provider_session_id=None,
)
auth_handler.complete_sso_login.reset_mock()
@@ -838,14 +891,26 @@ class OidcHandlerTestCase(HomeserverTestCase):
}
self.get_success(_make_callback_with_userinfo(self.hs, userinfo))
auth_handler.complete_sso_login.assert_called_once_with(
- user.to_string(), "oidc", ANY, ANY, None, new_user=False
+ user.to_string(),
+ "oidc",
+ ANY,
+ ANY,
+ None,
+ new_user=False,
+ auth_provider_session_id=None,
)
auth_handler.complete_sso_login.reset_mock()
# Subsequent calls should map to the same mxid.
self.get_success(_make_callback_with_userinfo(self.hs, userinfo))
auth_handler.complete_sso_login.assert_called_once_with(
- user.to_string(), "oidc", ANY, ANY, None, new_user=False
+ user.to_string(),
+ "oidc",
+ ANY,
+ ANY,
+ None,
+ new_user=False,
+ auth_provider_session_id=None,
)
auth_handler.complete_sso_login.reset_mock()
@@ -860,7 +925,13 @@ class OidcHandlerTestCase(HomeserverTestCase):
}
self.get_success(_make_callback_with_userinfo(self.hs, userinfo))
auth_handler.complete_sso_login.assert_called_once_with(
- user.to_string(), "oidc", ANY, ANY, None, new_user=False
+ user.to_string(),
+ "oidc",
+ ANY,
+ ANY,
+ None,
+ new_user=False,
+ auth_provider_session_id=None,
)
auth_handler.complete_sso_login.reset_mock()
@@ -896,7 +967,13 @@ class OidcHandlerTestCase(HomeserverTestCase):
self.get_success(_make_callback_with_userinfo(self.hs, userinfo))
auth_handler.complete_sso_login.assert_called_once_with(
- "@TEST_USER_2:test", "oidc", ANY, ANY, None, new_user=False
+ "@TEST_USER_2:test",
+ "oidc",
+ ANY,
+ ANY,
+ None,
+ new_user=False,
+ auth_provider_session_id=None,
)
@override_config({"oidc_config": DEFAULT_CONFIG})
@@ -934,7 +1011,13 @@ class OidcHandlerTestCase(HomeserverTestCase):
# test_user is already taken, so test_user1 gets registered instead.
auth_handler.complete_sso_login.assert_called_once_with(
- "@test_user1:test", "oidc", ANY, ANY, None, new_user=True
+ "@test_user1:test",
+ "oidc",
+ ANY,
+ ANY,
+ None,
+ new_user=True,
+ auth_provider_session_id=None,
)
auth_handler.complete_sso_login.reset_mock()
@@ -1018,7 +1101,13 @@ class OidcHandlerTestCase(HomeserverTestCase):
# check that the auth handler got called as expected
auth_handler.complete_sso_login.assert_called_once_with(
- "@tester:test", "oidc", ANY, ANY, None, new_user=True
+ "@tester:test",
+ "oidc",
+ ANY,
+ ANY,
+ None,
+ new_user=True,
+ auth_provider_session_id=None,
)
@override_config(
@@ -1043,7 +1132,13 @@ class OidcHandlerTestCase(HomeserverTestCase):
# check that the auth handler got called as expected
auth_handler.complete_sso_login.assert_called_once_with(
- "@tester:test", "oidc", ANY, ANY, None, new_user=True
+ "@tester:test",
+ "oidc",
+ ANY,
+ ANY,
+ None,
+ new_user=True,
+ auth_provider_session_id=None,
)
@override_config(
@@ -1156,7 +1251,7 @@ async def _make_callback_with_userinfo(
handler = hs.get_oidc_handler()
provider = handler._providers["oidc"]
- provider._exchange_code = simple_async_mock(return_value={})
+ provider._exchange_code = simple_async_mock(return_value={"id_token": ""})
provider._parse_id_token = simple_async_mock(return_value=userinfo)
provider._fetch_userinfo = simple_async_mock(return_value=userinfo)
diff --git a/tests/handlers/test_saml.py b/tests/handlers/test_saml.py
index 8cfc184fef..50551aa6e3 100644
--- a/tests/handlers/test_saml.py
+++ b/tests/handlers/test_saml.py
@@ -130,7 +130,13 @@ class SamlHandlerTestCase(HomeserverTestCase):
# check that the auth handler got called as expected
auth_handler.complete_sso_login.assert_called_once_with(
- "@test_user:test", "saml", request, "redirect_uri", None, new_user=True
+ "@test_user:test",
+ "saml",
+ request,
+ "redirect_uri",
+ None,
+ new_user=True,
+ auth_provider_session_id=None,
)
@override_config({"saml2_config": {"grandfathered_mxid_source_attribute": "mxid"}})
@@ -156,7 +162,13 @@ class SamlHandlerTestCase(HomeserverTestCase):
# check that the auth handler got called as expected
auth_handler.complete_sso_login.assert_called_once_with(
- "@test_user:test", "saml", request, "", None, new_user=False
+ "@test_user:test",
+ "saml",
+ request,
+ "",
+ None,
+ new_user=False,
+ auth_provider_session_id=None,
)
# Subsequent calls should map to the same mxid.
@@ -165,7 +177,13 @@ class SamlHandlerTestCase(HomeserverTestCase):
self.handler._handle_authn_response(request, saml_response, "")
)
auth_handler.complete_sso_login.assert_called_once_with(
- "@test_user:test", "saml", request, "", None, new_user=False
+ "@test_user:test",
+ "saml",
+ request,
+ "",
+ None,
+ new_user=False,
+ auth_provider_session_id=None,
)
def test_map_saml_response_to_invalid_localpart(self):
@@ -213,7 +231,13 @@ class SamlHandlerTestCase(HomeserverTestCase):
# test_user is already taken, so test_user1 gets registered instead.
auth_handler.complete_sso_login.assert_called_once_with(
- "@test_user1:test", "saml", request, "", None, new_user=True
+ "@test_user1:test",
+ "saml",
+ request,
+ "",
+ None,
+ new_user=True,
+ auth_provider_session_id=None,
)
auth_handler.complete_sso_login.reset_mock()
@@ -309,7 +333,13 @@ class SamlHandlerTestCase(HomeserverTestCase):
# check that the auth handler got called as expected
auth_handler.complete_sso_login.assert_called_once_with(
- "@test_user:test", "saml", request, "redirect_uri", None, new_user=True
+ "@test_user:test",
+ "saml",
+ request,
+ "redirect_uri",
+ None,
+ new_user=True,
+ auth_provider_session_id=None,
)
diff --git a/tests/rest/admin/test_admin.py b/tests/rest/admin/test_admin.py
index af849bd471..3adadcb46b 100644
--- a/tests/rest/admin/test_admin.py
+++ b/tests/rest/admin/test_admin.py
@@ -12,9 +12,9 @@
# See the License for the specific language governing permissions and
# limitations under the License.
-import json
import os
import urllib.parse
+from http import HTTPStatus
from unittest.mock import Mock
from twisted.internet.defer import Deferred
@@ -41,7 +41,7 @@ class VersionTestCase(unittest.HomeserverTestCase):
def test_version_string(self):
channel = self.make_request("GET", self.url, shorthand=False)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(
{"server_version", "python_version"}, set(channel.json_body.keys())
)
@@ -70,11 +70,11 @@ class DeleteGroupTestCase(unittest.HomeserverTestCase):
content={"localpart": "test"},
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
group_id = channel.json_body["group_id"]
- self._check_group(group_id, expect_code=200)
+ self._check_group(group_id, expect_code=HTTPStatus.OK)
# Invite/join another user
@@ -82,13 +82,13 @@ class DeleteGroupTestCase(unittest.HomeserverTestCase):
channel = self.make_request(
"PUT", url.encode("ascii"), access_token=self.admin_user_tok, content={}
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
url = "/groups/%s/self/accept_invite" % (group_id,)
channel = self.make_request(
"PUT", url.encode("ascii"), access_token=self.other_user_token, content={}
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Check other user knows they're in the group
self.assertIn(group_id, self._get_groups_user_is_in(self.admin_user_tok))
@@ -103,10 +103,10 @@ class DeleteGroupTestCase(unittest.HomeserverTestCase):
content={"localpart": "test"},
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
- # Check group returns 404
- self._check_group(group_id, expect_code=404)
+ # Check group returns HTTPStatus.NOT_FOUND
+ self._check_group(group_id, expect_code=HTTPStatus.NOT_FOUND)
# Check users don't think they're in the group
self.assertNotIn(group_id, self._get_groups_user_is_in(self.admin_user_tok))
@@ -122,15 +122,13 @@ class DeleteGroupTestCase(unittest.HomeserverTestCase):
"GET", url.encode("ascii"), access_token=self.admin_user_tok
)
- self.assertEqual(
- expect_code, int(channel.result["code"]), msg=channel.result["body"]
- )
+ self.assertEqual(expect_code, channel.code, msg=channel.json_body)
def _get_groups_user_is_in(self, access_token):
"""Returns the list of groups the user is in (given their access token)"""
channel = self.make_request("GET", b"/joined_groups", access_token=access_token)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
return channel.json_body["groups"]
@@ -210,10 +208,10 @@ class QuarantineMediaTestCase(unittest.HomeserverTestCase):
# Should be quarantined
self.assertEqual(
- 404,
- int(channel.code),
+ HTTPStatus.NOT_FOUND,
+ channel.code,
msg=(
- "Expected to receive a 404 on accessing quarantined media: %s"
+ "Expected to receive a HTTPStatus.NOT_FOUND on accessing quarantined media: %s"
% server_and_media_id
),
)
@@ -232,8 +230,8 @@ class QuarantineMediaTestCase(unittest.HomeserverTestCase):
# Expect a forbidden error
self.assertEqual(
- 403,
- int(channel.result["code"]),
+ HTTPStatus.FORBIDDEN,
+ channel.code,
msg="Expected forbidden on quarantining media as a non-admin",
)
@@ -247,8 +245,8 @@ class QuarantineMediaTestCase(unittest.HomeserverTestCase):
# Expect a forbidden error
self.assertEqual(
- 403,
- int(channel.result["code"]),
+ HTTPStatus.FORBIDDEN,
+ channel.code,
msg="Expected forbidden on quarantining media as a non-admin",
)
@@ -279,7 +277,7 @@ class QuarantineMediaTestCase(unittest.HomeserverTestCase):
)
# Should be successful
- self.assertEqual(200, int(channel.code), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code)
# Quarantine the media
url = "/_synapse/admin/v1/media/quarantine/%s/%s" % (
@@ -292,7 +290,7 @@ class QuarantineMediaTestCase(unittest.HomeserverTestCase):
access_token=admin_user_tok,
)
self.pump(1.0)
- self.assertEqual(200, int(channel.code), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Attempt to access the media
self._ensure_quarantined(admin_user_tok, server_name_and_media_id)
@@ -348,11 +346,9 @@ class QuarantineMediaTestCase(unittest.HomeserverTestCase):
access_token=admin_user_tok,
)
self.pump(1.0)
- self.assertEqual(200, int(channel.code), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(
- json.loads(channel.result["body"].decode("utf-8")),
- {"num_quarantined": 2},
- "Expected 2 quarantined items",
+ channel.json_body, {"num_quarantined": 2}, "Expected 2 quarantined items"
)
# Convert mxc URLs to server/media_id strings
@@ -396,11 +392,9 @@ class QuarantineMediaTestCase(unittest.HomeserverTestCase):
access_token=admin_user_tok,
)
self.pump(1.0)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(
- json.loads(channel.result["body"].decode("utf-8")),
- {"num_quarantined": 2},
- "Expected 2 quarantined items",
+ channel.json_body, {"num_quarantined": 2}, "Expected 2 quarantined items"
)
# Attempt to access each piece of media
@@ -432,7 +426,7 @@ class QuarantineMediaTestCase(unittest.HomeserverTestCase):
url = "/_synapse/admin/v1/media/protect/%s" % (urllib.parse.quote(media_id_2),)
channel = self.make_request("POST", url, access_token=admin_user_tok)
self.pump(1.0)
- self.assertEqual(200, int(channel.code), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Quarantine all media by this user
url = "/_synapse/admin/v1/user/%s/media/quarantine" % urllib.parse.quote(
@@ -444,11 +438,9 @@ class QuarantineMediaTestCase(unittest.HomeserverTestCase):
access_token=admin_user_tok,
)
self.pump(1.0)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(
- json.loads(channel.result["body"].decode("utf-8")),
- {"num_quarantined": 1},
- "Expected 1 quarantined item",
+ channel.json_body, {"num_quarantined": 1}, "Expected 1 quarantined item"
)
# Attempt to access each piece of media, the first should fail, the
@@ -467,10 +459,10 @@ class QuarantineMediaTestCase(unittest.HomeserverTestCase):
# Shouldn't be quarantined
self.assertEqual(
- 200,
- int(channel.code),
+ HTTPStatus.OK,
+ channel.code,
msg=(
- "Expected to receive a 200 on accessing not-quarantined media: %s"
+ "Expected to receive a HTTPStatus.OK on accessing not-quarantined media: %s"
% server_and_media_id_2
),
)
@@ -499,7 +491,7 @@ class PurgeHistoryTestCase(unittest.HomeserverTestCase):
def test_purge_history(self):
"""
Simple test of purge history API.
- Test only that is is possible to call, get status 200 and purge_id.
+ Test only that is is possible to call, get status HTTPStatus.OK and purge_id.
"""
channel = self.make_request(
@@ -509,7 +501,7 @@ class PurgeHistoryTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertIn("purge_id", channel.json_body)
purge_id = channel.json_body["purge_id"]
@@ -520,5 +512,5 @@ class PurgeHistoryTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("complete", channel.json_body["status"])
diff --git a/tests/rest/admin/test_background_updates.py b/tests/rest/admin/test_background_updates.py
index 62f242baf6..4d152c0d66 100644
--- a/tests/rest/admin/test_background_updates.py
+++ b/tests/rest/admin/test_background_updates.py
@@ -16,11 +16,14 @@ from typing import Collection
from parameterized import parameterized
+from twisted.test.proto_helpers import MemoryReactor
+
import synapse.rest.admin
from synapse.api.errors import Codes
from synapse.rest.client import login
from synapse.server import HomeServer
from synapse.storage.background_updates import BackgroundUpdater
+from synapse.util import Clock
from tests import unittest
@@ -31,7 +34,7 @@ class BackgroundUpdatesTestCase(unittest.HomeserverTestCase):
login.register_servlets,
]
- def prepare(self, reactor, clock, hs: HomeServer):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
self.store = hs.get_datastore()
self.admin_user = self.register_user("admin", "pass", admin=True)
self.admin_user_tok = self.login("admin", "pass")
@@ -44,9 +47,9 @@ class BackgroundUpdatesTestCase(unittest.HomeserverTestCase):
("POST", "/_synapse/admin/v1/background_updates/start_job"),
]
)
- def test_requester_is_no_admin(self, method: str, url: str):
+ def test_requester_is_no_admin(self, method: str, url: str) -> None:
"""
- If the user is not a server admin, an error 403 is returned.
+ If the user is not a server admin, an error HTTPStatus.FORBIDDEN is returned.
"""
self.register_user("user", "pass", admin=False)
@@ -62,7 +65,7 @@ class BackgroundUpdatesTestCase(unittest.HomeserverTestCase):
self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_invalid_parameter(self):
+ def test_invalid_parameter(self) -> None:
"""
If parameters are invalid, an error is returned.
"""
@@ -90,7 +93,7 @@ class BackgroundUpdatesTestCase(unittest.HomeserverTestCase):
self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
- def _register_bg_update(self):
+ def _register_bg_update(self) -> None:
"Adds a bg update but doesn't start it"
async def _fake_update(progress, batch_size) -> int:
@@ -112,7 +115,7 @@ class BackgroundUpdatesTestCase(unittest.HomeserverTestCase):
)
)
- def test_status_empty(self):
+ def test_status_empty(self) -> None:
"""Test the status API works."""
channel = self.make_request(
@@ -127,7 +130,7 @@ class BackgroundUpdatesTestCase(unittest.HomeserverTestCase):
channel.json_body, {"current_updates": {}, "enabled": True}
)
- def test_status_bg_update(self):
+ def test_status_bg_update(self) -> None:
"""Test the status API works with a background update."""
# Create a new background update
@@ -162,7 +165,7 @@ class BackgroundUpdatesTestCase(unittest.HomeserverTestCase):
},
)
- def test_enabled(self):
+ def test_enabled(self) -> None:
"""Test the enabled API works."""
# Create a new background update
@@ -299,7 +302,7 @@ class BackgroundUpdatesTestCase(unittest.HomeserverTestCase):
),
]
)
- def test_start_backround_job(self, job_name: str, updates: Collection[str]):
+ def test_start_backround_job(self, job_name: str, updates: Collection[str]) -> None:
"""
Test that background updates add to database and be processed.
@@ -341,7 +344,7 @@ class BackgroundUpdatesTestCase(unittest.HomeserverTestCase):
)
)
- def test_start_backround_job_twice(self):
+ def test_start_backround_job_twice(self) -> None:
"""Test that add a background update twice return an error."""
# add job to database
diff --git a/tests/rest/admin/test_device.py b/tests/rest/admin/test_device.py
index a3679be205..f7080bda87 100644
--- a/tests/rest/admin/test_device.py
+++ b/tests/rest/admin/test_device.py
@@ -11,14 +11,18 @@
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
-
import urllib.parse
+from http import HTTPStatus
from parameterized import parameterized
+from twisted.test.proto_helpers import MemoryReactor
+
import synapse.rest.admin
from synapse.api.errors import Codes
from synapse.rest.client import login
+from synapse.server import HomeServer
+from synapse.util import Clock
from tests import unittest
@@ -30,7 +34,7 @@ class DeviceRestTestCase(unittest.HomeserverTestCase):
login.register_servlets,
]
- def prepare(self, reactor, clock, hs):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
self.handler = hs.get_device_handler()
self.admin_user = self.register_user("admin", "pass", admin=True)
@@ -47,17 +51,21 @@ class DeviceRestTestCase(unittest.HomeserverTestCase):
)
@parameterized.expand(["GET", "PUT", "DELETE"])
- def test_no_auth(self, method: str):
+ def test_no_auth(self, method: str) -> None:
"""
Try to get a device of an user without authentication.
"""
channel = self.make_request(method, self.url, b"{}")
- self.assertEqual(401, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.UNAUTHORIZED,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
@parameterized.expand(["GET", "PUT", "DELETE"])
- def test_requester_is_no_admin(self, method: str):
+ def test_requester_is_no_admin(self, method: str) -> None:
"""
If the user is not a server admin, an error is returned.
"""
@@ -67,13 +75,17 @@ class DeviceRestTestCase(unittest.HomeserverTestCase):
access_token=self.other_user_token,
)
- self.assertEqual(403, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.FORBIDDEN,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
@parameterized.expand(["GET", "PUT", "DELETE"])
- def test_user_does_not_exist(self, method: str):
+ def test_user_does_not_exist(self, method: str) -> None:
"""
- Tests that a lookup for a user that does not exist returns a 404
+ Tests that a lookup for a user that does not exist returns a HTTPStatus.NOT_FOUND
"""
url = (
"/_synapse/admin/v2/users/@unknown_person:test/devices/%s"
@@ -86,13 +98,13 @@ class DeviceRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(404, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.NOT_FOUND, channel.code, msg=channel.json_body)
self.assertEqual(Codes.NOT_FOUND, channel.json_body["errcode"])
@parameterized.expand(["GET", "PUT", "DELETE"])
- def test_user_is_not_local(self, method: str):
+ def test_user_is_not_local(self, method: str) -> None:
"""
- Tests that a lookup for a user that is not a local returns a 400
+ Tests that a lookup for a user that is not a local returns a HTTPStatus.BAD_REQUEST
"""
url = (
"/_synapse/admin/v2/users/@unknown_person:unknown_domain/devices/%s"
@@ -105,12 +117,12 @@ class DeviceRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("Can only lookup local users", channel.json_body["error"])
- def test_unknown_device(self):
+ def test_unknown_device(self) -> None:
"""
- Tests that a lookup for a device that does not exist returns either 404 or 200.
+ Tests that a lookup for a device that does not exist returns either HTTPStatus.NOT_FOUND or HTTPStatus.OK.
"""
url = "/_synapse/admin/v2/users/%s/devices/unknown_device" % urllib.parse.quote(
self.other_user
@@ -122,7 +134,7 @@ class DeviceRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(404, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.NOT_FOUND, channel.code, msg=channel.json_body)
self.assertEqual(Codes.NOT_FOUND, channel.json_body["errcode"])
channel = self.make_request(
@@ -131,7 +143,7 @@ class DeviceRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
channel = self.make_request(
"DELETE",
@@ -139,10 +151,10 @@ class DeviceRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- # Delete unknown device returns status 200
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ # Delete unknown device returns status HTTPStatus.OK
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
- def test_update_device_too_long_display_name(self):
+ def test_update_device_too_long_display_name(self) -> None:
"""
Update a device with a display name that is invalid (too long).
"""
@@ -167,7 +179,7 @@ class DeviceRestTestCase(unittest.HomeserverTestCase):
content=update,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.TOO_LARGE, channel.json_body["errcode"])
# Ensure the display name was not updated.
@@ -177,12 +189,12 @@ class DeviceRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("new display", channel.json_body["display_name"])
- def test_update_no_display_name(self):
+ def test_update_no_display_name(self) -> None:
"""
- Tests that a update for a device without JSON returns a 200
+ Tests that a update for a device without JSON returns a HTTPStatus.OK
"""
# Set iniital display name.
update = {"display_name": "new display"}
@@ -198,7 +210,7 @@ class DeviceRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Ensure the display name was not updated.
channel = self.make_request(
@@ -207,10 +219,10 @@ class DeviceRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("new display", channel.json_body["display_name"])
- def test_update_display_name(self):
+ def test_update_display_name(self) -> None:
"""
Tests a normal successful update of display name
"""
@@ -222,7 +234,7 @@ class DeviceRestTestCase(unittest.HomeserverTestCase):
content={"display_name": "new displayname"},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Check new display_name
channel = self.make_request(
@@ -231,10 +243,10 @@ class DeviceRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("new displayname", channel.json_body["display_name"])
- def test_get_device(self):
+ def test_get_device(self) -> None:
"""
Tests that a normal lookup for a device is successfully
"""
@@ -244,7 +256,7 @@ class DeviceRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(self.other_user, channel.json_body["user_id"])
# Check that all fields are available
self.assertIn("user_id", channel.json_body)
@@ -253,7 +265,7 @@ class DeviceRestTestCase(unittest.HomeserverTestCase):
self.assertIn("last_seen_ip", channel.json_body)
self.assertIn("last_seen_ts", channel.json_body)
- def test_delete_device(self):
+ def test_delete_device(self) -> None:
"""
Tests that a remove of a device is successfully
"""
@@ -269,7 +281,7 @@ class DeviceRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Ensure that the number of devices is decreased
res = self.get_success(self.handler.get_devices_by_user(self.other_user))
@@ -283,7 +295,7 @@ class DevicesRestTestCase(unittest.HomeserverTestCase):
login.register_servlets,
]
- def prepare(self, reactor, clock, hs):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
self.admin_user = self.register_user("admin", "pass", admin=True)
self.admin_user_tok = self.login("admin", "pass")
@@ -293,16 +305,20 @@ class DevicesRestTestCase(unittest.HomeserverTestCase):
self.other_user
)
- def test_no_auth(self):
+ def test_no_auth(self) -> None:
"""
Try to list devices of an user without authentication.
"""
channel = self.make_request("GET", self.url, b"{}")
- self.assertEqual(401, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.UNAUTHORIZED,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
- def test_requester_is_no_admin(self):
+ def test_requester_is_no_admin(self) -> None:
"""
If the user is not a server admin, an error is returned.
"""
@@ -314,12 +330,16 @@ class DevicesRestTestCase(unittest.HomeserverTestCase):
access_token=other_user_token,
)
- self.assertEqual(403, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.FORBIDDEN,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_user_does_not_exist(self):
+ def test_user_does_not_exist(self) -> None:
"""
- Tests that a lookup for a user that does not exist returns a 404
+ Tests that a lookup for a user that does not exist returns a HTTPStatus.NOT_FOUND
"""
url = "/_synapse/admin/v2/users/@unknown_person:test/devices"
channel = self.make_request(
@@ -328,12 +348,12 @@ class DevicesRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(404, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.NOT_FOUND, channel.code, msg=channel.json_body)
self.assertEqual(Codes.NOT_FOUND, channel.json_body["errcode"])
- def test_user_is_not_local(self):
+ def test_user_is_not_local(self) -> None:
"""
- Tests that a lookup for a user that is not a local returns a 400
+ Tests that a lookup for a user that is not a local returns a HTTPStatus.BAD_REQUEST
"""
url = "/_synapse/admin/v2/users/@unknown_person:unknown_domain/devices"
@@ -343,10 +363,10 @@ class DevicesRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("Can only lookup local users", channel.json_body["error"])
- def test_user_has_no_devices(self):
+ def test_user_has_no_devices(self) -> None:
"""
Tests that a normal lookup for devices is successfully
if user has no devices
@@ -359,11 +379,11 @@ class DevicesRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(0, channel.json_body["total"])
self.assertEqual(0, len(channel.json_body["devices"]))
- def test_get_devices(self):
+ def test_get_devices(self) -> None:
"""
Tests that a normal lookup for devices is successfully
"""
@@ -379,7 +399,7 @@ class DevicesRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(number_devices, channel.json_body["total"])
self.assertEqual(number_devices, len(channel.json_body["devices"]))
self.assertEqual(self.other_user, channel.json_body["devices"][0]["user_id"])
@@ -399,7 +419,7 @@ class DeleteDevicesRestTestCase(unittest.HomeserverTestCase):
login.register_servlets,
]
- def prepare(self, reactor, clock, hs):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
self.handler = hs.get_device_handler()
self.admin_user = self.register_user("admin", "pass", admin=True)
@@ -411,16 +431,20 @@ class DeleteDevicesRestTestCase(unittest.HomeserverTestCase):
self.other_user
)
- def test_no_auth(self):
+ def test_no_auth(self) -> None:
"""
Try to delete devices of an user without authentication.
"""
channel = self.make_request("POST", self.url, b"{}")
- self.assertEqual(401, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.UNAUTHORIZED,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
- def test_requester_is_no_admin(self):
+ def test_requester_is_no_admin(self) -> None:
"""
If the user is not a server admin, an error is returned.
"""
@@ -432,12 +456,16 @@ class DeleteDevicesRestTestCase(unittest.HomeserverTestCase):
access_token=other_user_token,
)
- self.assertEqual(403, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.FORBIDDEN,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_user_does_not_exist(self):
+ def test_user_does_not_exist(self) -> None:
"""
- Tests that a lookup for a user that does not exist returns a 404
+ Tests that a lookup for a user that does not exist returns a HTTPStatus.NOT_FOUND
"""
url = "/_synapse/admin/v2/users/@unknown_person:test/delete_devices"
channel = self.make_request(
@@ -446,12 +474,12 @@ class DeleteDevicesRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(404, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.NOT_FOUND, channel.code, msg=channel.json_body)
self.assertEqual(Codes.NOT_FOUND, channel.json_body["errcode"])
- def test_user_is_not_local(self):
+ def test_user_is_not_local(self) -> None:
"""
- Tests that a lookup for a user that is not a local returns a 400
+ Tests that a lookup for a user that is not a local returns a HTTPStatus.BAD_REQUEST
"""
url = "/_synapse/admin/v2/users/@unknown_person:unknown_domain/delete_devices"
@@ -461,12 +489,12 @@ class DeleteDevicesRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("Can only lookup local users", channel.json_body["error"])
- def test_unknown_devices(self):
+ def test_unknown_devices(self) -> None:
"""
- Tests that a remove of a device that does not exist returns 200.
+ Tests that a remove of a device that does not exist returns HTTPStatus.OK.
"""
channel = self.make_request(
"POST",
@@ -475,10 +503,10 @@ class DeleteDevicesRestTestCase(unittest.HomeserverTestCase):
content={"devices": ["unknown_device1", "unknown_device2"]},
)
- # Delete unknown devices returns status 200
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ # Delete unknown devices returns status HTTPStatus.OK
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
- def test_delete_devices(self):
+ def test_delete_devices(self) -> None:
"""
Tests that a remove of devices is successfully
"""
@@ -505,7 +533,7 @@ class DeleteDevicesRestTestCase(unittest.HomeserverTestCase):
content={"devices": device_ids},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
res = self.get_success(self.handler.get_devices_by_user(self.other_user))
self.assertEqual(0, len(res))
diff --git a/tests/rest/admin/test_event_reports.py b/tests/rest/admin/test_event_reports.py
index e9ef89731f..4f89f8b534 100644
--- a/tests/rest/admin/test_event_reports.py
+++ b/tests/rest/admin/test_event_reports.py
@@ -11,12 +11,17 @@
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
+from http import HTTPStatus
+from typing import List
-import json
+from twisted.test.proto_helpers import MemoryReactor
import synapse.rest.admin
from synapse.api.errors import Codes
from synapse.rest.client import login, report_event, room
+from synapse.server import HomeServer
+from synapse.types import JsonDict
+from synapse.util import Clock
from tests import unittest
@@ -29,7 +34,7 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
report_event.register_servlets,
]
- def prepare(self, reactor, clock, hs):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
self.admin_user = self.register_user("admin", "pass", admin=True)
self.admin_user_tok = self.login("admin", "pass")
@@ -70,18 +75,22 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
self.url = "/_synapse/admin/v1/event_reports"
- def test_no_auth(self):
+ def test_no_auth(self) -> None:
"""
Try to get an event report without authentication.
"""
channel = self.make_request("GET", self.url, b"{}")
- self.assertEqual(401, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.UNAUTHORIZED,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
- def test_requester_is_no_admin(self):
+ def test_requester_is_no_admin(self) -> None:
"""
- If the user is not a server admin, an error 403 is returned.
+ If the user is not a server admin, an error HTTPStatus.FORBIDDEN is returned.
"""
channel = self.make_request(
@@ -90,10 +99,14 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
access_token=self.other_user_tok,
)
- self.assertEqual(403, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.FORBIDDEN,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_default_success(self):
+ def test_default_success(self) -> None:
"""
Testing list of reported events
"""
@@ -104,13 +117,13 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 20)
self.assertEqual(len(channel.json_body["event_reports"]), 20)
self.assertNotIn("next_token", channel.json_body)
self._check_fields(channel.json_body["event_reports"])
- def test_limit(self):
+ def test_limit(self) -> None:
"""
Testing list of reported events with limit
"""
@@ -121,13 +134,13 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 20)
self.assertEqual(len(channel.json_body["event_reports"]), 5)
self.assertEqual(channel.json_body["next_token"], 5)
self._check_fields(channel.json_body["event_reports"])
- def test_from(self):
+ def test_from(self) -> None:
"""
Testing list of reported events with a defined starting point (from)
"""
@@ -138,13 +151,13 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 20)
self.assertEqual(len(channel.json_body["event_reports"]), 15)
self.assertNotIn("next_token", channel.json_body)
self._check_fields(channel.json_body["event_reports"])
- def test_limit_and_from(self):
+ def test_limit_and_from(self) -> None:
"""
Testing list of reported events with a defined starting point and limit
"""
@@ -155,13 +168,13 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 20)
self.assertEqual(channel.json_body["next_token"], 15)
self.assertEqual(len(channel.json_body["event_reports"]), 10)
self._check_fields(channel.json_body["event_reports"])
- def test_filter_room(self):
+ def test_filter_room(self) -> None:
"""
Testing list of reported events with a filter of room
"""
@@ -172,7 +185,7 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 10)
self.assertEqual(len(channel.json_body["event_reports"]), 10)
self.assertNotIn("next_token", channel.json_body)
@@ -181,7 +194,7 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
for report in channel.json_body["event_reports"]:
self.assertEqual(report["room_id"], self.room_id1)
- def test_filter_user(self):
+ def test_filter_user(self) -> None:
"""
Testing list of reported events with a filter of user
"""
@@ -192,7 +205,7 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 10)
self.assertEqual(len(channel.json_body["event_reports"]), 10)
self.assertNotIn("next_token", channel.json_body)
@@ -201,7 +214,7 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
for report in channel.json_body["event_reports"]:
self.assertEqual(report["user_id"], self.other_user)
- def test_filter_user_and_room(self):
+ def test_filter_user_and_room(self) -> None:
"""
Testing list of reported events with a filter of user and room
"""
@@ -212,7 +225,7 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 5)
self.assertEqual(len(channel.json_body["event_reports"]), 5)
self.assertNotIn("next_token", channel.json_body)
@@ -222,7 +235,7 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
self.assertEqual(report["user_id"], self.other_user)
self.assertEqual(report["room_id"], self.room_id1)
- def test_valid_search_order(self):
+ def test_valid_search_order(self) -> None:
"""
Testing search order. Order by timestamps.
"""
@@ -234,7 +247,7 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 20)
self.assertEqual(len(channel.json_body["event_reports"]), 20)
report = 1
@@ -252,7 +265,7 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 20)
self.assertEqual(len(channel.json_body["event_reports"]), 20)
report = 1
@@ -263,9 +276,9 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
)
report += 1
- def test_invalid_search_order(self):
+ def test_invalid_search_order(self) -> None:
"""
- Testing that a invalid search order returns a 400
+ Testing that a invalid search order returns a HTTPStatus.BAD_REQUEST
"""
channel = self.make_request(
@@ -274,13 +287,17 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
self.assertEqual("Unknown direction: bar", channel.json_body["error"])
- def test_limit_is_negative(self):
+ def test_limit_is_negative(self) -> None:
"""
- Testing that a negative limit parameter returns a 400
+ Testing that a negative limit parameter returns a HTTPStatus.BAD_REQUEST
"""
channel = self.make_request(
@@ -289,12 +306,16 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
- def test_from_is_negative(self):
+ def test_from_is_negative(self) -> None:
"""
- Testing that a negative from parameter returns a 400
+ Testing that a negative from parameter returns a HTTPStatus.BAD_REQUEST
"""
channel = self.make_request(
@@ -303,10 +324,14 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
- def test_next_token(self):
+ def test_next_token(self) -> None:
"""
Testing that `next_token` appears at the right place
"""
@@ -319,7 +344,7 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 20)
self.assertEqual(len(channel.json_body["event_reports"]), 20)
self.assertNotIn("next_token", channel.json_body)
@@ -332,7 +357,7 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 20)
self.assertEqual(len(channel.json_body["event_reports"]), 20)
self.assertNotIn("next_token", channel.json_body)
@@ -345,7 +370,7 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 20)
self.assertEqual(len(channel.json_body["event_reports"]), 19)
self.assertEqual(channel.json_body["next_token"], 19)
@@ -359,12 +384,12 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 20)
self.assertEqual(len(channel.json_body["event_reports"]), 1)
self.assertNotIn("next_token", channel.json_body)
- def _create_event_and_report(self, room_id, user_tok):
+ def _create_event_and_report(self, room_id: str, user_tok: str) -> None:
"""Create and report events"""
resp = self.helper.send(room_id, tok=user_tok)
event_id = resp["event_id"]
@@ -372,12 +397,14 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
channel = self.make_request(
"POST",
"rooms/%s/report/%s" % (room_id, event_id),
- json.dumps({"score": -100, "reason": "this makes me sad"}),
+ {"score": -100, "reason": "this makes me sad"},
access_token=user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
- def _create_event_and_report_without_parameters(self, room_id, user_tok):
+ def _create_event_and_report_without_parameters(
+ self, room_id: str, user_tok: str
+ ) -> None:
"""Create and report an event, but omit reason and score"""
resp = self.helper.send(room_id, tok=user_tok)
event_id = resp["event_id"]
@@ -385,12 +412,12 @@ class EventReportsTestCase(unittest.HomeserverTestCase):
channel = self.make_request(
"POST",
"rooms/%s/report/%s" % (room_id, event_id),
- json.dumps({}),
+ {},
access_token=user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
- def _check_fields(self, content):
+ def _check_fields(self, content: List[JsonDict]) -> None:
"""Checks that all attributes are present in an event report"""
for c in content:
self.assertIn("id", c)
@@ -413,7 +440,7 @@ class EventReportDetailTestCase(unittest.HomeserverTestCase):
report_event.register_servlets,
]
- def prepare(self, reactor, clock, hs):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
self.admin_user = self.register_user("admin", "pass", admin=True)
self.admin_user_tok = self.login("admin", "pass")
@@ -433,18 +460,22 @@ class EventReportDetailTestCase(unittest.HomeserverTestCase):
# first created event report gets `id`=2
self.url = "/_synapse/admin/v1/event_reports/2"
- def test_no_auth(self):
+ def test_no_auth(self) -> None:
"""
Try to get event report without authentication.
"""
channel = self.make_request("GET", self.url, b"{}")
- self.assertEqual(401, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.UNAUTHORIZED,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
- def test_requester_is_no_admin(self):
+ def test_requester_is_no_admin(self) -> None:
"""
- If the user is not a server admin, an error 403 is returned.
+ If the user is not a server admin, an error HTTPStatus.FORBIDDEN is returned.
"""
channel = self.make_request(
@@ -453,10 +484,14 @@ class EventReportDetailTestCase(unittest.HomeserverTestCase):
access_token=self.other_user_tok,
)
- self.assertEqual(403, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.FORBIDDEN,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_default_success(self):
+ def test_default_success(self) -> None:
"""
Testing get a reported event
"""
@@ -467,12 +502,12 @@ class EventReportDetailTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self._check_fields(channel.json_body)
- def test_invalid_report_id(self):
+ def test_invalid_report_id(self) -> None:
"""
- Testing that an invalid `report_id` returns a 400.
+ Testing that an invalid `report_id` returns a HTTPStatus.BAD_REQUEST.
"""
# `report_id` is negative
@@ -482,7 +517,11 @@ class EventReportDetailTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
self.assertEqual(
"The report_id parameter must be a string representing a positive integer.",
@@ -496,7 +535,11 @@ class EventReportDetailTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
self.assertEqual(
"The report_id parameter must be a string representing a positive integer.",
@@ -510,16 +553,20 @@ class EventReportDetailTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
self.assertEqual(
"The report_id parameter must be a string representing a positive integer.",
channel.json_body["error"],
)
- def test_report_id_not_found(self):
+ def test_report_id_not_found(self) -> None:
"""
- Testing that a not existing `report_id` returns a 404.
+ Testing that a not existing `report_id` returns a HTTPStatus.NOT_FOUND.
"""
channel = self.make_request(
@@ -528,11 +575,15 @@ class EventReportDetailTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(404, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.NOT_FOUND,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.NOT_FOUND, channel.json_body["errcode"])
self.assertEqual("Event report not found", channel.json_body["error"])
- def _create_event_and_report(self, room_id, user_tok):
+ def _create_event_and_report(self, room_id: str, user_tok: str) -> None:
"""Create and report events"""
resp = self.helper.send(room_id, tok=user_tok)
event_id = resp["event_id"]
@@ -540,12 +591,12 @@ class EventReportDetailTestCase(unittest.HomeserverTestCase):
channel = self.make_request(
"POST",
"rooms/%s/report/%s" % (room_id, event_id),
- json.dumps({"score": -100, "reason": "this makes me sad"}),
+ {"score": -100, "reason": "this makes me sad"},
access_token=user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
- def _check_fields(self, content):
+ def _check_fields(self, content: JsonDict) -> None:
"""Checks that all attributes are present in a event report"""
self.assertIn("id", content)
self.assertIn("received_ts", content)
diff --git a/tests/rest/admin/test_federation.py b/tests/rest/admin/test_federation.py
new file mode 100644
index 0000000000..5188499ef2
--- /dev/null
+++ b/tests/rest/admin/test_federation.py
@@ -0,0 +1,456 @@
+# Copyright 2021 The Matrix.org Foundation C.I.C.
+#
+# Licensed under the Apache License, Version 2.0 (the "License");
+# you may not use this file except in compliance with the License.
+# You may obtain a copy of the License at
+#
+# http://www.apache.org/licenses/LICENSE-2.0
+#
+# Unless required by applicable law or agreed to in writing, software
+# distributed under the License is distributed on an "AS IS" BASIS,
+# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
+# See the License for the specific language governing permissions and
+# limitations under the License.
+from http import HTTPStatus
+from typing import List, Optional
+
+from parameterized import parameterized
+
+import synapse.rest.admin
+from synapse.api.errors import Codes
+from synapse.rest.client import login
+from synapse.server import HomeServer
+from synapse.types import JsonDict
+
+from tests import unittest
+
+
+class FederationTestCase(unittest.HomeserverTestCase):
+ servlets = [
+ synapse.rest.admin.register_servlets,
+ login.register_servlets,
+ ]
+
+ def prepare(self, reactor, clock, hs: HomeServer):
+ self.store = hs.get_datastore()
+ self.register_user("admin", "pass", admin=True)
+ self.admin_user_tok = self.login("admin", "pass")
+
+ self.url = "/_synapse/admin/v1/federation/destinations"
+
+ @parameterized.expand(
+ [
+ ("/_synapse/admin/v1/federation/destinations",),
+ ("/_synapse/admin/v1/federation/destinations/dummy",),
+ ]
+ )
+ def test_requester_is_no_admin(self, url: str):
+ """
+ If the user is not a server admin, an error 403 is returned.
+ """
+
+ self.register_user("user", "pass", admin=False)
+ other_user_tok = self.login("user", "pass")
+
+ channel = self.make_request(
+ "GET",
+ url,
+ content={},
+ access_token=other_user_tok,
+ )
+
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
+ self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
+
+ def test_invalid_parameter(self):
+ """
+ If parameters are invalid, an error is returned.
+ """
+
+ # negative limit
+ channel = self.make_request(
+ "GET",
+ self.url + "?limit=-5",
+ access_token=self.admin_user_tok,
+ )
+
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
+ self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
+
+ # negative from
+ channel = self.make_request(
+ "GET",
+ self.url + "?from=-5",
+ access_token=self.admin_user_tok,
+ )
+
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
+ self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
+
+ # unkown order_by
+ channel = self.make_request(
+ "GET",
+ self.url + "?order_by=bar",
+ access_token=self.admin_user_tok,
+ )
+
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
+ self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
+
+ # invalid search order
+ channel = self.make_request(
+ "GET",
+ self.url + "?dir=bar",
+ access_token=self.admin_user_tok,
+ )
+
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
+ self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
+
+ # invalid destination
+ channel = self.make_request(
+ "GET",
+ self.url + "/dummy",
+ access_token=self.admin_user_tok,
+ )
+
+ self.assertEqual(HTTPStatus.NOT_FOUND, channel.code, msg=channel.json_body)
+ self.assertEqual(Codes.NOT_FOUND, channel.json_body["errcode"])
+
+ def test_limit(self):
+ """
+ Testing list of destinations with limit
+ """
+
+ number_destinations = 20
+ self._create_destinations(number_destinations)
+
+ channel = self.make_request(
+ "GET",
+ self.url + "?limit=5",
+ access_token=self.admin_user_tok,
+ )
+
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
+ self.assertEqual(channel.json_body["total"], number_destinations)
+ self.assertEqual(len(channel.json_body["destinations"]), 5)
+ self.assertEqual(channel.json_body["next_token"], "5")
+ self._check_fields(channel.json_body["destinations"])
+
+ def test_from(self):
+ """
+ Testing list of destinations with a defined starting point (from)
+ """
+
+ number_destinations = 20
+ self._create_destinations(number_destinations)
+
+ channel = self.make_request(
+ "GET",
+ self.url + "?from=5",
+ access_token=self.admin_user_tok,
+ )
+
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
+ self.assertEqual(channel.json_body["total"], number_destinations)
+ self.assertEqual(len(channel.json_body["destinations"]), 15)
+ self.assertNotIn("next_token", channel.json_body)
+ self._check_fields(channel.json_body["destinations"])
+
+ def test_limit_and_from(self):
+ """
+ Testing list of destinations with a defined starting point and limit
+ """
+
+ number_destinations = 20
+ self._create_destinations(number_destinations)
+
+ channel = self.make_request(
+ "GET",
+ self.url + "?from=5&limit=10",
+ access_token=self.admin_user_tok,
+ )
+
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
+ self.assertEqual(channel.json_body["total"], number_destinations)
+ self.assertEqual(channel.json_body["next_token"], "15")
+ self.assertEqual(len(channel.json_body["destinations"]), 10)
+ self._check_fields(channel.json_body["destinations"])
+
+ def test_next_token(self):
+ """
+ Testing that `next_token` appears at the right place
+ """
+
+ number_destinations = 20
+ self._create_destinations(number_destinations)
+
+ # `next_token` does not appear
+ # Number of results is the number of entries
+ channel = self.make_request(
+ "GET",
+ self.url + "?limit=20",
+ access_token=self.admin_user_tok,
+ )
+
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
+ self.assertEqual(channel.json_body["total"], number_destinations)
+ self.assertEqual(len(channel.json_body["destinations"]), number_destinations)
+ self.assertNotIn("next_token", channel.json_body)
+
+ # `next_token` does not appear
+ # Number of max results is larger than the number of entries
+ channel = self.make_request(
+ "GET",
+ self.url + "?limit=21",
+ access_token=self.admin_user_tok,
+ )
+
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
+ self.assertEqual(channel.json_body["total"], number_destinations)
+ self.assertEqual(len(channel.json_body["destinations"]), number_destinations)
+ self.assertNotIn("next_token", channel.json_body)
+
+ # `next_token` does appear
+ # Number of max results is smaller than the number of entries
+ channel = self.make_request(
+ "GET",
+ self.url + "?limit=19",
+ access_token=self.admin_user_tok,
+ )
+
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
+ self.assertEqual(channel.json_body["total"], number_destinations)
+ self.assertEqual(len(channel.json_body["destinations"]), 19)
+ self.assertEqual(channel.json_body["next_token"], "19")
+
+ # Check
+ # Set `from` to value of `next_token` for request remaining entries
+ # `next_token` does not appear
+ channel = self.make_request(
+ "GET",
+ self.url + "?from=19",
+ access_token=self.admin_user_tok,
+ )
+
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
+ self.assertEqual(channel.json_body["total"], number_destinations)
+ self.assertEqual(len(channel.json_body["destinations"]), 1)
+ self.assertNotIn("next_token", channel.json_body)
+
+ def test_list_all_destinations(self):
+ """
+ List all destinations.
+ """
+ number_destinations = 5
+ self._create_destinations(number_destinations)
+
+ channel = self.make_request(
+ "GET",
+ self.url,
+ {},
+ access_token=self.admin_user_tok,
+ )
+
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
+ self.assertEqual(number_destinations, len(channel.json_body["destinations"]))
+ self.assertEqual(number_destinations, channel.json_body["total"])
+
+ # Check that all fields are available
+ self._check_fields(channel.json_body["destinations"])
+
+ def test_order_by(self):
+ """
+ Testing order list with parameter `order_by`
+ """
+
+ def _order_test(
+ expected_destination_list: List[str],
+ order_by: Optional[str],
+ dir: Optional[str] = None,
+ ):
+ """Request the list of destinations in a certain order.
+ Assert that order is what we expect
+
+ Args:
+ expected_destination_list: The list of user_id in the order
+ we expect to get back from the server
+ order_by: The type of ordering to give the server
+ dir: The direction of ordering to give the server
+ """
+
+ url = f"{self.url}?"
+ if order_by is not None:
+ url += f"order_by={order_by}&"
+ if dir is not None and dir in ("b", "f"):
+ url += f"dir={dir}"
+ channel = self.make_request(
+ "GET",
+ url,
+ access_token=self.admin_user_tok,
+ )
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
+ self.assertEqual(channel.json_body["total"], len(expected_destination_list))
+
+ returned_order = [
+ row["destination"] for row in channel.json_body["destinations"]
+ ]
+ self.assertEqual(expected_destination_list, returned_order)
+ self._check_fields(channel.json_body["destinations"])
+
+ # create destinations
+ dest = [
+ ("sub-a.example.com", 100, 300, 200, 300),
+ ("sub-b.example.com", 200, 200, 100, 100),
+ ("sub-c.example.com", 300, 100, 300, 200),
+ ]
+ for (
+ destination,
+ failure_ts,
+ retry_last_ts,
+ retry_interval,
+ last_successful_stream_ordering,
+ ) in dest:
+ self.get_success(
+ self.store.set_destination_retry_timings(
+ destination, failure_ts, retry_last_ts, retry_interval
+ )
+ )
+ self.get_success(
+ self.store.set_destination_last_successful_stream_ordering(
+ destination, last_successful_stream_ordering
+ )
+ )
+
+ # order by default (destination)
+ _order_test([dest[0][0], dest[1][0], dest[2][0]], None)
+ _order_test([dest[0][0], dest[1][0], dest[2][0]], None, "f")
+ _order_test([dest[2][0], dest[1][0], dest[0][0]], None, "b")
+
+ # order by destination
+ _order_test([dest[0][0], dest[1][0], dest[2][0]], "destination")
+ _order_test([dest[0][0], dest[1][0], dest[2][0]], "destination", "f")
+ _order_test([dest[2][0], dest[1][0], dest[0][0]], "destination", "b")
+
+ # order by failure_ts
+ _order_test([dest[0][0], dest[1][0], dest[2][0]], "failure_ts")
+ _order_test([dest[0][0], dest[1][0], dest[2][0]], "failure_ts", "f")
+ _order_test([dest[2][0], dest[1][0], dest[0][0]], "failure_ts", "b")
+
+ # order by retry_last_ts
+ _order_test([dest[2][0], dest[1][0], dest[0][0]], "retry_last_ts")
+ _order_test([dest[2][0], dest[1][0], dest[0][0]], "retry_last_ts", "f")
+ _order_test([dest[0][0], dest[1][0], dest[2][0]], "retry_last_ts", "b")
+
+ # order by retry_interval
+ _order_test([dest[1][0], dest[0][0], dest[2][0]], "retry_interval")
+ _order_test([dest[1][0], dest[0][0], dest[2][0]], "retry_interval", "f")
+ _order_test([dest[2][0], dest[0][0], dest[1][0]], "retry_interval", "b")
+
+ # order by last_successful_stream_ordering
+ _order_test(
+ [dest[1][0], dest[2][0], dest[0][0]], "last_successful_stream_ordering"
+ )
+ _order_test(
+ [dest[1][0], dest[2][0], dest[0][0]], "last_successful_stream_ordering", "f"
+ )
+ _order_test(
+ [dest[0][0], dest[2][0], dest[1][0]], "last_successful_stream_ordering", "b"
+ )
+
+ def test_search_term(self):
+ """Test that searching for a destination works correctly"""
+
+ def _search_test(
+ expected_destination: Optional[str],
+ search_term: str,
+ ):
+ """Search for a destination and check that the returned destinationis a match
+
+ Args:
+ expected_destination: The room_id expected to be returned by the API.
+ Set to None to expect zero results for the search
+ search_term: The term to search for room names with
+ """
+ url = f"{self.url}?destination={search_term}"
+ channel = self.make_request(
+ "GET",
+ url.encode("ascii"),
+ access_token=self.admin_user_tok,
+ )
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
+
+ # Check that destinations were returned
+ self.assertTrue("destinations" in channel.json_body)
+ self._check_fields(channel.json_body["destinations"])
+ destinations = channel.json_body["destinations"]
+
+ # Check that the expected number of destinations were returned
+ expected_destination_count = 1 if expected_destination else 0
+ self.assertEqual(len(destinations), expected_destination_count)
+ self.assertEqual(channel.json_body["total"], expected_destination_count)
+
+ if expected_destination:
+ # Check that the first returned destination is correct
+ self.assertEqual(expected_destination, destinations[0]["destination"])
+
+ number_destinations = 3
+ self._create_destinations(number_destinations)
+
+ # Test searching
+ _search_test("sub0.example.com", "0")
+ _search_test("sub0.example.com", "sub0")
+
+ _search_test("sub1.example.com", "1")
+ _search_test("sub1.example.com", "1.")
+
+ # Test case insensitive
+ _search_test("sub0.example.com", "SUB0")
+
+ _search_test(None, "foo")
+ _search_test(None, "bar")
+
+ def test_get_single_destination(self):
+ """
+ Get one specific destinations.
+ """
+ self._create_destinations(5)
+
+ channel = self.make_request(
+ "GET",
+ self.url + "/sub0.example.com",
+ access_token=self.admin_user_tok,
+ )
+
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
+ self.assertEqual("sub0.example.com", channel.json_body["destination"])
+
+ # Check that all fields are available
+ # convert channel.json_body into a List
+ self._check_fields([channel.json_body])
+
+ def _create_destinations(self, number_destinations: int):
+ """Create a number of destinations
+
+ Args:
+ number_destinations: Number of destinations to be created
+ """
+ for i in range(0, number_destinations):
+ dest = f"sub{i}.example.com"
+ self.get_success(self.store.set_destination_retry_timings(dest, 50, 50, 50))
+ self.get_success(
+ self.store.set_destination_last_successful_stream_ordering(dest, 100)
+ )
+
+ def _check_fields(self, content: List[JsonDict]):
+ """Checks that the expected destination attributes are present in content
+
+ Args:
+ content: List that is checked for content
+ """
+ for c in content:
+ self.assertIn("destination", c)
+ self.assertIn("retry_last_ts", c)
+ self.assertIn("retry_interval", c)
+ self.assertIn("failure_ts", c)
+ self.assertIn("last_successful_stream_ordering", c)
diff --git a/tests/rest/admin/test_media.py b/tests/rest/admin/test_media.py
index db0e78c039..81e578fd26 100644
--- a/tests/rest/admin/test_media.py
+++ b/tests/rest/admin/test_media.py
@@ -12,16 +12,19 @@
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
-
-import json
import os
+from http import HTTPStatus
from parameterized import parameterized
+from twisted.test.proto_helpers import MemoryReactor
+
import synapse.rest.admin
from synapse.api.errors import Codes
from synapse.rest.client import login, profile, room
from synapse.rest.media.v1.filepath import MediaFilePaths
+from synapse.server import HomeServer
+from synapse.util import Clock
from tests import unittest
from tests.server import FakeSite, make_request
@@ -39,7 +42,7 @@ class DeleteMediaByIDTestCase(unittest.HomeserverTestCase):
login.register_servlets,
]
- def prepare(self, reactor, clock, hs):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
self.media_repo = hs.get_media_repository_resource()
self.server_name = hs.hostname
@@ -48,7 +51,7 @@ class DeleteMediaByIDTestCase(unittest.HomeserverTestCase):
self.filepaths = MediaFilePaths(hs.config.media.media_store_path)
- def test_no_auth(self):
+ def test_no_auth(self) -> None:
"""
Try to delete media without authentication.
"""
@@ -56,10 +59,14 @@ class DeleteMediaByIDTestCase(unittest.HomeserverTestCase):
channel = self.make_request("DELETE", url, b"{}")
- self.assertEqual(401, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.UNAUTHORIZED,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
- def test_requester_is_no_admin(self):
+ def test_requester_is_no_admin(self) -> None:
"""
If the user is not a server admin, an error is returned.
"""
@@ -74,12 +81,16 @@ class DeleteMediaByIDTestCase(unittest.HomeserverTestCase):
access_token=self.other_user_token,
)
- self.assertEqual(403, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.FORBIDDEN,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_media_does_not_exist(self):
+ def test_media_does_not_exist(self) -> None:
"""
- Tests that a lookup for a media that does not exist returns a 404
+ Tests that a lookup for a media that does not exist returns a HTTPStatus.NOT_FOUND
"""
url = "/_synapse/admin/v1/media/%s/%s" % (self.server_name, "12345")
@@ -89,12 +100,12 @@ class DeleteMediaByIDTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(404, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.NOT_FOUND, channel.code, msg=channel.json_body)
self.assertEqual(Codes.NOT_FOUND, channel.json_body["errcode"])
- def test_media_is_not_local(self):
+ def test_media_is_not_local(self) -> None:
"""
- Tests that a lookup for a media that is not a local returns a 400
+ Tests that a lookup for a media that is not a local returns a HTTPStatus.BAD_REQUEST
"""
url = "/_synapse/admin/v1/media/%s/%s" % ("unknown_domain", "12345")
@@ -104,10 +115,10 @@ class DeleteMediaByIDTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("Can only delete local media", channel.json_body["error"])
- def test_delete_media(self):
+ def test_delete_media(self) -> None:
"""
Tests that delete a media is successfully
"""
@@ -117,7 +128,10 @@ class DeleteMediaByIDTestCase(unittest.HomeserverTestCase):
# Upload some media into the room
response = self.helper.upload_media(
- upload_resource, SMALL_PNG, tok=self.admin_user_tok, expect_code=200
+ upload_resource,
+ SMALL_PNG,
+ tok=self.admin_user_tok,
+ expect_code=HTTPStatus.OK,
)
# Extract media ID from the response
server_and_media_id = response["content_uri"][6:] # Cut off 'mxc://'
@@ -137,10 +151,11 @@ class DeleteMediaByIDTestCase(unittest.HomeserverTestCase):
# Should be successful
self.assertEqual(
- 200,
+ HTTPStatus.OK,
channel.code,
msg=(
- "Expected to receive a 200 on accessing media: %s" % server_and_media_id
+ "Expected to receive a HTTPStatus.OK on accessing media: %s"
+ % server_and_media_id
),
)
@@ -157,7 +172,7 @@ class DeleteMediaByIDTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(1, channel.json_body["total"])
self.assertEqual(
media_id,
@@ -174,10 +189,10 @@ class DeleteMediaByIDTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
self.assertEqual(
- 404,
+ HTTPStatus.NOT_FOUND,
channel.code,
msg=(
- "Expected to receive a 404 on accessing deleted media: %s"
+ "Expected to receive a HTTPStatus.NOT_FOUND on accessing deleted media: %s"
% server_and_media_id
),
)
@@ -196,7 +211,7 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
room.register_servlets,
]
- def prepare(self, reactor, clock, hs):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
self.media_repo = hs.get_media_repository_resource()
self.server_name = hs.hostname
@@ -209,17 +224,21 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
# Move clock up to somewhat realistic time
self.reactor.advance(1000000000)
- def test_no_auth(self):
+ def test_no_auth(self) -> None:
"""
Try to delete media without authentication.
"""
channel = self.make_request("POST", self.url, b"{}")
- self.assertEqual(401, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.UNAUTHORIZED,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
- def test_requester_is_no_admin(self):
+ def test_requester_is_no_admin(self) -> None:
"""
If the user is not a server admin, an error is returned.
"""
@@ -232,12 +251,16 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
access_token=self.other_user_token,
)
- self.assertEqual(403, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.FORBIDDEN,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_media_is_not_local(self):
+ def test_media_is_not_local(self) -> None:
"""
- Tests that a lookup for media that is not local returns a 400
+ Tests that a lookup for media that is not local returns a HTTPStatus.BAD_REQUEST
"""
url = "/_synapse/admin/v1/media/%s/delete" % "unknown_domain"
@@ -247,10 +270,10 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("Can only delete local media", channel.json_body["error"])
- def test_missing_parameter(self):
+ def test_missing_parameter(self) -> None:
"""
If the parameter `before_ts` is missing, an error is returned.
"""
@@ -260,13 +283,17 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_PARAM, channel.json_body["errcode"])
self.assertEqual(
"Missing integer query parameter 'before_ts'", channel.json_body["error"]
)
- def test_invalid_parameter(self):
+ def test_invalid_parameter(self) -> None:
"""
If parameters are invalid, an error is returned.
"""
@@ -276,7 +303,11 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
self.assertEqual(
"Query parameter before_ts must be a positive integer.",
@@ -289,7 +320,11 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
self.assertEqual(
"Query parameter before_ts you provided is from the year 1970. "
@@ -303,7 +338,11 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
self.assertEqual(
"Query parameter size_gt must be a string representing a positive integer.",
@@ -316,14 +355,18 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
self.assertEqual(
"Boolean query parameter 'keep_profiles' must be one of ['true', 'false']",
channel.json_body["error"],
)
- def test_delete_media_never_accessed(self):
+ def test_delete_media_never_accessed(self) -> None:
"""
Tests that media deleted if it is older than `before_ts` and never accessed
`last_access_ts` is `NULL` and `created_ts` < `before_ts`
@@ -345,7 +388,7 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
self.url + "?before_ts=" + str(now_ms),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(1, channel.json_body["total"])
self.assertEqual(
media_id,
@@ -354,7 +397,7 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
self._access_media(server_and_media_id, False)
- def test_keep_media_by_date(self):
+ def test_keep_media_by_date(self) -> None:
"""
Tests that media is not deleted if it is newer than `before_ts`
"""
@@ -370,7 +413,7 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
self.url + "?before_ts=" + str(now_ms),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(0, channel.json_body["total"])
self._access_media(server_and_media_id)
@@ -382,7 +425,7 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
self.url + "?before_ts=" + str(now_ms),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(1, channel.json_body["total"])
self.assertEqual(
server_and_media_id.split("/")[1],
@@ -391,7 +434,7 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
self._access_media(server_and_media_id, False)
- def test_keep_media_by_size(self):
+ def test_keep_media_by_size(self) -> None:
"""
Tests that media is not deleted if its size is smaller than or equal
to `size_gt`
@@ -406,7 +449,7 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
self.url + "?before_ts=" + str(now_ms) + "&size_gt=67",
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(0, channel.json_body["total"])
self._access_media(server_and_media_id)
@@ -417,7 +460,7 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
self.url + "?before_ts=" + str(now_ms) + "&size_gt=66",
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(1, channel.json_body["total"])
self.assertEqual(
server_and_media_id.split("/")[1],
@@ -426,7 +469,7 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
self._access_media(server_and_media_id, False)
- def test_keep_media_by_user_avatar(self):
+ def test_keep_media_by_user_avatar(self) -> None:
"""
Tests that we do not delete media if is used as a user avatar
Tests parameter `keep_profiles`
@@ -439,10 +482,10 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
channel = self.make_request(
"PUT",
"/profile/%s/avatar_url" % (self.admin_user,),
- content=json.dumps({"avatar_url": "mxc://%s" % (server_and_media_id,)}),
+ content={"avatar_url": "mxc://%s" % (server_and_media_id,)},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
now_ms = self.clock.time_msec()
channel = self.make_request(
@@ -450,7 +493,7 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
self.url + "?before_ts=" + str(now_ms) + "&keep_profiles=true",
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(0, channel.json_body["total"])
self._access_media(server_and_media_id)
@@ -461,7 +504,7 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
self.url + "?before_ts=" + str(now_ms) + "&keep_profiles=false",
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(1, channel.json_body["total"])
self.assertEqual(
server_and_media_id.split("/")[1],
@@ -470,7 +513,7 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
self._access_media(server_and_media_id, False)
- def test_keep_media_by_room_avatar(self):
+ def test_keep_media_by_room_avatar(self) -> None:
"""
Tests that we do not delete media if it is used as a room avatar
Tests parameter `keep_profiles`
@@ -484,10 +527,10 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
channel = self.make_request(
"PUT",
"/rooms/%s/state/m.room.avatar" % (room_id,),
- content=json.dumps({"url": "mxc://%s" % (server_and_media_id,)}),
+ content={"url": "mxc://%s" % (server_and_media_id,)},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
now_ms = self.clock.time_msec()
channel = self.make_request(
@@ -495,7 +538,7 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
self.url + "?before_ts=" + str(now_ms) + "&keep_profiles=true",
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(0, channel.json_body["total"])
self._access_media(server_and_media_id)
@@ -506,7 +549,7 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
self.url + "?before_ts=" + str(now_ms) + "&keep_profiles=false",
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(1, channel.json_body["total"])
self.assertEqual(
server_and_media_id.split("/")[1],
@@ -515,7 +558,7 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
self._access_media(server_and_media_id, False)
- def _create_media(self):
+ def _create_media(self) -> str:
"""
Create a media and return media_id and server_and_media_id
"""
@@ -523,7 +566,10 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
# Upload some media into the room
response = self.helper.upload_media(
- upload_resource, SMALL_PNG, tok=self.admin_user_tok, expect_code=200
+ upload_resource,
+ SMALL_PNG,
+ tok=self.admin_user_tok,
+ expect_code=HTTPStatus.OK,
)
# Extract media ID from the response
server_and_media_id = response["content_uri"][6:] # Cut off 'mxc://'
@@ -534,7 +580,7 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
return server_and_media_id
- def _access_media(self, server_and_media_id, expect_success=True):
+ def _access_media(self, server_and_media_id, expect_success=True) -> None:
"""
Try to access a media and check the result
"""
@@ -554,10 +600,10 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
if expect_success:
self.assertEqual(
- 200,
+ HTTPStatus.OK,
channel.code,
msg=(
- "Expected to receive a 200 on accessing media: %s"
+ "Expected to receive a HTTPStatus.OK on accessing media: %s"
% server_and_media_id
),
)
@@ -565,10 +611,10 @@ class DeleteMediaByDateSizeTestCase(unittest.HomeserverTestCase):
self.assertTrue(os.path.exists(local_path))
else:
self.assertEqual(
- 404,
+ HTTPStatus.NOT_FOUND,
channel.code,
msg=(
- "Expected to receive a 404 on accessing deleted media: %s"
+ "Expected to receive a HTTPStatus.NOT_FOUND on accessing deleted media: %s"
% (server_and_media_id)
),
)
@@ -584,7 +630,7 @@ class QuarantineMediaByIDTestCase(unittest.HomeserverTestCase):
login.register_servlets,
]
- def prepare(self, reactor, clock, hs):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
media_repo = hs.get_media_repository_resource()
self.store = hs.get_datastore()
self.server_name = hs.hostname
@@ -597,7 +643,10 @@ class QuarantineMediaByIDTestCase(unittest.HomeserverTestCase):
# Upload some media into the room
response = self.helper.upload_media(
- upload_resource, SMALL_PNG, tok=self.admin_user_tok, expect_code=200
+ upload_resource,
+ SMALL_PNG,
+ tok=self.admin_user_tok,
+ expect_code=HTTPStatus.OK,
)
# Extract media ID from the response
server_and_media_id = response["content_uri"][6:] # Cut off 'mxc://'
@@ -606,7 +655,7 @@ class QuarantineMediaByIDTestCase(unittest.HomeserverTestCase):
self.url = "/_synapse/admin/v1/media/%s/%s/%s"
@parameterized.expand(["quarantine", "unquarantine"])
- def test_no_auth(self, action: str):
+ def test_no_auth(self, action: str) -> None:
"""
Try to protect media without authentication.
"""
@@ -617,11 +666,15 @@ class QuarantineMediaByIDTestCase(unittest.HomeserverTestCase):
b"{}",
)
- self.assertEqual(401, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.UNAUTHORIZED,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
@parameterized.expand(["quarantine", "unquarantine"])
- def test_requester_is_no_admin(self, action: str):
+ def test_requester_is_no_admin(self, action: str) -> None:
"""
If the user is not a server admin, an error is returned.
"""
@@ -634,10 +687,14 @@ class QuarantineMediaByIDTestCase(unittest.HomeserverTestCase):
access_token=self.other_user_token,
)
- self.assertEqual(403, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.FORBIDDEN,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_quarantine_media(self):
+ def test_quarantine_media(self) -> None:
"""
Tests that quarantining and remove from quarantine a media is successfully
"""
@@ -652,7 +709,7 @@ class QuarantineMediaByIDTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertFalse(channel.json_body)
media_info = self.get_success(self.store.get_local_media(self.media_id))
@@ -665,13 +722,13 @@ class QuarantineMediaByIDTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertFalse(channel.json_body)
media_info = self.get_success(self.store.get_local_media(self.media_id))
self.assertFalse(media_info["quarantined_by"])
- def test_quarantine_protected_media(self):
+ def test_quarantine_protected_media(self) -> None:
"""
Tests that quarantining from protected media fails
"""
@@ -690,7 +747,7 @@ class QuarantineMediaByIDTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertFalse(channel.json_body)
# verify that is not in quarantine
@@ -706,7 +763,7 @@ class ProtectMediaByIDTestCase(unittest.HomeserverTestCase):
login.register_servlets,
]
- def prepare(self, reactor, clock, hs):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
media_repo = hs.get_media_repository_resource()
self.store = hs.get_datastore()
@@ -718,7 +775,10 @@ class ProtectMediaByIDTestCase(unittest.HomeserverTestCase):
# Upload some media into the room
response = self.helper.upload_media(
- upload_resource, SMALL_PNG, tok=self.admin_user_tok, expect_code=200
+ upload_resource,
+ SMALL_PNG,
+ tok=self.admin_user_tok,
+ expect_code=HTTPStatus.OK,
)
# Extract media ID from the response
server_and_media_id = response["content_uri"][6:] # Cut off 'mxc://'
@@ -727,18 +787,22 @@ class ProtectMediaByIDTestCase(unittest.HomeserverTestCase):
self.url = "/_synapse/admin/v1/media/%s/%s"
@parameterized.expand(["protect", "unprotect"])
- def test_no_auth(self, action: str):
+ def test_no_auth(self, action: str) -> None:
"""
Try to protect media without authentication.
"""
channel = self.make_request("POST", self.url % (action, self.media_id), b"{}")
- self.assertEqual(401, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.UNAUTHORIZED,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
@parameterized.expand(["protect", "unprotect"])
- def test_requester_is_no_admin(self, action: str):
+ def test_requester_is_no_admin(self, action: str) -> None:
"""
If the user is not a server admin, an error is returned.
"""
@@ -751,10 +815,14 @@ class ProtectMediaByIDTestCase(unittest.HomeserverTestCase):
access_token=self.other_user_token,
)
- self.assertEqual(403, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.FORBIDDEN,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_protect_media(self):
+ def test_protect_media(self) -> None:
"""
Tests that protect and unprotect a media is successfully
"""
@@ -769,7 +837,7 @@ class ProtectMediaByIDTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertFalse(channel.json_body)
media_info = self.get_success(self.store.get_local_media(self.media_id))
@@ -782,7 +850,7 @@ class ProtectMediaByIDTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertFalse(channel.json_body)
media_info = self.get_success(self.store.get_local_media(self.media_id))
@@ -799,7 +867,7 @@ class PurgeMediaCacheTestCase(unittest.HomeserverTestCase):
room.register_servlets,
]
- def prepare(self, reactor, clock, hs):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
self.media_repo = hs.get_media_repository_resource()
self.server_name = hs.hostname
@@ -809,17 +877,21 @@ class PurgeMediaCacheTestCase(unittest.HomeserverTestCase):
self.filepaths = MediaFilePaths(hs.config.media.media_store_path)
self.url = "/_synapse/admin/v1/purge_media_cache"
- def test_no_auth(self):
+ def test_no_auth(self) -> None:
"""
Try to delete media without authentication.
"""
channel = self.make_request("POST", self.url, b"{}")
- self.assertEqual(401, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.UNAUTHORIZED,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
- def test_requester_is_not_admin(self):
+ def test_requester_is_not_admin(self) -> None:
"""
If the user is not a server admin, an error is returned.
"""
@@ -832,10 +904,14 @@ class PurgeMediaCacheTestCase(unittest.HomeserverTestCase):
access_token=self.other_user_token,
)
- self.assertEqual(403, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.FORBIDDEN,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_invalid_parameter(self):
+ def test_invalid_parameter(self) -> None:
"""
If parameters are invalid, an error is returned.
"""
@@ -845,7 +921,11 @@ class PurgeMediaCacheTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
self.assertEqual(
"Query parameter before_ts must be a positive integer.",
@@ -858,7 +938,11 @@ class PurgeMediaCacheTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
self.assertEqual(
"Query parameter before_ts you provided is from the year 1970. "
diff --git a/tests/rest/admin/test_registration_tokens.py b/tests/rest/admin/test_registration_tokens.py
index 9bac423ae0..350a62dda6 100644
--- a/tests/rest/admin/test_registration_tokens.py
+++ b/tests/rest/admin/test_registration_tokens.py
@@ -11,13 +11,17 @@
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
-
import random
import string
+from http import HTTPStatus
+
+from twisted.test.proto_helpers import MemoryReactor
import synapse.rest.admin
from synapse.api.errors import Codes
from synapse.rest.client import login
+from synapse.server import HomeServer
+from synapse.util import Clock
from tests import unittest
@@ -28,7 +32,7 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
login.register_servlets,
]
- def prepare(self, reactor, clock, hs):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
self.store = hs.get_datastore()
self.admin_user = self.register_user("admin", "pass", admin=True)
self.admin_user_tok = self.login("admin", "pass")
@@ -38,7 +42,7 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
self.url = "/_synapse/admin/v1/registration_tokens"
- def _new_token(self, **kwargs):
+ def _new_token(self, **kwargs) -> str:
"""Helper function to create a token."""
token = kwargs.get(
"token",
@@ -60,13 +64,17 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
# CREATION
- def test_create_no_auth(self):
+ def test_create_no_auth(self) -> None:
"""Try to create a token without authentication."""
channel = self.make_request("POST", self.url + "/new", {})
- self.assertEqual(401, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.UNAUTHORIZED,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
- def test_create_requester_not_admin(self):
+ def test_create_requester_not_admin(self) -> None:
"""Try to create a token while not an admin."""
channel = self.make_request(
"POST",
@@ -74,10 +82,14 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{},
access_token=self.other_user_tok,
)
- self.assertEqual(403, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.FORBIDDEN,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_create_using_defaults(self):
+ def test_create_using_defaults(self) -> None:
"""Create a token using all the defaults."""
channel = self.make_request(
"POST",
@@ -86,14 +98,14 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(len(channel.json_body["token"]), 16)
self.assertIsNone(channel.json_body["uses_allowed"])
self.assertIsNone(channel.json_body["expiry_time"])
self.assertEqual(channel.json_body["pending"], 0)
self.assertEqual(channel.json_body["completed"], 0)
- def test_create_specifying_fields(self):
+ def test_create_specifying_fields(self) -> None:
"""Create a token specifying the value of all fields."""
# As many of the allowed characters as possible with length <= 64
token = "adefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789._~-"
@@ -110,14 +122,14 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["token"], token)
self.assertEqual(channel.json_body["uses_allowed"], 1)
self.assertEqual(channel.json_body["expiry_time"], data["expiry_time"])
self.assertEqual(channel.json_body["pending"], 0)
self.assertEqual(channel.json_body["completed"], 0)
- def test_create_with_null_value(self):
+ def test_create_with_null_value(self) -> None:
"""Create a token specifying unlimited uses and no expiry."""
data = {
"uses_allowed": None,
@@ -131,14 +143,14 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(len(channel.json_body["token"]), 16)
self.assertIsNone(channel.json_body["uses_allowed"])
self.assertIsNone(channel.json_body["expiry_time"])
self.assertEqual(channel.json_body["pending"], 0)
self.assertEqual(channel.json_body["completed"], 0)
- def test_create_token_too_long(self):
+ def test_create_token_too_long(self) -> None:
"""Check token longer than 64 chars is invalid."""
data = {"token": "a" * 65}
@@ -149,10 +161,14 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.INVALID_PARAM)
- def test_create_token_invalid_chars(self):
+ def test_create_token_invalid_chars(self) -> None:
"""Check you can't create token with invalid characters."""
data = {
"token": "abc/def",
@@ -165,10 +181,14 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.INVALID_PARAM)
- def test_create_token_already_exists(self):
+ def test_create_token_already_exists(self) -> None:
"""Check you can't create token that already exists."""
data = {
"token": "abcd",
@@ -180,7 +200,7 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
data,
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel1.result["code"]), msg=channel1.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel1.code, msg=channel1.json_body)
channel2 = self.make_request(
"POST",
@@ -188,10 +208,10 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
data,
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel2.result["code"]), msg=channel2.result["body"])
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel2.code, msg=channel2.json_body)
self.assertEqual(channel2.json_body["errcode"], Codes.INVALID_PARAM)
- def test_create_unable_to_generate_token(self):
+ def test_create_unable_to_generate_token(self) -> None:
"""Check right error is raised when server can't generate unique token."""
# Create all possible single character tokens
tokens = []
@@ -220,9 +240,9 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"length": 1},
access_token=self.admin_user_tok,
)
- self.assertEqual(500, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(500, channel.code, msg=channel.json_body)
- def test_create_uses_allowed(self):
+ def test_create_uses_allowed(self) -> None:
"""Check you can only create a token with good values for uses_allowed."""
# Should work with 0 (token is invalid from the start)
channel = self.make_request(
@@ -231,7 +251,7 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"uses_allowed": 0},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["uses_allowed"], 0)
# Should fail with negative integer
@@ -241,7 +261,11 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"uses_allowed": -5},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.INVALID_PARAM)
# Should fail with float
@@ -251,10 +275,14 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"uses_allowed": 1.5},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.INVALID_PARAM)
- def test_create_expiry_time(self):
+ def test_create_expiry_time(self) -> None:
"""Check you can't create a token with an invalid expiry_time."""
# Should fail with a time in the past
channel = self.make_request(
@@ -263,7 +291,11 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"expiry_time": self.clock.time_msec() - 10000},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.INVALID_PARAM)
# Should fail with float
@@ -273,10 +305,14 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"expiry_time": self.clock.time_msec() + 1000000.5},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.INVALID_PARAM)
- def test_create_length(self):
+ def test_create_length(self) -> None:
"""Check you can only generate a token with a valid length."""
# Should work with 64
channel = self.make_request(
@@ -285,7 +321,7 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"length": 64},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(len(channel.json_body["token"]), 64)
# Should fail with 0
@@ -295,7 +331,11 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"length": 0},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.INVALID_PARAM)
# Should fail with a negative integer
@@ -305,7 +345,11 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"length": -5},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.INVALID_PARAM)
# Should fail with a float
@@ -315,7 +359,11 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"length": 8.5},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.INVALID_PARAM)
# Should fail with 65
@@ -325,22 +373,30 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"length": 65},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.INVALID_PARAM)
# UPDATING
- def test_update_no_auth(self):
+ def test_update_no_auth(self) -> None:
"""Try to update a token without authentication."""
channel = self.make_request(
"PUT",
self.url + "/1234", # Token doesn't exist but that doesn't matter
{},
)
- self.assertEqual(401, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.UNAUTHORIZED,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
- def test_update_requester_not_admin(self):
+ def test_update_requester_not_admin(self) -> None:
"""Try to update a token while not an admin."""
channel = self.make_request(
"PUT",
@@ -348,10 +404,14 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{},
access_token=self.other_user_tok,
)
- self.assertEqual(403, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.FORBIDDEN,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_update_non_existent(self):
+ def test_update_non_existent(self) -> None:
"""Try to update a token that doesn't exist."""
channel = self.make_request(
"PUT",
@@ -360,10 +420,14 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(404, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.NOT_FOUND,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.NOT_FOUND)
- def test_update_uses_allowed(self):
+ def test_update_uses_allowed(self) -> None:
"""Test updating just uses_allowed."""
# Create new token using default values
token = self._new_token()
@@ -375,7 +439,7 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"uses_allowed": 1},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["uses_allowed"], 1)
self.assertIsNone(channel.json_body["expiry_time"])
@@ -386,7 +450,7 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"uses_allowed": 0},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["uses_allowed"], 0)
self.assertIsNone(channel.json_body["expiry_time"])
@@ -397,7 +461,7 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"uses_allowed": None},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertIsNone(channel.json_body["uses_allowed"])
self.assertIsNone(channel.json_body["expiry_time"])
@@ -408,7 +472,11 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"uses_allowed": 1.5},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.INVALID_PARAM)
# Should fail with a negative integer
@@ -418,10 +486,14 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"uses_allowed": -5},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.INVALID_PARAM)
- def test_update_expiry_time(self):
+ def test_update_expiry_time(self) -> None:
"""Test updating just expiry_time."""
# Create new token using default values
token = self._new_token()
@@ -434,7 +506,7 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"expiry_time": new_expiry_time},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["expiry_time"], new_expiry_time)
self.assertIsNone(channel.json_body["uses_allowed"])
@@ -445,7 +517,7 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"expiry_time": None},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertIsNone(channel.json_body["expiry_time"])
self.assertIsNone(channel.json_body["uses_allowed"])
@@ -457,7 +529,11 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"expiry_time": past_time},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.INVALID_PARAM)
# Should fail a float
@@ -467,10 +543,14 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{"expiry_time": new_expiry_time + 0.5},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.INVALID_PARAM)
- def test_update_both(self):
+ def test_update_both(self) -> None:
"""Test updating both uses_allowed and expiry_time."""
# Create new token using default values
token = self._new_token()
@@ -488,11 +568,11 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["uses_allowed"], 1)
self.assertEqual(channel.json_body["expiry_time"], new_expiry_time)
- def test_update_invalid_type(self):
+ def test_update_invalid_type(self) -> None:
"""Test using invalid types doesn't work."""
# Create new token using default values
token = self._new_token()
@@ -509,22 +589,30 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.INVALID_PARAM)
# DELETING
- def test_delete_no_auth(self):
+ def test_delete_no_auth(self) -> None:
"""Try to delete a token without authentication."""
channel = self.make_request(
"DELETE",
self.url + "/1234", # Token doesn't exist but that doesn't matter
{},
)
- self.assertEqual(401, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.UNAUTHORIZED,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
- def test_delete_requester_not_admin(self):
+ def test_delete_requester_not_admin(self) -> None:
"""Try to delete a token while not an admin."""
channel = self.make_request(
"DELETE",
@@ -532,10 +620,14 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{},
access_token=self.other_user_tok,
)
- self.assertEqual(403, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.FORBIDDEN,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_delete_non_existent(self):
+ def test_delete_non_existent(self) -> None:
"""Try to delete a token that doesn't exist."""
channel = self.make_request(
"DELETE",
@@ -544,10 +636,14 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(404, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.NOT_FOUND,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.NOT_FOUND)
- def test_delete(self):
+ def test_delete(self) -> None:
"""Test deleting a token."""
# Create new token using default values
token = self._new_token()
@@ -559,21 +655,25 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# GETTING ONE
- def test_get_no_auth(self):
+ def test_get_no_auth(self) -> None:
"""Try to get a token without authentication."""
channel = self.make_request(
"GET",
self.url + "/1234", # Token doesn't exist but that doesn't matter
{},
)
- self.assertEqual(401, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.UNAUTHORIZED,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
- def test_get_requester_not_admin(self):
+ def test_get_requester_not_admin(self) -> None:
"""Try to get a token while not an admin."""
channel = self.make_request(
"GET",
@@ -581,10 +681,14 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{},
access_token=self.other_user_tok,
)
- self.assertEqual(403, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.FORBIDDEN,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_get_non_existent(self):
+ def test_get_non_existent(self) -> None:
"""Try to get a token that doesn't exist."""
channel = self.make_request(
"GET",
@@ -593,10 +697,14 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(404, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.NOT_FOUND,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], Codes.NOT_FOUND)
- def test_get(self):
+ def test_get(self) -> None:
"""Test getting a token."""
# Create new token using default values
token = self._new_token()
@@ -608,7 +716,7 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["token"], token)
self.assertIsNone(channel.json_body["uses_allowed"])
self.assertIsNone(channel.json_body["expiry_time"])
@@ -617,13 +725,17 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
# LISTING
- def test_list_no_auth(self):
+ def test_list_no_auth(self) -> None:
"""Try to list tokens without authentication."""
channel = self.make_request("GET", self.url, {})
- self.assertEqual(401, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.UNAUTHORIZED,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
- def test_list_requester_not_admin(self):
+ def test_list_requester_not_admin(self) -> None:
"""Try to list tokens while not an admin."""
channel = self.make_request(
"GET",
@@ -631,10 +743,14 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
{},
access_token=self.other_user_tok,
)
- self.assertEqual(403, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.FORBIDDEN,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_list_all(self):
+ def test_list_all(self) -> None:
"""Test listing all tokens."""
# Create new token using default values
token = self._new_token()
@@ -646,7 +762,7 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(len(channel.json_body["registration_tokens"]), 1)
token_info = channel.json_body["registration_tokens"][0]
self.assertEqual(token_info["token"], token)
@@ -655,7 +771,7 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
self.assertEqual(token_info["pending"], 0)
self.assertEqual(token_info["completed"], 0)
- def test_list_invalid_query_parameter(self):
+ def test_list_invalid_query_parameter(self) -> None:
"""Test with `valid` query parameter not `true` or `false`."""
channel = self.make_request(
"GET",
@@ -664,9 +780,13 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
- def _test_list_query_parameter(self, valid: str):
+ def _test_list_query_parameter(self, valid: str) -> None:
"""Helper used to test both valid=true and valid=false."""
# Create 2 valid and 2 invalid tokens.
now = self.hs.get_clock().time_msec()
@@ -696,17 +816,17 @@ class ManageRegistrationTokensTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(len(channel.json_body["registration_tokens"]), 2)
token_info_1 = channel.json_body["registration_tokens"][0]
token_info_2 = channel.json_body["registration_tokens"][1]
self.assertIn(token_info_1["token"], tokens)
self.assertIn(token_info_2["token"], tokens)
- def test_list_valid(self):
+ def test_list_valid(self) -> None:
"""Test listing just valid tokens."""
self._test_list_query_parameter(valid="true")
- def test_list_invalid(self):
+ def test_list_invalid(self) -> None:
"""Test listing just invalid tokens."""
self._test_list_query_parameter(valid="false")
diff --git a/tests/rest/admin/test_room.py b/tests/rest/admin/test_room.py
index 07077aff78..22f9aa6234 100644
--- a/tests/rest/admin/test_room.py
+++ b/tests/rest/admin/test_room.py
@@ -11,8 +11,6 @@
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
-
-import json
import urllib.parse
from http import HTTPStatus
from typing import List, Optional
@@ -20,11 +18,15 @@ from unittest.mock import Mock
from parameterized import parameterized
+from twisted.test.proto_helpers import MemoryReactor
+
import synapse.rest.admin
from synapse.api.constants import EventTypes, Membership
from synapse.api.errors import Codes
from synapse.handlers.pagination import PaginationHandler
from synapse.rest.client import directory, events, login, room
+from synapse.server import HomeServer
+from synapse.util import Clock
from tests import unittest
@@ -40,7 +42,7 @@ class DeleteRoomTestCase(unittest.HomeserverTestCase):
room.register_deprecated_servlets,
]
- def prepare(self, reactor, clock, hs):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
self.event_creation_handler = hs.get_event_creation_handler()
hs.config.consent.user_consent_version = "1"
@@ -66,7 +68,7 @@ class DeleteRoomTestCase(unittest.HomeserverTestCase):
def test_requester_is_no_admin(self):
"""
- If the user is not a server admin, an error 403 is returned.
+ If the user is not a server admin, an error HTTPStatus.FORBIDDEN is returned.
"""
channel = self.make_request(
@@ -76,12 +78,12 @@ class DeleteRoomTestCase(unittest.HomeserverTestCase):
access_token=self.other_user_tok,
)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
def test_room_does_not_exist(self):
"""
- Check that unknown rooms/server return error 404.
+ Check that unknown rooms/server return 200
"""
url = "/_synapse/admin/v1/rooms/%s" % "!unknown:test"
@@ -92,12 +94,11 @@ class DeleteRoomTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(404, channel.code, msg=channel.json_body)
- self.assertEqual(Codes.NOT_FOUND, channel.json_body["errcode"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
def test_room_is_not_valid(self):
"""
- Check that invalid room names, return an error 400.
+ Check that invalid room names, return an error HTTPStatus.BAD_REQUEST.
"""
url = "/_synapse/admin/v1/rooms/%s" % "invalidroom"
@@ -108,7 +109,7 @@ class DeleteRoomTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(
"invalidroom is not a legal room ID",
channel.json_body["error"],
@@ -118,16 +119,15 @@ class DeleteRoomTestCase(unittest.HomeserverTestCase):
"""
Tests that the user ID must be from local server but it does not have to exist.
"""
- body = json.dumps({"new_room_user_id": "@unknown:test"})
channel = self.make_request(
"DELETE",
self.url,
- content=body,
+ content={"new_room_user_id": "@unknown:test"},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertIn("new_room_id", channel.json_body)
self.assertIn("kicked_users", channel.json_body)
self.assertIn("failed_to_kick_users", channel.json_body)
@@ -137,16 +137,15 @@ class DeleteRoomTestCase(unittest.HomeserverTestCase):
"""
Check that only local users can create new room to move members.
"""
- body = json.dumps({"new_room_user_id": "@not:exist.bla"})
channel = self.make_request(
"DELETE",
self.url,
- content=body,
+ content={"new_room_user_id": "@not:exist.bla"},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(
"User must be our own: @not:exist.bla",
channel.json_body["error"],
@@ -156,32 +155,30 @@ class DeleteRoomTestCase(unittest.HomeserverTestCase):
"""
If parameter `block` is not boolean, return an error
"""
- body = json.dumps({"block": "NotBool"})
channel = self.make_request(
"DELETE",
self.url,
- content=body,
+ content={"block": "NotBool"},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.BAD_JSON, channel.json_body["errcode"])
def test_purge_is_not_bool(self):
"""
If parameter `purge` is not boolean, return an error
"""
- body = json.dumps({"purge": "NotBool"})
channel = self.make_request(
"DELETE",
self.url,
- content=body,
+ content={"purge": "NotBool"},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.BAD_JSON, channel.json_body["errcode"])
def test_purge_room_and_block(self):
@@ -198,16 +195,14 @@ class DeleteRoomTestCase(unittest.HomeserverTestCase):
# Assert one user in room
self._is_member(room_id=self.room_id, user_id=self.other_user)
- body = json.dumps({"block": True, "purge": True})
-
channel = self.make_request(
"DELETE",
self.url.encode("ascii"),
- content=body,
+ content={"block": True, "purge": True},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(None, channel.json_body["new_room_id"])
self.assertEqual(self.other_user, channel.json_body["kicked_users"][0])
self.assertIn("failed_to_kick_users", channel.json_body)
@@ -231,16 +226,14 @@ class DeleteRoomTestCase(unittest.HomeserverTestCase):
# Assert one user in room
self._is_member(room_id=self.room_id, user_id=self.other_user)
- body = json.dumps({"block": False, "purge": True})
-
channel = self.make_request(
"DELETE",
self.url.encode("ascii"),
- content=body,
+ content={"block": False, "purge": True},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(None, channel.json_body["new_room_id"])
self.assertEqual(self.other_user, channel.json_body["kicked_users"][0])
self.assertIn("failed_to_kick_users", channel.json_body)
@@ -265,16 +258,14 @@ class DeleteRoomTestCase(unittest.HomeserverTestCase):
# Assert one user in room
self._is_member(room_id=self.room_id, user_id=self.other_user)
- body = json.dumps({"block": True, "purge": False})
-
channel = self.make_request(
"DELETE",
self.url.encode("ascii"),
- content=body,
+ content={"block": True, "purge": False},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(None, channel.json_body["new_room_id"])
self.assertEqual(self.other_user, channel.json_body["kicked_users"][0])
self.assertIn("failed_to_kick_users", channel.json_body)
@@ -305,9 +296,7 @@ class DeleteRoomTestCase(unittest.HomeserverTestCase):
)
# The room is now blocked.
- self.assertEqual(
- HTTPStatus.OK, int(channel.result["code"]), msg=channel.result["body"]
- )
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self._is_blocked(room_id)
def test_shutdown_room_consent(self):
@@ -327,7 +316,10 @@ class DeleteRoomTestCase(unittest.HomeserverTestCase):
# Assert that the user is getting consent error
self.helper.send(
- self.room_id, body="foo", tok=self.other_user_tok, expect_code=403
+ self.room_id,
+ body="foo",
+ tok=self.other_user_tok,
+ expect_code=HTTPStatus.FORBIDDEN,
)
# Test that room is not purged
@@ -341,11 +333,11 @@ class DeleteRoomTestCase(unittest.HomeserverTestCase):
channel = self.make_request(
"DELETE",
self.url,
- json.dumps({"new_room_user_id": self.admin_user}),
+ {"new_room_user_id": self.admin_user},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(self.other_user, channel.json_body["kicked_users"][0])
self.assertIn("new_room_id", channel.json_body)
self.assertIn("failed_to_kick_users", channel.json_body)
@@ -371,10 +363,10 @@ class DeleteRoomTestCase(unittest.HomeserverTestCase):
channel = self.make_request(
"PUT",
url.encode("ascii"),
- json.dumps({"history_visibility": "world_readable"}),
+ {"history_visibility": "world_readable"},
access_token=self.other_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Test that room is not purged
with self.assertRaises(AssertionError):
@@ -387,11 +379,11 @@ class DeleteRoomTestCase(unittest.HomeserverTestCase):
channel = self.make_request(
"DELETE",
self.url,
- json.dumps({"new_room_user_id": self.admin_user}),
+ {"new_room_user_id": self.admin_user},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(self.other_user, channel.json_body["kicked_users"][0])
self.assertIn("new_room_id", channel.json_body)
self.assertIn("failed_to_kick_users", channel.json_body)
@@ -406,7 +398,7 @@ class DeleteRoomTestCase(unittest.HomeserverTestCase):
self._has_no_members(self.room_id)
# Assert we can no longer peek into the room
- self._assert_peek(self.room_id, expect_code=403)
+ self._assert_peek(self.room_id, expect_code=HTTPStatus.FORBIDDEN)
def _is_blocked(self, room_id, expect=True):
"""Assert that the room is blocked or not"""
@@ -465,7 +457,7 @@ class DeleteRoomV2TestCase(unittest.HomeserverTestCase):
room.register_deprecated_servlets,
]
- def prepare(self, reactor, clock, hs):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
self.event_creation_handler = hs.get_event_creation_handler()
hs.config.consent.user_consent_version = "1"
@@ -502,7 +494,7 @@ class DeleteRoomV2TestCase(unittest.HomeserverTestCase):
)
def test_requester_is_no_admin(self, method: str, url: str):
"""
- If the user is not a server admin, an error 403 is returned.
+ If the user is not a server admin, an error HTTPStatus.FORBIDDEN is returned.
"""
channel = self.make_request(
@@ -515,27 +507,36 @@ class DeleteRoomV2TestCase(unittest.HomeserverTestCase):
self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- @parameterized.expand(
- [
- ("DELETE", "/_synapse/admin/v2/rooms/%s"),
- ("GET", "/_synapse/admin/v2/rooms/%s/delete_status"),
- ("GET", "/_synapse/admin/v2/rooms/delete_status/%s"),
- ]
- )
- def test_room_does_not_exist(self, method: str, url: str):
- """
- Check that unknown rooms/server return error 404.
+ def test_room_does_not_exist(self):
"""
+ Check that unknown rooms/server return 200
+ This is important, as it allows incomplete vestiges of rooms to be cleared up
+ even if the create event/etc is missing.
+ """
+ room_id = "!unknown:test"
channel = self.make_request(
- method,
- url % "!unknown:test",
+ "DELETE",
+ f"/_synapse/admin/v2/rooms/{room_id}",
content={},
access_token=self.admin_user_tok,
)
- self.assertEqual(HTTPStatus.NOT_FOUND, channel.code, msg=channel.json_body)
- self.assertEqual(Codes.NOT_FOUND, channel.json_body["errcode"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
+ self.assertIn("delete_id", channel.json_body)
+ delete_id = channel.json_body["delete_id"]
+
+ # get status
+ channel = self.make_request(
+ "GET",
+ f"/_synapse/admin/v2/rooms/{room_id}/delete_status",
+ access_token=self.admin_user_tok,
+ )
+
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
+ self.assertEqual(1, len(channel.json_body["results"]))
+ self.assertEqual("complete", channel.json_body["results"][0]["status"])
+ self.assertEqual(delete_id, channel.json_body["results"][0]["delete_id"])
@parameterized.expand(
[
@@ -545,7 +546,7 @@ class DeleteRoomV2TestCase(unittest.HomeserverTestCase):
)
def test_room_is_not_valid(self, method: str, url: str):
"""
- Check that invalid room names, return an error 400.
+ Check that invalid room names, return an error HTTPStatus.BAD_REQUEST.
"""
channel = self.make_request(
@@ -854,7 +855,10 @@ class DeleteRoomV2TestCase(unittest.HomeserverTestCase):
# Assert that the user is getting consent error
self.helper.send(
- self.room_id, body="foo", tok=self.other_user_tok, expect_code=403
+ self.room_id,
+ body="foo",
+ tok=self.other_user_tok,
+ expect_code=HTTPStatus.FORBIDDEN,
)
# Test that room is not purged
@@ -951,7 +955,7 @@ class DeleteRoomV2TestCase(unittest.HomeserverTestCase):
self._has_no_members(self.room_id)
# Assert we can no longer peek into the room
- self._assert_peek(self.room_id, expect_code=403)
+ self._assert_peek(self.room_id, expect_code=HTTPStatus.FORBIDDEN)
def _is_blocked(self, room_id: str, expect: bool = True) -> None:
"""Assert that the room is blocked or not"""
@@ -1069,12 +1073,12 @@ class RoomTestCase(unittest.HomeserverTestCase):
directory.register_servlets,
]
- def prepare(self, reactor, clock, hs):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
# Create user
self.admin_user = self.register_user("admin", "pass", admin=True)
self.admin_user_tok = self.login("admin", "pass")
- def test_list_rooms(self):
+ def test_list_rooms(self) -> None:
"""Test that we can list rooms"""
# Create 3 test rooms
total_rooms = 3
@@ -1094,7 +1098,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
)
# Check request completed successfully
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Check that response json body contains a "rooms" key
self.assertTrue(
@@ -1138,7 +1142,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
# We shouldn't receive a next token here as there's no further rooms to show
self.assertNotIn("next_batch", channel.json_body)
- def test_list_rooms_pagination(self):
+ def test_list_rooms_pagination(self) -> None:
"""Test that we can get a full list of rooms through pagination"""
# Create 5 test rooms
total_rooms = 5
@@ -1178,7 +1182,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
url.encode("ascii"),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertTrue("rooms" in channel.json_body)
for r in channel.json_body["rooms"]:
@@ -1218,9 +1222,9 @@ class RoomTestCase(unittest.HomeserverTestCase):
url.encode("ascii"),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
- def test_correct_room_attributes(self):
+ def test_correct_room_attributes(self) -> None:
"""Test the correct attributes for a room are returned"""
# Create a test room
room_id = self.helper.create_room_as(self.admin_user, tok=self.admin_user_tok)
@@ -1241,7 +1245,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
{"room_id": room_id},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Set this new alias as the canonical alias for this room
self.helper.send_state(
@@ -1273,7 +1277,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
url.encode("ascii"),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Check that rooms were returned
self.assertTrue("rooms" in channel.json_body)
@@ -1301,7 +1305,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
self.assertEqual(test_room_name, r["name"])
self.assertEqual(test_alias, r["canonical_alias"])
- def test_room_list_sort_order(self):
+ def test_room_list_sort_order(self) -> None:
"""Test room list sort ordering. alphabetical name versus number of members,
reversing the order, etc.
"""
@@ -1310,7 +1314,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
order_type: str,
expected_room_list: List[str],
reverse: bool = False,
- ):
+ ) -> None:
"""Request the list of rooms in a certain order. Assert that order is what
we expect
@@ -1328,7 +1332,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
url.encode("ascii"),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Check that rooms were returned
self.assertTrue("rooms" in channel.json_body)
@@ -1439,7 +1443,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
_order_test("state_events", [room_id_3, room_id_2, room_id_1])
_order_test("state_events", [room_id_1, room_id_2, room_id_3], reverse=True)
- def test_search_term(self):
+ def test_search_term(self) -> None:
"""Test that searching for a room works correctly"""
# Create two test rooms
room_id_1 = self.helper.create_room_as(self.admin_user, tok=self.admin_user_tok)
@@ -1467,8 +1471,8 @@ class RoomTestCase(unittest.HomeserverTestCase):
def _search_test(
expected_room_id: Optional[str],
search_term: str,
- expected_http_code: int = 200,
- ):
+ expected_http_code: int = HTTPStatus.OK,
+ ) -> None:
"""Search for a room and check that the returned room's id is a match
Args:
@@ -1485,7 +1489,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
)
self.assertEqual(expected_http_code, channel.code, msg=channel.json_body)
- if expected_http_code != 200:
+ if expected_http_code != HTTPStatus.OK:
return
# Check that rooms were returned
@@ -1528,7 +1532,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
_search_test(None, "foo")
_search_test(None, "bar")
- _search_test(None, "", expected_http_code=400)
+ _search_test(None, "", expected_http_code=HTTPStatus.BAD_REQUEST)
# Test that the whole room id returns the room
_search_test(room_id_1, room_id_1)
@@ -1542,7 +1546,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
# Test search local part of alias
_search_test(room_id_1, "alias1")
- def test_search_term_non_ascii(self):
+ def test_search_term_non_ascii(self) -> None:
"""Test that searching for a room with non-ASCII characters works correctly"""
# Create test room
@@ -1565,11 +1569,11 @@ class RoomTestCase(unittest.HomeserverTestCase):
url.encode("ascii"),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(room_id, channel.json_body.get("rooms")[0].get("room_id"))
self.assertEqual("ж", channel.json_body.get("rooms")[0].get("name"))
- def test_single_room(self):
+ def test_single_room(self) -> None:
"""Test that a single room can be requested correctly"""
# Create two test rooms
room_id_1 = self.helper.create_room_as(self.admin_user, tok=self.admin_user_tok)
@@ -1598,7 +1602,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
url.encode("ascii"),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertIn("room_id", channel.json_body)
self.assertIn("name", channel.json_body)
@@ -1620,7 +1624,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
self.assertEqual(room_id_1, channel.json_body["room_id"])
- def test_single_room_devices(self):
+ def test_single_room_devices(self) -> None:
"""Test that `joined_local_devices` can be requested correctly"""
room_id_1 = self.helper.create_room_as(self.admin_user, tok=self.admin_user_tok)
@@ -1630,7 +1634,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
url.encode("ascii"),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(1, channel.json_body["joined_local_devices"])
# Have another user join the room
@@ -1644,7 +1648,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
url.encode("ascii"),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(2, channel.json_body["joined_local_devices"])
# leave room
@@ -1656,10 +1660,10 @@ class RoomTestCase(unittest.HomeserverTestCase):
url.encode("ascii"),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(0, channel.json_body["joined_local_devices"])
- def test_room_members(self):
+ def test_room_members(self) -> None:
"""Test that room members can be requested correctly"""
# Create two test rooms
room_id_1 = self.helper.create_room_as(self.admin_user, tok=self.admin_user_tok)
@@ -1687,7 +1691,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
url.encode("ascii"),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertCountEqual(
["@admin:test", "@foo:test", "@bar:test"], channel.json_body["members"]
@@ -1700,14 +1704,14 @@ class RoomTestCase(unittest.HomeserverTestCase):
url.encode("ascii"),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertCountEqual(
["@admin:test", "@bar:test", "@foobar:test"], channel.json_body["members"]
)
self.assertEqual(channel.json_body["total"], 3)
- def test_room_state(self):
+ def test_room_state(self) -> None:
"""Test that room state can be requested correctly"""
# Create two test rooms
room_id = self.helper.create_room_as(self.admin_user, tok=self.admin_user_tok)
@@ -1718,13 +1722,15 @@ class RoomTestCase(unittest.HomeserverTestCase):
url.encode("ascii"),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertIn("state", channel.json_body)
# testing that the state events match is painful and not done here. We assume that
# the create_room already does the right thing, so no need to verify that we got
# the state events it created.
- def _set_canonical_alias(self, room_id: str, test_alias: str, admin_user_tok: str):
+ def _set_canonical_alias(
+ self, room_id: str, test_alias: str, admin_user_tok: str
+ ) -> None:
# Create a new alias to this room
url = "/_matrix/client/r0/directory/room/%s" % (urllib.parse.quote(test_alias),)
channel = self.make_request(
@@ -1733,7 +1739,7 @@ class RoomTestCase(unittest.HomeserverTestCase):
{"room_id": room_id},
access_token=admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Set this new alias as the canonical alias for this room
self.helper.send_state(
@@ -1759,7 +1765,7 @@ class JoinAliasRoomTestCase(unittest.HomeserverTestCase):
login.register_servlets,
]
- def prepare(self, reactor, clock, homeserver):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
self.admin_user = self.register_user("admin", "pass", admin=True)
self.admin_user_tok = self.login("admin", "pass")
@@ -1774,124 +1780,117 @@ class JoinAliasRoomTestCase(unittest.HomeserverTestCase):
)
self.url = f"/_synapse/admin/v1/join/{self.public_room_id}"
- def test_requester_is_no_admin(self):
+ def test_requester_is_no_admin(self) -> None:
"""
- If the user is not a server admin, an error 403 is returned.
+ If the user is not a server admin, an error HTTPStatus.FORBIDDEN is returned.
"""
- body = json.dumps({"user_id": self.second_user_id})
channel = self.make_request(
"POST",
self.url,
- content=body,
+ content={"user_id": self.second_user_id},
access_token=self.second_tok,
)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_invalid_parameter(self):
+ def test_invalid_parameter(self) -> None:
"""
If a parameter is missing, return an error
"""
- body = json.dumps({"unknown_parameter": "@unknown:test"})
channel = self.make_request(
"POST",
self.url,
- content=body,
+ content={"unknown_parameter": "@unknown:test"},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.MISSING_PARAM, channel.json_body["errcode"])
- def test_local_user_does_not_exist(self):
+ def test_local_user_does_not_exist(self) -> None:
"""
- Tests that a lookup for a user that does not exist returns a 404
+ Tests that a lookup for a user that does not exist returns a HTTPStatus.NOT_FOUND
"""
- body = json.dumps({"user_id": "@unknown:test"})
channel = self.make_request(
"POST",
self.url,
- content=body,
+ content={"user_id": "@unknown:test"},
access_token=self.admin_user_tok,
)
- self.assertEqual(404, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.NOT_FOUND, channel.code, msg=channel.json_body)
self.assertEqual(Codes.NOT_FOUND, channel.json_body["errcode"])
- def test_remote_user(self):
+ def test_remote_user(self) -> None:
"""
Check that only local user can join rooms.
"""
- body = json.dumps({"user_id": "@not:exist.bla"})
channel = self.make_request(
"POST",
self.url,
- content=body,
+ content={"user_id": "@not:exist.bla"},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(
"This endpoint can only be used with local users",
channel.json_body["error"],
)
- def test_room_does_not_exist(self):
+ def test_room_does_not_exist(self) -> None:
"""
- Check that unknown rooms/server return error 404.
+ Check that unknown rooms/server return error HTTPStatus.NOT_FOUND.
"""
- body = json.dumps({"user_id": self.second_user_id})
url = "/_synapse/admin/v1/join/!unknown:test"
channel = self.make_request(
"POST",
url,
- content=body,
+ content={"user_id": self.second_user_id},
access_token=self.admin_user_tok,
)
- self.assertEqual(404, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.NOT_FOUND, channel.code, msg=channel.json_body)
self.assertEqual("No known servers", channel.json_body["error"])
- def test_room_is_not_valid(self):
+ def test_room_is_not_valid(self) -> None:
"""
- Check that invalid room names, return an error 400.
+ Check that invalid room names, return an error HTTPStatus.BAD_REQUEST.
"""
- body = json.dumps({"user_id": self.second_user_id})
url = "/_synapse/admin/v1/join/invalidroom"
channel = self.make_request(
"POST",
url,
- content=body,
+ content={"user_id": self.second_user_id},
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(
"invalidroom was not legal room ID or room alias",
channel.json_body["error"],
)
- def test_join_public_room(self):
+ def test_join_public_room(self) -> None:
"""
Test joining a local user to a public room with "JoinRules.PUBLIC"
"""
- body = json.dumps({"user_id": self.second_user_id})
channel = self.make_request(
"POST",
self.url,
- content=body,
+ content={"user_id": self.second_user_id},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(self.public_room_id, channel.json_body["room_id"])
# Validate if user is a member of the room
@@ -1901,10 +1900,10 @@ class JoinAliasRoomTestCase(unittest.HomeserverTestCase):
"/_matrix/client/r0/joined_rooms",
access_token=self.second_tok,
)
- self.assertEquals(200, channel.code, msg=channel.json_body)
+ self.assertEquals(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(self.public_room_id, channel.json_body["joined_rooms"][0])
- def test_join_private_room_if_not_member(self):
+ def test_join_private_room_if_not_member(self) -> None:
"""
Test joining a local user to a private room with "JoinRules.INVITE"
when server admin is not member of this room.
@@ -1913,19 +1912,18 @@ class JoinAliasRoomTestCase(unittest.HomeserverTestCase):
self.creator, tok=self.creator_tok, is_public=False
)
url = f"/_synapse/admin/v1/join/{private_room_id}"
- body = json.dumps({"user_id": self.second_user_id})
channel = self.make_request(
"POST",
url,
- content=body,
+ content={"user_id": self.second_user_id},
access_token=self.admin_user_tok,
)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_join_private_room_if_member(self):
+ def test_join_private_room_if_member(self) -> None:
"""
Test joining a local user to a private room with "JoinRules.INVITE",
when server admin is member of this room.
@@ -1950,21 +1948,20 @@ class JoinAliasRoomTestCase(unittest.HomeserverTestCase):
"/_matrix/client/r0/joined_rooms",
access_token=self.admin_user_tok,
)
- self.assertEquals(200, channel.code, msg=channel.json_body)
+ self.assertEquals(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(private_room_id, channel.json_body["joined_rooms"][0])
# Join user to room.
url = f"/_synapse/admin/v1/join/{private_room_id}"
- body = json.dumps({"user_id": self.second_user_id})
channel = self.make_request(
"POST",
url,
- content=body,
+ content={"user_id": self.second_user_id},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(private_room_id, channel.json_body["room_id"])
# Validate if user is a member of the room
@@ -1974,10 +1971,10 @@ class JoinAliasRoomTestCase(unittest.HomeserverTestCase):
"/_matrix/client/r0/joined_rooms",
access_token=self.second_tok,
)
- self.assertEquals(200, channel.code, msg=channel.json_body)
+ self.assertEquals(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(private_room_id, channel.json_body["joined_rooms"][0])
- def test_join_private_room_if_owner(self):
+ def test_join_private_room_if_owner(self) -> None:
"""
Test joining a local user to a private room with "JoinRules.INVITE",
when server admin is owner of this room.
@@ -1986,16 +1983,15 @@ class JoinAliasRoomTestCase(unittest.HomeserverTestCase):
self.admin_user, tok=self.admin_user_tok, is_public=False
)
url = f"/_synapse/admin/v1/join/{private_room_id}"
- body = json.dumps({"user_id": self.second_user_id})
channel = self.make_request(
"POST",
url,
- content=body,
+ content={"user_id": self.second_user_id},
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(private_room_id, channel.json_body["room_id"])
# Validate if user is a member of the room
@@ -2005,10 +2001,10 @@ class JoinAliasRoomTestCase(unittest.HomeserverTestCase):
"/_matrix/client/r0/joined_rooms",
access_token=self.second_tok,
)
- self.assertEquals(200, channel.code, msg=channel.json_body)
+ self.assertEquals(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(private_room_id, channel.json_body["joined_rooms"][0])
- def test_context_as_non_admin(self):
+ def test_context_as_non_admin(self) -> None:
"""
Test that, without being admin, one cannot use the context admin API
"""
@@ -2039,10 +2035,10 @@ class JoinAliasRoomTestCase(unittest.HomeserverTestCase):
% (room_id, events[midway]["event_id"]),
access_token=tok,
)
- self.assertEquals(403, channel.code, msg=channel.json_body)
+ self.assertEquals(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_context_as_admin(self):
+ def test_context_as_admin(self) -> None:
"""
Test that, as admin, we can find the context of an event without having joined the room.
"""
@@ -2069,7 +2065,7 @@ class JoinAliasRoomTestCase(unittest.HomeserverTestCase):
% (room_id, events[midway]["event_id"]),
access_token=self.admin_user_tok,
)
- self.assertEquals(200, channel.code, msg=channel.json_body)
+ self.assertEquals(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEquals(
channel.json_body["event"]["event_id"], events[midway]["event_id"]
)
@@ -2098,7 +2094,7 @@ class MakeRoomAdminTestCase(unittest.HomeserverTestCase):
login.register_servlets,
]
- def prepare(self, reactor, clock, homeserver):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
self.admin_user = self.register_user("admin", "pass", admin=True)
self.admin_user_tok = self.login("admin", "pass")
@@ -2115,7 +2111,7 @@ class MakeRoomAdminTestCase(unittest.HomeserverTestCase):
self.public_room_id
)
- def test_public_room(self):
+ def test_public_room(self) -> None:
"""Test that getting admin in a public room works."""
room_id = self.helper.create_room_as(
self.creator, tok=self.creator_tok, is_public=True
@@ -2128,7 +2124,7 @@ class MakeRoomAdminTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Now we test that we can join the room and ban a user.
self.helper.join(room_id, self.admin_user, tok=self.admin_user_tok)
@@ -2140,7 +2136,7 @@ class MakeRoomAdminTestCase(unittest.HomeserverTestCase):
tok=self.admin_user_tok,
)
- def test_private_room(self):
+ def test_private_room(self) -> None:
"""Test that getting admin in a private room works and we get invited."""
room_id = self.helper.create_room_as(
self.creator,
@@ -2155,7 +2151,7 @@ class MakeRoomAdminTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Now we test that we can join the room (we should have received an
# invite) and can ban a user.
@@ -2168,7 +2164,7 @@ class MakeRoomAdminTestCase(unittest.HomeserverTestCase):
tok=self.admin_user_tok,
)
- def test_other_user(self):
+ def test_other_user(self) -> None:
"""Test that giving admin in a public room works to a non-admin user works."""
room_id = self.helper.create_room_as(
self.creator, tok=self.creator_tok, is_public=True
@@ -2181,7 +2177,7 @@ class MakeRoomAdminTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Now we test that we can join the room and ban a user.
self.helper.join(room_id, self.second_user_id, tok=self.second_tok)
@@ -2193,7 +2189,7 @@ class MakeRoomAdminTestCase(unittest.HomeserverTestCase):
tok=self.second_tok,
)
- def test_not_enough_power(self):
+ def test_not_enough_power(self) -> None:
"""Test that we get a sensible error if there are no local room admins."""
room_id = self.helper.create_room_as(
self.creator, tok=self.creator_tok, is_public=True
@@ -2215,11 +2211,11 @@ class MakeRoomAdminTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- # We expect this to fail with a 400 as there are no room admins.
+ # We expect this to fail with a HTTPStatus.BAD_REQUEST as there are no room admins.
#
# (Note we assert the error message to ensure that it's not denied for
# some other reason)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(
channel.json_body["error"],
"No local admin user in room with power to update power levels.",
@@ -2233,7 +2229,7 @@ class BlockRoomTestCase(unittest.HomeserverTestCase):
login.register_servlets,
]
- def prepare(self, reactor, clock, hs):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
self._store = hs.get_datastore()
self.admin_user = self.register_user("admin", "pass", admin=True)
@@ -2248,8 +2244,8 @@ class BlockRoomTestCase(unittest.HomeserverTestCase):
self.url = "/_synapse/admin/v1/rooms/%s/block"
@parameterized.expand([("PUT",), ("GET",)])
- def test_requester_is_no_admin(self, method: str):
- """If the user is not a server admin, an error 403 is returned."""
+ def test_requester_is_no_admin(self, method: str) -> None:
+ """If the user is not a server admin, an error HTTPStatus.FORBIDDEN is returned."""
channel = self.make_request(
method,
@@ -2262,8 +2258,8 @@ class BlockRoomTestCase(unittest.HomeserverTestCase):
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
@parameterized.expand([("PUT",), ("GET",)])
- def test_room_is_not_valid(self, method: str):
- """Check that invalid room names, return an error 400."""
+ def test_room_is_not_valid(self, method: str) -> None:
+ """Check that invalid room names, return an error HTTPStatus.BAD_REQUEST."""
channel = self.make_request(
method,
@@ -2278,7 +2274,7 @@ class BlockRoomTestCase(unittest.HomeserverTestCase):
channel.json_body["error"],
)
- def test_block_is_not_valid(self):
+ def test_block_is_not_valid(self) -> None:
"""If parameter `block` is not valid, return an error."""
# `block` is not valid
@@ -2313,7 +2309,7 @@ class BlockRoomTestCase(unittest.HomeserverTestCase):
self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.NOT_JSON, channel.json_body["errcode"])
- def test_block_room(self):
+ def test_block_room(self) -> None:
"""Test that block a room is successful."""
def _request_and_test_block_room(room_id: str) -> None:
@@ -2337,7 +2333,7 @@ class BlockRoomTestCase(unittest.HomeserverTestCase):
# unknown remote room
_request_and_test_block_room("!unknown:remote")
- def test_block_room_twice(self):
+ def test_block_room_twice(self) -> None:
"""Test that block a room that is already blocked is successful."""
self._is_blocked(self.room_id, expect=False)
@@ -2352,7 +2348,7 @@ class BlockRoomTestCase(unittest.HomeserverTestCase):
self.assertTrue(channel.json_body["block"])
self._is_blocked(self.room_id, expect=True)
- def test_unblock_room(self):
+ def test_unblock_room(self) -> None:
"""Test that unblock a room is successful."""
def _request_and_test_unblock_room(room_id: str) -> None:
@@ -2377,7 +2373,7 @@ class BlockRoomTestCase(unittest.HomeserverTestCase):
# unknown remote room
_request_and_test_unblock_room("!unknown:remote")
- def test_unblock_room_twice(self):
+ def test_unblock_room_twice(self) -> None:
"""Test that unblock a room that is not blocked is successful."""
self._block_room(self.room_id)
@@ -2392,7 +2388,7 @@ class BlockRoomTestCase(unittest.HomeserverTestCase):
self.assertFalse(channel.json_body["block"])
self._is_blocked(self.room_id, expect=False)
- def test_get_blocked_room(self):
+ def test_get_blocked_room(self) -> None:
"""Test get status of a blocked room"""
def _request_blocked_room(room_id: str) -> None:
@@ -2416,7 +2412,7 @@ class BlockRoomTestCase(unittest.HomeserverTestCase):
# unknown remote room
_request_blocked_room("!unknown:remote")
- def test_get_unblocked_room(self):
+ def test_get_unblocked_room(self) -> None:
"""Test get status of a unblocked room"""
def _request_unblocked_room(room_id: str) -> None:
diff --git a/tests/rest/admin/test_server_notice.py b/tests/rest/admin/test_server_notice.py
index fbceba3254..3c59f5f766 100644
--- a/tests/rest/admin/test_server_notice.py
+++ b/tests/rest/admin/test_server_notice.py
@@ -11,14 +11,18 @@
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
-
+from http import HTTPStatus
from typing import List
+from twisted.test.proto_helpers import MemoryReactor
+
import synapse.rest.admin
from synapse.api.errors import Codes
from synapse.rest.client import login, room, sync
+from synapse.server import HomeServer
from synapse.storage.roommember import RoomsForUser
from synapse.types import JsonDict
+from synapse.util import Clock
from tests import unittest
from tests.unittest import override_config
@@ -33,7 +37,7 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
sync.register_servlets,
]
- def prepare(self, reactor, clock, hs):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
self.store = hs.get_datastore()
self.room_shutdown_handler = hs.get_room_shutdown_handler()
self.pagination_handler = hs.get_pagination_handler()
@@ -48,14 +52,18 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
self.url = "/_synapse/admin/v1/send_server_notice"
- def test_no_auth(self):
+ def test_no_auth(self) -> None:
"""Try to send a server notice without authentication."""
channel = self.make_request("POST", self.url)
- self.assertEqual(401, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.UNAUTHORIZED,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
- def test_requester_is_no_admin(self):
+ def test_requester_is_no_admin(self) -> None:
"""If the user is not a server admin, an error is returned."""
channel = self.make_request(
"POST",
@@ -63,12 +71,16 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
access_token=self.other_user_token,
)
- self.assertEqual(403, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.FORBIDDEN,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
@override_config({"server_notices": {"system_mxid_localpart": "notices"}})
- def test_user_does_not_exist(self):
- """Tests that a lookup for a user that does not exist returns a 404"""
+ def test_user_does_not_exist(self) -> None:
+ """Tests that a lookup for a user that does not exist returns a HTTPStatus.NOT_FOUND"""
channel = self.make_request(
"POST",
self.url,
@@ -76,13 +88,13 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
content={"user_id": "@unknown_person:test", "content": ""},
)
- self.assertEqual(404, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.NOT_FOUND, channel.code, msg=channel.json_body)
self.assertEqual(Codes.NOT_FOUND, channel.json_body["errcode"])
@override_config({"server_notices": {"system_mxid_localpart": "notices"}})
- def test_user_is_not_local(self):
+ def test_user_is_not_local(self) -> None:
"""
- Tests that a lookup for a user that is not a local returns a 400
+ Tests that a lookup for a user that is not a local returns a HTTPStatus.BAD_REQUEST
"""
channel = self.make_request(
"POST",
@@ -94,13 +106,13 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(
"Server notices can only be sent to local users", channel.json_body["error"]
)
@override_config({"server_notices": {"system_mxid_localpart": "notices"}})
- def test_invalid_parameter(self):
+ def test_invalid_parameter(self) -> None:
"""If parameters are invalid, an error is returned."""
# no content, no user
@@ -110,7 +122,7 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.NOT_JSON, channel.json_body["errcode"])
# no content
@@ -121,7 +133,7 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
content={"user_id": self.other_user},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.MISSING_PARAM, channel.json_body["errcode"])
# no body
@@ -132,7 +144,7 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
content={"user_id": self.other_user, "content": ""},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
self.assertEqual("'body' not in content", channel.json_body["error"])
@@ -144,11 +156,11 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
content={"user_id": self.other_user, "content": {"body": ""}},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
self.assertEqual("'msgtype' not in content", channel.json_body["error"])
- def test_server_notice_disabled(self):
+ def test_server_notice_disabled(self) -> None:
"""Tests that server returns error if server notice is disabled"""
channel = self.make_request(
"POST",
@@ -160,14 +172,14 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
self.assertEqual(
"Server notices are not enabled on this server", channel.json_body["error"]
)
@override_config({"server_notices": {"system_mxid_localpart": "notices"}})
- def test_send_server_notice(self):
+ def test_send_server_notice(self) -> None:
"""
Tests that sending two server notices is successfully,
the server uses the same room and do not send messages twice.
@@ -185,7 +197,7 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
"content": {"msgtype": "m.text", "body": "test msg one"},
},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# user has one invite
invited_rooms = self._check_invite_and_join_status(self.other_user, 1, 0)
@@ -216,7 +228,7 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
"content": {"msgtype": "m.text", "body": "test msg two"},
},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# user has no new invites or memberships
self._check_invite_and_join_status(self.other_user, 0, 1)
@@ -231,7 +243,7 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
self.assertEqual(messages[1]["sender"], "@notices:test")
@override_config({"server_notices": {"system_mxid_localpart": "notices"}})
- def test_send_server_notice_leave_room(self):
+ def test_send_server_notice_leave_room(self) -> None:
"""
Tests that sending a server notices is successfully.
The user leaves the room and the second message appears
@@ -250,7 +262,7 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
"content": {"msgtype": "m.text", "body": "test msg one"},
},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# user has one invite
invited_rooms = self._check_invite_and_join_status(self.other_user, 1, 0)
@@ -293,7 +305,7 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
"content": {"msgtype": "m.text", "body": "test msg two"},
},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# user has one invite
invited_rooms = self._check_invite_and_join_status(self.other_user, 1, 0)
@@ -315,7 +327,7 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
self.assertNotEqual(first_room_id, second_room_id)
@override_config({"server_notices": {"system_mxid_localpart": "notices"}})
- def test_send_server_notice_delete_room(self):
+ def test_send_server_notice_delete_room(self) -> None:
"""
Tests that the user get server notice in a new room
after the first server notice room was deleted.
@@ -333,7 +345,7 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
"content": {"msgtype": "m.text", "body": "test msg one"},
},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# user has one invite
invited_rooms = self._check_invite_and_join_status(self.other_user, 1, 0)
@@ -382,7 +394,7 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
"content": {"msgtype": "m.text", "body": "test msg two"},
},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# user has one invite
invited_rooms = self._check_invite_and_join_status(self.other_user, 1, 0)
@@ -405,7 +417,7 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
def _check_invite_and_join_status(
self, user_id: str, expected_invites: int, expected_memberships: int
- ) -> RoomsForUser:
+ ) -> List[RoomsForUser]:
"""Check invite and room membership status of a user.
Args
@@ -440,7 +452,7 @@ class ServerNoticeTestCase(unittest.HomeserverTestCase):
channel = self.make_request(
"GET", "/_matrix/client/r0/sync", access_token=token
)
- self.assertEqual(channel.code, 200)
+ self.assertEqual(channel.code, HTTPStatus.OK)
# Get the messages
room = channel.json_body["rooms"]["join"][room_id]
diff --git a/tests/rest/admin/test_statistics.py b/tests/rest/admin/test_statistics.py
index ece89a65ac..7cb8ec57ba 100644
--- a/tests/rest/admin/test_statistics.py
+++ b/tests/rest/admin/test_statistics.py
@@ -12,13 +12,17 @@
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
+from http import HTTPStatus
+from typing import List, Optional
-import json
-from typing import Any, Dict, List, Optional
+from twisted.test.proto_helpers import MemoryReactor
import synapse.rest.admin
from synapse.api.errors import Codes
from synapse.rest.client import login
+from synapse.server import HomeServer
+from synapse.types import JsonDict
+from synapse.util import Clock
from tests import unittest
from tests.test_utils import SMALL_PNG
@@ -30,7 +34,7 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
login.register_servlets,
]
- def prepare(self, reactor, clock, hs):
+ def prepare(self, reactor: MemoryReactor, clock: Clock, hs: HomeServer) -> None:
self.media_repo = hs.get_media_repository_resource()
self.admin_user = self.register_user("admin", "pass", admin=True)
@@ -41,30 +45,38 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
self.url = "/_synapse/admin/v1/statistics/users/media"
- def test_no_auth(self):
+ def test_no_auth(self) -> None:
"""
Try to list users without authentication.
"""
channel = self.make_request("GET", self.url, b"{}")
- self.assertEqual(401, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.UNAUTHORIZED,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
- def test_requester_is_no_admin(self):
+ def test_requester_is_no_admin(self) -> None:
"""
- If the user is not a server admin, an error 403 is returned.
+ If the user is not a server admin, an error HTTPStatus.FORBIDDEN is returned.
"""
channel = self.make_request(
"GET",
self.url,
- json.dumps({}),
+ {},
access_token=self.other_user_tok,
)
- self.assertEqual(403, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.FORBIDDEN,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
- def test_invalid_parameter(self):
+ def test_invalid_parameter(self) -> None:
"""
If parameters are invalid, an error is returned.
"""
@@ -75,7 +87,11 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
# negative from
@@ -85,7 +101,11 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
# negative limit
@@ -95,7 +115,11 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
# negative from_ts
@@ -105,7 +129,11 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
# negative until_ts
@@ -115,7 +143,11 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
# until_ts smaller from_ts
@@ -125,7 +157,11 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
# empty search term
@@ -135,7 +171,11 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
# invalid search order
@@ -145,10 +185,14 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
- def test_limit(self):
+ def test_limit(self) -> None:
"""
Testing list of media with limit
"""
@@ -160,13 +204,13 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 10)
self.assertEqual(len(channel.json_body["users"]), 5)
self.assertEqual(channel.json_body["next_token"], 5)
self._check_fields(channel.json_body["users"])
- def test_from(self):
+ def test_from(self) -> None:
"""
Testing list of media with a defined starting point (from)
"""
@@ -178,13 +222,13 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 20)
self.assertEqual(len(channel.json_body["users"]), 15)
self.assertNotIn("next_token", channel.json_body)
self._check_fields(channel.json_body["users"])
- def test_limit_and_from(self):
+ def test_limit_and_from(self) -> None:
"""
Testing list of media with a defined starting point and limit
"""
@@ -196,13 +240,13 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 20)
self.assertEqual(channel.json_body["next_token"], 15)
self.assertEqual(len(channel.json_body["users"]), 10)
self._check_fields(channel.json_body["users"])
- def test_next_token(self):
+ def test_next_token(self) -> None:
"""
Testing that `next_token` appears at the right place
"""
@@ -218,7 +262,7 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_users)
self.assertEqual(len(channel.json_body["users"]), number_users)
self.assertNotIn("next_token", channel.json_body)
@@ -231,7 +275,7 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_users)
self.assertEqual(len(channel.json_body["users"]), number_users)
self.assertNotIn("next_token", channel.json_body)
@@ -244,7 +288,7 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_users)
self.assertEqual(len(channel.json_body["users"]), 19)
self.assertEqual(channel.json_body["next_token"], 19)
@@ -257,12 +301,12 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_users)
self.assertEqual(len(channel.json_body["users"]), 1)
self.assertNotIn("next_token", channel.json_body)
- def test_no_media(self):
+ def test_no_media(self) -> None:
"""
Tests that a normal lookup for statistics is successfully
if users have no media created
@@ -274,11 +318,11 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(0, channel.json_body["total"])
self.assertEqual(0, len(channel.json_body["users"]))
- def test_order_by(self):
+ def test_order_by(self) -> None:
"""
Testing order list with parameter `order_by`
"""
@@ -356,7 +400,7 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
"b",
)
- def test_from_until_ts(self):
+ def test_from_until_ts(self) -> None:
"""
Testing filter by time with parameters `from_ts` and `until_ts`
"""
@@ -371,7 +415,7 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
self.url,
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["users"][0]["media_count"], 3)
# filter media starting at `ts1` after creating first media
@@ -381,7 +425,7 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
self.url + "?from_ts=%s" % (ts1,),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 0)
self._create_media(self.other_user_tok, 3)
@@ -396,7 +440,7 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
self.url + "?from_ts=%s&until_ts=%s" % (ts1, ts2),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["users"][0]["media_count"], 3)
# filter media until `ts2` and earlier
@@ -405,10 +449,10 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
self.url + "?until_ts=%s" % (ts2,),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["users"][0]["media_count"], 6)
- def test_search_term(self):
+ def test_search_term(self) -> None:
self._create_users_with_media(20, 1)
# check without filter get all users
@@ -417,7 +461,7 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
self.url,
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 20)
# filter user 1 and 10-19 by `user_id`
@@ -426,7 +470,7 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
self.url + "?search_term=foo_user_1",
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 11)
# filter on this user in `displayname`
@@ -435,7 +479,7 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
self.url + "?search_term=bar_user_10",
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["users"][0]["displayname"], "bar_user_10")
self.assertEqual(channel.json_body["total"], 1)
@@ -445,10 +489,10 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
self.url + "?search_term=foobar",
access_token=self.admin_user_tok,
)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 0)
- def _create_users_with_media(self, number_users: int, media_per_user: int):
+ def _create_users_with_media(self, number_users: int, media_per_user: int) -> None:
"""
Create a number of users with a number of media
Args:
@@ -460,7 +504,7 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
user_tok = self.login("foo_user_%s" % i, "pass")
self._create_media(user_tok, media_per_user)
- def _create_media(self, user_token: str, number_media: int):
+ def _create_media(self, user_token: str, number_media: int) -> None:
"""
Create a number of media for a specific user
Args:
@@ -471,10 +515,10 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
for _ in range(number_media):
# Upload some media into the room
self.helper.upload_media(
- upload_resource, SMALL_PNG, tok=user_token, expect_code=200
+ upload_resource, SMALL_PNG, tok=user_token, expect_code=HTTPStatus.OK
)
- def _check_fields(self, content: List[Dict[str, Any]]):
+ def _check_fields(self, content: List[JsonDict]) -> None:
"""Checks that all attributes are present in content
Args:
content: List that is checked for content
@@ -487,7 +531,7 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
def _order_test(
self, order_type: str, expected_user_list: List[str], dir: Optional[str] = None
- ):
+ ) -> None:
"""Request the list of users in a certain order. Assert that order is what
we expect
Args:
@@ -505,7 +549,7 @@ class UserMediaStatisticsTestCase(unittest.HomeserverTestCase):
url.encode("ascii"),
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], len(expected_user_list))
returned_order = [row["user_id"] for row in channel.json_body["users"]]
diff --git a/tests/rest/admin/test_user.py b/tests/rest/admin/test_user.py
index 5011e54563..4fedd5fd08 100644
--- a/tests/rest/admin/test_user.py
+++ b/tests/rest/admin/test_user.py
@@ -17,6 +17,7 @@ import hmac
import os
import urllib.parse
from binascii import unhexlify
+from http import HTTPStatus
from typing import List, Optional
from unittest.mock import Mock, patch
@@ -74,7 +75,7 @@ class UserRegisterTestCase(unittest.HomeserverTestCase):
channel = self.make_request("POST", self.url, b"{}")
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(
"Shared secret registration is not enabled", channel.json_body["error"]
)
@@ -106,7 +107,7 @@ class UserRegisterTestCase(unittest.HomeserverTestCase):
body = {"nonce": nonce}
channel = self.make_request("POST", self.url, body)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("username must be specified", channel.json_body["error"])
# 61 seconds
@@ -114,7 +115,7 @@ class UserRegisterTestCase(unittest.HomeserverTestCase):
channel = self.make_request("POST", self.url, body)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("unrecognised nonce", channel.json_body["error"])
def test_register_incorrect_nonce(self):
@@ -126,18 +127,18 @@ class UserRegisterTestCase(unittest.HomeserverTestCase):
want_mac = hmac.new(key=b"shared", digestmod=hashlib.sha1)
want_mac.update(b"notthenonce\x00bob\x00abc123\x00admin")
- want_mac = want_mac.hexdigest()
+ want_mac_str = want_mac.hexdigest()
body = {
"nonce": nonce,
"username": "bob",
"password": "abc123",
"admin": True,
- "mac": want_mac,
+ "mac": want_mac_str,
}
channel = self.make_request("POST", self.url, body)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual("HMAC incorrect", channel.json_body["error"])
def test_register_correct_nonce(self):
@@ -152,7 +153,7 @@ class UserRegisterTestCase(unittest.HomeserverTestCase):
want_mac.update(
nonce.encode("ascii") + b"\x00bob\x00abc123\x00admin\x00support"
)
- want_mac = want_mac.hexdigest()
+ want_mac_str = want_mac.hexdigest()
body = {
"nonce": nonce,
@@ -160,11 +161,11 @@ class UserRegisterTestCase(unittest.HomeserverTestCase):
"password": "abc123",
"admin": True,
"user_type": UserTypes.SUPPORT,
- "mac": want_mac,
+ "mac": want_mac_str,
}
channel = self.make_request("POST", self.url, body)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@bob:test", channel.json_body["user_id"])
def test_nonce_reuse(self):
@@ -176,24 +177,24 @@ class UserRegisterTestCase(unittest.HomeserverTestCase):
want_mac = hmac.new(key=b"shared", digestmod=hashlib.sha1)
want_mac.update(nonce.encode("ascii") + b"\x00bob\x00abc123\x00admin")
- want_mac = want_mac.hexdigest()
+ want_mac_str = want_mac.hexdigest()
body = {
"nonce": nonce,
"username": "bob",
"password": "abc123",
"admin": True,
- "mac": want_mac,
+ "mac": want_mac_str,
}
channel = self.make_request("POST", self.url, body)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@bob:test", channel.json_body["user_id"])
# Now, try and reuse it
channel = self.make_request("POST", self.url, body)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("unrecognised nonce", channel.json_body["error"])
def test_missing_parts(self):
@@ -214,7 +215,7 @@ class UserRegisterTestCase(unittest.HomeserverTestCase):
# Must be an empty body present
channel = self.make_request("POST", self.url, {})
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("nonce must be specified", channel.json_body["error"])
#
@@ -224,28 +225,28 @@ class UserRegisterTestCase(unittest.HomeserverTestCase):
# Must be present
channel = self.make_request("POST", self.url, {"nonce": nonce()})
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("username must be specified", channel.json_body["error"])
# Must be a string
body = {"nonce": nonce(), "username": 1234}
channel = self.make_request("POST", self.url, body)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("Invalid username", channel.json_body["error"])
# Must not have null bytes
body = {"nonce": nonce(), "username": "abcd\u0000"}
channel = self.make_request("POST", self.url, body)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("Invalid username", channel.json_body["error"])
# Must not have null bytes
body = {"nonce": nonce(), "username": "a" * 1000}
channel = self.make_request("POST", self.url, body)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("Invalid username", channel.json_body["error"])
#
@@ -256,28 +257,28 @@ class UserRegisterTestCase(unittest.HomeserverTestCase):
body = {"nonce": nonce(), "username": "a"}
channel = self.make_request("POST", self.url, body)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("password must be specified", channel.json_body["error"])
# Must be a string
body = {"nonce": nonce(), "username": "a", "password": 1234}
channel = self.make_request("POST", self.url, body)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("Invalid password", channel.json_body["error"])
# Must not have null bytes
body = {"nonce": nonce(), "username": "a", "password": "abcd\u0000"}
channel = self.make_request("POST", self.url, body)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("Invalid password", channel.json_body["error"])
# Super long
body = {"nonce": nonce(), "username": "a", "password": "A" * 1000}
channel = self.make_request("POST", self.url, body)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("Invalid password", channel.json_body["error"])
#
@@ -293,7 +294,7 @@ class UserRegisterTestCase(unittest.HomeserverTestCase):
}
channel = self.make_request("POST", self.url, body)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("Invalid user type", channel.json_body["error"])
def test_displayname(self):
@@ -307,22 +308,22 @@ class UserRegisterTestCase(unittest.HomeserverTestCase):
want_mac = hmac.new(key=b"shared", digestmod=hashlib.sha1)
want_mac.update(nonce.encode("ascii") + b"\x00bob1\x00abc123\x00notadmin")
- want_mac = want_mac.hexdigest()
+ want_mac_str = want_mac.hexdigest()
body = {
"nonce": nonce,
"username": "bob1",
"password": "abc123",
- "mac": want_mac,
+ "mac": want_mac_str,
}
channel = self.make_request("POST", self.url, body)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@bob1:test", channel.json_body["user_id"])
channel = self.make_request("GET", "/profile/@bob1:test/displayname")
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("bob1", channel.json_body["displayname"])
# displayname is None
@@ -331,22 +332,22 @@ class UserRegisterTestCase(unittest.HomeserverTestCase):
want_mac = hmac.new(key=b"shared", digestmod=hashlib.sha1)
want_mac.update(nonce.encode("ascii") + b"\x00bob2\x00abc123\x00notadmin")
- want_mac = want_mac.hexdigest()
+ want_mac_str = want_mac.hexdigest()
body = {
"nonce": nonce,
"username": "bob2",
"displayname": None,
"password": "abc123",
- "mac": want_mac,
+ "mac": want_mac_str,
}
channel = self.make_request("POST", self.url, body)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@bob2:test", channel.json_body["user_id"])
channel = self.make_request("GET", "/profile/@bob2:test/displayname")
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("bob2", channel.json_body["displayname"])
# displayname is empty
@@ -355,22 +356,22 @@ class UserRegisterTestCase(unittest.HomeserverTestCase):
want_mac = hmac.new(key=b"shared", digestmod=hashlib.sha1)
want_mac.update(nonce.encode("ascii") + b"\x00bob3\x00abc123\x00notadmin")
- want_mac = want_mac.hexdigest()
+ want_mac_str = want_mac.hexdigest()
body = {
"nonce": nonce,
"username": "bob3",
"displayname": "",
"password": "abc123",
- "mac": want_mac,
+ "mac": want_mac_str,
}
channel = self.make_request("POST", self.url, body)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@bob3:test", channel.json_body["user_id"])
channel = self.make_request("GET", "/profile/@bob3:test/displayname")
- self.assertEqual(404, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.NOT_FOUND, channel.code, msg=channel.json_body)
# set displayname
channel = self.make_request("GET", self.url)
@@ -378,22 +379,22 @@ class UserRegisterTestCase(unittest.HomeserverTestCase):
want_mac = hmac.new(key=b"shared", digestmod=hashlib.sha1)
want_mac.update(nonce.encode("ascii") + b"\x00bob4\x00abc123\x00notadmin")
- want_mac = want_mac.hexdigest()
+ want_mac_str = want_mac.hexdigest()
body = {
"nonce": nonce,
"username": "bob4",
"displayname": "Bob's Name",
"password": "abc123",
- "mac": want_mac,
+ "mac": want_mac_str,
}
channel = self.make_request("POST", self.url, body)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@bob4:test", channel.json_body["user_id"])
channel = self.make_request("GET", "/profile/@bob4:test/displayname")
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("Bob's Name", channel.json_body["displayname"])
@override_config(
@@ -425,7 +426,7 @@ class UserRegisterTestCase(unittest.HomeserverTestCase):
want_mac.update(
nonce.encode("ascii") + b"\x00bob\x00abc123\x00admin\x00support"
)
- want_mac = want_mac.hexdigest()
+ want_mac_str = want_mac.hexdigest()
body = {
"nonce": nonce,
@@ -433,11 +434,11 @@ class UserRegisterTestCase(unittest.HomeserverTestCase):
"password": "abc123",
"admin": True,
"user_type": UserTypes.SUPPORT,
- "mac": want_mac,
+ "mac": want_mac_str,
}
channel = self.make_request("POST", self.url, body)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@bob:test", channel.json_body["user_id"])
@@ -461,7 +462,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
"""
channel = self.make_request("GET", self.url, b"{}")
- self.assertEqual(401, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.UNAUTHORIZED, channel.code, msg=channel.json_body)
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
def test_requester_is_no_admin(self):
@@ -473,7 +474,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
channel = self.make_request("GET", self.url, access_token=other_user_token)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
def test_all_users(self):
@@ -489,7 +490,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(3, len(channel.json_body["users"]))
self.assertEqual(3, channel.json_body["total"])
@@ -503,7 +504,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
expected_user_id: Optional[str],
search_term: str,
search_field: Optional[str] = "name",
- expected_http_code: Optional[int] = 200,
+ expected_http_code: Optional[int] = HTTPStatus.OK,
):
"""Search for a user and check that the returned user's id is a match
@@ -525,7 +526,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
)
self.assertEqual(expected_http_code, channel.code, msg=channel.json_body)
- if expected_http_code != 200:
+ if expected_http_code != HTTPStatus.OK:
return
# Check that users were returned
@@ -586,7 +587,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
# negative from
@@ -596,7 +597,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
# invalid guests
@@ -606,7 +607,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
# invalid deactivated
@@ -616,7 +617,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
# unkown order_by
@@ -626,7 +627,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
# invalid search order
@@ -636,7 +637,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
def test_limit(self):
@@ -654,7 +655,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_users)
self.assertEqual(len(channel.json_body["users"]), 5)
self.assertEqual(channel.json_body["next_token"], "5")
@@ -675,7 +676,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_users)
self.assertEqual(len(channel.json_body["users"]), 15)
self.assertNotIn("next_token", channel.json_body)
@@ -696,7 +697,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_users)
self.assertEqual(channel.json_body["next_token"], "15")
self.assertEqual(len(channel.json_body["users"]), 10)
@@ -719,7 +720,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_users)
self.assertEqual(len(channel.json_body["users"]), number_users)
self.assertNotIn("next_token", channel.json_body)
@@ -732,7 +733,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_users)
self.assertEqual(len(channel.json_body["users"]), number_users)
self.assertNotIn("next_token", channel.json_body)
@@ -745,7 +746,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_users)
self.assertEqual(len(channel.json_body["users"]), 19)
self.assertEqual(channel.json_body["next_token"], "19")
@@ -759,7 +760,7 @@ class UsersListTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_users)
self.assertEqual(len(channel.json_body["users"]), 1)
self.assertNotIn("next_token", channel.json_body)
@@ -862,14 +863,14 @@ class UsersListTestCase(unittest.HomeserverTestCase):
url,
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], len(expected_user_list))
returned_order = [row["name"] for row in channel.json_body["users"]]
self.assertEqual(expected_user_list, returned_order)
self._check_fields(channel.json_body["users"])
- def _check_fields(self, content: JsonDict):
+ def _check_fields(self, content: List[JsonDict]):
"""Checks that the expected user attributes are present in content
Args:
content: List that is checked for content
@@ -936,7 +937,7 @@ class DeactivateAccountTestCase(unittest.HomeserverTestCase):
"""
channel = self.make_request("POST", self.url, b"{}")
- self.assertEqual(401, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.UNAUTHORIZED, channel.code, msg=channel.json_body)
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
def test_requester_is_not_admin(self):
@@ -947,7 +948,7 @@ class DeactivateAccountTestCase(unittest.HomeserverTestCase):
channel = self.make_request("POST", url, access_token=self.other_user_token)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual("You are not a server admin", channel.json_body["error"])
channel = self.make_request(
@@ -957,12 +958,12 @@ class DeactivateAccountTestCase(unittest.HomeserverTestCase):
content=b"{}",
)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual("You are not a server admin", channel.json_body["error"])
def test_user_does_not_exist(self):
"""
- Tests that deactivation for a user that does not exist returns a 404
+ Tests that deactivation for a user that does not exist returns a HTTPStatus.NOT_FOUND
"""
channel = self.make_request(
@@ -971,7 +972,7 @@ class DeactivateAccountTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(404, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.NOT_FOUND, channel.code, msg=channel.json_body)
self.assertEqual(Codes.NOT_FOUND, channel.json_body["errcode"])
def test_erase_is_not_bool(self):
@@ -986,18 +987,18 @@ class DeactivateAccountTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.BAD_JSON, channel.json_body["errcode"])
def test_user_is_not_local(self):
"""
- Tests that deactivation for a user that is not a local returns a 400
+ Tests that deactivation for a user that is not a local returns a HTTPStatus.BAD_REQUEST
"""
url = "/_synapse/admin/v1/deactivate/@unknown_person:unknown_domain"
channel = self.make_request("POST", url, access_token=self.admin_user_tok)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("Can only deactivate local users", channel.json_body["error"])
def test_deactivate_user_erase_true(self):
@@ -1012,7 +1013,7 @@ class DeactivateAccountTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(False, channel.json_body["deactivated"])
self.assertEqual("foo@bar.com", channel.json_body["threepids"][0]["address"])
@@ -1027,7 +1028,7 @@ class DeactivateAccountTestCase(unittest.HomeserverTestCase):
content={"erase": True},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Get user
channel = self.make_request(
@@ -1036,7 +1037,7 @@ class DeactivateAccountTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(True, channel.json_body["deactivated"])
self.assertEqual(0, len(channel.json_body["threepids"]))
@@ -1057,7 +1058,7 @@ class DeactivateAccountTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(False, channel.json_body["deactivated"])
self.assertEqual("foo@bar.com", channel.json_body["threepids"][0]["address"])
@@ -1072,7 +1073,7 @@ class DeactivateAccountTestCase(unittest.HomeserverTestCase):
content={"erase": False},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Get user
channel = self.make_request(
@@ -1081,7 +1082,7 @@ class DeactivateAccountTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(True, channel.json_body["deactivated"])
self.assertEqual(0, len(channel.json_body["threepids"]))
@@ -1111,7 +1112,7 @@ class DeactivateAccountTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(False, channel.json_body["deactivated"])
self.assertEqual("foo@bar.com", channel.json_body["threepids"][0]["address"])
@@ -1126,7 +1127,7 @@ class DeactivateAccountTestCase(unittest.HomeserverTestCase):
content={"erase": True},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Get user
channel = self.make_request(
@@ -1135,7 +1136,7 @@ class DeactivateAccountTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(True, channel.json_body["deactivated"])
self.assertEqual(0, len(channel.json_body["threepids"]))
@@ -1195,7 +1196,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.other_user_token,
)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual("You are not a server admin", channel.json_body["error"])
channel = self.make_request(
@@ -1205,12 +1206,12 @@ class UserRestTestCase(unittest.HomeserverTestCase):
content=b"{}",
)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual("You are not a server admin", channel.json_body["error"])
def test_user_does_not_exist(self):
"""
- Tests that a lookup for a user that does not exist returns a 404
+ Tests that a lookup for a user that does not exist returns a HTTPStatus.NOT_FOUND
"""
channel = self.make_request(
@@ -1219,7 +1220,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(404, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.NOT_FOUND, channel.code, msg=channel.json_body)
self.assertEqual("M_NOT_FOUND", channel.json_body["errcode"])
def test_invalid_parameter(self):
@@ -1234,7 +1235,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"admin": "not_bool"},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.BAD_JSON, channel.json_body["errcode"])
# deactivated not bool
@@ -1244,7 +1245,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"deactivated": "not_bool"},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
# password not str
@@ -1254,7 +1255,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"password": True},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
# password not length
@@ -1264,7 +1265,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"password": "x" * 513},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
# user_type not valid
@@ -1274,7 +1275,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"user_type": "new type"},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
# external_ids not valid
@@ -1286,7 +1287,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
"external_ids": {"auth_provider": "prov", "wrong_external_id": "id"}
},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.MISSING_PARAM, channel.json_body["errcode"])
channel = self.make_request(
@@ -1295,7 +1296,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"external_ids": {"external_id": "id"}},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.MISSING_PARAM, channel.json_body["errcode"])
# threepids not valid
@@ -1305,7 +1306,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"threepids": {"medium": "email", "wrong_address": "id"}},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.MISSING_PARAM, channel.json_body["errcode"])
channel = self.make_request(
@@ -1314,7 +1315,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"threepids": {"address": "value"}},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.MISSING_PARAM, channel.json_body["errcode"])
def test_get_user(self):
@@ -1327,7 +1328,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual("User", channel.json_body["displayname"])
self._check_fields(channel.json_body)
@@ -1370,7 +1371,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@bob:test", channel.json_body["name"])
self.assertEqual("Bob's name", channel.json_body["displayname"])
self.assertEqual("email", channel.json_body["threepids"][0]["medium"])
@@ -1433,7 +1434,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@bob:test", channel.json_body["name"])
self.assertEqual("Bob's name", channel.json_body["displayname"])
self.assertEqual("email", channel.json_body["threepids"][0]["medium"])
@@ -1461,9 +1462,9 @@ class UserRestTestCase(unittest.HomeserverTestCase):
# before limit of monthly active users is reached
channel = self.make_request("GET", "/sync", access_token=self.admin_user_tok)
- if channel.code != 200:
+ if channel.code != HTTPStatus.OK:
raise HttpResponseException(
- channel.code, channel.result["reason"], channel.result["body"]
+ channel.code, channel.result["reason"], channel.json_body
)
# Set monthly active users to the limit
@@ -1625,7 +1626,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
content={"password": "hahaha"},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self._check_fields(channel.json_body)
def test_set_displayname(self):
@@ -1641,7 +1642,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
content={"displayname": "foobar"},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual("foobar", channel.json_body["displayname"])
@@ -1652,7 +1653,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual("foobar", channel.json_body["displayname"])
@@ -1674,7 +1675,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(2, len(channel.json_body["threepids"]))
# result does not always have the same sort order, therefore it becomes sorted
@@ -1700,7 +1701,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(2, len(channel.json_body["threepids"]))
self.assertEqual("email", channel.json_body["threepids"][0]["medium"])
@@ -1716,7 +1717,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(2, len(channel.json_body["threepids"]))
self.assertEqual("email", channel.json_body["threepids"][0]["medium"])
@@ -1732,7 +1733,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"threepids": []},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(0, len(channel.json_body["threepids"]))
self._check_fields(channel.json_body)
@@ -1759,7 +1760,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(first_user, channel.json_body["name"])
self.assertEqual(1, len(channel.json_body["threepids"]))
self.assertEqual("email", channel.json_body["threepids"][0]["medium"])
@@ -1778,7 +1779,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(1, len(channel.json_body["threepids"]))
self.assertEqual("email", channel.json_body["threepids"][0]["medium"])
@@ -1800,7 +1801,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
)
# other user has this two threepids
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(2, len(channel.json_body["threepids"]))
# result does not always have the same sort order, therefore it becomes sorted
@@ -1819,7 +1820,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
url_first_user,
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(first_user, channel.json_body["name"])
self.assertEqual(0, len(channel.json_body["threepids"]))
self._check_fields(channel.json_body)
@@ -1848,7 +1849,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(2, len(channel.json_body["external_ids"]))
# result does not always have the same sort order, therefore it becomes sorted
@@ -1880,7 +1881,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(2, len(channel.json_body["external_ids"]))
self.assertEqual(
@@ -1899,7 +1900,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(2, len(channel.json_body["external_ids"]))
self.assertEqual(
@@ -1918,7 +1919,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"external_ids": []},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(0, len(channel.json_body["external_ids"]))
@@ -1947,7 +1948,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(first_user, channel.json_body["name"])
self.assertEqual(1, len(channel.json_body["external_ids"]))
self.assertEqual(
@@ -1973,7 +1974,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(1, len(channel.json_body["external_ids"]))
self.assertEqual(
@@ -2005,7 +2006,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
)
# must fail
- self.assertEqual(409, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.CONFLICT, channel.code, msg=channel.json_body)
self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
self.assertEqual("External id is already in use.", channel.json_body["error"])
@@ -2016,7 +2017,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(1, len(channel.json_body["external_ids"]))
self.assertEqual(
@@ -2034,7 +2035,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(first_user, channel.json_body["name"])
self.assertEqual(1, len(channel.json_body["external_ids"]))
self.assertEqual(
@@ -2065,7 +2066,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertFalse(channel.json_body["deactivated"])
self.assertEqual("foo@bar.com", channel.json_body["threepids"][0]["address"])
@@ -2080,7 +2081,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
content={"deactivated": True},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertTrue(channel.json_body["deactivated"])
self.assertIsNone(channel.json_body["password_hash"])
@@ -2096,7 +2097,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertTrue(channel.json_body["deactivated"])
self.assertIsNone(channel.json_body["password_hash"])
@@ -2123,7 +2124,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
content={"deactivated": True},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertTrue(channel.json_body["deactivated"])
@@ -2139,7 +2140,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
content={"displayname": "Foobar"},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertTrue(channel.json_body["deactivated"])
self.assertEqual("Foobar", channel.json_body["displayname"])
@@ -2163,7 +2164,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"deactivated": False},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
# Reactivate the user.
channel = self.make_request(
@@ -2172,7 +2173,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"deactivated": False, "password": "foo"},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertFalse(channel.json_body["deactivated"])
self.assertIsNotNone(channel.json_body["password_hash"])
@@ -2194,7 +2195,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"deactivated": False, "password": "foo"},
)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
# Reactivate the user without a password.
@@ -2204,7 +2205,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"deactivated": False},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertFalse(channel.json_body["deactivated"])
self.assertIsNone(channel.json_body["password_hash"])
@@ -2226,7 +2227,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"deactivated": False, "password": "foo"},
)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
# Reactivate the user without a password.
@@ -2236,7 +2237,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"deactivated": False},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertFalse(channel.json_body["deactivated"])
self.assertIsNone(channel.json_body["password_hash"])
@@ -2255,7 +2256,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
content={"admin": True},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertTrue(channel.json_body["admin"])
@@ -2266,7 +2267,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertTrue(channel.json_body["admin"])
@@ -2283,7 +2284,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
content={"user_type": UserTypes.SUPPORT},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(UserTypes.SUPPORT, channel.json_body["user_type"])
@@ -2294,7 +2295,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertEqual(UserTypes.SUPPORT, channel.json_body["user_type"])
@@ -2306,7 +2307,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
content={"user_type": None},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertIsNone(channel.json_body["user_type"])
@@ -2317,7 +2318,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@user:test", channel.json_body["name"])
self.assertIsNone(channel.json_body["user_type"])
@@ -2347,7 +2348,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@bob:test", channel.json_body["name"])
self.assertEqual("bob", channel.json_body["displayname"])
self.assertEqual(0, channel.json_body["deactivated"])
@@ -2360,7 +2361,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
content={"password": "abc123", "deactivated": "false"},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
# Check user is not deactivated
channel = self.make_request(
@@ -2369,7 +2370,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual("@bob:test", channel.json_body["name"])
self.assertEqual("bob", channel.json_body["displayname"])
@@ -2394,7 +2395,7 @@ class UserRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"deactivated": True},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertTrue(channel.json_body["deactivated"])
self.assertIsNone(channel.json_body["password_hash"])
self._is_erased(user_id, False)
@@ -2445,7 +2446,7 @@ class UserMembershipRestTestCase(unittest.HomeserverTestCase):
"""
channel = self.make_request("GET", self.url, b"{}")
- self.assertEqual(401, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.UNAUTHORIZED, channel.code, msg=channel.json_body)
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
def test_requester_is_no_admin(self):
@@ -2460,7 +2461,7 @@ class UserMembershipRestTestCase(unittest.HomeserverTestCase):
access_token=other_user_token,
)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
def test_user_does_not_exist(self):
@@ -2474,7 +2475,7 @@ class UserMembershipRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(0, channel.json_body["total"])
self.assertEqual(0, len(channel.json_body["joined_rooms"]))
@@ -2490,7 +2491,7 @@ class UserMembershipRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(0, channel.json_body["total"])
self.assertEqual(0, len(channel.json_body["joined_rooms"]))
@@ -2506,7 +2507,7 @@ class UserMembershipRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(0, channel.json_body["total"])
self.assertEqual(0, len(channel.json_body["joined_rooms"]))
@@ -2527,7 +2528,7 @@ class UserMembershipRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(number_rooms, channel.json_body["total"])
self.assertEqual(number_rooms, len(channel.json_body["joined_rooms"]))
@@ -2574,7 +2575,7 @@ class UserMembershipRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(1, channel.json_body["total"])
self.assertEqual([local_and_remote_room_id], channel.json_body["joined_rooms"])
@@ -2603,7 +2604,7 @@ class PushersRestTestCase(unittest.HomeserverTestCase):
"""
channel = self.make_request("GET", self.url, b"{}")
- self.assertEqual(401, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.UNAUTHORIZED, channel.code, msg=channel.json_body)
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
def test_requester_is_no_admin(self):
@@ -2618,12 +2619,12 @@ class PushersRestTestCase(unittest.HomeserverTestCase):
access_token=other_user_token,
)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
def test_user_does_not_exist(self):
"""
- Tests that a lookup for a user that does not exist returns a 404
+ Tests that a lookup for a user that does not exist returns a HTTPStatus.NOT_FOUND
"""
url = "/_synapse/admin/v1/users/@unknown_person:test/pushers"
channel = self.make_request(
@@ -2632,12 +2633,12 @@ class PushersRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(404, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.NOT_FOUND, channel.code, msg=channel.json_body)
self.assertEqual(Codes.NOT_FOUND, channel.json_body["errcode"])
def test_user_is_not_local(self):
"""
- Tests that a lookup for a user that is not a local returns a 400
+ Tests that a lookup for a user that is not a local returns a HTTPStatus.BAD_REQUEST
"""
url = "/_synapse/admin/v1/users/@unknown_person:unknown_domain/pushers"
@@ -2647,7 +2648,7 @@ class PushersRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("Can only look up local users", channel.json_body["error"])
def test_get_pushers(self):
@@ -2662,7 +2663,7 @@ class PushersRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(0, channel.json_body["total"])
# Register the pusher
@@ -2693,7 +2694,7 @@ class PushersRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(1, channel.json_body["total"])
for p in channel.json_body["pushers"]:
@@ -2732,7 +2733,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
"""Try to list media of an user without authentication."""
channel = self.make_request(method, self.url, {})
- self.assertEqual(401, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.UNAUTHORIZED, channel.code, msg=channel.json_body)
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
@parameterized.expand(["GET", "DELETE"])
@@ -2746,12 +2747,12 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=other_user_token,
)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
@parameterized.expand(["GET", "DELETE"])
def test_user_does_not_exist(self, method: str):
- """Tests that a lookup for a user that does not exist returns a 404"""
+ """Tests that a lookup for a user that does not exist returns a HTTPStatus.NOT_FOUND"""
url = "/_synapse/admin/v1/users/@unknown_person:test/media"
channel = self.make_request(
method,
@@ -2759,12 +2760,12 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(404, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.NOT_FOUND, channel.code, msg=channel.json_body)
self.assertEqual(Codes.NOT_FOUND, channel.json_body["errcode"])
@parameterized.expand(["GET", "DELETE"])
def test_user_is_not_local(self, method: str):
- """Tests that a lookup for a user that is not a local returns a 400"""
+ """Tests that a lookup for a user that is not a local returns a HTTPStatus.BAD_REQUEST"""
url = "/_synapse/admin/v1/users/@unknown_person:unknown_domain/media"
channel = self.make_request(
@@ -2773,7 +2774,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("Can only look up local users", channel.json_body["error"])
def test_limit_GET(self):
@@ -2789,7 +2790,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_media)
self.assertEqual(len(channel.json_body["media"]), 5)
self.assertEqual(channel.json_body["next_token"], 5)
@@ -2808,7 +2809,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 5)
self.assertEqual(len(channel.json_body["deleted_media"]), 5)
@@ -2825,7 +2826,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_media)
self.assertEqual(len(channel.json_body["media"]), 15)
self.assertNotIn("next_token", channel.json_body)
@@ -2844,7 +2845,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 15)
self.assertEqual(len(channel.json_body["deleted_media"]), 15)
@@ -2861,7 +2862,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_media)
self.assertEqual(channel.json_body["next_token"], 15)
self.assertEqual(len(channel.json_body["media"]), 10)
@@ -2880,7 +2881,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], 10)
self.assertEqual(len(channel.json_body["deleted_media"]), 10)
@@ -2894,7 +2895,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
# invalid search order
@@ -2904,7 +2905,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.UNKNOWN, channel.json_body["errcode"])
# negative limit
@@ -2914,7 +2915,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
# negative from
@@ -2924,7 +2925,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
def test_next_token(self):
@@ -2947,7 +2948,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_media)
self.assertEqual(len(channel.json_body["media"]), number_media)
self.assertNotIn("next_token", channel.json_body)
@@ -2960,7 +2961,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_media)
self.assertEqual(len(channel.json_body["media"]), number_media)
self.assertNotIn("next_token", channel.json_body)
@@ -2973,7 +2974,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_media)
self.assertEqual(len(channel.json_body["media"]), 19)
self.assertEqual(channel.json_body["next_token"], 19)
@@ -2987,7 +2988,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], number_media)
self.assertEqual(len(channel.json_body["media"]), 1)
self.assertNotIn("next_token", channel.json_body)
@@ -3004,7 +3005,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(0, channel.json_body["total"])
self.assertEqual(0, len(channel.json_body["media"]))
@@ -3019,7 +3020,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(0, channel.json_body["total"])
self.assertEqual(0, len(channel.json_body["deleted_media"]))
@@ -3036,7 +3037,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(number_media, channel.json_body["total"])
self.assertEqual(number_media, len(channel.json_body["media"]))
self.assertNotIn("next_token", channel.json_body)
@@ -3062,7 +3063,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(number_media, channel.json_body["total"])
self.assertEqual(number_media, len(channel.json_body["deleted_media"]))
self.assertCountEqual(channel.json_body["deleted_media"], media_ids)
@@ -3207,7 +3208,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
# Upload some media into the room
response = self.helper.upload_media(
- upload_resource, image_data, user_token, filename, expect_code=200
+ upload_resource, image_data, user_token, filename, expect_code=HTTPStatus.OK
)
# Extract media ID from the response
@@ -3225,16 +3226,16 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
)
self.assertEqual(
- 200,
+ HTTPStatus.OK,
channel.code,
msg=(
- f"Expected to receive a 200 on accessing media: {server_and_media_id}"
+ f"Expected to receive a HTTPStatus.OK on accessing media: {server_and_media_id}"
),
)
return media_id
- def _check_fields(self, content: JsonDict):
+ def _check_fields(self, content: List[JsonDict]):
"""Checks that the expected user attributes are present in content
Args:
content: List that is checked for content
@@ -3274,7 +3275,7 @@ class UserMediaRestTestCase(unittest.HomeserverTestCase):
url,
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(channel.json_body["total"], len(expected_media_list))
returned_order = [row["media_id"] for row in channel.json_body["media"]]
@@ -3310,14 +3311,14 @@ class UserTokenRestTestCase(unittest.HomeserverTestCase):
channel = self.make_request(
"POST", self.url, b"{}", access_token=self.admin_user_tok
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
return channel.json_body["access_token"]
def test_no_auth(self):
"""Try to login as a user without authentication."""
channel = self.make_request("POST", self.url, b"{}")
- self.assertEqual(401, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.UNAUTHORIZED, channel.code, msg=channel.json_body)
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
def test_not_admin(self):
@@ -3326,7 +3327,7 @@ class UserTokenRestTestCase(unittest.HomeserverTestCase):
"POST", self.url, b"{}", access_token=self.other_user_tok
)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
def test_send_event(self):
"""Test that sending event as a user works."""
@@ -3351,7 +3352,7 @@ class UserTokenRestTestCase(unittest.HomeserverTestCase):
channel = self.make_request(
"GET", "devices", b"{}", access_token=self.other_user_tok
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# We should only see the one device (from the login in `prepare`)
self.assertEqual(len(channel.json_body["devices"]), 1)
@@ -3363,21 +3364,21 @@ class UserTokenRestTestCase(unittest.HomeserverTestCase):
# Test that we can successfully make a request
channel = self.make_request("GET", "devices", b"{}", access_token=puppet_token)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Logout with the puppet token
channel = self.make_request("POST", "logout", b"{}", access_token=puppet_token)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# The puppet token should no longer work
channel = self.make_request("GET", "devices", b"{}", access_token=puppet_token)
- self.assertEqual(401, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.UNAUTHORIZED, channel.code, msg=channel.json_body)
# .. but the real user's tokens should still work
channel = self.make_request(
"GET", "devices", b"{}", access_token=self.other_user_tok
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
def test_user_logout_all(self):
"""Tests that the target user calling `/logout/all` does *not* expire
@@ -3388,23 +3389,23 @@ class UserTokenRestTestCase(unittest.HomeserverTestCase):
# Test that we can successfully make a request
channel = self.make_request("GET", "devices", b"{}", access_token=puppet_token)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Logout all with the real user token
channel = self.make_request(
"POST", "logout/all", b"{}", access_token=self.other_user_tok
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# The puppet token should still work
channel = self.make_request("GET", "devices", b"{}", access_token=puppet_token)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# .. but the real user's tokens shouldn't
channel = self.make_request(
"GET", "devices", b"{}", access_token=self.other_user_tok
)
- self.assertEqual(401, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.UNAUTHORIZED, channel.code, msg=channel.json_body)
def test_admin_logout_all(self):
"""Tests that the admin user calling `/logout/all` does expire the
@@ -3415,23 +3416,23 @@ class UserTokenRestTestCase(unittest.HomeserverTestCase):
# Test that we can successfully make a request
channel = self.make_request("GET", "devices", b"{}", access_token=puppet_token)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# Logout all with the admin user token
channel = self.make_request(
"POST", "logout/all", b"{}", access_token=self.admin_user_tok
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
# The puppet token should no longer work
channel = self.make_request("GET", "devices", b"{}", access_token=puppet_token)
- self.assertEqual(401, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.UNAUTHORIZED, channel.code, msg=channel.json_body)
# .. but the real user's tokens should still work
channel = self.make_request(
"GET", "devices", b"{}", access_token=self.other_user_tok
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
@unittest.override_config(
{
@@ -3459,7 +3460,10 @@ class UserTokenRestTestCase(unittest.HomeserverTestCase):
# Now unaccept it and check that we can't send an event
self.get_success(self.store.user_set_consent_version(self.other_user, "0.0"))
self.helper.send_event(
- room_id, "com.example.test", tok=self.other_user_tok, expect_code=403
+ room_id,
+ "com.example.test",
+ tok=self.other_user_tok,
+ expect_code=HTTPStatus.FORBIDDEN,
)
# Login in as the user
@@ -3477,7 +3481,10 @@ class UserTokenRestTestCase(unittest.HomeserverTestCase):
# Trying to join as the other user should fail due to reaching MAU limit.
self.helper.join(
- room_id, user=self.other_user, tok=self.other_user_tok, expect_code=403
+ room_id,
+ user=self.other_user,
+ tok=self.other_user_tok,
+ expect_code=HTTPStatus.FORBIDDEN,
)
# Logging in as the other user and joining a room should work, even
@@ -3512,7 +3519,7 @@ class WhoisRestTestCase(unittest.HomeserverTestCase):
Try to get information of an user without authentication.
"""
channel = self.make_request("GET", self.url, b"{}")
- self.assertEqual(401, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.UNAUTHORIZED, channel.code, msg=channel.json_body)
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
def test_requester_is_not_admin(self):
@@ -3527,12 +3534,12 @@ class WhoisRestTestCase(unittest.HomeserverTestCase):
self.url,
access_token=other_user2_token,
)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
def test_user_is_not_local(self):
"""
- Tests that a lookup for a user that is not a local returns a 400
+ Tests that a lookup for a user that is not a local returns a HTTPStatus.BAD_REQUEST
"""
url = self.url_prefix % "@unknown_person:unknown_domain"
@@ -3541,7 +3548,7 @@ class WhoisRestTestCase(unittest.HomeserverTestCase):
url,
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual("Can only whois a local user", channel.json_body["error"])
def test_get_whois_admin(self):
@@ -3553,7 +3560,7 @@ class WhoisRestTestCase(unittest.HomeserverTestCase):
self.url,
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(self.other_user, channel.json_body["user_id"])
self.assertIn("devices", channel.json_body)
@@ -3568,7 +3575,7 @@ class WhoisRestTestCase(unittest.HomeserverTestCase):
self.url,
access_token=other_user_token,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(self.other_user, channel.json_body["user_id"])
self.assertIn("devices", channel.json_body)
@@ -3598,7 +3605,7 @@ class ShadowBanRestTestCase(unittest.HomeserverTestCase):
Try to get information of an user without authentication.
"""
channel = self.make_request(method, self.url)
- self.assertEqual(401, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.UNAUTHORIZED, channel.code, msg=channel.json_body)
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
@parameterized.expand(["POST", "DELETE"])
@@ -3609,18 +3616,18 @@ class ShadowBanRestTestCase(unittest.HomeserverTestCase):
other_user_token = self.login("user", "pass")
channel = self.make_request(method, self.url, access_token=other_user_token)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
@parameterized.expand(["POST", "DELETE"])
def test_user_is_not_local(self, method: str):
"""
- Tests that shadow-banning for a user that is not a local returns a 400
+ Tests that shadow-banning for a user that is not a local returns a HTTPStatus.BAD_REQUEST
"""
url = "/_synapse/admin/v1/whois/@unknown_person:unknown_domain"
channel = self.make_request(method, url, access_token=self.admin_user_tok)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
def test_success(self):
"""
@@ -3632,7 +3639,7 @@ class ShadowBanRestTestCase(unittest.HomeserverTestCase):
self.assertFalse(result.shadow_banned)
channel = self.make_request("POST", self.url, access_token=self.admin_user_tok)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual({}, channel.json_body)
# Ensure the user is shadow-banned (and the cache was cleared).
@@ -3643,7 +3650,7 @@ class ShadowBanRestTestCase(unittest.HomeserverTestCase):
channel = self.make_request(
"DELETE", self.url, access_token=self.admin_user_tok
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual({}, channel.json_body)
# Ensure the user is no longer shadow-banned (and the cache was cleared).
@@ -3677,7 +3684,7 @@ class RateLimitTestCase(unittest.HomeserverTestCase):
"""
channel = self.make_request(method, self.url, b"{}")
- self.assertEqual(401, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.UNAUTHORIZED, channel.code, msg=channel.json_body)
self.assertEqual(Codes.MISSING_TOKEN, channel.json_body["errcode"])
@parameterized.expand(["GET", "POST", "DELETE"])
@@ -3693,13 +3700,13 @@ class RateLimitTestCase(unittest.HomeserverTestCase):
access_token=other_user_token,
)
- self.assertEqual(403, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.FORBIDDEN, channel.code, msg=channel.json_body)
self.assertEqual(Codes.FORBIDDEN, channel.json_body["errcode"])
@parameterized.expand(["GET", "POST", "DELETE"])
def test_user_does_not_exist(self, method: str):
"""
- Tests that a lookup for a user that does not exist returns a 404
+ Tests that a lookup for a user that does not exist returns a HTTPStatus.NOT_FOUND
"""
url = "/_synapse/admin/v1/users/@unknown_person:test/override_ratelimit"
@@ -3709,7 +3716,7 @@ class RateLimitTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(404, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.NOT_FOUND, channel.code, msg=channel.json_body)
self.assertEqual(Codes.NOT_FOUND, channel.json_body["errcode"])
@parameterized.expand(
@@ -3721,7 +3728,7 @@ class RateLimitTestCase(unittest.HomeserverTestCase):
)
def test_user_is_not_local(self, method: str, error_msg: str):
"""
- Tests that a lookup for a user that is not a local returns a 400
+ Tests that a lookup for a user that is not a local returns a HTTPStatus.BAD_REQUEST
"""
url = (
"/_synapse/admin/v1/users/@unknown_person:unknown_domain/override_ratelimit"
@@ -3733,7 +3740,7 @@ class RateLimitTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(error_msg, channel.json_body["error"])
def test_invalid_parameter(self):
@@ -3748,7 +3755,7 @@ class RateLimitTestCase(unittest.HomeserverTestCase):
content={"messages_per_second": "string"},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
# messages_per_second is negative
@@ -3759,7 +3766,7 @@ class RateLimitTestCase(unittest.HomeserverTestCase):
content={"messages_per_second": -1},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
# burst_count is a string
@@ -3770,7 +3777,7 @@ class RateLimitTestCase(unittest.HomeserverTestCase):
content={"burst_count": "string"},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
# burst_count is negative
@@ -3781,7 +3788,7 @@ class RateLimitTestCase(unittest.HomeserverTestCase):
content={"burst_count": -1},
)
- self.assertEqual(400, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.BAD_REQUEST, channel.code, msg=channel.json_body)
self.assertEqual(Codes.INVALID_PARAM, channel.json_body["errcode"])
def test_return_zero_when_null(self):
@@ -3806,7 +3813,7 @@ class RateLimitTestCase(unittest.HomeserverTestCase):
self.url,
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(0, channel.json_body["messages_per_second"])
self.assertEqual(0, channel.json_body["burst_count"])
@@ -3820,7 +3827,7 @@ class RateLimitTestCase(unittest.HomeserverTestCase):
self.url,
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertNotIn("messages_per_second", channel.json_body)
self.assertNotIn("burst_count", channel.json_body)
@@ -3831,7 +3838,7 @@ class RateLimitTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"messages_per_second": 10, "burst_count": 11},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(10, channel.json_body["messages_per_second"])
self.assertEqual(11, channel.json_body["burst_count"])
@@ -3842,7 +3849,7 @@ class RateLimitTestCase(unittest.HomeserverTestCase):
access_token=self.admin_user_tok,
content={"messages_per_second": 20, "burst_count": 21},
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(20, channel.json_body["messages_per_second"])
self.assertEqual(21, channel.json_body["burst_count"])
@@ -3852,7 +3859,7 @@ class RateLimitTestCase(unittest.HomeserverTestCase):
self.url,
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertEqual(20, channel.json_body["messages_per_second"])
self.assertEqual(21, channel.json_body["burst_count"])
@@ -3862,7 +3869,7 @@ class RateLimitTestCase(unittest.HomeserverTestCase):
self.url,
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertNotIn("messages_per_second", channel.json_body)
self.assertNotIn("burst_count", channel.json_body)
@@ -3872,6 +3879,6 @@ class RateLimitTestCase(unittest.HomeserverTestCase):
self.url,
access_token=self.admin_user_tok,
)
- self.assertEqual(200, channel.code, msg=channel.json_body)
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertNotIn("messages_per_second", channel.json_body)
self.assertNotIn("burst_count", channel.json_body)
diff --git a/tests/rest/admin/test_username_available.py b/tests/rest/admin/test_username_available.py
index 4e1c49c28b..7978626e71 100644
--- a/tests/rest/admin/test_username_available.py
+++ b/tests/rest/admin/test_username_available.py
@@ -12,6 +12,8 @@
# See the License for the specific language governing permissions and
# limitations under the License.
+from http import HTTPStatus
+
import synapse.rest.admin
from synapse.api.errors import Codes, SynapseError
from synapse.rest.client import login
@@ -33,30 +35,38 @@ class UsernameAvailableTestCase(unittest.HomeserverTestCase):
async def check_username(username):
if username == "allowed":
return True
- raise SynapseError(400, "User ID already taken.", errcode=Codes.USER_IN_USE)
+ raise SynapseError(
+ HTTPStatus.BAD_REQUEST,
+ "User ID already taken.",
+ errcode=Codes.USER_IN_USE,
+ )
handler = self.hs.get_registration_handler()
handler.check_username = check_username
def test_username_available(self):
"""
- The endpoint should return a 200 response if the username does not exist
+ The endpoint should return a HTTPStatus.OK response if the username does not exist
"""
url = "%s?username=%s" % (self.url, "allowed")
channel = self.make_request("GET", url, None, self.admin_user_tok)
- self.assertEqual(200, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(HTTPStatus.OK, channel.code, msg=channel.json_body)
self.assertTrue(channel.json_body["available"])
def test_username_unavailable(self):
"""
- The endpoint should return a 200 response if the username does not exist
+ The endpoint should return a HTTPStatus.OK response if the username does not exist
"""
url = "%s?username=%s" % (self.url, "disallowed")
channel = self.make_request("GET", url, None, self.admin_user_tok)
- self.assertEqual(400, int(channel.result["code"]), msg=channel.result["body"])
+ self.assertEqual(
+ HTTPStatus.BAD_REQUEST,
+ channel.code,
+ msg=channel.json_body,
+ )
self.assertEqual(channel.json_body["errcode"], "M_USER_IN_USE")
self.assertEqual(channel.json_body["error"], "User ID already taken.")
diff --git a/tests/rest/client/test_auth.py b/tests/rest/client/test_auth.py
index d8a94f4c12..72bbc87b4a 100644
--- a/tests/rest/client/test_auth.py
+++ b/tests/rest/client/test_auth.py
@@ -520,10 +520,23 @@ class RefreshAuthTests(unittest.HomeserverTestCase):
"""
return self.make_request(
"POST",
- "/_matrix/client/unstable/org.matrix.msc2918.refresh_token/refresh",
+ "/_matrix/client/v1/refresh",
{"refresh_token": refresh_token},
)
+ def is_access_token_valid(self, access_token) -> bool:
+ """
+ Checks whether an access token is valid, returning whether it is or not.
+ """
+ code = self.make_request(
+ "GET", "/_matrix/client/v3/account/whoami", access_token=access_token
+ ).code
+
+ # Either 200 or 401 is what we get back; anything else is a bug.
+ assert code in {HTTPStatus.OK, HTTPStatus.UNAUTHORIZED}
+
+ return code == HTTPStatus.OK
+
def test_login_issue_refresh_token(self):
"""
A login response should include a refresh_token only if asked.
@@ -544,7 +557,7 @@ class RefreshAuthTests(unittest.HomeserverTestCase):
login_with_refresh = self.make_request(
"POST",
"/_matrix/client/r0/login",
- {"org.matrix.msc2918.refresh_token": True, **body},
+ {"refresh_token": True, **body},
)
self.assertEqual(login_with_refresh.code, 200, login_with_refresh.result)
self.assertIn("refresh_token", login_with_refresh.json_body)
@@ -575,7 +588,7 @@ class RefreshAuthTests(unittest.HomeserverTestCase):
"username": "test3",
"password": self.user_pass,
"auth": {"type": LoginType.DUMMY},
- "org.matrix.msc2918.refresh_token": True,
+ "refresh_token": True,
},
)
self.assertEqual(register_with_refresh.code, 200, register_with_refresh.result)
@@ -590,7 +603,7 @@ class RefreshAuthTests(unittest.HomeserverTestCase):
"type": "m.login.password",
"user": "test",
"password": self.user_pass,
- "org.matrix.msc2918.refresh_token": True,
+ "refresh_token": True,
}
login_response = self.make_request(
"POST",
@@ -601,7 +614,7 @@ class RefreshAuthTests(unittest.HomeserverTestCase):
refresh_response = self.make_request(
"POST",
- "/_matrix/client/unstable/org.matrix.msc2918.refresh_token/refresh",
+ "/_matrix/client/v1/refresh",
{"refresh_token": login_response.json_body["refresh_token"]},
)
self.assertEqual(refresh_response.code, 200, refresh_response.result)
@@ -628,7 +641,7 @@ class RefreshAuthTests(unittest.HomeserverTestCase):
"type": "m.login.password",
"user": "test",
"password": self.user_pass,
- "org.matrix.msc2918.refresh_token": True,
+ "refresh_token": True,
}
login_response = self.make_request(
"POST",
@@ -642,7 +655,7 @@ class RefreshAuthTests(unittest.HomeserverTestCase):
refresh_response = self.make_request(
"POST",
- "/_matrix/client/unstable/org.matrix.msc2918.refresh_token/refresh",
+ "/_matrix/client/v1/refresh",
{"refresh_token": login_response.json_body["refresh_token"]},
)
self.assertEqual(refresh_response.code, 200, refresh_response.result)
@@ -672,6 +685,69 @@ class RefreshAuthTests(unittest.HomeserverTestCase):
)
@override_config(
+ {
+ "refreshable_access_token_lifetime": "1m",
+ "nonrefreshable_access_token_lifetime": "10m",
+ }
+ )
+ def test_different_expiry_for_refreshable_and_nonrefreshable_access_tokens(self):
+ """
+ Tests that the expiry times for refreshable and non-refreshable access
+ tokens can be different.
+ """
+ body = {
+ "type": "m.login.password",
+ "user": "test",
+ "password": self.user_pass,
+ }
+ login_response1 = self.make_request(
+ "POST",
+ "/_matrix/client/r0/login",
+ {"refresh_token": True, **body},
+ )
+ self.assertEqual(login_response1.code, 200, login_response1.result)
+ self.assertApproximates(
+ login_response1.json_body["expires_in_ms"], 60 * 1000, 100
+ )
+ refreshable_access_token = login_response1.json_body["access_token"]
+
+ login_response2 = self.make_request(
+ "POST",
+ "/_matrix/client/r0/login",
+ body,
+ )
+ self.assertEqual(login_response2.code, 200, login_response2.result)
+ nonrefreshable_access_token = login_response2.json_body["access_token"]
+
+ # Advance 59 seconds in the future (just shy of 1 minute, the time of expiry)
+ self.reactor.advance(59.0)
+
+ # Both tokens should still be valid.
+ self.assertTrue(self.is_access_token_valid(refreshable_access_token))
+ self.assertTrue(self.is_access_token_valid(nonrefreshable_access_token))
+
+ # Advance to 61 s (just past 1 minute, the time of expiry)
+ self.reactor.advance(2.0)
+
+ # Only the non-refreshable token is still valid.
+ self.assertFalse(self.is_access_token_valid(refreshable_access_token))
+ self.assertTrue(self.is_access_token_valid(nonrefreshable_access_token))
+
+ # Advance to 599 s (just shy of 10 minutes, the time of expiry)
+ self.reactor.advance(599.0 - 61.0)
+
+ # It's still the case that only the non-refreshable token is still valid.
+ self.assertFalse(self.is_access_token_valid(refreshable_access_token))
+ self.assertTrue(self.is_access_token_valid(nonrefreshable_access_token))
+
+ # Advance to 601 s (just past 10 minutes, the time of expiry)
+ self.reactor.advance(2.0)
+
+ # Now neither token is valid.
+ self.assertFalse(self.is_access_token_valid(refreshable_access_token))
+ self.assertFalse(self.is_access_token_valid(nonrefreshable_access_token))
+
+ @override_config(
{"refreshable_access_token_lifetime": "1m", "refresh_token_lifetime": "2m"}
)
def test_refresh_token_expiry(self):
@@ -685,7 +761,7 @@ class RefreshAuthTests(unittest.HomeserverTestCase):
"type": "m.login.password",
"user": "test",
"password": self.user_pass,
- "org.matrix.msc2918.refresh_token": True,
+ "refresh_token": True,
}
login_response = self.make_request(
"POST",
@@ -735,7 +811,7 @@ class RefreshAuthTests(unittest.HomeserverTestCase):
"type": "m.login.password",
"user": "test",
"password": self.user_pass,
- "org.matrix.msc2918.refresh_token": True,
+ "refresh_token": True,
}
login_response = self.make_request(
"POST",
@@ -792,7 +868,7 @@ class RefreshAuthTests(unittest.HomeserverTestCase):
"type": "m.login.password",
"user": "test",
"password": self.user_pass,
- "org.matrix.msc2918.refresh_token": True,
+ "refresh_token": True,
}
login_response = self.make_request(
"POST",
@@ -804,7 +880,7 @@ class RefreshAuthTests(unittest.HomeserverTestCase):
# This first refresh should work properly
first_refresh_response = self.make_request(
"POST",
- "/_matrix/client/unstable/org.matrix.msc2918.refresh_token/refresh",
+ "/_matrix/client/v1/refresh",
{"refresh_token": login_response.json_body["refresh_token"]},
)
self.assertEqual(
@@ -814,7 +890,7 @@ class RefreshAuthTests(unittest.HomeserverTestCase):
# This one as well, since the token in the first one was never used
second_refresh_response = self.make_request(
"POST",
- "/_matrix/client/unstable/org.matrix.msc2918.refresh_token/refresh",
+ "/_matrix/client/v1/refresh",
{"refresh_token": login_response.json_body["refresh_token"]},
)
self.assertEqual(
@@ -824,7 +900,7 @@ class RefreshAuthTests(unittest.HomeserverTestCase):
# This one should not, since the token from the first refresh is not valid anymore
third_refresh_response = self.make_request(
"POST",
- "/_matrix/client/unstable/org.matrix.msc2918.refresh_token/refresh",
+ "/_matrix/client/v1/refresh",
{"refresh_token": first_refresh_response.json_body["refresh_token"]},
)
self.assertEqual(
@@ -852,7 +928,7 @@ class RefreshAuthTests(unittest.HomeserverTestCase):
# Now that the access token from the last valid refresh was used once, refreshing with the N-1 token should fail
fourth_refresh_response = self.make_request(
"POST",
- "/_matrix/client/unstable/org.matrix.msc2918.refresh_token/refresh",
+ "/_matrix/client/v1/refresh",
{"refresh_token": login_response.json_body["refresh_token"]},
)
self.assertEqual(
@@ -862,7 +938,7 @@ class RefreshAuthTests(unittest.HomeserverTestCase):
# But refreshing from the last valid refresh token still works
fifth_refresh_response = self.make_request(
"POST",
- "/_matrix/client/unstable/org.matrix.msc2918.refresh_token/refresh",
+ "/_matrix/client/v1/refresh",
{"refresh_token": second_refresh_response.json_body["refresh_token"]},
)
self.assertEqual(
diff --git a/tests/rest/client/test_relations.py b/tests/rest/client/test_relations.py
index eb10d43217..397c12c2a6 100644
--- a/tests/rest/client/test_relations.py
+++ b/tests/rest/client/test_relations.py
@@ -19,7 +19,7 @@ from typing import Dict, List, Optional, Tuple
from synapse.api.constants import EventTypes, RelationTypes
from synapse.rest import admin
-from synapse.rest.client import login, register, relations, room
+from synapse.rest.client import login, register, relations, room, sync
from tests import unittest
from tests.server import FakeChannel
@@ -29,6 +29,7 @@ class RelationsTestCase(unittest.HomeserverTestCase):
servlets = [
relations.register_servlets,
room.register_servlets,
+ sync.register_servlets,
login.register_servlets,
register.register_servlets,
admin.register_servlets_for_client_rest_resource,
@@ -454,11 +455,9 @@ class RelationsTestCase(unittest.HomeserverTestCase):
self.assertEquals(400, channel.code, channel.json_body)
@unittest.override_config({"experimental_features": {"msc3440_enabled": True}})
- def test_aggregation_get_event(self):
- """Test that annotations, references, and threads get correctly bundled when
- getting the parent event.
- """
-
+ def test_bundled_aggregations(self):
+ """Test that annotations, references, and threads get correctly bundled."""
+ # Setup by sending a variety of relations.
channel = self._send_relation(RelationTypes.ANNOTATION, "m.reaction", "a")
self.assertEquals(200, channel.code, channel.json_body)
@@ -485,43 +484,169 @@ class RelationsTestCase(unittest.HomeserverTestCase):
self.assertEquals(200, channel.code, channel.json_body)
thread_2 = channel.json_body["event_id"]
+ def assert_bundle(actual):
+ """Assert the expected values of the bundled aggregations."""
+
+ # Ensure the fields are as expected.
+ self.assertCountEqual(
+ actual.keys(),
+ (
+ RelationTypes.ANNOTATION,
+ RelationTypes.REFERENCE,
+ RelationTypes.THREAD,
+ ),
+ )
+
+ # Check the values of each field.
+ self.assertEquals(
+ {
+ "chunk": [
+ {"type": "m.reaction", "key": "a", "count": 2},
+ {"type": "m.reaction", "key": "b", "count": 1},
+ ]
+ },
+ actual[RelationTypes.ANNOTATION],
+ )
+
+ self.assertEquals(
+ {"chunk": [{"event_id": reply_1}, {"event_id": reply_2}]},
+ actual[RelationTypes.REFERENCE],
+ )
+
+ self.assertEquals(
+ 2,
+ actual[RelationTypes.THREAD].get("count"),
+ )
+ # The latest thread event has some fields that don't matter.
+ self.assert_dict(
+ {
+ "content": {
+ "m.relates_to": {
+ "event_id": self.parent_id,
+ "rel_type": RelationTypes.THREAD,
+ }
+ },
+ "event_id": thread_2,
+ "room_id": self.room,
+ "sender": self.user_id,
+ "type": "m.room.test",
+ "user_id": self.user_id,
+ },
+ actual[RelationTypes.THREAD].get("latest_event"),
+ )
+
+ def _find_and_assert_event(events):
+ """
+ Find the parent event in a chunk of events and assert that it has the proper bundled aggregations.
+ """
+ for event in events:
+ if event["event_id"] == self.parent_id:
+ break
+ else:
+ raise AssertionError(f"Event {self.parent_id} not found in chunk")
+ assert_bundle(event["unsigned"].get("m.relations"))
+
+ # Request the event directly.
channel = self.make_request(
"GET",
- "/rooms/%s/event/%s" % (self.room, self.parent_id),
+ f"/rooms/{self.room}/event/{self.parent_id}",
access_token=self.user_token,
)
self.assertEquals(200, channel.code, channel.json_body)
+ assert_bundle(channel.json_body["unsigned"].get("m.relations"))
+ # Request the room messages.
+ channel = self.make_request(
+ "GET",
+ f"/rooms/{self.room}/messages?dir=b",
+ access_token=self.user_token,
+ )
+ self.assertEquals(200, channel.code, channel.json_body)
+ _find_and_assert_event(channel.json_body["chunk"])
+
+ # Request the room context.
+ channel = self.make_request(
+ "GET",
+ f"/rooms/{self.room}/context/{self.parent_id}",
+ access_token=self.user_token,
+ )
+ self.assertEquals(200, channel.code, channel.json_body)
+ assert_bundle(channel.json_body["event"]["unsigned"].get("m.relations"))
+
+ # Request sync.
+ channel = self.make_request("GET", "/sync", access_token=self.user_token)
+ self.assertEquals(200, channel.code, channel.json_body)
+ room_timeline = channel.json_body["rooms"]["join"][self.room]["timeline"]
+ self.assertTrue(room_timeline["limited"])
+ _find_and_assert_event(room_timeline["events"])
+
+ # Note that /relations is tested separately in test_aggregation_get_event_for_thread
+ # since it needs different data configured.
+
+ def test_aggregation_get_event_for_annotation(self):
+ """Test that annotations do not get bundled aggregations included
+ when directly requested.
+ """
+ channel = self._send_relation(RelationTypes.ANNOTATION, "m.reaction", "a")
+ self.assertEquals(200, channel.code, channel.json_body)
+ annotation_id = channel.json_body["event_id"]
+
+ # Annotate the annotation.
+ channel = self._send_relation(
+ RelationTypes.ANNOTATION, "m.reaction", "a", parent_id=annotation_id
+ )
+ self.assertEquals(200, channel.code, channel.json_body)
+
+ channel = self.make_request(
+ "GET",
+ f"/rooms/{self.room}/event/{annotation_id}",
+ access_token=self.user_token,
+ )
+ self.assertEquals(200, channel.code, channel.json_body)
+ self.assertIsNone(channel.json_body["unsigned"].get("m.relations"))
+
+ def test_aggregation_get_event_for_thread(self):
+ """Test that threads get bundled aggregations included when directly requested."""
+ channel = self._send_relation(RelationTypes.THREAD, "m.room.test")
+ self.assertEquals(200, channel.code, channel.json_body)
+ thread_id = channel.json_body["event_id"]
+
+ # Annotate the annotation.
+ channel = self._send_relation(
+ RelationTypes.ANNOTATION, "m.reaction", "a", parent_id=thread_id
+ )
+ self.assertEquals(200, channel.code, channel.json_body)
+
+ channel = self.make_request(
+ "GET",
+ f"/rooms/{self.room}/event/{thread_id}",
+ access_token=self.user_token,
+ )
+ self.assertEquals(200, channel.code, channel.json_body)
self.assertEquals(
channel.json_body["unsigned"].get("m.relations"),
{
RelationTypes.ANNOTATION: {
- "chunk": [
- {"type": "m.reaction", "key": "a", "count": 2},
- {"type": "m.reaction", "key": "b", "count": 1},
- ]
- },
- RelationTypes.REFERENCE: {
- "chunk": [{"event_id": reply_1}, {"event_id": reply_2}]
+ "chunk": [{"count": 1, "key": "a", "type": "m.reaction"}]
},
- RelationTypes.THREAD: {
- "count": 2,
- "latest_event": {
- "age": 100,
- "content": {
- "m.relates_to": {
- "event_id": self.parent_id,
- "rel_type": RelationTypes.THREAD,
- }
- },
- "event_id": thread_2,
- "origin_server_ts": 1600,
- "room_id": self.room,
- "sender": self.user_id,
- "type": "m.room.test",
- "unsigned": {"age": 100},
- "user_id": self.user_id,
- },
+ },
+ )
+
+ # It should also be included when the entire thread is requested.
+ channel = self.make_request(
+ "GET",
+ f"/_matrix/client/unstable/rooms/{self.room}/relations/{self.parent_id}?limit=1",
+ access_token=self.user_token,
+ )
+ self.assertEquals(200, channel.code, channel.json_body)
+ self.assertEqual(len(channel.json_body["chunk"]), 1)
+
+ thread_message = channel.json_body["chunk"][0]
+ self.assertEquals(
+ thread_message["unsigned"].get("m.relations"),
+ {
+ RelationTypes.ANNOTATION: {
+ "chunk": [{"count": 1, "key": "a", "type": "m.reaction"}]
},
},
)
@@ -672,6 +797,56 @@ class RelationsTestCase(unittest.HomeserverTestCase):
{"event_id": edit_event_id, "sender": self.user_id}, m_replace_dict
)
+ def test_edit_edit(self):
+ """Test that an edit cannot be edited."""
+ new_body = {"msgtype": "m.text", "body": "Initial edit"}
+ channel = self._send_relation(
+ RelationTypes.REPLACE,
+ "m.room.message",
+ content={
+ "msgtype": "m.text",
+ "body": "Wibble",
+ "m.new_content": new_body,
+ },
+ )
+ self.assertEquals(200, channel.code, channel.json_body)
+ edit_event_id = channel.json_body["event_id"]
+
+ # Edit the edit event.
+ channel = self._send_relation(
+ RelationTypes.REPLACE,
+ "m.room.message",
+ content={
+ "msgtype": "m.text",
+ "body": "foo",
+ "m.new_content": {"msgtype": "m.text", "body": "Ignored edit"},
+ },
+ parent_id=edit_event_id,
+ )
+ self.assertEquals(200, channel.code, channel.json_body)
+
+ # Request the original event.
+ channel = self.make_request(
+ "GET",
+ "/rooms/%s/event/%s" % (self.room, self.parent_id),
+ access_token=self.user_token,
+ )
+ self.assertEquals(200, channel.code, channel.json_body)
+ # The edit to the edit should be ignored.
+ self.assertEquals(channel.json_body["content"], new_body)
+
+ # The relations information should not include the edit to the edit.
+ relations_dict = channel.json_body["unsigned"].get("m.relations")
+ self.assertIn(RelationTypes.REPLACE, relations_dict)
+
+ m_replace_dict = relations_dict[RelationTypes.REPLACE]
+ for key in ["event_id", "sender", "origin_server_ts"]:
+ self.assertIn(key, m_replace_dict)
+
+ self.assert_dict(
+ {"event_id": edit_event_id, "sender": self.user_id}, m_replace_dict
+ )
+
def test_relations_redaction_redacts_edits(self):
"""Test that edits of an event are redacted when the original event
is redacted.
diff --git a/tests/rest/media/v1/test_filepath.py b/tests/rest/media/v1/test_filepath.py
index 8fe94f7d85..913bc530aa 100644
--- a/tests/rest/media/v1/test_filepath.py
+++ b/tests/rest/media/v1/test_filepath.py
@@ -12,9 +12,10 @@
# See the License for the specific language governing permissions and
# limitations under the License.
import inspect
+import os
from typing import Iterable
-from synapse.rest.media.v1.filepath import MediaFilePaths
+from synapse.rest.media.v1.filepath import MediaFilePaths, _wrap_with_jail_check
from tests import unittest
@@ -486,3 +487,109 @@ class MediaFilePathsTestCase(unittest.TestCase):
f"{value!r} unexpectedly passed validation: "
f"{method} returned {path_or_list!r}"
)
+
+
+class MediaFilePathsJailTestCase(unittest.TestCase):
+ def _check_relative_path(self, filepaths: MediaFilePaths, path: str) -> None:
+ """Passes a relative path through the jail check.
+
+ Args:
+ filepaths: The `MediaFilePaths` instance.
+ path: A path relative to the media store directory.
+
+ Raises:
+ ValueError: If the jail check fails.
+ """
+
+ @_wrap_with_jail_check(relative=True)
+ def _make_relative_path(self: MediaFilePaths, path: str) -> str:
+ return path
+
+ _make_relative_path(filepaths, path)
+
+ def _check_absolute_path(self, filepaths: MediaFilePaths, path: str) -> None:
+ """Passes an absolute path through the jail check.
+
+ Args:
+ filepaths: The `MediaFilePaths` instance.
+ path: A path relative to the media store directory.
+
+ Raises:
+ ValueError: If the jail check fails.
+ """
+
+ @_wrap_with_jail_check(relative=False)
+ def _make_absolute_path(self: MediaFilePaths, path: str) -> str:
+ return os.path.join(self.base_path, path)
+
+ _make_absolute_path(filepaths, path)
+
+ def test_traversal_inside(self) -> None:
+ """Test the jail check for paths that stay within the media directory."""
+ # Despite the `../`s, these paths still lie within the media directory and it's
+ # expected for the jail check to allow them through.
+ # These paths ought to trip the other checks in place and should never be
+ # returned.
+ filepaths = MediaFilePaths("/media_store")
+ path = "url_cache/2020-01-02/../../GerZNDnDZVjsOtar"
+ self._check_relative_path(filepaths, path)
+ self._check_absolute_path(filepaths, path)
+
+ def test_traversal_outside(self) -> None:
+ """Test that the jail check fails for paths that escape the media directory."""
+ filepaths = MediaFilePaths("/media_store")
+ path = "url_cache/2020-01-02/../../../GerZNDnDZVjsOtar"
+ with self.assertRaises(ValueError):
+ self._check_relative_path(filepaths, path)
+ with self.assertRaises(ValueError):
+ self._check_absolute_path(filepaths, path)
+
+ def test_traversal_reentry(self) -> None:
+ """Test the jail check for paths that exit and re-enter the media directory."""
+ # These paths lie outside the media directory if it is a symlink, and inside
+ # otherwise. Ideally the check should fail, but this proves difficult.
+ # This test documents the behaviour for this edge case.
+ # These paths ought to trip the other checks in place and should never be
+ # returned.
+ filepaths = MediaFilePaths("/media_store")
+ path = "url_cache/2020-01-02/../../../media_store/GerZNDnDZVjsOtar"
+ self._check_relative_path(filepaths, path)
+ self._check_absolute_path(filepaths, path)
+
+ def test_symlink(self) -> None:
+ """Test that a symlink does not cause the jail check to fail."""
+ media_store_path = self.mktemp()
+
+ # symlink the media store directory
+ os.symlink("/mnt/synapse/media_store", media_store_path)
+
+ # Test that relative and absolute paths don't trip the check
+ # NB: `media_store_path` is a relative path
+ filepaths = MediaFilePaths(media_store_path)
+ self._check_relative_path(filepaths, "url_cache/2020-01-02/GerZNDnDZVjsOtar")
+ self._check_absolute_path(filepaths, "url_cache/2020-01-02/GerZNDnDZVjsOtar")
+
+ filepaths = MediaFilePaths(os.path.abspath(media_store_path))
+ self._check_relative_path(filepaths, "url_cache/2020-01-02/GerZNDnDZVjsOtar")
+ self._check_absolute_path(filepaths, "url_cache/2020-01-02/GerZNDnDZVjsOtar")
+
+ def test_symlink_subdirectory(self) -> None:
+ """Test that a symlinked subdirectory does not cause the jail check to fail."""
+ media_store_path = self.mktemp()
+ os.mkdir(media_store_path)
+
+ # symlink `url_cache/`
+ os.symlink(
+ "/mnt/synapse/media_store_url_cache",
+ os.path.join(media_store_path, "url_cache"),
+ )
+
+ # Test that relative and absolute paths don't trip the check
+ # NB: `media_store_path` is a relative path
+ filepaths = MediaFilePaths(media_store_path)
+ self._check_relative_path(filepaths, "url_cache/2020-01-02/GerZNDnDZVjsOtar")
+ self._check_absolute_path(filepaths, "url_cache/2020-01-02/GerZNDnDZVjsOtar")
+
+ filepaths = MediaFilePaths(os.path.abspath(media_store_path))
+ self._check_relative_path(filepaths, "url_cache/2020-01-02/GerZNDnDZVjsOtar")
+ self._check_absolute_path(filepaths, "url_cache/2020-01-02/GerZNDnDZVjsOtar")
diff --git a/tests/storage/test_appservice.py b/tests/storage/test_appservice.py
index f26d5acf9c..329490caad 100644
--- a/tests/storage/test_appservice.py
+++ b/tests/storage/test_appservice.py
@@ -14,35 +14,37 @@
import json
import os
import tempfile
+from typing import List, Optional, cast
from unittest.mock import Mock
import yaml
from twisted.internet import defer
+from twisted.test.proto_helpers import MemoryReactor
from synapse.appservice import ApplicationService, ApplicationServiceState
from synapse.config._base import ConfigError
+from synapse.events import EventBase
+from synapse.server import HomeServer
from synapse.storage.database import DatabasePool, make_conn
from synapse.storage.databases.main.appservice import (
ApplicationServiceStore,
ApplicationServiceTransactionStore,
)
+from synapse.util import Clock
from tests import unittest
from tests.test_utils import make_awaitable
-from tests.utils import setup_test_homeserver
-class ApplicationServiceStoreTestCase(unittest.TestCase):
- @defer.inlineCallbacks
+class ApplicationServiceStoreTestCase(unittest.HomeserverTestCase):
def setUp(self):
- self.as_yaml_files = []
- hs = yield setup_test_homeserver(
- self.addCleanup, federation_sender=Mock(), federation_client=Mock()
- )
+ super(ApplicationServiceStoreTestCase, self).setUp()
+
+ self.as_yaml_files: List[str] = []
- hs.config.appservice.app_service_config_files = self.as_yaml_files
- hs.config.caches.event_cache_size = 1
+ self.hs.config.appservice.app_service_config_files = self.as_yaml_files
+ self.hs.config.caches.event_cache_size = 1
self.as_token = "token1"
self.as_url = "some_url"
@@ -53,12 +55,14 @@ class ApplicationServiceStoreTestCase(unittest.TestCase):
self._add_appservice("token2", "as2", "some_url", "some_hs_token", "bob")
self._add_appservice("token3", "as3", "some_url", "some_hs_token", "bob")
# must be done after inserts
- database = hs.get_datastores().databases[0]
+ database = self.hs.get_datastores().databases[0]
self.store = ApplicationServiceStore(
- database, make_conn(database._database_config, database.engine, "test"), hs
+ database,
+ make_conn(database._database_config, database.engine, "test"),
+ self.hs,
)
- def tearDown(self):
+ def tearDown(self) -> None:
# TODO: suboptimal that we need to create files for tests!
for f in self.as_yaml_files:
try:
@@ -66,7 +70,9 @@ class ApplicationServiceStoreTestCase(unittest.TestCase):
except Exception:
pass
- def _add_appservice(self, as_token, id, url, hs_token, sender):
+ super(ApplicationServiceStoreTestCase, self).tearDown()
+
+ def _add_appservice(self, as_token, id, url, hs_token, sender) -> None:
as_yaml = {
"url": url,
"as_token": as_token,
@@ -80,12 +86,13 @@ class ApplicationServiceStoreTestCase(unittest.TestCase):
outfile.write(yaml.dump(as_yaml))
self.as_yaml_files.append(as_token)
- def test_retrieve_unknown_service_token(self):
+ def test_retrieve_unknown_service_token(self) -> None:
service = self.store.get_app_service_by_token("invalid_token")
self.assertEquals(service, None)
- def test_retrieval_of_service(self):
+ def test_retrieval_of_service(self) -> None:
stored_service = self.store.get_app_service_by_token(self.as_token)
+ assert stored_service is not None
self.assertEquals(stored_service.token, self.as_token)
self.assertEquals(stored_service.id, self.as_id)
self.assertEquals(stored_service.url, self.as_url)
@@ -93,22 +100,18 @@ class ApplicationServiceStoreTestCase(unittest.TestCase):
self.assertEquals(stored_service.namespaces[ApplicationService.NS_ROOMS], [])
self.assertEquals(stored_service.namespaces[ApplicationService.NS_USERS], [])
- def test_retrieval_of_all_services(self):
+ def test_retrieval_of_all_services(self) -> None:
services = self.store.get_app_services()
self.assertEquals(len(services), 3)
-class ApplicationServiceTransactionStoreTestCase(unittest.TestCase):
- @defer.inlineCallbacks
- def setUp(self):
- self.as_yaml_files = []
-
- hs = yield setup_test_homeserver(
- self.addCleanup, federation_sender=Mock(), federation_client=Mock()
- )
+class ApplicationServiceTransactionStoreTestCase(unittest.HomeserverTestCase):
+ def setUp(self) -> None:
+ super(ApplicationServiceTransactionStoreTestCase, self).setUp()
+ self.as_yaml_files: List[str] = []
- hs.config.appservice.app_service_config_files = self.as_yaml_files
- hs.config.caches.event_cache_size = 1
+ self.hs.config.appservice.app_service_config_files = self.as_yaml_files
+ self.hs.config.caches.event_cache_size = 1
self.as_list = [
{"token": "token1", "url": "https://matrix-as.org", "id": "id_1"},
@@ -117,21 +120,21 @@ class ApplicationServiceTransactionStoreTestCase(unittest.TestCase):
{"token": "gamma_tok", "url": "https://gamma.com", "id": "id_gamma"},
]
for s in self.as_list:
- yield self._add_service(s["url"], s["token"], s["id"])
+ self._add_service(s["url"], s["token"], s["id"])
self.as_yaml_files = []
# We assume there is only one database in these tests
- database = hs.get_datastores().databases[0]
+ database = self.hs.get_datastores().databases[0]
self.db_pool = database._db_pool
self.engine = database.engine
- db_config = hs.config.database.get_single_database()
+ db_config = self.hs.config.database.get_single_database()
self.store = TestTransactionStore(
- database, make_conn(db_config, self.engine, "test"), hs
+ database, make_conn(db_config, self.engine, "test"), self.hs
)
- def _add_service(self, url, as_token, id):
+ def _add_service(self, url, as_token, id) -> None:
as_yaml = {
"url": url,
"as_token": as_token,
@@ -145,13 +148,15 @@ class ApplicationServiceTransactionStoreTestCase(unittest.TestCase):
outfile.write(yaml.dump(as_yaml))
self.as_yaml_files.append(as_token)
- def _set_state(self, id, state, txn=None):
+ def _set_state(
+ self, id: str, state: ApplicationServiceState, txn: Optional[int] = None
+ ):
return self.db_pool.runOperation(
self.engine.convert_param_style(
"INSERT INTO application_services_state(as_id, state, last_txn) "
"VALUES(?,?,?)"
),
- (id, state, txn),
+ (id, state.value, txn),
)
def _insert_txn(self, as_id, txn_id, events):
@@ -169,234 +174,277 @@ class ApplicationServiceTransactionStoreTestCase(unittest.TestCase):
"INSERT INTO application_services_state(as_id, last_txn, state) "
"VALUES(?,?,?)"
),
- (as_id, txn_id, ApplicationServiceState.UP),
+ (as_id, txn_id, ApplicationServiceState.UP.value),
)
- @defer.inlineCallbacks
- def test_get_appservice_state_none(self):
+ def test_get_appservice_state_none(
+ self,
+ ) -> None:
service = Mock(id="999")
- state = yield defer.ensureDeferred(self.store.get_appservice_state(service))
+ state = self.get_success(self.store.get_appservice_state(service))
self.assertEquals(None, state)
- @defer.inlineCallbacks
- def test_get_appservice_state_up(self):
- yield self._set_state(self.as_list[0]["id"], ApplicationServiceState.UP)
+ def test_get_appservice_state_up(
+ self,
+ ) -> None:
+ self.get_success(
+ self._set_state(self.as_list[0]["id"], ApplicationServiceState.UP)
+ )
service = Mock(id=self.as_list[0]["id"])
- state = yield defer.ensureDeferred(self.store.get_appservice_state(service))
+ state = self.get_success(
+ defer.ensureDeferred(self.store.get_appservice_state(service))
+ )
self.assertEquals(ApplicationServiceState.UP, state)
- @defer.inlineCallbacks
- def test_get_appservice_state_down(self):
- yield self._set_state(self.as_list[0]["id"], ApplicationServiceState.UP)
- yield self._set_state(self.as_list[1]["id"], ApplicationServiceState.DOWN)
- yield self._set_state(self.as_list[2]["id"], ApplicationServiceState.DOWN)
+ def test_get_appservice_state_down(
+ self,
+ ) -> None:
+ self.get_success(
+ self._set_state(self.as_list[0]["id"], ApplicationServiceState.UP)
+ )
+ self.get_success(
+ self._set_state(self.as_list[1]["id"], ApplicationServiceState.DOWN)
+ )
+ self.get_success(
+ self._set_state(self.as_list[2]["id"], ApplicationServiceState.DOWN)
+ )
service = Mock(id=self.as_list[1]["id"])
- state = yield defer.ensureDeferred(self.store.get_appservice_state(service))
+ state = self.get_success(self.store.get_appservice_state(service))
self.assertEquals(ApplicationServiceState.DOWN, state)
- @defer.inlineCallbacks
- def test_get_appservices_by_state_none(self):
- services = yield defer.ensureDeferred(
+ def test_get_appservices_by_state_none(
+ self,
+ ) -> None:
+ services = self.get_success(
self.store.get_appservices_by_state(ApplicationServiceState.DOWN)
)
self.assertEquals(0, len(services))
- @defer.inlineCallbacks
- def test_set_appservices_state_down(self):
+ def test_set_appservices_state_down(
+ self,
+ ) -> None:
service = Mock(id=self.as_list[1]["id"])
- yield defer.ensureDeferred(
+ self.get_success(
self.store.set_appservice_state(service, ApplicationServiceState.DOWN)
)
- rows = yield self.db_pool.runQuery(
- self.engine.convert_param_style(
- "SELECT as_id FROM application_services_state WHERE state=?"
- ),
- (ApplicationServiceState.DOWN,),
+ rows = self.get_success(
+ self.db_pool.runQuery(
+ self.engine.convert_param_style(
+ "SELECT as_id FROM application_services_state WHERE state=?"
+ ),
+ (ApplicationServiceState.DOWN.value,),
+ )
)
self.assertEquals(service.id, rows[0][0])
- @defer.inlineCallbacks
- def test_set_appservices_state_multiple_up(self):
+ def test_set_appservices_state_multiple_up(
+ self,
+ ) -> None:
service = Mock(id=self.as_list[1]["id"])
- yield defer.ensureDeferred(
+ self.get_success(
self.store.set_appservice_state(service, ApplicationServiceState.UP)
)
- yield defer.ensureDeferred(
+ self.get_success(
self.store.set_appservice_state(service, ApplicationServiceState.DOWN)
)
- yield defer.ensureDeferred(
+ self.get_success(
self.store.set_appservice_state(service, ApplicationServiceState.UP)
)
- rows = yield self.db_pool.runQuery(
- self.engine.convert_param_style(
- "SELECT as_id FROM application_services_state WHERE state=?"
- ),
- (ApplicationServiceState.UP,),
+ rows = self.get_success(
+ self.db_pool.runQuery(
+ self.engine.convert_param_style(
+ "SELECT as_id FROM application_services_state WHERE state=?"
+ ),
+ (ApplicationServiceState.UP.value,),
+ )
)
self.assertEquals(service.id, rows[0][0])
- @defer.inlineCallbacks
- def test_create_appservice_txn_first(self):
+ def test_create_appservice_txn_first(
+ self,
+ ) -> None:
service = Mock(id=self.as_list[0]["id"])
- events = [Mock(event_id="e1"), Mock(event_id="e2")]
- txn = yield defer.ensureDeferred(
- self.store.create_appservice_txn(service, events, [])
+ events = cast(List[EventBase], [Mock(event_id="e1"), Mock(event_id="e2")])
+ txn = self.get_success(
+ defer.ensureDeferred(self.store.create_appservice_txn(service, events, []))
)
self.assertEquals(txn.id, 1)
self.assertEquals(txn.events, events)
self.assertEquals(txn.service, service)
- @defer.inlineCallbacks
- def test_create_appservice_txn_older_last_txn(self):
+ def test_create_appservice_txn_older_last_txn(
+ self,
+ ) -> None:
service = Mock(id=self.as_list[0]["id"])
- events = [Mock(event_id="e1"), Mock(event_id="e2")]
- yield self._set_last_txn(service.id, 9643) # AS is falling behind
- yield self._insert_txn(service.id, 9644, events)
- yield self._insert_txn(service.id, 9645, events)
- txn = yield defer.ensureDeferred(
- self.store.create_appservice_txn(service, events, [])
- )
+ events = cast(List[EventBase], [Mock(event_id="e1"), Mock(event_id="e2")])
+ self.get_success(self._set_last_txn(service.id, 9643)) # AS is falling behind
+ self.get_success(self._insert_txn(service.id, 9644, events))
+ self.get_success(self._insert_txn(service.id, 9645, events))
+ txn = self.get_success(self.store.create_appservice_txn(service, events, []))
self.assertEquals(txn.id, 9646)
self.assertEquals(txn.events, events)
self.assertEquals(txn.service, service)
- @defer.inlineCallbacks
- def test_create_appservice_txn_up_to_date_last_txn(self):
+ def test_create_appservice_txn_up_to_date_last_txn(
+ self,
+ ) -> None:
service = Mock(id=self.as_list[0]["id"])
- events = [Mock(event_id="e1"), Mock(event_id="e2")]
- yield self._set_last_txn(service.id, 9643)
- txn = yield defer.ensureDeferred(
- self.store.create_appservice_txn(service, events, [])
- )
+ events = cast(List[EventBase], [Mock(event_id="e1"), Mock(event_id="e2")])
+ self.get_success(self._set_last_txn(service.id, 9643))
+ txn = self.get_success(self.store.create_appservice_txn(service, events, []))
self.assertEquals(txn.id, 9644)
self.assertEquals(txn.events, events)
self.assertEquals(txn.service, service)
- @defer.inlineCallbacks
- def test_create_appservice_txn_up_fuzzing(self):
+ def test_create_appservice_txn_up_fuzzing(
+ self,
+ ) -> None:
service = Mock(id=self.as_list[0]["id"])
- events = [Mock(event_id="e1"), Mock(event_id="e2")]
- yield self._set_last_txn(service.id, 9643)
+ events = cast(List[EventBase], [Mock(event_id="e1"), Mock(event_id="e2")])
+ self.get_success(self._set_last_txn(service.id, 9643))
# dump in rows with higher IDs to make sure the queries aren't wrong.
- yield self._set_last_txn(self.as_list[1]["id"], 119643)
- yield self._set_last_txn(self.as_list[2]["id"], 9)
- yield self._set_last_txn(self.as_list[3]["id"], 9643)
- yield self._insert_txn(self.as_list[1]["id"], 119644, events)
- yield self._insert_txn(self.as_list[1]["id"], 119645, events)
- yield self._insert_txn(self.as_list[1]["id"], 119646, events)
- yield self._insert_txn(self.as_list[2]["id"], 10, events)
- yield self._insert_txn(self.as_list[3]["id"], 9643, events)
-
- txn = yield defer.ensureDeferred(
- self.store.create_appservice_txn(service, events, [])
- )
+ self.get_success(self._set_last_txn(self.as_list[1]["id"], 119643))
+ self.get_success(self._set_last_txn(self.as_list[2]["id"], 9))
+ self.get_success(self._set_last_txn(self.as_list[3]["id"], 9643))
+ self.get_success(self._insert_txn(self.as_list[1]["id"], 119644, events))
+ self.get_success(self._insert_txn(self.as_list[1]["id"], 119645, events))
+ self.get_success(self._insert_txn(self.as_list[1]["id"], 119646, events))
+ self.get_success(self._insert_txn(self.as_list[2]["id"], 10, events))
+ self.get_success(self._insert_txn(self.as_list[3]["id"], 9643, events))
+
+ txn = self.get_success(self.store.create_appservice_txn(service, events, []))
self.assertEquals(txn.id, 9644)
self.assertEquals(txn.events, events)
self.assertEquals(txn.service, service)
- @defer.inlineCallbacks
- def test_complete_appservice_txn_first_txn(self):
+ def test_complete_appservice_txn_first_txn(
+ self,
+ ) -> None:
service = Mock(id=self.as_list[0]["id"])
events = [Mock(event_id="e1"), Mock(event_id="e2")]
txn_id = 1
- yield self._insert_txn(service.id, txn_id, events)
- yield defer.ensureDeferred(
+ self.get_success(self._insert_txn(service.id, txn_id, events))
+ self.get_success(
self.store.complete_appservice_txn(txn_id=txn_id, service=service)
)
- res = yield self.db_pool.runQuery(
- self.engine.convert_param_style(
- "SELECT last_txn FROM application_services_state WHERE as_id=?"
- ),
- (service.id,),
+ res = self.get_success(
+ self.db_pool.runQuery(
+ self.engine.convert_param_style(
+ "SELECT last_txn FROM application_services_state WHERE as_id=?"
+ ),
+ (service.id,),
+ )
)
self.assertEquals(1, len(res))
self.assertEquals(txn_id, res[0][0])
- res = yield self.db_pool.runQuery(
- self.engine.convert_param_style(
- "SELECT * FROM application_services_txns WHERE txn_id=?"
- ),
- (txn_id,),
+ res = self.get_success(
+ self.db_pool.runQuery(
+ self.engine.convert_param_style(
+ "SELECT * FROM application_services_txns WHERE txn_id=?"
+ ),
+ (txn_id,),
+ )
)
self.assertEquals(0, len(res))
- @defer.inlineCallbacks
- def test_complete_appservice_txn_existing_in_state_table(self):
+ def test_complete_appservice_txn_existing_in_state_table(
+ self,
+ ) -> None:
service = Mock(id=self.as_list[0]["id"])
events = [Mock(event_id="e1"), Mock(event_id="e2")]
txn_id = 5
- yield self._set_last_txn(service.id, 4)
- yield self._insert_txn(service.id, txn_id, events)
- yield defer.ensureDeferred(
+ self.get_success(self._set_last_txn(service.id, 4))
+ self.get_success(self._insert_txn(service.id, txn_id, events))
+ self.get_success(
self.store.complete_appservice_txn(txn_id=txn_id, service=service)
)
- res = yield self.db_pool.runQuery(
- self.engine.convert_param_style(
- "SELECT last_txn, state FROM application_services_state WHERE as_id=?"
- ),
- (service.id,),
+ res = self.get_success(
+ self.db_pool.runQuery(
+ self.engine.convert_param_style(
+ "SELECT last_txn, state FROM application_services_state WHERE as_id=?"
+ ),
+ (service.id,),
+ )
)
self.assertEquals(1, len(res))
self.assertEquals(txn_id, res[0][0])
- self.assertEquals(ApplicationServiceState.UP, res[0][1])
-
- res = yield self.db_pool.runQuery(
- self.engine.convert_param_style(
- "SELECT * FROM application_services_txns WHERE txn_id=?"
- ),
- (txn_id,),
+ self.assertEquals(ApplicationServiceState.UP.value, res[0][1])
+
+ res = self.get_success(
+ self.db_pool.runQuery(
+ self.engine.convert_param_style(
+ "SELECT * FROM application_services_txns WHERE txn_id=?"
+ ),
+ (txn_id,),
+ )
)
self.assertEquals(0, len(res))
- @defer.inlineCallbacks
- def test_get_oldest_unsent_txn_none(self):
+ def test_get_oldest_unsent_txn_none(
+ self,
+ ) -> None:
service = Mock(id=self.as_list[0]["id"])
- txn = yield defer.ensureDeferred(self.store.get_oldest_unsent_txn(service))
+ txn = self.get_success(self.store.get_oldest_unsent_txn(service))
self.assertEquals(None, txn)
- @defer.inlineCallbacks
- def test_get_oldest_unsent_txn(self):
+ def test_get_oldest_unsent_txn(self) -> None:
service = Mock(id=self.as_list[0]["id"])
events = [Mock(event_id="e1"), Mock(event_id="e2")]
other_events = [Mock(event_id="e5"), Mock(event_id="e6")]
# we aren't testing store._base stuff here, so mock this out
- self.store.get_events_as_list = Mock(return_value=make_awaitable(events))
+ # (ignore needed because Mypy won't allow us to assign to a method otherwise)
+ self.store.get_events_as_list = Mock(return_value=make_awaitable(events)) # type: ignore[assignment]
- yield self._insert_txn(self.as_list[1]["id"], 9, other_events)
- yield self._insert_txn(service.id, 10, events)
- yield self._insert_txn(service.id, 11, other_events)
- yield self._insert_txn(service.id, 12, other_events)
+ self.get_success(self._insert_txn(self.as_list[1]["id"], 9, other_events))
+ self.get_success(self._insert_txn(service.id, 10, events))
+ self.get_success(self._insert_txn(service.id, 11, other_events))
+ self.get_success(self._insert_txn(service.id, 12, other_events))
- txn = yield defer.ensureDeferred(self.store.get_oldest_unsent_txn(service))
+ txn = self.get_success(self.store.get_oldest_unsent_txn(service))
self.assertEquals(service, txn.service)
self.assertEquals(10, txn.id)
self.assertEquals(events, txn.events)
- @defer.inlineCallbacks
- def test_get_appservices_by_state_single(self):
- yield self._set_state(self.as_list[0]["id"], ApplicationServiceState.DOWN)
- yield self._set_state(self.as_list[1]["id"], ApplicationServiceState.UP)
+ def test_get_appservices_by_state_single(
+ self,
+ ) -> None:
+ self.get_success(
+ self._set_state(self.as_list[0]["id"], ApplicationServiceState.DOWN)
+ )
+ self.get_success(
+ self._set_state(self.as_list[1]["id"], ApplicationServiceState.UP)
+ )
- services = yield defer.ensureDeferred(
+ services = self.get_success(
self.store.get_appservices_by_state(ApplicationServiceState.DOWN)
)
self.assertEquals(1, len(services))
self.assertEquals(self.as_list[0]["id"], services[0].id)
- @defer.inlineCallbacks
- def test_get_appservices_by_state_multiple(self):
- yield self._set_state(self.as_list[0]["id"], ApplicationServiceState.DOWN)
- yield self._set_state(self.as_list[1]["id"], ApplicationServiceState.UP)
- yield self._set_state(self.as_list[2]["id"], ApplicationServiceState.DOWN)
- yield self._set_state(self.as_list[3]["id"], ApplicationServiceState.UP)
+ def test_get_appservices_by_state_multiple(
+ self,
+ ) -> None:
+ self.get_success(
+ self._set_state(self.as_list[0]["id"], ApplicationServiceState.DOWN)
+ )
+ self.get_success(
+ self._set_state(self.as_list[1]["id"], ApplicationServiceState.UP)
+ )
+ self.get_success(
+ self._set_state(self.as_list[2]["id"], ApplicationServiceState.DOWN)
+ )
+ self.get_success(
+ self._set_state(self.as_list[3]["id"], ApplicationServiceState.UP)
+ )
- services = yield defer.ensureDeferred(
+ services = self.get_success(
self.store.get_appservices_by_state(ApplicationServiceState.DOWN)
)
self.assertEquals(2, len(services))
@@ -407,16 +455,16 @@ class ApplicationServiceTransactionStoreTestCase(unittest.TestCase):
class ApplicationServiceStoreTypeStreamIds(unittest.HomeserverTestCase):
- def make_homeserver(self, reactor, clock):
- hs = self.setup_test_homeserver()
- return hs
-
- def prepare(self, hs, reactor, clock):
+ def prepare(
+ self, reactor: MemoryReactor, clock: Clock, homeserver: HomeServer
+ ) -> None:
self.service = Mock(id="foo")
self.store = self.hs.get_datastore()
- self.get_success(self.store.set_appservice_state(self.service, "up"))
+ self.get_success(
+ self.store.set_appservice_state(self.service, ApplicationServiceState.UP)
+ )
- def test_get_type_stream_id_for_appservice_no_value(self):
+ def test_get_type_stream_id_for_appservice_no_value(self) -> None:
value = self.get_success(
self.store.get_type_stream_id_for_appservice(self.service, "read_receipt")
)
@@ -427,13 +475,13 @@ class ApplicationServiceStoreTypeStreamIds(unittest.HomeserverTestCase):
)
self.assertEquals(value, 0)
- def test_get_type_stream_id_for_appservice_invalid_type(self):
+ def test_get_type_stream_id_for_appservice_invalid_type(self) -> None:
self.get_failure(
self.store.get_type_stream_id_for_appservice(self.service, "foobar"),
ValueError,
)
- def test_set_type_stream_id_for_appservice(self):
+ def test_set_type_stream_id_for_appservice(self) -> None:
read_receipt_value = 1024
self.get_success(
self.store.set_type_stream_id_for_appservice(
@@ -455,7 +503,7 @@ class ApplicationServiceStoreTypeStreamIds(unittest.HomeserverTestCase):
)
self.assertEqual(result, read_receipt_value)
- def test_set_type_stream_id_for_appservice_invalid_type(self):
+ def test_set_type_stream_id_for_appservice_invalid_type(self) -> None:
self.get_failure(
self.store.set_type_stream_id_for_appservice(self.service, "foobar", 1024),
ValueError,
@@ -464,12 +512,12 @@ class ApplicationServiceStoreTypeStreamIds(unittest.HomeserverTestCase):
# required for ApplicationServiceTransactionStoreTestCase tests
class TestTransactionStore(ApplicationServiceTransactionStore, ApplicationServiceStore):
- def __init__(self, database: DatabasePool, db_conn, hs):
+ def __init__(self, database: DatabasePool, db_conn, hs) -> None:
super().__init__(database, db_conn, hs)
-class ApplicationServiceStoreConfigTestCase(unittest.TestCase):
- def _write_config(self, suffix, **kwargs):
+class ApplicationServiceStoreConfigTestCase(unittest.HomeserverTestCase):
+ def _write_config(self, suffix, **kwargs) -> str:
vals = {
"id": "id" + suffix,
"url": "url" + suffix,
@@ -485,41 +533,33 @@ class ApplicationServiceStoreConfigTestCase(unittest.TestCase):
f.write(yaml.dump(vals))
return path
- @defer.inlineCallbacks
- def test_unique_works(self):
+ def test_unique_works(self) -> None:
f1 = self._write_config(suffix="1")
f2 = self._write_config(suffix="2")
- hs = yield setup_test_homeserver(
- self.addCleanup, federation_sender=Mock(), federation_client=Mock()
- )
-
- hs.config.appservice.app_service_config_files = [f1, f2]
- hs.config.caches.event_cache_size = 1
+ self.hs.config.appservice.app_service_config_files = [f1, f2]
+ self.hs.config.caches.event_cache_size = 1
- database = hs.get_datastores().databases[0]
+ database = self.hs.get_datastores().databases[0]
ApplicationServiceStore(
- database, make_conn(database._database_config, database.engine, "test"), hs
+ database,
+ make_conn(database._database_config, database.engine, "test"),
+ self.hs,
)
- @defer.inlineCallbacks
- def test_duplicate_ids(self):
+ def test_duplicate_ids(self) -> None:
f1 = self._write_config(id="id", suffix="1")
f2 = self._write_config(id="id", suffix="2")
- hs = yield setup_test_homeserver(
- self.addCleanup, federation_sender=Mock(), federation_client=Mock()
- )
-
- hs.config.appservice.app_service_config_files = [f1, f2]
- hs.config.caches.event_cache_size = 1
+ self.hs.config.appservice.app_service_config_files = [f1, f2]
+ self.hs.config.caches.event_cache_size = 1
with self.assertRaises(ConfigError) as cm:
- database = hs.get_datastores().databases[0]
+ database = self.hs.get_datastores().databases[0]
ApplicationServiceStore(
database,
make_conn(database._database_config, database.engine, "test"),
- hs,
+ self.hs,
)
e = cm.exception
@@ -527,24 +567,19 @@ class ApplicationServiceStoreConfigTestCase(unittest.TestCase):
self.assertIn(f2, str(e))
self.assertIn("id", str(e))
- @defer.inlineCallbacks
- def test_duplicate_as_tokens(self):
+ def test_duplicate_as_tokens(self) -> None:
f1 = self._write_config(as_token="as_token", suffix="1")
f2 = self._write_config(as_token="as_token", suffix="2")
- hs = yield setup_test_homeserver(
- self.addCleanup, federation_sender=Mock(), federation_client=Mock()
- )
-
- hs.config.appservice.app_service_config_files = [f1, f2]
- hs.config.caches.event_cache_size = 1
+ self.hs.config.appservice.app_service_config_files = [f1, f2]
+ self.hs.config.caches.event_cache_size = 1
with self.assertRaises(ConfigError) as cm:
- database = hs.get_datastores().databases[0]
+ database = self.hs.get_datastores().databases[0]
ApplicationServiceStore(
database,
make_conn(database._database_config, database.engine, "test"),
- hs,
+ self.hs,
)
e = cm.exception
diff --git a/tests/storage/test_background_update.py b/tests/storage/test_background_update.py
index 216d816d56..d77c001506 100644
--- a/tests/storage/test_background_update.py
+++ b/tests/storage/test_background_update.py
@@ -1,3 +1,18 @@
+# Copyright 2021 The Matrix.org Foundation C.I.C.
+#
+# Licensed under the Apache License, Version 2.0 (the "License");
+# you may not use this file except in compliance with the License.
+# You may obtain a copy of the License at
+#
+# http://www.apache.org/licenses/LICENSE-2.0
+#
+# Unless required by applicable law or agreed to in writing, software
+# distributed under the License is distributed on an "AS IS" BASIS,
+# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
+# See the License for the specific language governing permissions and
+# limitations under the License.
+
+# Use backported mock for AsyncMock support on Python 3.6.
from mock import Mock
from twisted.internet.defer import Deferred, ensureDeferred
diff --git a/tests/storage/test_main.py b/tests/storage/test_main.py
index d2b7b89952..f8d11bac4e 100644
--- a/tests/storage/test_main.py
+++ b/tests/storage/test_main.py
@@ -13,42 +13,35 @@
# limitations under the License.
-from twisted.internet import defer
-
from synapse.types import UserID
from tests import unittest
-from tests.utils import setup_test_homeserver
-class DataStoreTestCase(unittest.TestCase):
- @defer.inlineCallbacks
- def setUp(self):
- hs = yield setup_test_homeserver(self.addCleanup)
+class DataStoreTestCase(unittest.HomeserverTestCase):
+ def setUp(self) -> None:
+ super(DataStoreTestCase, self).setUp()
- self.store = hs.get_datastore()
+ self.store = self.hs.get_datastore()
self.user = UserID.from_string("@abcde:test")
self.displayname = "Frank"
- @defer.inlineCallbacks
- def test_get_users_paginate(self):
- yield defer.ensureDeferred(
- self.store.register_user(self.user.to_string(), "pass")
- )
- yield defer.ensureDeferred(self.store.create_profile(self.user.localpart))
- yield defer.ensureDeferred(
+ def test_get_users_paginate(self) -> None:
+ self.get_success(self.store.register_user(self.user.to_string(), "pass"))
+ self.get_success(self.store.create_profile(self.user.localpart))
+ self.get_success(
self.store.set_profile_displayname(self.user.localpart, self.displayname)
)
- users, total = yield defer.ensureDeferred(
+ users, total = self.get_success(
self.store.get_users_paginate(0, 10, name="bc", guests=False)
)
self.assertEquals(1, total)
self.assertEquals(self.displayname, users.pop()["displayname"])
- users, total = yield defer.ensureDeferred(
+ users, total = self.get_success(
self.store.get_users_paginate(0, 10, name="BC", guests=False)
)
diff --git a/tests/test_visibility.py b/tests/test_visibility.py
index 94b19788d7..e0b08d67d4 100644
--- a/tests/test_visibility.py
+++ b/tests/test_visibility.py
@@ -13,35 +13,30 @@
# limitations under the License.
import logging
from typing import Optional
-from unittest.mock import Mock
-
-from twisted.internet import defer
-from twisted.internet.defer import succeed
from synapse.api.room_versions import RoomVersions
-from synapse.events import FrozenEvent
+from synapse.events import EventBase
+from synapse.types import JsonDict
from synapse.visibility import filter_events_for_server
-import tests.unittest
-from tests.utils import create_room, setup_test_homeserver
+from tests import unittest
+from tests.utils import create_room
logger = logging.getLogger(__name__)
TEST_ROOM_ID = "!TEST:ROOM"
-class FilterEventsForServerTestCase(tests.unittest.TestCase):
- @defer.inlineCallbacks
- def setUp(self):
- self.hs = yield setup_test_homeserver(self.addCleanup)
+class FilterEventsForServerTestCase(unittest.HomeserverTestCase):
+ def setUp(self) -> None:
+ super(FilterEventsForServerTestCase, self).setUp()
self.event_creation_handler = self.hs.get_event_creation_handler()
self.event_builder_factory = self.hs.get_event_builder_factory()
self.storage = self.hs.get_storage()
- yield defer.ensureDeferred(create_room(self.hs, TEST_ROOM_ID, "@someone:ROOM"))
+ self.get_success(create_room(self.hs, TEST_ROOM_ID, "@someone:ROOM"))
- @defer.inlineCallbacks
- def test_filtering(self):
+ def test_filtering(self) -> None:
#
# The events to be filtered consist of 10 membership events (it doesn't
# really matter if they are joins or leaves, so let's make them joins).
@@ -51,18 +46,20 @@ class FilterEventsForServerTestCase(tests.unittest.TestCase):
#
# before we do that, we persist some other events to act as state.
- yield self.inject_visibility("@admin:hs", "joined")
+ self.get_success(self._inject_visibility("@admin:hs", "joined"))
for i in range(0, 10):
- yield self.inject_room_member("@resident%i:hs" % i)
+ self.get_success(self._inject_room_member("@resident%i:hs" % i))
events_to_filter = []
for i in range(0, 10):
user = "@user%i:%s" % (i, "test_server" if i == 5 else "other_server")
- evt = yield self.inject_room_member(user, extra_content={"a": "b"})
+ evt = self.get_success(
+ self._inject_room_member(user, extra_content={"a": "b"})
+ )
events_to_filter.append(evt)
- filtered = yield defer.ensureDeferred(
+ filtered = self.get_success(
filter_events_for_server(self.storage, "test_server", events_to_filter)
)
@@ -75,34 +72,31 @@ class FilterEventsForServerTestCase(tests.unittest.TestCase):
self.assertEqual(events_to_filter[i].event_id, filtered[i].event_id)
self.assertEqual(filtered[i].content["a"], "b")
- @defer.inlineCallbacks
- def test_erased_user(self):
+ def test_erased_user(self) -> None:
# 4 message events, from erased and unerased users, with a membership
# change in the middle of them.
events_to_filter = []
- evt = yield self.inject_message("@unerased:local_hs")
+ evt = self.get_success(self._inject_message("@unerased:local_hs"))
events_to_filter.append(evt)
- evt = yield self.inject_message("@erased:local_hs")
+ evt = self.get_success(self._inject_message("@erased:local_hs"))
events_to_filter.append(evt)
- evt = yield self.inject_room_member("@joiner:remote_hs")
+ evt = self.get_success(self._inject_room_member("@joiner:remote_hs"))
events_to_filter.append(evt)
- evt = yield self.inject_message("@unerased:local_hs")
+ evt = self.get_success(self._inject_message("@unerased:local_hs"))
events_to_filter.append(evt)
- evt = yield self.inject_message("@erased:local_hs")
+ evt = self.get_success(self._inject_message("@erased:local_hs"))
events_to_filter.append(evt)
# the erasey user gets erased
- yield defer.ensureDeferred(
- self.hs.get_datastore().mark_user_erased("@erased:local_hs")
- )
+ self.get_success(self.hs.get_datastore().mark_user_erased("@erased:local_hs"))
# ... and the filtering happens.
- filtered = yield defer.ensureDeferred(
+ filtered = self.get_success(
filter_events_for_server(self.storage, "test_server", events_to_filter)
)
@@ -123,8 +117,7 @@ class FilterEventsForServerTestCase(tests.unittest.TestCase):
for i in (1, 4):
self.assertNotIn("body", filtered[i].content)
- @defer.inlineCallbacks
- def inject_visibility(self, user_id, visibility):
+ def _inject_visibility(self, user_id: str, visibility: str) -> EventBase:
content = {"history_visibility": visibility}
builder = self.event_builder_factory.for_room_version(
RoomVersions.V1,
@@ -137,18 +130,18 @@ class FilterEventsForServerTestCase(tests.unittest.TestCase):
},
)
- event, context = yield defer.ensureDeferred(
+ event, context = self.get_success(
self.event_creation_handler.create_new_client_event(builder)
)
- yield defer.ensureDeferred(
- self.storage.persistence.persist_event(event, context)
- )
+ self.get_success(self.storage.persistence.persist_event(event, context))
return event
- @defer.inlineCallbacks
- def inject_room_member(
- self, user_id, membership="join", extra_content: Optional[dict] = None
- ):
+ def _inject_room_member(
+ self,
+ user_id: str,
+ membership: str = "join",
+ extra_content: Optional[JsonDict] = None,
+ ) -> EventBase:
content = {"membership": membership}
content.update(extra_content or {})
builder = self.event_builder_factory.for_room_version(
@@ -162,17 +155,16 @@ class FilterEventsForServerTestCase(tests.unittest.TestCase):
},
)
- event, context = yield defer.ensureDeferred(
+ event, context = self.get_success(
self.event_creation_handler.create_new_client_event(builder)
)
- yield defer.ensureDeferred(
- self.storage.persistence.persist_event(event, context)
- )
+ self.get_success(self.storage.persistence.persist_event(event, context))
return event
- @defer.inlineCallbacks
- def inject_message(self, user_id, content=None):
+ def _inject_message(
+ self, user_id: str, content: Optional[JsonDict] = None
+ ) -> EventBase:
if content is None:
content = {"body": "testytest", "msgtype": "m.text"}
builder = self.event_builder_factory.for_room_version(
@@ -185,164 +177,9 @@ class FilterEventsForServerTestCase(tests.unittest.TestCase):
},
)
- event, context = yield defer.ensureDeferred(
+ event, context = self.get_success(
self.event_creation_handler.create_new_client_event(builder)
)
- yield defer.ensureDeferred(
- self.storage.persistence.persist_event(event, context)
- )
+ self.get_success(self.storage.persistence.persist_event(event, context))
return event
-
- @defer.inlineCallbacks
- def test_large_room(self):
- # see what happens when we have a large room with hundreds of thousands
- # of membership events
-
- # As above, the events to be filtered consist of 10 membership events,
- # where one of them is for a user on the server we are filtering for.
-
- import cProfile
- import pstats
- import time
-
- # we stub out the store, because building up all that state the normal
- # way is very slow.
- test_store = _TestStore()
-
- # our initial state is 100000 membership events and one
- # history_visibility event.
- room_state = []
-
- history_visibility_evt = FrozenEvent(
- {
- "event_id": "$history_vis",
- "type": "m.room.history_visibility",
- "sender": "@resident_user_0:test.com",
- "state_key": "",
- "room_id": TEST_ROOM_ID,
- "content": {"history_visibility": "joined"},
- }
- )
- room_state.append(history_visibility_evt)
- test_store.add_event(history_visibility_evt)
-
- for i in range(0, 100000):
- user = "@resident_user_%i:test.com" % (i,)
- evt = FrozenEvent(
- {
- "event_id": "$res_event_%i" % (i,),
- "type": "m.room.member",
- "state_key": user,
- "sender": user,
- "room_id": TEST_ROOM_ID,
- "content": {"membership": "join", "extra": "zzz,"},
- }
- )
- room_state.append(evt)
- test_store.add_event(evt)
-
- events_to_filter = []
- for i in range(0, 10):
- user = "@user%i:%s" % (i, "test_server" if i == 5 else "other_server")
- evt = FrozenEvent(
- {
- "event_id": "$evt%i" % (i,),
- "type": "m.room.member",
- "state_key": user,
- "sender": user,
- "room_id": TEST_ROOM_ID,
- "content": {"membership": "join", "extra": "zzz"},
- }
- )
- events_to_filter.append(evt)
- room_state.append(evt)
-
- test_store.add_event(evt)
- test_store.set_state_ids_for_event(
- evt, {(e.type, e.state_key): e.event_id for e in room_state}
- )
-
- pr = cProfile.Profile()
- pr.enable()
-
- logger.info("Starting filtering")
- start = time.time()
-
- storage = Mock()
- storage.main = test_store
- storage.state = test_store
-
- filtered = yield defer.ensureDeferred(
- filter_events_for_server(test_store, "test_server", events_to_filter)
- )
- logger.info("Filtering took %f seconds", time.time() - start)
-
- pr.disable()
- with open("filter_events_for_server.profile", "w+") as f:
- ps = pstats.Stats(pr, stream=f).sort_stats("cumulative")
- ps.print_stats()
-
- # the result should be 5 redacted events, and 5 unredacted events.
- for i in range(0, 5):
- self.assertEqual(events_to_filter[i].event_id, filtered[i].event_id)
- self.assertNotIn("extra", filtered[i].content)
-
- for i in range(5, 10):
- self.assertEqual(events_to_filter[i].event_id, filtered[i].event_id)
- self.assertEqual(filtered[i].content["extra"], "zzz")
-
- test_large_room.skip = "Disabled by default because it's slow"
-
-
-class _TestStore:
- """Implements a few methods of the DataStore, so that we can test
- filter_events_for_server
-
- """
-
- def __init__(self):
- # data for get_events: a map from event_id to event
- self.events = {}
-
- # data for get_state_ids_for_events mock: a map from event_id to
- # a map from (type_state_key) -> event_id for the state at that
- # event
- self.state_ids_for_events = {}
-
- def add_event(self, event):
- self.events[event.event_id] = event
-
- def set_state_ids_for_event(self, event, state):
- self.state_ids_for_events[event.event_id] = state
-
- def get_state_ids_for_events(self, events, types):
- res = {}
- include_memberships = False
- for (type, state_key) in types:
- if type == "m.room.history_visibility":
- continue
- if type != "m.room.member" or state_key is not None:
- raise RuntimeError(
- "Unimplemented: get_state_ids with type (%s, %s)"
- % (type, state_key)
- )
- include_memberships = True
-
- if include_memberships:
- for event_id in events:
- res[event_id] = self.state_ids_for_events[event_id]
-
- else:
- k = ("m.room.history_visibility", "")
- for event_id in events:
- hve = self.state_ids_for_events[event_id][k]
- res[event_id] = {k: hve}
-
- return succeed(res)
-
- def get_events(self, events):
- return succeed({event_id: self.events[event_id] for event_id in events})
-
- def are_users_erased(self, users):
- return succeed({u: False for u in users})
diff --git a/tests/unittest.py b/tests/unittest.py
index eea0903f05..1431848367 100644
--- a/tests/unittest.py
+++ b/tests/unittest.py
@@ -331,16 +331,13 @@ class HomeserverTestCase(TestCase):
time.sleep(0.01)
def wait_for_background_updates(self) -> None:
- """Block until all background database updates have completed.
-
- Note that callers must ensure there's a store property created on the
- testcase.
- """
+ """Block until all background database updates have completed."""
+ store = self.hs.get_datastore()
while not self.get_success(
- self.store.db_pool.updates.has_completed_background_updates()
+ store.db_pool.updates.has_completed_background_updates()
):
self.get_success(
- self.store.db_pool.updates.do_next_background_update(False), by=0.1
+ store.db_pool.updates.do_next_background_update(False), by=0.1
)
def make_homeserver(self, reactor, clock):
diff --git a/tests/util/test_lrucache.py b/tests/util/test_lrucache.py
index 6578f3411e..291644eb7d 100644
--- a/tests/util/test_lrucache.py
+++ b/tests/util/test_lrucache.py
@@ -13,6 +13,7 @@
# limitations under the License.
+from typing import List
from unittest.mock import Mock
from synapse.util.caches.lrucache import LruCache, setup_expire_lru_cache_entries
@@ -261,6 +262,17 @@ class LruCacheSizedTestCase(unittest.HomeserverTestCase):
self.assertEquals(cache["key4"], [4])
self.assertEquals(cache["key5"], [5, 6])
+ def test_zero_size_drop_from_cache(self) -> None:
+ """Test that `drop_from_cache` works correctly with 0-sized entries."""
+ cache: LruCache[str, List[int]] = LruCache(5, size_callback=lambda x: 0)
+ cache["key1"] = []
+
+ self.assertEqual(len(cache), 0)
+ cache.cache["key1"].drop_from_cache()
+ self.assertIsNone(
+ cache.pop("key1"), "Cache entry should have been evicted but wasn't"
+ )
+
class TimeEvictionTestCase(unittest.HomeserverTestCase):
"""Test that time based eviction works correctly."""
|
